Failover Configuration
Deployment Scenarios
The failover feature is useful in deployments where redundancy is required to ensure near 100-percent uptime of the network devices. Although the failover feature can be deployed in many ways, we will cover only two design scenarios for ease of understanding:
- Active/Standby failover in single mode
- Active/Active failover in multiple security contexts
Note
The design scenarios discussed in this section should be used solely to reinforce learning. They should be used only for reference purposes.
Active/Standby Failover in Single Mode
In the first deployment scenario, SecureMe, Inc. is looking to implement failover at its Chicago location. It has purchased two Cisco ASA 5540 Cisco ASA for this purpose. The company requires implementation of the stateful failover feature to ensure that all the active connections (excluding the HTTP connections) are replicated to the standby unit in case there is a failure on the primary unit. Additionally, SecureMe requires the standby Cisco ASA to become active if the primary Cisco ASA does not acknowledge the keepalive packets for 3 seconds. Figure 11-4 illustrates a proposed design for Active/Standby failover.
Figure 11-4. Deployment Scenario Using Active/Standby Failover
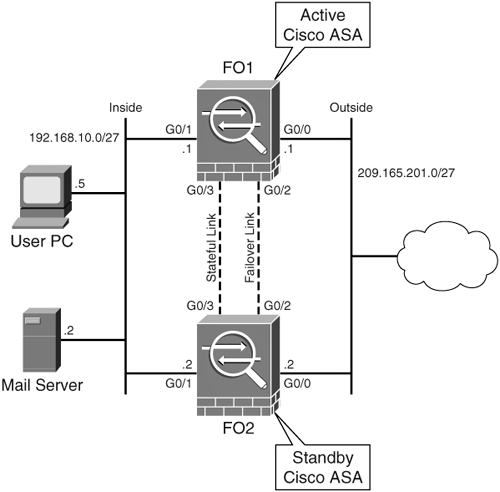
Example 11-29 shows relevant configuration of the primary Cisco ASA and the bootstrap configuration of the secondary Cisco ASA. The primary Cisco ASA, being the active unit, synchronizes the entire running configuration to the secondary Cisco ASA. The connection and translation tables are constantly replicated to the secondary Cisco ASA over a dedicated interface.
Example 11-29. Cisco ASA Full Configuration Using Active/Standby Failover
Configuration of Primary Cisco ASA Chicago# show run !outside interface with security level set to 0. The system IP address is ! 209.165.200.225 and the Standby IP address is 209.165.200.226 interface GigabitEthernet0/0 nameif outside security-level 0 ip address 209.165.200.225 255.255.255.224 standby 209.165.200.226 !inside interface with security level set to 100. The system IP address is ! 192.168.10.1 and the Standby IP address is 192.168.10.2 interface GigabitEthernet0/1 nameif inside security-level 100 ip address 192.168.10.1 255.255.255.0 standby 192.168.10.2 ! Interface used as a failover control interface interface GigabitEthernet0/2 description LAN Failover Interface ! Interface used as a Stateful link interface GigabitEthernet0/3 description STATE Failover Interface ! Failover is enabled and the unit is acting as a Primary device failover failover lan unit primary ! Failover control interface is GigabitEthernet0/2 failover lan interface FOCtrlIntf GigabitEthernet0/2 ! Cisco ASA will send periodic hellos every 500 milliseconds, and initiate a ! failover if hellos are not acknowledged for 3 seconds failover polltime unit msec 500 holdtime 3 ! Failover key to encrypt the control messages. This keys will be X'ed out ! in the configuration failover key cisco123 ! Stateful interface failover link statefullink GigabitEthernet0/3 ! IP address assignment on the failover control interface failover interface ip FOCtrlIntf 10.10.10.1 255.255.255.252 standby 10.10.10.2 ! IP address assignment on the stateful failover interface failover interface ip statefullink 10.10.10.5 255.255.255.252 standby 10.10.10.6 ! interfaces to be monitored for failover monitor-interface outside monitor-interface inside ! Address translation for the inside hosts to get Internet Access global (outside) 1 interface nat (inside) 1 192.168.10.0 255.255.255.0 ______________________________________________________________________________ Configuration of Secondary Cisco ASA ! The unit is acting as a Secondary device failover lan unit secondary ! Failover control interface is GigabitEthernet0/2 failover lan interface FOCtrlIntf GigabitEthernet0/2 ! Failover key to encrypt the control messages. This keys will be X'ed out in the configuration failover key cisco123 ! IP address assignment on the failover control interface failover interface ip FOCtrlIntf 10.10.10.1 255.255.255.252 standby 10.10.10.2 ! Failover is enabled failover
Active/Active Failover in Multiple Security Contexts
SecureMe's London office is currently using a Cisco ASA 5520 Cisco ASA as the security device. SecureUs, another firm in the same building, wants SecureMe to provide the firewall services for it as well. SecureMe's management is looking to implement an Active/Active failover solution where it can create two customer contextsone for SecureMe and the other for SecureUs. It has purchased another Cisco ASA 5520 Cisco ASA to implement this solution. This requires one Cisco ASA to act as an active unit for SecureMe and the other Cisco ASA to act as an active unit for SecureUs while backing up each other in the event of a failure. Figure 11-5 illustrates a proposed design to meet these requirements.
Figure 11-5. Deployment Scenario Using Active/Active Failover
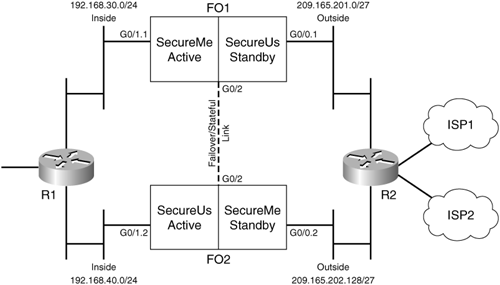
Example 11-30 shows relevant configuration of the primary Cisco ASA and the bootstrap configuration of the secondary Cisco ASA. The primary Cisco ASA synchronizes the entire running configuration to the secondary Cisco ASA. Once both Cisco ASA are active and passing traffic, the administrator also wants these devices to send connection and translation table updates to one another using the failover control interface. The administrator has implemented the asymmetric routing feature to avoid routing issues if packets arrive on the other active Cisco ASA.
Example 11-30. Cisco ASA Configuration Using Active/Active Failover in Multiple Security Contexts
Configuration of Primary Cisco ASA System Execution Space ! Main GigabitEthernet0/0 interface interface GigabitEthernet0/0 ! Sub-interface assigned to the SecureMe context as the ! outside interface. A VLAN ID is assigned to the interface interface GigabitEthernet0/0.1 vlan 5 ! Sub-interface assigned to the SecureUs context as the ! outside interface. A VLAN ID is assigned to the interface interface GigabitEthernet0/0.2 vlan 10 ! Main GigabitEthernet0/1 interface interface GigabitEthernet0/1 ! Sub-interface assigned to the SecureMe context as the ! inside interface. A VLAN ID is assigned to the interface interface GigabitEthernet0/1.1 vlan 105 ! Sub-interface assigned to the SecureUs context as the ! inside interface. A VLAN ID is assigned to the interface interface GigabitEthernet0/1.2 vlan 110 ! Interface used as a Failover control and Stateful link interface GigabitEthernet0/2 description LAN/STATE Failover Interface ! Failover is enabled and the unit is acting as a Primary device failover failover lan unit primary ! Failover control interface is GigabitEthernet0/2 failover lan interface FOCtrlIntf GigabitEthernet0/2 ! Failover key to encrypt the control messages failover key cisco123 ! IP address assignment on the failover control interface failover interface ip FOCtrlIntf 10.10.10.1 255.255.255.252 standby 10.10.10.2 ! Failover link interface is GigabitEthernet0/2 failover link FOCtrlIntf GigabitEthernet0/2 ! Failover group configuration. Group 1 is primary and group 2 is secondary failover group 1 preempt 10 polltime interface 10 ! A virtual MAC address is defined for this group mac address Ethernet0 0000.1111.2222 0000.1111.2223 failover group 2 secondary preempt ! A virtual MAC address is defined for this group mac address Ethernet0 0000.2222.3333 0000.2222.3334 ! Context Assignment with the failover group ID admin-context SecureMe context SecureMe allocate-interface GigabitEthernet0/0.1 A_outside invisible allocate-interface GigabitEthernet0/1.1 A_inside invisible config-url disk0:/SecureMe.cfg join-failover-group 1 ! Context Assignment with the failover group ID context SecureUs allocate-interface GigabitEthernet0/0.2 B_outside invisible allocate-interface GigabitEthernet0/1.2 B_inside invisible config-url disk0:/SecureUs.cfg join-failover-group 2 _________________________________________________________________________________ Configuration of Primary Cisco ASA's SecureMe Context !outside interface with security level set to 0. The system IP address is !209.165.201.1 and the Standby IP address is 209.165.201.2. The asr-group ID is 1 interface A_outside nameif outside security-level 0 ip address 209.165.201.1 255.255.255.224 standby 209.165.201.2 asr-group 1 !inside interface with security level set to 0. The system IP address is !192.168.30.1 and the Standby IP address is 192.168.30.2. The asr-group ID is 1 interface A_inside nameif inside security-level 100 ip address 192.168.30.1 255.255.255.0 standby 192.168.30.2 ! interfaces to be monitored for failover monitor-interface A_outside monitor-interface A_inside ! Address translation Policies global (A_outside) 1 209.165.201.3 netmask 255.255.255.224 nat (A_inside) 1 192.168.30.0 255.255.255.0 route A_outside 0.0.0.0 0.0.0.0 209.165.201.30 _______________________________________________________________________________ Configuration of Primary Cisco ASA's SecureUs Context !outside interface with security level set to 0. The system and standby IPs !are 209.165.202.129 and 209.165.202.130 respectively. The asr-group ID is 1 interface B_outside nameif outside security-level 0 ip address 209.165.202.129 255.255.255.224 standby 209.165.202.130 asr-group 1 !inside interface with security level set to 0. The system and standby IPs are !192.168.40.1 and 192.168.40.2 respectively. interface B_inside nameif inside security-level 100 ip address 192.168.40.1 255.255.255.0 standby 192.168.40.2 ! interfaces to be monitored for failover monitor-interface B_inside monitor-interface B_outside ! Address translation Policies global (B_outside) 1 209.165.202.131 netmask 255.255.255.0 nat (B_inside) 1 192.168.40.0 255.255.255.0 route B_outside 0.0.0.0 0.0.0.0 209.165.202.158
Part I: Product Overview
Introduction to Network Security
- Introduction to Network Security
- Firewall Technologies
- Intrusion Detection and Prevention Technologies
- Network-Based Attacks
- Virtual Private Networks
- Summary
Product History
- Product History
- Cisco Firewall Products
- Cisco IDS Products
- Cisco VPN Products
- Cisco ASA All-in-One Solution
- Summary
Hardware Overview
Part II: Firewall Solution
Initial Setup and System Maintenance
- Initial Setup and System Maintenance
- Accessing the Cisco ASA Appliances
- Managing Licenses
- Initial Setup
- IP Version 6
- Setting Up the System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Network Access Control
- Network Access Control
- Packet Filtering
- Advanced ACL Features
- Content and URL Filtering
- Deployment Scenarios Using ACLs
- Monitoring Network Access Control
- Understanding Address Translation
- DNS Doctoring
- Monitoring Address Translations
- Summary
IP Routing
Authentication, Authorization, and Accounting (AAA)
- Authentication, Authorization, and Accounting (AAA)
- AAA Protocols and Services Supported by Cisco ASA
- Defining an Authentication Server
- Configuring Authentication of Administrative Sessions
- Authenticating Firewall Sessions (Cut-Through Proxy Feature)
- Configuring Authorization
- Configuring Accounting
- Deployment Scenarios
- Troubleshooting AAA
- Summary
Application Inspection
- Application Inspection
- Enabling Application Inspection Using the Modular Policy Framework
- Selective Inspection
- Computer Telephony Interface Quick Buffer Encoding Inspection
- Domain Name System
- Extended Simple Mail Transfer Protocol
- File Transfer Protocol
- General Packet Radio Service Tunneling Protocol
- H.323
- HTTP
- ICMP
- ILS
- MGCP
- NetBIOS
- PPTP
- Sun RPC
- RSH
- RTSP
- SIP
- Skinny
- SNMP
- SQL*Net
- TFTP
- XDMCP
- Deployment Scenarios
- Summary
Security Contexts
- Security Contexts
- Architectural Overview
- Configuration of Security Contexts
- Deployment Scenarios
- Monitoring and Troubleshooting the Security Contexts
- Summary
Transparent Firewalls
- Transparent Firewalls
- Architectural Overview
- Transparent Firewalls and VPNs
- Configuration of Transparent Firewall
- Deployment Scenarios
- Monitoring and Troubleshooting the Transparent Firewall
- Summary
Failover and Redundancy
- Failover and Redundancy
- Architectural Overview
- Failover Configuration
- Deployment Scenarios
- Monitoring and Troubleshooting Failovers
- Summary
Quality of Service
- Quality of Service
- Architectural Overview
- Configuring Quality of Service
- QoS Deployment Scenarios
- Monitoring QoS
- Summary
Part III: Intrusion Prevention System (IPS) Solution
Intrusion Prevention System Integration
- Intrusion Prevention System Integration
- Adaptive Inspection Prevention Security Services Module Overview (AIP-SSM)
- Directing Traffic to the AIP-SSM
- AIP-SSM Module Software Recovery
- Additional IPS Features
- Summary
Configuring and Troubleshooting Cisco IPS Software via CLI
- Configuring and Troubleshooting Cisco IPS Software via CLI
- Cisco IPS Software Architecture
- Introduction to the CIPS 5.x Command-Line Interface
- User Administration
- AIP-SSM Maintenance
- Advanced Features and Configuration
- Summary
Part IV: Virtual Private Network (VPN) Solution
Site-to-Site IPSec VPNs
- Site-to-Site IPSec VPNs
- Preconfiguration Checklist
- Configuration Steps
- Advanced Features
- Optional Commands
- Deployment Scenarios
- Monitoring and Troubleshooting Site-to-Site IPSec VPNs
- Summary
Remote Access VPN
- Remote Access VPN
- Cisco IPSec Remote Access VPN Solution
- Advanced Cisco IPSec VPN Features
- Deployment Scenarios of Cisco IPSec VPN
- Monitoring and Troubleshooting Cisco Remote Access VPN
- Cisco WebVPN Solution
- Advanced WebVPN Features
- Deployment Scenarios of WebVPN
- Monitoring and Troubleshooting WebVPN
- Summary
Public Key Infrastructure (PKI)
- Public Key Infrastructure (PKI)
- Introduction to PKI
- Enrolling the Cisco ASA to a CA Using SCEP
- Manual (Cut-and-Paste) Enrollment
- Configuring CRL Options
- Configuring IPSec Site-to-Site Tunnels Using Certificates
- Configuring the Cisco ASA to Accept Remote-Access VPN Clients Using Certificates
- Troubleshooting PKI
- Summary
Part V: Adaptive Security Device Manager
Introduction to ASDM
- Introduction to ASDM
- Setting Up ASDM
- Initial Setup
- Functional Screens
- Interface Management
- System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Firewall Management Using ASDM
- Firewall Management Using ASDM
- Access Control Lists
- Address Translation
- Routing Protocols
- AAA
- Application Inspection
- Security Contexts
- Transparent Firewalls
- Failover
- QoS
- Summary
IPS Management Using ASDM
- IPS Management Using ASDM
- Accessing the IPS Device Management Console from ASDM
- Configuring Basic AIP-SSM Settings
- Advanced IPS Configuration and Monitoring Using ASDM
- Summary
VPN Management Using ASDM
- VPN Management Using ASDM
- Site-to-Site VPN Setup Using Preshared Keys
- Site-to-Site VPN Setup Using PKI
- Cisco Remote-Access IPSec VPN Setup
- WebVPN
- VPN Monitoring
- Summary
Case Studies
EAN: 2147483647
Pages: 231
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter XI User Satisfaction with Web Portals: An Empirical Study
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment
- Chapter XVI Turning Web Surfers into Loyal Customers: Cognitive Lock-In Through Interface Design and Web Site Usability
- Chapter XVII Internet Markets and E-Loyalty
