Case Study 1: Deploying the Cisco ASA at Branch Offices and Small Businesses
Case Study 1 Deploying the Cisco ASA at Branch Offices and Small Businesses
This section demonstrates how Cisco ASA appliances are deployed in SecureMe's branch offices, as well as how a business partner company uses Cisco ASA to provide firewall and site-to-site VPN connectivity to SecureMe.
Branch Offices
SecureMe has several small branch offices around the world. There are 20 to 25 users at each branch office. A Cisco ASA 5510 is deployed at each of the three branch offices (New York, Los Angeles, and Atlanta), as shown in Figure 22-1.
Figure 22-1. Branch Offices

The Cisco ASA 5510 at each location is connected to a Cisco IOS router providing Internet connectivity. The Cisco ASAs are also connected to Cisco Catalyst switches (not shown in Figure 22-1) to provide connectivity to internal users.
SecureMe's security policies restrict all of its branch office users from communicating to the Internet on any port other than TCP port 80 (www) and TCP port 443 (SSL). Its business model requires the following:
- The use of a third-party application that uses TCP ports 8912 and 8913. Client machines from users at remote locations will access this third-party application server over the site-to-site VPN tunnel to SecureMe's regional site in Washington.
- Users access their e-mail (Simple Mail Transfer Protocol [SMTP], Post Office Protocol [POP], and Internet Message Access Protocol [IMAP]) from an e-mail server in Washington over the VPN tunnel.
- DNS is allowed for name resolution.
The IT staff in Washington developed an application to provide the capability to remotely control user workstations at remote branch offices from the Washington regional site network. This application is also used to remotely install software (that is, operating system patches and antivirus updates) and it communicates over TCP port 7788. Figure 22-2 is a diagram of the New York branch office network with all the assigned IP addresses.
Figure 22-2. New York Branch Office Network
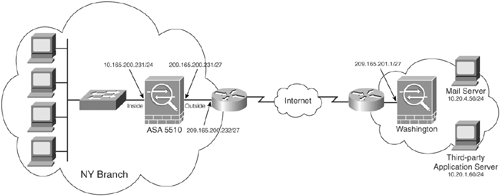
To accommodate the previously listed requirements, the configuration in Example 22-1 is deployed at the New York branch office. This same configuration is deployed on the Cisco ASA at Los Angeles and Atlanta branch offices as well, with the exception of the IP addresses corresponding to each specific location.
Example 22-1. New York Branch Configuration
! The public outside interface interface GigabitEthernet0/0 nameif outside security-level 0 ip address 209.165.200.231 255.255.255.224 ! ! The private inside interface interface GigabitEthernet0/1 nameif inside security-level 100 ip address 10.165.200.231 255.255.255.0 ! ! hostname NewYork ! !The following access control list entries restrict internal users to only be able to !send HTTP, HTTPS, and DNS traffic to the Internet access-list insideACL extended permit tcp 10.165.200.0 255.255.255.0 any eq www access-list insideACL extended permit tcp 10.165.200.0 255.255.255.0 any eq https access-list insideACL extended permit udp 10.165.200.0 255.255.255.0 any eq domain ! !The following access control list entries restrict internal users to only be able to !send TCP port 8912 and 8913 traffic to the 10.20.1.60 server in Washington, which hosts !the previously mentioned third-party application. access-list insideACL extended permit tcp 10.165.200.0 255.255.255.0 host 10.20.1.60 eq 8912 access-list insideACL extended permit tcp 10.165.200.0 255.255.255.0 host 10.20.1.60 eq 8913 ! !The following access control list entries restrict internal users to only be able to !send SMTP, POP3, and IMAP4 traffic to the 10.20.4.50 mail server in Washington. access-list insideACL extended permit tcp 10.165.200.0 255.255.255.0 host 10.20.4.50 eq smtp access-list insideACL extended permit tcp 10.165.200.0 255.255.255.0 host 10.20.4.50 eq pop3 access-list insideACL extended permit tcp 10.165.200.0 255.255.255.0 host 10.20.4.50 eq imap4 ! !The following access control list entry allows the 10.10.220.0/24 management segment in !Washington to be able to launch a remote control session to the internal user workstations !in NY. access-list outsideACL extended permit tcp 10.10.220.0 255.255.255.0 10.165.200.0 255.255.255.0 eq 7788 ! !The following access control list entries are used to define what traffic should be !encrypted over the IPSec site-to-site tunnel to Washington. access-list encryptACL extended permit ip 10.165.200.0 255.255.255.0 10.20.4.0 255.255.255.0 access-list encryptACL extended permit ip 10.165.200.0 255.255.255.0 10.20.1.0 255.255.255.0 access-list encryptACL extended permit ip 10.165.200.0 255.255.255.0 10.10.220.0 255.255.255.0 ! !The following access control list entries allows the ASA to bypass NAT for the IPSec !tunnel traffic. access-list nonat extended permit ip 10.165.200.0 255.255.255.0 10.20.4.0 255.255.255.0 access-list nonat extended permit ip 10.165.200.0 255.255.255.0 10.20.1.0 255.255.255.0 access-list nonat extended permit ip 10.165.200.0 255.255.255.0 10.10.220.0 255.255.255.0 ! !The following NAT configuration allows all the internal devices within the !10.165.200.0/24 network to be port address translated to the outside interface address !except for the VPN traffic. global (outside) 1 interface nat (inside) 0 access-list nonat nat (inside) 1 10.165.200.0 255.255.255.0 ! !Access-lists are applied to the corresponding access-groups access-group insideACL in interface inside access-group outsideACL in interface outside ! ! Default gateway pointing to the external router's IP address route outside 0.0.0.0 0.0.0.0 209.165.200.232 1 ! !The following is the IPSec site-to-site tunnel configuration to the Washington ASA !209.165.201.1. crypto ipsec transform-set myset esp-aes-256 esp-sha-hmac crypto map IPSec_map 10 set peer 209.165.201.1 crypto map IPSec_map 10 set transform-set myset crypto map IPSec_map 10 match address encryptACL crypto map IPSec_map interface outside isakmp enable outside isakmp policy 10 authentication pre-share isakmp policy 10 encryption aes-256 isakmp policy 10 hash sha isakmp policy 10 group 2 isakmp policy 10 lifetime 86400 tunnel-group 209.165.201.1 type ipsec-l2l tunnel-group 209.165.201.1 ipsec-attributes pre-shared-key 1qaz@WSX
Note that the sysopt connection permit-ipsec command is not used in the configuration in Example 22-1. This is purposefully done to ensure that the decrypted VPN traffic passes through the interface ACL applied to the outside interface.
Small Business Partners
Partner-A is a small company that buys supplies from SecureMe on a regular basis. There is a specific ecommerce application that SecureMe and Partner-A use to do all of their business transactions. Partner-A deploys the Cisco ASA 5510 to provide site-to-site extranet VPN services and to secure its infrastructure, as shown in Figure 22-3.
Figure 22-3. Extranet Communication
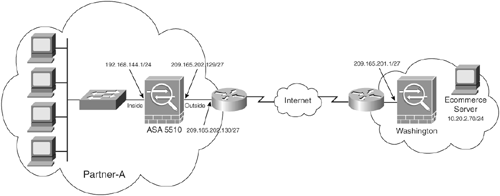
The e-commerce application used by Partner-A to buy its materials is a web-based application over Secure HTTP (HTTPS). SecureMe and Partner-A policies dictate that only TCP port 443 (HTTPS) traffic should be allowed over their site-to-site VPN connection to the e-commerce server in Washington (10.20.2.70). Traffic destined to the rest of 10.x.x.x networks in Washington is not allowed. All other traffic is allowed to leave the security appliance. Example 22-2 shows the configuration for Partner-A's Cisco ASA to achieve this goal.
Example 22-2. Partner-A Configuration
! The public outside interface interface GigabitEthernet0/0 nameif outside security-level 0 ip address 209.165.202.129 255.255.255.224 ! ! The private inside interface interface GigabitEthernet0/1 nameif inside security-level 100 ip address 192.168.144.1 255.255.255.0 ! hostname Partner-A ! Access-list allowing only HTTPS communication to the 10.20.2.70 server and dropping all ! other communication to the 10.0.0.0/8 supersubnet for networks in Washington. access-list Part_in_ACL extended permit tcp 192.168.144.0 255.255.255.0 host 10.20.2.70 eq https access-list Part_in_ACL extended deny ip 192.168.144.0 255.255.255.0 10.0.0.0 255.0.0.0 access-list Part_in_ACL extended permit ip any any ! ! Access-lists to bypass NAT and classify what packets will be encrypted over the tunnel access-list nonat extended permit ip 192.168.144.0 255.255.255.0 host 10.20.2.70 access-list encryptACL extended permit ip 192.168.144.0 255.255.255.0 host 10.20.2.70 ! ! NAT configuration global (outside) 1 interface nat (inside) 0 access-list nonat nat (inside) 1 192.168.144.0 255.255.255.0 ! !Access-list Part_in_ACL applied to inside interface access-group Part_in_ACL in interface inside route outside 0.0.0.0 0.0.0.0 209.165.202.130 1 !IPSec site-to-site configuration crypto ipsec transform-set myset esp-aes-256 esp-sha-hmac crypto map IPSec_map 10 match address encryptACL crypto map IPSec_map 10 set peer 209.165.201.1 crypto map IPSec_map 10 set transform-set myset crypto map IPSec_map interface outside isakmp enable outside isakmp policy 10 authentication pre-share isakmp policy 10 encryption aes-256 isakmp policy 10 hash sha isakmp policy 10 group 2 isakmp policy 10 lifetime 86400 tunnel-group 209.165.201.1 type ipsec-l2l tunnel-group 209.165.201.1 ipsec-attributes pre-shared-key 3edc$RFV
Partner-A has a total of 75 users. Its Network Address Translation (NAT) configuration is designed to allow all of its users to have Port Address Translation (PAT) resolve the address of the ASA's public interface.
The network security administrator at Partner-A receives a call from Partner-A's Chief Information Officer (CIO) mentioning that the security policy has been changed such that ActiveX and Java should be blocked for all of Partner-A's user web traffic to the Internet. The commands shown in Example 22-3 are appended to SecureMe's Cisco ASA configuration to fulfill this requirement.
Example 22-3. Blocking ActiveX and Java
filter activex 80 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 filter java 80 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0
ActiveX and Java are filtered for all sources, and destinations on port 80.
Part I: Product Overview
Introduction to Network Security
- Introduction to Network Security
- Firewall Technologies
- Intrusion Detection and Prevention Technologies
- Network-Based Attacks
- Virtual Private Networks
- Summary
Product History
- Product History
- Cisco Firewall Products
- Cisco IDS Products
- Cisco VPN Products
- Cisco ASA All-in-One Solution
- Summary
Hardware Overview
Part II: Firewall Solution
Initial Setup and System Maintenance
- Initial Setup and System Maintenance
- Accessing the Cisco ASA Appliances
- Managing Licenses
- Initial Setup
- IP Version 6
- Setting Up the System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Network Access Control
- Network Access Control
- Packet Filtering
- Advanced ACL Features
- Content and URL Filtering
- Deployment Scenarios Using ACLs
- Monitoring Network Access Control
- Understanding Address Translation
- DNS Doctoring
- Monitoring Address Translations
- Summary
IP Routing
Authentication, Authorization, and Accounting (AAA)
- Authentication, Authorization, and Accounting (AAA)
- AAA Protocols and Services Supported by Cisco ASA
- Defining an Authentication Server
- Configuring Authentication of Administrative Sessions
- Authenticating Firewall Sessions (Cut-Through Proxy Feature)
- Configuring Authorization
- Configuring Accounting
- Deployment Scenarios
- Troubleshooting AAA
- Summary
Application Inspection
- Application Inspection
- Enabling Application Inspection Using the Modular Policy Framework
- Selective Inspection
- Computer Telephony Interface Quick Buffer Encoding Inspection
- Domain Name System
- Extended Simple Mail Transfer Protocol
- File Transfer Protocol
- General Packet Radio Service Tunneling Protocol
- H.323
- HTTP
- ICMP
- ILS
- MGCP
- NetBIOS
- PPTP
- Sun RPC
- RSH
- RTSP
- SIP
- Skinny
- SNMP
- SQL*Net
- TFTP
- XDMCP
- Deployment Scenarios
- Summary
Security Contexts
- Security Contexts
- Architectural Overview
- Configuration of Security Contexts
- Deployment Scenarios
- Monitoring and Troubleshooting the Security Contexts
- Summary
Transparent Firewalls
- Transparent Firewalls
- Architectural Overview
- Transparent Firewalls and VPNs
- Configuration of Transparent Firewall
- Deployment Scenarios
- Monitoring and Troubleshooting the Transparent Firewall
- Summary
Failover and Redundancy
- Failover and Redundancy
- Architectural Overview
- Failover Configuration
- Deployment Scenarios
- Monitoring and Troubleshooting Failovers
- Summary
Quality of Service
- Quality of Service
- Architectural Overview
- Configuring Quality of Service
- QoS Deployment Scenarios
- Monitoring QoS
- Summary
Part III: Intrusion Prevention System (IPS) Solution
Intrusion Prevention System Integration
- Intrusion Prevention System Integration
- Adaptive Inspection Prevention Security Services Module Overview (AIP-SSM)
- Directing Traffic to the AIP-SSM
- AIP-SSM Module Software Recovery
- Additional IPS Features
- Summary
Configuring and Troubleshooting Cisco IPS Software via CLI
- Configuring and Troubleshooting Cisco IPS Software via CLI
- Cisco IPS Software Architecture
- Introduction to the CIPS 5.x Command-Line Interface
- User Administration
- AIP-SSM Maintenance
- Advanced Features and Configuration
- Summary
Part IV: Virtual Private Network (VPN) Solution
Site-to-Site IPSec VPNs
- Site-to-Site IPSec VPNs
- Preconfiguration Checklist
- Configuration Steps
- Advanced Features
- Optional Commands
- Deployment Scenarios
- Monitoring and Troubleshooting Site-to-Site IPSec VPNs
- Summary
Remote Access VPN
- Remote Access VPN
- Cisco IPSec Remote Access VPN Solution
- Advanced Cisco IPSec VPN Features
- Deployment Scenarios of Cisco IPSec VPN
- Monitoring and Troubleshooting Cisco Remote Access VPN
- Cisco WebVPN Solution
- Advanced WebVPN Features
- Deployment Scenarios of WebVPN
- Monitoring and Troubleshooting WebVPN
- Summary
Public Key Infrastructure (PKI)
- Public Key Infrastructure (PKI)
- Introduction to PKI
- Enrolling the Cisco ASA to a CA Using SCEP
- Manual (Cut-and-Paste) Enrollment
- Configuring CRL Options
- Configuring IPSec Site-to-Site Tunnels Using Certificates
- Configuring the Cisco ASA to Accept Remote-Access VPN Clients Using Certificates
- Troubleshooting PKI
- Summary
Part V: Adaptive Security Device Manager
Introduction to ASDM
- Introduction to ASDM
- Setting Up ASDM
- Initial Setup
- Functional Screens
- Interface Management
- System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Firewall Management Using ASDM
- Firewall Management Using ASDM
- Access Control Lists
- Address Translation
- Routing Protocols
- AAA
- Application Inspection
- Security Contexts
- Transparent Firewalls
- Failover
- QoS
- Summary
IPS Management Using ASDM
- IPS Management Using ASDM
- Accessing the IPS Device Management Console from ASDM
- Configuring Basic AIP-SSM Settings
- Advanced IPS Configuration and Monitoring Using ASDM
- Summary
VPN Management Using ASDM
- VPN Management Using ASDM
- Site-to-Site VPN Setup Using Preshared Keys
- Site-to-Site VPN Setup Using PKI
- Cisco Remote-Access IPSec VPN Setup
- WebVPN
- VPN Monitoring
- Summary
Case Studies
- Case Studies
- Case Study 1: Deploying the Cisco ASA at Branch Offices and Small Businesses
- Case Study 2: Large Enterprise Firewall, VPN, and IPS Deployment
- Summary
EAN: 2147483647
Pages: 231
- The Effects of an Enterprise Resource Planning System (ERP) Implementation on Job Characteristics – A Study using the Hackman and Oldham Job Characteristics Model
- Data Mining for Business Process Reengineering
- Intrinsic and Contextual Data Quality: The Effect of Media and Personal Involvement
- A Hybrid Clustering Technique to Improve Patient Data Quality
- Relevance and Micro-Relevance for the Professional as Determinants of IT-Diffusion and IT-Use in Healthcare
