Implementing View-Level Security
Using a read access list is a way in which view access can be restricted. This can be considered security, however, only if the user who cannot access the view is also restricted from creating views of her own. Keep in mind that any user with design capabilities and the ability to create a view in your database can mimic any view that you restrict.
The read access list is contained in the Security tab of the View properties, as shown in Figure 23.17. The Security tab is represented by a key in all design elements that contain security.
Figure 23.17. The read access list for a view can be used to restrict access to data.
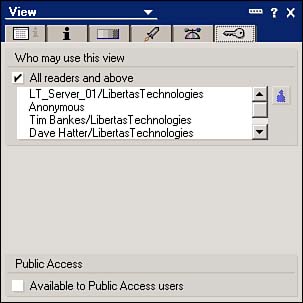
To restrict access to the view, uncheck the All Readers and Above check box, and check the individual and group names in the name list for those names that should have access to the view. The entries that appear in the list are all the entries in the ACL, including any roles you've defined. You can also select individual names from the Domino Directory by clicking on the person icon next to the names list. Remember, this is a security refinement and does not override the ACL.
Notice the check box for Available to Public Access Users in Figure 23.17. Checking this box is all that's required to make a view available to public access users.
Part I. Introduction to Release 6
Whats New in Release 6?
- Whats New in Release 6?
- A Brief History of Lotus Notes
- Major Features of Lotus Notes
- Types of Applications
- Whats New in Domino Designer?
- New Design Element Features
- New Language Features
The Release 6 Object Store
- The Release 6 Object Store
- Defining a Domino Database
- Understanding the Database Structure
- Creating a Database
- Working with Database Properties
- Understanding Design Templates
- Creating Your Own Templates
- Inheriting Designs from Templates
- Using Templates to Replicate Design Changes
- Using Templates as Design Libraries
- Archiving Versions with Templates
The Integrated Development Environment
- The Integrated Development Environment
- Working in the Application Design Environment
- Working with the Properties Box
- Understanding the Work Pane
- Using the Programmers Pane
- Understanding the Info List
- Understanding the Action Pane
- Customizing the Tools Menu
- Printing Source Code
- Using the HTML Editor
- Locking Design Elements
Part II. Foundations of Application Design
Forms Design
- Forms Design
- Designing Forms
- Setting Form Properties
- Working with Text Properties
- Working with Fields
- Writing Formulas in Fields
Advanced Form Design
- Advanced Form Design
- Working with Tables
- Using Graphic Objects on Forms
- Working with Form-Level Events
- Using Form Actions
- Working with Hotspots
- Understanding Sections and Section Properties
- Using Layout Regions
- Working with Special Forms
- Creating Reusable Design Objects
- Using Embedded Elements
- Using the Form Design Document
Designing Views
- Designing Views
- Defining the Elements of a View
- Creating a View
- Setting View Properties
- Creating Advanced View Selections
- Adding and Editing View Columns
- Using View Column Properties
- Adding Actions to a View
- Creating Calendar Views
- Understanding Folders
Using Shared Resources in Domino Applications
- Shared Resources
- Sharing Images Within a Database
- Creating Shared Files
- Creating Shared Applets
- Shared Code
- Creating Subforms
- Creating Shared Fields
- Creating Shared Actions
- Script Libraries
- Database Resources
Using the Page Designer
- Using the Page Designer
- Understanding Pages
- Working with the Page Properties Box
- Using the Page Designer
- Adding Layers to Your Pages
Creating Outlines
- Creating Outlines
- Creating an Outline
- Working with Outline Entries
- Embedding Outlines
- Adding an Outline to a Frameset
Adding Framesets to Domino Applications
- Adding Framesets to Domino Applications
- Creating a Frameset
- Using the Frameset Designer
- Working with Frames
- Viewing the HTML Source of Your Frameset
- Launching the Frameset
Automating Your Application with Agents
- Automating Your Application with Agents
- Working with Agents
- Creating an Agent
- Working in the Agent Builder Design Window
- Using @Commands in Agents
- Putting Your Agent to Work
- Creating a Complex Agent
- Using LotusScript in Agents
- Creating Web Agents Using Formulas and LotusScript
- Using Java in Agents
- Testing and Debugging Agents, the Agent Log, and Agent Properties
- Agent Properties via the Agent InfoBox
Part III. Programming Domino Applications
Using the Formula Language
- Using the Formula Language
- Overview of the Formula Language
- Knowing Where to Use @Functions and @Commands
- Formula Syntax
- Limitations of the Formula Language
- Working with Statements
- Using Logical @Functions
- Working with Date and Time @Functions
- Working with Strings
- Getting Session and User Information
- Working with Documents
- Retrieving Data with @DbColumn and @DbLookup
- Working with Lists
- Getting User Input
- Controlling the Flow of a Formula
- Error Handling
Real-World Examples Using the Formula Language
- Real-World Examples Using the Formula Language
- Programming Practices
- Using Formulas in Forms and Subforms
- Writing Field Formulas
- Writing View Formulas
- Using Hide When Formulas
- Working with Forms, Views, and Shared Actions
Writing LotusScript for Domino Applications
- Writing LotusScript for Domino Applications
- Software Construction
- Fundamental Elements of LotusScript
- New Technologies and LotusScript
Real-World LotusScript Examples
- Real-World LotusScript Examples
- Real-World Example 1: Importing a Delimited Text File
- Real-World Example 2: Delete a Parent Document and All Its Children: DeleteParentAndChildren
- Real-World Example 3: Schedule an Agent Robot to Refresh All the Documents in a View: Robot-DailyRefreshAllDocs
- Real-World Example 4: Return a Web User to the Place Where He Started After a Document Is Submitted: WebQuerySave-DocSubmit
Writing JavaScript for Domino Applications
- Writing JavaScript for Domino Applications
- What Is JavaScript?
- JavaScript Is Not Java
- JavaScript and the Domino IDE
- The Document Object Model
- JavaScript Support in Domino 6
- When to Use JavaScript
- A Look at JavaScript in Domino
- JavaScript Libraries in Domino
- JavaScript Principles 101
- Syntax and Command Blocks
- Statements
- Output
- Functions
- Objects
- Input Validation
- Validating Check Boxes
- Validating Radio Buttons
- Validating Selection Lists
- Calculations
- JavaScript Application
Real-World JavaScript Examples
- Real-World JavaScript Examples
- Real-World Example 1: Dynamic Drop-Down Lists on the Web
- Real-World Example 2: Dialog Boxes and window. opener on the Web
- Real-World Example 3: Dynamic Tables
- Real-World Example 4: Useful JavaScript Utilities
Writing Java for Domino Applications
- Writing Java for Domino Applications
- Introduction to Java
- Choosing a Java Solution in Domino
- Understanding the Notes Object Interface
- Writing Java Agents
- Using Other Java IDEs
- Other Uses for Java
Real-World Java Examples
Enhancing Domino Applications for the Web
- Enhancing Domino Applications for the Web
- Whats New in Designer 6
- Understanding the Domino Web Application Server
- Understanding the Basics of HTML
- Using HTML in Domino Designer
- Adding Power with Domino URLs
- Views and Forms Working Together on the Web
- Incorporating Flash into Your Web Pages
- What Its All About: XML Exposed
- How Does Domino Use XML?
Part IV. Advanced Design Topics
Accessing Data with XML
Accessing Data with DECS and DCRs
- Accessing Data with DECS and DCRs
- What Is DECS?
- The External Data Source
- DECS Administrator
- Creating the Activity
- Accessing the Application
- DECS Summary
- Data Connection Resources
- DCR Example
- Tips on External Data Access
Security and Domino Applications
- Security and Domino Applications
- How Does Domino Security Work?
- Enabling Physical Security
- Setting Server Access
- Database Access Control Lists
- The Role of the Domino Directory in Application Security
- ACL Privileges
- Enabling Database Encryption
- Using Roles
- Implementing View-Level Security
- Implementing Form-Level Security
- Implementing Document-Level Security
- Applying Field-Level Security
- Hiding the Design of Your Application
Creating Workflow Applications
- Creating Workflow Applications
- The Evolution of Groupware
- Introducing Workflow
- Creating Mail-Enabled Applications
- Using Triggers to Send Email
- Sending Mail with LotusScript
Analyzing Domino Applications
Part V. Appendices
Appendix A. HTML Reference
Appendix B. Domino URL Reference
EAN: 2147483647
Pages: 288
