Objective 5. Describe Networks and Define Network Terms
As discussed earlier, computers and the various peripherals that are connected to them are called hardware. However, connecting one computer to another creates a network. Networks consist of two or more connected computers plus the various peripheral devices that are attached to them. Each object connected to a network, whether it is a computer or a peripheral device, is known as a node. Some of the benefits of computer networks include the ability to share resources (such as printers and scanners) and software, and improved communication and data sharing. Computers can be connected to a network in several ways. They can use existing telephone wires or power lines, or use coaxial, UTP, or fiber-optic cable. Networks can also be wireless, in which case they use radio waves instead of wires or cables to connect.
A computer network that connects computers reasonably close together, such as within a home or in a small office or business, is called a local area network (LAN). Usually these networks are contained within a single building or group of adjacent buildings. If the network begins to cover a larger geographic area or begins to include other networks, it becomes a wide area network (WAN). An example of this is the network used by Penn State University. Penn State has many campuses located across the state of Pennsylvania. Because the different campuses are connected through a WAN, students and teachers are able to use a computer in one location and access files or resources located at any of the other campuses, wherever they might be located. Both LANs and WANs can be wired or wireless. Wired LANs might use phone lines or cable connections, while wired WANs might use phone lines, satellites, or special leased lines, known as T-1 or T-3 lines, for high-speed communication. Did you realize the Internet is actually the largest network of all because it connects computers all over the globe?
Networks can be configured in several ways. There are two main categories: peer-to-peer and client/server. Peer-to-peer or P2P networks are most commonly found in homes and small businesses. In a peer-to-peer network, each node on the network can communicate with every other node. Peer-to-peer networks are relatively easy to set up, but tend to be rather small. This makes them ideal for home use, although not as desirable in the workplace. If a network has more than ten nodes, it is generally best to use the client/server network instead. Remember that a node can be a computer, printer, scanner, modem, or any other peripheral device that can be connected to a computer. Therefore, it isn't difficult to find more than ten nodes in an office or business setting. Client/server networks typically have two different types of computers. The client computer is the one most people directly interact with. This is the computer used at your desk or workstation to write letters, send e-mail, produce invoices, or perform any of the many tasks that can be accomplished with a computer. In contrast, the server computer is typically kept in a secure location and is used to manage network resources. Sometimes servers are dedicated and are assigned specific tasks. For instance, a Web server is used to deliver Web pages, a file server is used to store and archive files, and a print server manages the printing resources for the network.
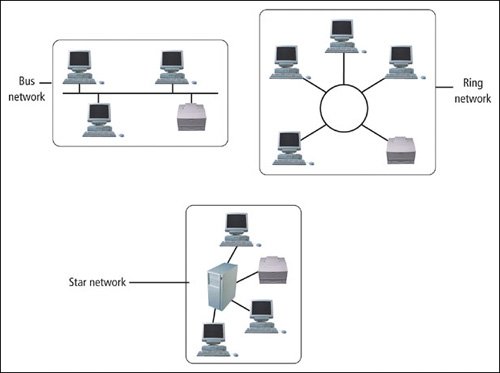
Network topology describes the different types of network architecture used for client/server networks. Just as there are different sizes and styles of buildings that are designed for different purposes, networks are designed to be physically configured and connected in different ways. The three most common layouts are explained in the following list. Figure 1.27 shows an example of each of these layouts, while Figure 1.28 discusses the advantages and disadvantages of each of these topographies.
Figure 1.27.
|
Topology |
Advantages |
Disadvantages |
|---|---|---|
|
Bus |
Uses a minimal amount of cabling Easy, reliable, and inexpensive to install |
Breaks in the cable can disable the network Large numbers of users will greatly decrease performance because of high volumes of data traffic |
|
Ring |
Allocates access to the network fairly Performance remains acceptable even with large numbers of users |
Adding or removing nodes disables the network Failure of one computer can bring down the entire network Problems in data transmission can sometimes be difficult to find |
|
Star |
Failure of one computer does not affect other computers on the network Centralized design simplifies trouble-shooting and repairs Easy to add additional computers or network segments as needed (high scalability) Performance remains acceptable even with large numbers of users |
Requires more cable and is often more expensive than a bus or ring topology The switch is a central point of failure. If it fails, all computers connected to that switch are affected |
- Bus topology connects each node to a single, central high-speed line known as a bus. No server is used, and, although it is possible for each node to communicate with all the others, they can only do so one at a time. If one computer or device is sending over the network, all the others must wait till the transmission is complete before they can begin. Because this is an inexpensive and easy way to connect, this topology is often found in peer-to-peer networks.
- Ring topology, sometimes known as token-ring topology, connects each node to the next, forming a loop or a circle. The data that's sent is passed from node to node, traveling around the circle in only one direction. A token travels around the ring until one of the nodes is ready to send a transmission. The node then holds the token until the transmission is finished, preventing any of the other devices from sending until the token is released to make its way around the circle again. This type of topology gives each device an equal chance of being able to send data and prevents one node from doing all the communicating.
- Star topology is the most frequent networking style used for businesses. It offers a high degree of flexibility. Each node is connected to a special device known as a switch, which is centrally located. Each node must go through the switch to communicate with the others. If something happens to one node, the others are still able to communicate.
Objective 6 Identify Safe Computing Practices |
Windows XP
- Chapter One. Getting Started with Windows XP
- Project 1A. Windows XP
- Objective 1. Get Started with Windows XP
- Objective 2. Resize, Move, and Scroll Windows
- Objective 3. Maximize, Restore, Minimize, and Close a Window
- Objective 4. Create a New Folder
- Objective 5. Copy, Move, Rename, and Delete Files
- Objective 6. Find Files and Folders
- Objective 7. Compress Files
- Summary
- Key Terms
- Concepts Assessments
Outlook 2003
- Chapter One. Getting Started with Outlook 2003
- Getting Started with Microsoft Office Outlook 2003
- Project 1A. Exploring Outlook 2003
- Objective 1. Start and Navigate Outlook
- Objective 2. Read and Respond to E-mail
- Objective 3. Store Contact and Task Information
- Objective 4. Work with the Calendar
- Objective 5. Delete Outlook Information and Close Outlook
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- GO! with Help
Internet Explorer
- Chapter One. Getting Started with Internet Explorer
- Getting Started with Internet Explorer 6.0
- Project 1A. College and Career Information
- Objective 1. Start Internet Explorer and Identify Screen Elements
- Objective 2. Navigate the Internet
- Objective 3. Create and Manage Favorites
- Objective 4. Search the Internet
- Objective 5. Save and Print Web Pages
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
Computer Concepts
- Chapter One. Basic Computer Concepts
- Objective 1. Define Computer and Identify the Four Basic Computing Functions
- Objective 2. Identify the Different Types of Computers
- Objective 3. Describe Hardware Devices and Their Uses
- Objective 4. Identify Types of Software and Their Uses
- Objective 5. Describe Networks and Define Network Terms
- Objective 6. Identify Safe Computing Practices
- Summary
- In this Chapter You Learned How to
- Key Terms
- Concepts Assessments
Word 2003
Chapter One. Creating Documents with Microsoft Word 2003
- Chapter One. Creating Documents with Microsoft Word 2003
- Getting Started with Microsoft Office Word 2003
- Project 1A. Thank You Letter
- Objective 1. Create and Save a New Document
- Objective 2. Edit Text
- Objective 3. Select, Delete, and Format Text
- Objective 4. Create Footers and Print Documents
- Project 1B. Party Themes
- Objective 5. Navigate the Word Window
- Objective 6. Add a Graphic to a Document
- Objective 7. Use the Spelling and Grammar Checker
- Objective 8. Preview and Print Documents, Close a Document, and Close Word
- Objective 9. Use the Microsoft Help System
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Help
Chapter Two. Formatting and Organizing Text
- Formatting and Organizing Text
- Project 2A. Alaska Trip
- Objective 1. Change Document and Paragraph Layout
- Objective 2. Change and Reorganize Text
- Objective 3. Create and Modify Lists
- Project 2B. Research Paper
- Objective 4. Insert and Format Headers and Footers
- Objective 5. Insert Frequently Used Text
- Objective 6. Insert and Format References
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Help
Chapter Three. Using Graphics and Tables
- Using Graphics and Tables
- Project 3A. Job Opportunities
- Objective 1. Insert and Modify Clip Art and Pictures
- Objective 2. Use the Drawing Toolbar
- Project 3B. Park Changes
- Objective 3. Set Tab Stops
- Objective 4. Create a Table
- Objective 5. Format a Table
- Objective 6. Create a Table from Existing Text
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Help
Chapter Four. Using Special Document Formats, Columns, and Mail Merge
- Using Special Document Formats, Columns, and Mail Merge
- Project 4A. Garden Newsletter
- Objective 1. Create a Decorative Title
- Objective 2. Create Multicolumn Documents
- Objective 3. Add Special Paragraph Formatting
- Objective 4. Use Special Character Formats
- Project 4B. Water Matters
- Objective 5. Insert Hyperlinks
- Objective 6. Preview and Save a Document as a Web Page
- Project 4C. Recreation Ideas
- Objective 7. Locate Supporting Information
- Objective 8. Find Objects with the Select Browse Object Button
- Project 4D. Mailing Labels
- Objective 9. Create Labels Using the Mail Merge Wizard
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Help
Excel 2003
Chapter One. Creating a Worksheet and Charting Data
- Creating a Worksheet and Charting Data
- Project 1A. Tableware
- Objective 1. Start Excel and Navigate a Workbook
- Objective 2. Select Parts of a Worksheet
- Objective 3. Enter and Edit Data in a Worksheet
- Objective 4. Construct a Formula and Use the Sum Function
- Objective 5. Format Data and Cells
- Objective 6. Chart Data
- Objective 7. Annotate a Chart
- Objective 8. Prepare a Worksheet for Printing
- Objective 9. Use the Excel Help System
- Project 1B. Gas Usage
- Objective 10. Open and Save an Existing Workbook
- Objective 11. Navigate and Rename Worksheets
- Objective 12. Enter Dates and Clear Formats
- Objective 13. Use a Summary Sheet
- Objective 14. Format Worksheets in a Workbook
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Help
Chapter Two. Designing Effective Worksheets
- Designing Effective Worksheets
- Project 2A. Staff Schedule
- Objective 1. Use AutoFill to Fill a Pattern of Column and Row Titles
- Objective 2. Copy Text Using the Fill Handle
- Objective 3. Use AutoFormat
- Objective 4. View, Scroll, and Print Large Worksheets
- Project 2B. Inventory Value
- Objective 5. Design a Worksheet
- Objective 6. Copy Formulas
- Objective 7. Format Percents, Move Formulas, and Wrap Text
- Objective 8. Make Comparisons Using a Pie Chart
- Objective 9. Print a Chart on a Separate Worksheet
- Project 2C. Population Growth
- Objective 10. Design a Worksheet for What-If Analysis
- Objective 11. Perform What-If Analysis
- Objective 12. Compare Data with a Line Chart
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Help
Chapter Three. Using Functions and Data Tables
- Using Functions and Data Tables
- Project 3A. Geography Lecture
- Objective 1. Use SUM, AVERAGE, MIN, and MAX Functions
- Objective 2. Use a Chart to Make Comparisons
- Project 3B. Lab Supervisors
- Objective 3. Use COUNTIF and IF Functions, and Apply Conditional Formatting
- Objective 4. Use a Date Function
- Project 3C. Loan Payment
- Objective 5. Use Financial Functions
- Objective 6. Use Goal Seek
- Objective 7. Create a Data Table
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Help
Access 2003
Chapter One. Getting Started with Access Databases and Tables
- Getting Started with Access Databases and Tables
- Project 1A. Academic Departments
- Objective 1. Rename a Database
- Objective 2. Start Access, Open an Existing Database, and View Database Objects
- Project 1B. Fundraising
- Objective 3. Create a New Database
- Objective 4. Create a New Table
- Objective 5. Add Records to a Table
- Objective 6. Modify the Table Design
- Objective 7. Create Table Relationships
- Objective 8. Find and Edit Records in a Table
- Objective 9. Print a Table
- Objective 10. Close and Save a Database
- Objective 11. Use the Access Help System
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Help
Chapter Two. Sort, Filter, and Query a Database
- Sort, Filter, and Query a Database
- Project 2A. Club Fundraiser
- Objective 1. Sort Records
- Objective 2. Filter Records
- Objective 3. Create a Select Query
- Objective 4. Open and Edit an Existing Query
- Objective 5. Sort Data in a Query
- Objective 6. Specify Text Criteria in a Query
- Objective 7. Print a Query
- Objective 8. Specify Numeric Criteria in a Query
- Objective 9. Use Compound Criteria
- Objective 10. Create a Query Based on More Than One Table
- Objective 11. Use Wildcards in a Query
- Objective 12. Use Calculated Fields in a Query
- Objective 13. Group Data and Calculate Statistics in a Query
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Access Help
Chapter Three. Forms and Reports
- Forms and Reports
- Project 3A. Fundraiser
- Objective 1. Create an AutoForm
- Objective 2. Use a Form to Add and Delete Records
- Objective 3. Create a Form Using the Form Wizard
- Objective 4. Modify a Form
- Objective 5. Create an AutoReport
- Objective 6. Create a Report Using the Report Wizard
- Objective 7. Modify the Design of a Report
- Objective 8. Print a Report and Keep Data Together
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Help
Powerpoint 2003
Chapter One. Getting Started with PowerPoint 2003
- Getting Started with PowerPoint 2003
- Project 1A. Expansion
- Objective 1. Start and Exit PowerPoint
- Objective 2. Edit a Presentation Using the Outline/Slides Pane
- Objective 3. Format and Edit a Presentation Using the Slide Pane
- Objective 4. View and Edit a Presentation in Slide Sorter View
- Objective 5. View a Slide Show
- Objective 6. Create Headers and Footers
- Objective 7. Print a Presentation
- Objective 8. Use PowerPoint Help
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Help
Chapter Two. Creating a Presentation
- Creating a Presentation
- Project 2A. Teenagers
- Objective 1. Create a Presentation
- Objective 2. Modify Slides
- Project 2B. History
- Objective 3. Create a Presentation Using a Design Template
- Objective 4. Import Text from Word
- Objective 5. Move and Copy Text
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Help
Chapter Three. Formatting a Presentation
- Project 3A. Emergency
- Objective 1. Format Slide Text
- Objective 2. Modify Placeholders
- Objective 3. Modify Slide Master Elements
- Objective 4. Insert Clip Art
- Project 3B. Volunteers
- Objective 5. Apply Bullets and Numbering
- Objective 6. Customize a Color Scheme
- Objective 7. Modify the Slide Background
- Objective 8. Apply an Animation Scheme
- Summary
- Key Terms
- Concepts Assessments
- Skill Assessments
- Performance Assessments
- Mastery Assessments
- Problem Solving
- You and GO!
- Business Running Case
- GO! with Help
Integrated Projects
Chapter One. Using Access Data with Other Office Applications
- Chapter One. Using Access Data with Other Office Applications
- Introduction
- Project 1A. Meeting Slides
- Objective 1. Export Access Data to Excel
- Objective 2. Create a Formula in Excel
- Objective 3. Create a Chart in Excel
- Objective 4. Copy Access Data into a Word Document
- Objective 5. Copy Excel Data into a Word Document
- Objective 6. Insert an Excel Chart into a PowerPoint Presentation
Chapter Two. Using Tables in Word and Excel
- Chapter Two. Using Tables in Word and Excel
- Introduction
- Project 2A. Meeting Notes
- Objective 1. Plan a Table in Word
- Objective 2. Enter Data and Format a Table in Word
- Objective 3. Create a Table in Word from Excel Data
- Objective 4. Create Excel Worksheet Data from a Word Table
Chapter Three. Using Excel as a Data Source in a Mail Merge
- Chapter Three. Using Excel as a Data Source in a Mail Merge
- Introduction
- Project 3A. Mailing Labels
- Objective 1. Prepare a Mail Merge Document as Mailing Labels
- Objective 2. Choose an Excel Worksheet as a Data Source
- Objective 3. Produce and Save Merged Mailing Labels
- Objective 4. Open a Saved Main Document for Mail Merge
Chapter Four. Linking Data in Office Documents
- Chapter Four. Linking Data in Office Documents
- Introduction
- Project 4A. Weekly Sales
- Objective 1. Insert and Link in Word an Excel Object
- Objective 2. Format an Object in Word
- Objective 3. Open a Word Document That Includes a Linked Object, and Update Links
Chapter Five. Creating Presentation Content from Office Documents
EAN: 2147483647
Pages: 448
