Firewall Technologies
A detailed understanding of how firewalls and their related technologies work is extremely important for all network security professionals. This knowledge will help them to configure and manage the security of their networks accurately and effectively. The word firewall commonly describes systems or devices that are placed between a trusted and an untrusted network.
Several network firewall solutions offer user and application policy enforcement that provide multivector attack protection for different types of security threats. They often provide logging capabilities that allow the security administrators to identify, investigate, validate, and mitigate such threats.
Additionally, several software applications can run on a system to protect only that host. These types of applications are known as personal firewalls. This section includes an overview of network and personal firewalls and their related technologies.
Network Firewalls
It is important to recognize the value of perimeter security in today's networking world. Network-based firewalls provide key features used for perimeter security. The primary task of a network firewall is to deny or permit traffic that attempts to enter the network based on explicit preconfigured policies and rules. The processes that are used to allow or block traffic may include the following:
- Simple packet-filtering techniques
- Multifaceted application proxies
- Stateful inspection systems
Packet-Filtering Techniques
The purpose of packet filters is simply to control access to specific network segments by defining which traffic can pass through them. They usually inspect incoming traffic at the transport layer of the Open System Interconnection (OSI) model. For example, packet filters can analyze TCP or UDP packets and judge them against a set of predetermined rules called access control lists (ACLs). They inspect the following elements within a packet:
- Source address
- Destination address
- Source port
- Destination port
- Protocol
Note
Packet filters do not commonly inspect additional Layer 3 and Layer 4 fields such as sequence numbers, TCP control flags, and TCP acknowledgement (ACK) field.
Various packet-filtering firewalls can also inspect packet header information to find out if the packet is from a new or an existing connection. Simple packet-filtering firewalls have several limitations and weaknesses:
- Their ACLs or rules can be relatively large and difficult to manage.
- They can be deceived into permitting unauthorized access of spoofed packets. Attackers can orchestrate a packet with an IP address that is authorized by the ACL.
- Numerous applications can build multiple connections on randomly negotiated ports. This makes it difficult to determine which ports will be selected and used until after the connection is completed. Examples of this type of application are several multimedia applications, including RealAudio, QuickTime, and other streaming audio and video applications. Packet filters do not understand the underlying upper-layer protocols used by this type of application, and providing support for this type of application is difficult because the ACLs need to be manually configured in packet-filtering firewalls.
Application Proxies
Application proxies, or proxy servers, are devices that operate as intermediary agents on behalf of clients that are on a private or protected network. Clients on the protected network send connection requests to the application proxy in order to transfer data to the unprotected network or the Internet. Consequently, the application proxy sends the request on behalf of the internal client. The majority of proxy firewalls work at the application layer of the OSI model. Few proxy firewalls have the ability to cache information to accelerate their transactions. This is a great tool for networks that have numerous servers that experience considerably high usage. A disadvantage of application proxies is their inability to scale. This makes them difficult to deploy in large environments.
Network Address Translation
Several Layer 3 devices can provide Network Address Translation (NAT) services. The application proxy translates the internal host's IP addresses to a publicly routable address. NAT is often used by firewalls; however, other devices such as wireless access points provide support for NAT. By using NAT, the firewall exposes its own network address or public address range of an unprotected network. This enables a network professional to use any IP address space as the internal network. A best practice is to use the address spaces that are reserved for private use (see RFC 1918, "Address Allocation for Private Internets"). Table 1-1 lists the private address ranges specified in RFC 1918.
|
Network Address Range |
Network/Mask |
|---|---|
|
10.0.0.010.255.255.255 |
10.0.0.0/8 |
|
172.16.0.0172.31.255.255 |
172.16.0.0/12 |
|
192.168.0.0192.168.255.255 |
192.168.0.0/16 |
It is important to think about the different private address spaces when you plan your network (for example, number of hosts and subnets that can be configured). Careful planning and preparation will lead to substantial time savings if changes are encountered down the road.
Port Address Translation
Normally, application proxies perform a technique called Port Address Translation (PAT). This feature allows many devices on the internal protected network to share one IP address by inspecting the Layer 4 information on the packet. This address is usually the firewall's public address. Figure 1-1 shows how PAT works.
Figure 1-1. PAT Example
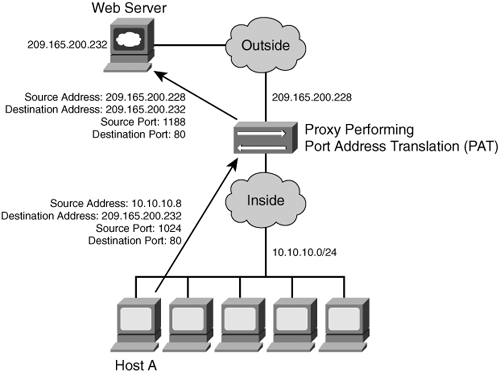
As illustrated in Figure 1-1, several hosts on a protected network labeled "inside" are configured with an address from the network 10.10.10.0 with a 24-bit subnet mask. The application proxy is performing PAT for the internal hosts and translating the 10.10.10.x addresses into its own address (209.165.200.228). In this example, Host A sends a TCP port 80 packet to the web server located in the "outside" unprotected network. The application proxy translates the request from the original 10.10.10.8 IP address of Host A to its own address. It does this by randomly selecting a different Layer 4 source port when forwarding the request to the web server.
Static Translation
A different methodology is used when hosts in the unprotected network need to contact specific hosts behind the NAT device. This is done by creating a static mapping of the public IP address and the address of the internal protected device. For example, static NAT can be configured when a web server has a private IP address but needs to be contacted by hosts located in the unprotected network or the Internet. Figure 1-2 demonstrates how static translation works.
Figure 1-2. Example of Static Translation
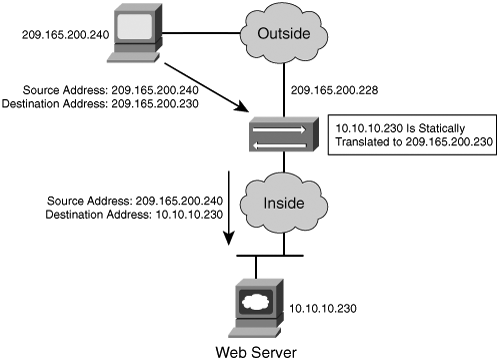
In Figure 1-2, the web server address (10.10.10.230) is statically translated to an address in the outside network (209.165.200.240, in this case). This allows the outside host to initiate a connection to the web server by directing the traffic to 209.165.200.240. The device performing NAT then translates and sends the request to the web server on the inside network.
Address translation is not limited to firewalls. Nowadays, devices from simple small office, home office (SOHO) routers to very sophisticated stateful inspection firewalls are able to perform different types of NAT techniques.
Stateful Inspection Firewalls
Stateful inspection firewalls provide enhanced benefits when compared to the simple packet-filtering firewalls. They track every connection passing through their interfaces by assuring that they are valid connections. They examine not only the packet header contents, but also the application layer information within the payload. This is done to find out more about the transaction than just the source and destination addresses and ports. A stateful firewall monitors the state of the connection and maintains a database with this information. This database is usually called the state table. The state of the connection details whether such connection has been established, closed, reset, or is being negotiated. These mechanisms offer protection for different types of network attacks.
Numerous firewalls have the capability to configure a network (or zone) where you can place devices to allow outside or Internet hosts to access them. These areas or network segments are usually called demilitarized zones (DMZs). These zones provide security to the systems that reside within them, but with a different security level than your network within your inside network. Sophisticated firewall solutions can be configured with several DMZs. Figure 1-3 exemplifies this technique.
Figure 1-3. Firewall DMZ Configurations
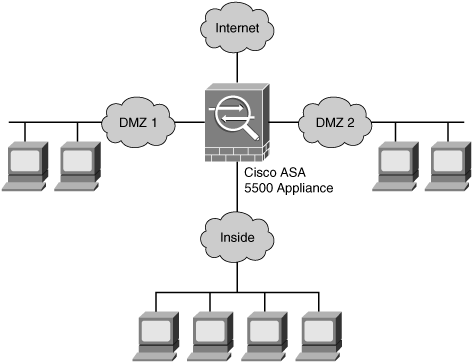
The example in Figure 1-3 shows how a firewall (a Cisco ASA 5500 appliance, in this case) can be deployed and configured to protect several DMZ networks. DMZs minimize the exposure of devices and clients on your external network by allowing only recognized and managed services on those hosts to be accessible by hosts on the Internet.
Personal Firewalls
Personal firewalls use similar methods as network-based firewalls. They provide filtering techniques and stateful inspection of connections directed to the specific host. Conversely, they abridge the operation of the application to meet the needs of a less technically inclined consumer. Personal firewall applications can restrict access to services and applications installed within a single host. This is commonly deployed to telecommuters and remote mobile users. Several personal firewalls generally protect the host from inbound connections and attacks; however, they allow all outbound connections.
There are many differences between personal firewalls and network-based firewalls. One of the major differences is the deployment model and the security services each of them provides.
Part I: Product Overview
Introduction to Network Security
- Introduction to Network Security
- Firewall Technologies
- Intrusion Detection and Prevention Technologies
- Network-Based Attacks
- Virtual Private Networks
- Summary
Product History
- Product History
- Cisco Firewall Products
- Cisco IDS Products
- Cisco VPN Products
- Cisco ASA All-in-One Solution
- Summary
Hardware Overview
Part II: Firewall Solution
Initial Setup and System Maintenance
- Initial Setup and System Maintenance
- Accessing the Cisco ASA Appliances
- Managing Licenses
- Initial Setup
- IP Version 6
- Setting Up the System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Network Access Control
- Network Access Control
- Packet Filtering
- Advanced ACL Features
- Content and URL Filtering
- Deployment Scenarios Using ACLs
- Monitoring Network Access Control
- Understanding Address Translation
- DNS Doctoring
- Monitoring Address Translations
- Summary
IP Routing
Authentication, Authorization, and Accounting (AAA)
- Authentication, Authorization, and Accounting (AAA)
- AAA Protocols and Services Supported by Cisco ASA
- Defining an Authentication Server
- Configuring Authentication of Administrative Sessions
- Authenticating Firewall Sessions (Cut-Through Proxy Feature)
- Configuring Authorization
- Configuring Accounting
- Deployment Scenarios
- Troubleshooting AAA
- Summary
Application Inspection
- Application Inspection
- Enabling Application Inspection Using the Modular Policy Framework
- Selective Inspection
- Computer Telephony Interface Quick Buffer Encoding Inspection
- Domain Name System
- Extended Simple Mail Transfer Protocol
- File Transfer Protocol
- General Packet Radio Service Tunneling Protocol
- H.323
- HTTP
- ICMP
- ILS
- MGCP
- NetBIOS
- PPTP
- Sun RPC
- RSH
- RTSP
- SIP
- Skinny
- SNMP
- SQL*Net
- TFTP
- XDMCP
- Deployment Scenarios
- Summary
Security Contexts
- Security Contexts
- Architectural Overview
- Configuration of Security Contexts
- Deployment Scenarios
- Monitoring and Troubleshooting the Security Contexts
- Summary
Transparent Firewalls
- Transparent Firewalls
- Architectural Overview
- Transparent Firewalls and VPNs
- Configuration of Transparent Firewall
- Deployment Scenarios
- Monitoring and Troubleshooting the Transparent Firewall
- Summary
Failover and Redundancy
- Failover and Redundancy
- Architectural Overview
- Failover Configuration
- Deployment Scenarios
- Monitoring and Troubleshooting Failovers
- Summary
Quality of Service
- Quality of Service
- Architectural Overview
- Configuring Quality of Service
- QoS Deployment Scenarios
- Monitoring QoS
- Summary
Part III: Intrusion Prevention System (IPS) Solution
Intrusion Prevention System Integration
- Intrusion Prevention System Integration
- Adaptive Inspection Prevention Security Services Module Overview (AIP-SSM)
- Directing Traffic to the AIP-SSM
- AIP-SSM Module Software Recovery
- Additional IPS Features
- Summary
Configuring and Troubleshooting Cisco IPS Software via CLI
- Configuring and Troubleshooting Cisco IPS Software via CLI
- Cisco IPS Software Architecture
- Introduction to the CIPS 5.x Command-Line Interface
- User Administration
- AIP-SSM Maintenance
- Advanced Features and Configuration
- Summary
Part IV: Virtual Private Network (VPN) Solution
Site-to-Site IPSec VPNs
- Site-to-Site IPSec VPNs
- Preconfiguration Checklist
- Configuration Steps
- Advanced Features
- Optional Commands
- Deployment Scenarios
- Monitoring and Troubleshooting Site-to-Site IPSec VPNs
- Summary
Remote Access VPN
- Remote Access VPN
- Cisco IPSec Remote Access VPN Solution
- Advanced Cisco IPSec VPN Features
- Deployment Scenarios of Cisco IPSec VPN
- Monitoring and Troubleshooting Cisco Remote Access VPN
- Cisco WebVPN Solution
- Advanced WebVPN Features
- Deployment Scenarios of WebVPN
- Monitoring and Troubleshooting WebVPN
- Summary
Public Key Infrastructure (PKI)
- Public Key Infrastructure (PKI)
- Introduction to PKI
- Enrolling the Cisco ASA to a CA Using SCEP
- Manual (Cut-and-Paste) Enrollment
- Configuring CRL Options
- Configuring IPSec Site-to-Site Tunnels Using Certificates
- Configuring the Cisco ASA to Accept Remote-Access VPN Clients Using Certificates
- Troubleshooting PKI
- Summary
Part V: Adaptive Security Device Manager
Introduction to ASDM
- Introduction to ASDM
- Setting Up ASDM
- Initial Setup
- Functional Screens
- Interface Management
- System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Firewall Management Using ASDM
- Firewall Management Using ASDM
- Access Control Lists
- Address Translation
- Routing Protocols
- AAA
- Application Inspection
- Security Contexts
- Transparent Firewalls
- Failover
- QoS
- Summary
IPS Management Using ASDM
- IPS Management Using ASDM
- Accessing the IPS Device Management Console from ASDM
- Configuring Basic AIP-SSM Settings
- Advanced IPS Configuration and Monitoring Using ASDM
- Summary
VPN Management Using ASDM
- VPN Management Using ASDM
- Site-to-Site VPN Setup Using Preshared Keys
- Site-to-Site VPN Setup Using PKI
- Cisco Remote-Access IPSec VPN Setup
- WebVPN
- VPN Monitoring
- Summary
Case Studies
EAN: 2147483647
Pages: 231
