Configuring Static Routes
Deployment and configuration of static routes is appropriate when the Cisco ASAs cannot dynamically build a route to a specific destination. The device to which the Cisco ASA is forwarding the packets might not support any dynamic routing protocols or the deployment is basic and uncomplicated. Dynamic routing protocols, such as RIP and OSPF, must be considered if the network is fairly large and complex. Static routes are easy to configure. However, they do not scale well in large environments.
It is strongly recommended that you have a complete understanding of your network topology before configuring routing in your Cisco ASA. A best practice is to have a network topology diagram on hand that you can refer to when configuring your Cisco ASA.
Static routes are configured using the route command, as shown in the following syntax:
route interface network mask gateway metric [tunneled]
Table 6-1 details the options available within the route command.
|
Option |
Description |
|---|---|
|
interface |
The specific interface name for which the route will apply. It must match the interface name configured by the nameif command under the specific interface configuration section. |
|
network |
The address of the remote network or host. If configuring a default route, use 0.0.0.0 or just 0. |
|
mask |
The subnet mask of the remote network. If configuring a default route, use 0.0.0.0 or just 0 as the subnet mask. |
|
gateway |
The gateway to which the ASA will forward the packets. |
|
metric |
The number of hops between the ASA and the destination network or host. |
|
tunneled |
This option is used to configure a tunnel default gateway. This option can be used only with default gateways. |
Figure 6-1 shows a simple static route topology that includes a Cisco ASA with two interfaces configured (outside and inside).
Figure 6-1. Basic IP Routing Configuration Using Static Routes
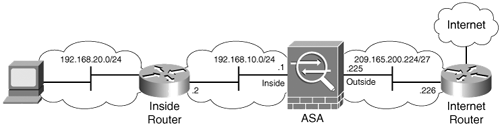
In the example shown in Figure 6-1, a static default route is configured for the Cisco ASA to be able to forward packets to the Internet through the Internet router. The route statement will look like this:
route outside 0.0.0.0 0.0.0.0 209.165.200.226 1
Note
You can configure up to three default routes for traffic load-balancing. They should all point to the same interface.
A separate static route needs to be configured for the Cisco ASA to be able to reach the private network 192.168.20.0/24. This route entry must be configured as follows:
route inside 192.168.20.0 255.255.255.0 192.168.10.2 1
The show route command can be used to view the Cisco ASA's routing table and verify the configuration. Here is an example of the output of the show route command after configuring the previously mentioned static route statements:
Chicago# show route S 0.0.0.0 0.0.0.0 [1/0] via 209.165.200.226, outside C 192.168.10.0 255.255.255.0 is directly connected, inside S 192.168.20.0 255.255.255.0 [1/0] via 192.168.10.2, inside C 209.165.200.224 255.255.255.224 is directly connected, outside
The letter S by each route statement indicates that it is a statically configured route entry. The letter C indicates that it is a directly connected route. The first number in the brackets is the administrative distance of the information source; the second number is the metric for the route. Administrative distance is the feature used by routing devices to select the best path when there are two or more different routes to the same destination from two different routing protocols.
Tip
The show route command is useful when troubleshooting any routing problems. It provides not only the gateway's IP address for each route entry, but also the interface that is connected to that gateway.
The show route command can be used with an interface name to display only the routes going out of the specified interface.
Figure 6-2 shows another simple static route topology with the addition of a demilitarized zone (DMZ).
Figure 6-2. IP Routing Configuration Using Static Routes to a Network on a DMZ Interface
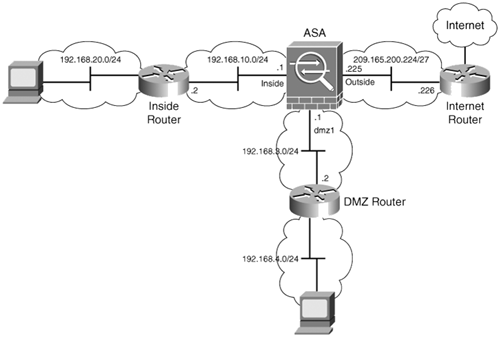
To forward IP packets to the 192.168.4.0/24 network, a static route must be configured as follows (assuming that the DMZ interface is labeled dmz1):
route dmz1 192.168.4.0 255.255.255.0 192.168.3.2 1
Earlier, the tunneled keyword on a default gateway was mentioned. This option configures a tunnel default gateway. When configured, the Cisco ASA forwards all tunnel (decrypted) traffic to the specified device. This is similar to the tunnel default gateway option on the Cisco VPN 3000 Series Concentrators. Chapter 15, "Site-to-Site IPSec VPNs," covers the use of the tunnel default gateway feature.
Note
Dynamic routing protocols are not supported when the security Cisco ASA is running in multimode. Cisco ASA has the ability to create multiple security contexts (virtual firewalls), as covered in Chapter 9, "Security Contexts."
A Cisco ASA configured with dynamic routing protocols can advertise configured static routes to its neighbors or peers. This process is called redistribution of static routes. This methodology is discussed later in this chapter under the "Configuring the Cisco ASA as an ASBR" section.
Part I: Product Overview
Introduction to Network Security
- Introduction to Network Security
- Firewall Technologies
- Intrusion Detection and Prevention Technologies
- Network-Based Attacks
- Virtual Private Networks
- Summary
Product History
- Product History
- Cisco Firewall Products
- Cisco IDS Products
- Cisco VPN Products
- Cisco ASA All-in-One Solution
- Summary
Hardware Overview
Part II: Firewall Solution
Initial Setup and System Maintenance
- Initial Setup and System Maintenance
- Accessing the Cisco ASA Appliances
- Managing Licenses
- Initial Setup
- IP Version 6
- Setting Up the System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Network Access Control
- Network Access Control
- Packet Filtering
- Advanced ACL Features
- Content and URL Filtering
- Deployment Scenarios Using ACLs
- Monitoring Network Access Control
- Understanding Address Translation
- DNS Doctoring
- Monitoring Address Translations
- Summary
IP Routing
- IP Routing
- Configuring Static Routes
- RIP
- OSPF
- IP Multicast
- Deployment Scenarios
- Summary
Authentication, Authorization, and Accounting (AAA)
- Authentication, Authorization, and Accounting (AAA)
- AAA Protocols and Services Supported by Cisco ASA
- Defining an Authentication Server
- Configuring Authentication of Administrative Sessions
- Authenticating Firewall Sessions (Cut-Through Proxy Feature)
- Configuring Authorization
- Configuring Accounting
- Deployment Scenarios
- Troubleshooting AAA
- Summary
Application Inspection
- Application Inspection
- Enabling Application Inspection Using the Modular Policy Framework
- Selective Inspection
- Computer Telephony Interface Quick Buffer Encoding Inspection
- Domain Name System
- Extended Simple Mail Transfer Protocol
- File Transfer Protocol
- General Packet Radio Service Tunneling Protocol
- H.323
- HTTP
- ICMP
- ILS
- MGCP
- NetBIOS
- PPTP
- Sun RPC
- RSH
- RTSP
- SIP
- Skinny
- SNMP
- SQL*Net
- TFTP
- XDMCP
- Deployment Scenarios
- Summary
Security Contexts
- Security Contexts
- Architectural Overview
- Configuration of Security Contexts
- Deployment Scenarios
- Monitoring and Troubleshooting the Security Contexts
- Summary
Transparent Firewalls
- Transparent Firewalls
- Architectural Overview
- Transparent Firewalls and VPNs
- Configuration of Transparent Firewall
- Deployment Scenarios
- Monitoring and Troubleshooting the Transparent Firewall
- Summary
Failover and Redundancy
- Failover and Redundancy
- Architectural Overview
- Failover Configuration
- Deployment Scenarios
- Monitoring and Troubleshooting Failovers
- Summary
Quality of Service
- Quality of Service
- Architectural Overview
- Configuring Quality of Service
- QoS Deployment Scenarios
- Monitoring QoS
- Summary
Part III: Intrusion Prevention System (IPS) Solution
Intrusion Prevention System Integration
- Intrusion Prevention System Integration
- Adaptive Inspection Prevention Security Services Module Overview (AIP-SSM)
- Directing Traffic to the AIP-SSM
- AIP-SSM Module Software Recovery
- Additional IPS Features
- Summary
Configuring and Troubleshooting Cisco IPS Software via CLI
- Configuring and Troubleshooting Cisco IPS Software via CLI
- Cisco IPS Software Architecture
- Introduction to the CIPS 5.x Command-Line Interface
- User Administration
- AIP-SSM Maintenance
- Advanced Features and Configuration
- Summary
Part IV: Virtual Private Network (VPN) Solution
Site-to-Site IPSec VPNs
- Site-to-Site IPSec VPNs
- Preconfiguration Checklist
- Configuration Steps
- Advanced Features
- Optional Commands
- Deployment Scenarios
- Monitoring and Troubleshooting Site-to-Site IPSec VPNs
- Summary
Remote Access VPN
- Remote Access VPN
- Cisco IPSec Remote Access VPN Solution
- Advanced Cisco IPSec VPN Features
- Deployment Scenarios of Cisco IPSec VPN
- Monitoring and Troubleshooting Cisco Remote Access VPN
- Cisco WebVPN Solution
- Advanced WebVPN Features
- Deployment Scenarios of WebVPN
- Monitoring and Troubleshooting WebVPN
- Summary
Public Key Infrastructure (PKI)
- Public Key Infrastructure (PKI)
- Introduction to PKI
- Enrolling the Cisco ASA to a CA Using SCEP
- Manual (Cut-and-Paste) Enrollment
- Configuring CRL Options
- Configuring IPSec Site-to-Site Tunnels Using Certificates
- Configuring the Cisco ASA to Accept Remote-Access VPN Clients Using Certificates
- Troubleshooting PKI
- Summary
Part V: Adaptive Security Device Manager
Introduction to ASDM
- Introduction to ASDM
- Setting Up ASDM
- Initial Setup
- Functional Screens
- Interface Management
- System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Firewall Management Using ASDM
- Firewall Management Using ASDM
- Access Control Lists
- Address Translation
- Routing Protocols
- AAA
- Application Inspection
- Security Contexts
- Transparent Firewalls
- Failover
- QoS
- Summary
IPS Management Using ASDM
- IPS Management Using ASDM
- Accessing the IPS Device Management Console from ASDM
- Configuring Basic AIP-SSM Settings
- Advanced IPS Configuration and Monitoring Using ASDM
- Summary
VPN Management Using ASDM
- VPN Management Using ASDM
- Site-to-Site VPN Setup Using Preshared Keys
- Site-to-Site VPN Setup Using PKI
- Cisco Remote-Access IPSec VPN Setup
- WebVPN
- VPN Monitoring
- Summary
Case Studies
EAN: 2147483647
Pages: 231
- Challenging the Unpredictable: Changeable Order Management Systems
- Context Management of ERP Processes in Virtual Communities
- Distributed Data Warehouse for Geo-spatial Services
- A Hybrid Clustering Technique to Improve Patient Data Quality
- Relevance and Micro-Relevance for the Professional as Determinants of IT-Diffusion and IT-Use in Healthcare
