Access Control Lists
As discussed in Chapter 5, "Network Access Control," you can use access control lists (ACLs) to filter traffic passing through Cisco ASA. You can set up a traffic-filtering ACL under Configuration > Features > Security Policy > Access Rules. Click Add to create a new ACL. Figure 19-1 shows a new access control entry (ACE) added into ASDM to block web traffic coming in from the outside host located at 209.165.201.1 to an inside web server located at 209.165.202.131. This ACE is a part of an ACL, which is automatically created by ASDM and applied to the interface. ASDM provides a nice Rule Flow Diagram section to illustrate how the ACL policy will be applied to the traffic. The source or destination host/network addresses may be IP addresses, an interface name, or an object group. You may also enter a description at the bottom of the screen to label the purpose of this entry.
Figure 19-1. Setting Up an ACE
Note
An ACE is referred to as an access rule in the ASDM interface.
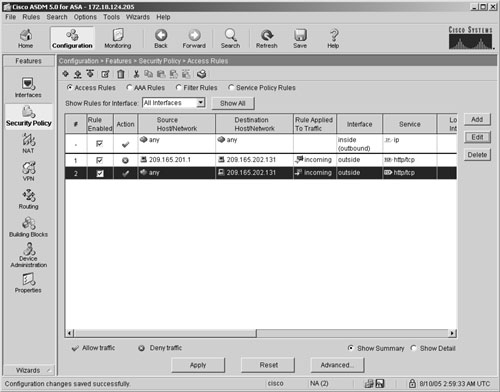
Figure 19-2 illustrates the complete ACL with two ACEs.
Figure 19-2. Displaying the Entire ACL
The first entry denies the traffic originating from the host located at 209.165.201.1. The second entry allows web traffic to pass through Cisco ASA if it is either of the following:
- Sourced from any IP address, except the one that is blocked.
- Destined for the IP address of the web server.
Example 19-1 shows the corresponding ACL generated by ASDM. The ACL name is outside_access_in and it is applied to the outside interface in the inbound direction.
Example 19-1. ACL Generated by ASDM
access-list outside_access_in remark ACE to block web-traffic destined to 209.165.202.131 from 209.165.201.1 access-list outside_access_in extended deny tcp host 209.165.201.1 host 209.165.202.131 eq www access-list outside_access_in extended permit tcp any host 209.165.202.131 eq www access-group outside_access_in in interface outside
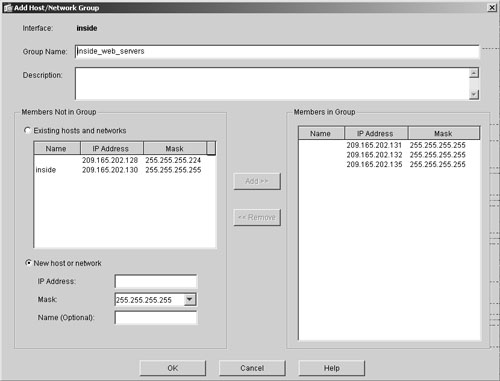
The use of object groups can simplify both the CLI and GUI configuration if numerous hosts need to be filtered using similar properties. For network-based object groups, Cisco ASA needs to know where a host or a network exists. To accomplish this, navigate to Configuration > Features > Building Blocks > Host/Networks and then click Add under Hosts/Networks Groups. You can enter the IP addresses of the hosts either by clicking Existing Hosts and Networks and adding them from the list or by clicking New Host or Network, typing the new address, and then adding it with the Add button, as shown in Figure 19-3. The existing hosts are the previously added hosts in the ASDM list. The administrator has named this object group inside_web_servers and has grouped three inside IP addresses in the list.
Figure 19-3. Defining an Object Group in ASDM
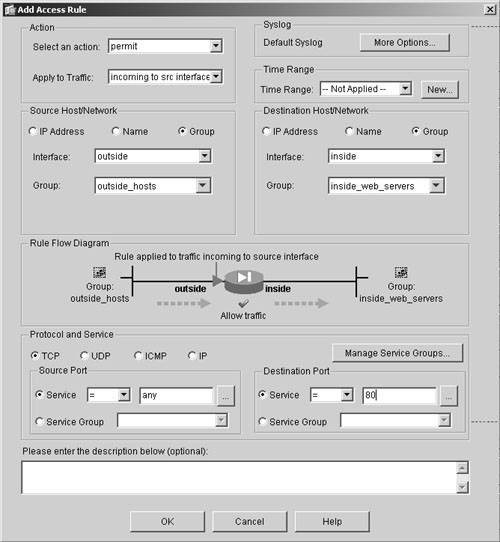
After defining the object groups, you can map an ACE, as shown in Figure 19-4. The traffic from the outside hosts defined in the outside_hosts network group is allowed to pass through Cisco ASA to the hosts on the inside network that are identified in the inside_web_servers group on TCP port 80.
Figure 19-4. Mapping an Object Group in ASDM
Example 19-2 shows the configuration generated by ASDM when using object groups.
Example 19-2. ACL with Object Groups Generated by ASDM
object-group network inside_web_servers network-object 209.165.202.131 255.255.255.255 network-object 209.165.202.132 255.255.255.255 network-object 209.165.202.135 255.255.255.255 object-group network outside_hosts network-object 209.165.201.1 255.255.255.255 network-object 209.165.201.2 255.255.255.255 network-object 209.165.201.10 255.255.255.255 access-list outside_access_in line 1 extended permit tcp object-group outside_hosts object-group inside_web_servers eq 80 access-group outside_access_in in interface outside
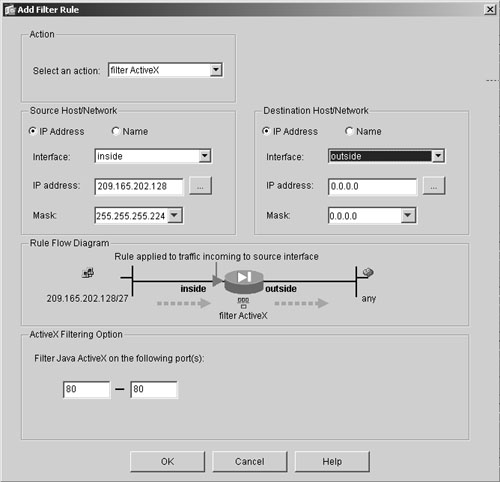
Using ASDM, you can configure a security Cisco ASA to filter ActiveX and Java applets from the traffic passing through it. To set this up, choose Configuration > Features > Security Policy > Filter Rules, which results in the window shown in Figure 19-5. Here, Cisco ASA is being set up to filter ActiveX code from the web requests that originated from the inside network 209.165.202.128/27 and are destined for any address on the outside network.
Figure 19-5. Content Filtering
Part I: Product Overview
Introduction to Network Security
- Introduction to Network Security
- Firewall Technologies
- Intrusion Detection and Prevention Technologies
- Network-Based Attacks
- Virtual Private Networks
- Summary
Product History
- Product History
- Cisco Firewall Products
- Cisco IDS Products
- Cisco VPN Products
- Cisco ASA All-in-One Solution
- Summary
Hardware Overview
Part II: Firewall Solution
Initial Setup and System Maintenance
- Initial Setup and System Maintenance
- Accessing the Cisco ASA Appliances
- Managing Licenses
- Initial Setup
- IP Version 6
- Setting Up the System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Network Access Control
- Network Access Control
- Packet Filtering
- Advanced ACL Features
- Content and URL Filtering
- Deployment Scenarios Using ACLs
- Monitoring Network Access Control
- Understanding Address Translation
- DNS Doctoring
- Monitoring Address Translations
- Summary
IP Routing
Authentication, Authorization, and Accounting (AAA)
- Authentication, Authorization, and Accounting (AAA)
- AAA Protocols and Services Supported by Cisco ASA
- Defining an Authentication Server
- Configuring Authentication of Administrative Sessions
- Authenticating Firewall Sessions (Cut-Through Proxy Feature)
- Configuring Authorization
- Configuring Accounting
- Deployment Scenarios
- Troubleshooting AAA
- Summary
Application Inspection
- Application Inspection
- Enabling Application Inspection Using the Modular Policy Framework
- Selective Inspection
- Computer Telephony Interface Quick Buffer Encoding Inspection
- Domain Name System
- Extended Simple Mail Transfer Protocol
- File Transfer Protocol
- General Packet Radio Service Tunneling Protocol
- H.323
- HTTP
- ICMP
- ILS
- MGCP
- NetBIOS
- PPTP
- Sun RPC
- RSH
- RTSP
- SIP
- Skinny
- SNMP
- SQL*Net
- TFTP
- XDMCP
- Deployment Scenarios
- Summary
Security Contexts
- Security Contexts
- Architectural Overview
- Configuration of Security Contexts
- Deployment Scenarios
- Monitoring and Troubleshooting the Security Contexts
- Summary
Transparent Firewalls
- Transparent Firewalls
- Architectural Overview
- Transparent Firewalls and VPNs
- Configuration of Transparent Firewall
- Deployment Scenarios
- Monitoring and Troubleshooting the Transparent Firewall
- Summary
Failover and Redundancy
- Failover and Redundancy
- Architectural Overview
- Failover Configuration
- Deployment Scenarios
- Monitoring and Troubleshooting Failovers
- Summary
Quality of Service
- Quality of Service
- Architectural Overview
- Configuring Quality of Service
- QoS Deployment Scenarios
- Monitoring QoS
- Summary
Part III: Intrusion Prevention System (IPS) Solution
Intrusion Prevention System Integration
- Intrusion Prevention System Integration
- Adaptive Inspection Prevention Security Services Module Overview (AIP-SSM)
- Directing Traffic to the AIP-SSM
- AIP-SSM Module Software Recovery
- Additional IPS Features
- Summary
Configuring and Troubleshooting Cisco IPS Software via CLI
- Configuring and Troubleshooting Cisco IPS Software via CLI
- Cisco IPS Software Architecture
- Introduction to the CIPS 5.x Command-Line Interface
- User Administration
- AIP-SSM Maintenance
- Advanced Features and Configuration
- Summary
Part IV: Virtual Private Network (VPN) Solution
Site-to-Site IPSec VPNs
- Site-to-Site IPSec VPNs
- Preconfiguration Checklist
- Configuration Steps
- Advanced Features
- Optional Commands
- Deployment Scenarios
- Monitoring and Troubleshooting Site-to-Site IPSec VPNs
- Summary
Remote Access VPN
- Remote Access VPN
- Cisco IPSec Remote Access VPN Solution
- Advanced Cisco IPSec VPN Features
- Deployment Scenarios of Cisco IPSec VPN
- Monitoring and Troubleshooting Cisco Remote Access VPN
- Cisco WebVPN Solution
- Advanced WebVPN Features
- Deployment Scenarios of WebVPN
- Monitoring and Troubleshooting WebVPN
- Summary
Public Key Infrastructure (PKI)
- Public Key Infrastructure (PKI)
- Introduction to PKI
- Enrolling the Cisco ASA to a CA Using SCEP
- Manual (Cut-and-Paste) Enrollment
- Configuring CRL Options
- Configuring IPSec Site-to-Site Tunnels Using Certificates
- Configuring the Cisco ASA to Accept Remote-Access VPN Clients Using Certificates
- Troubleshooting PKI
- Summary
Part V: Adaptive Security Device Manager
Introduction to ASDM
- Introduction to ASDM
- Setting Up ASDM
- Initial Setup
- Functional Screens
- Interface Management
- System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Firewall Management Using ASDM
- Firewall Management Using ASDM
- Access Control Lists
- Address Translation
- Routing Protocols
- AAA
- Application Inspection
- Security Contexts
- Transparent Firewalls
- Failover
- QoS
- Summary
IPS Management Using ASDM
- IPS Management Using ASDM
- Accessing the IPS Device Management Console from ASDM
- Configuring Basic AIP-SSM Settings
- Advanced IPS Configuration and Monitoring Using ASDM
- Summary
VPN Management Using ASDM
- VPN Management Using ASDM
- Site-to-Site VPN Setup Using Preshared Keys
- Site-to-Site VPN Setup Using PKI
- Cisco Remote-Access IPSec VPN Setup
- WebVPN
- VPN Monitoring
- Summary
Case Studies
EAN: 2147483647
Pages: 231
