Adaptive Inspection Prevention Security Services Module Overview (AIP-SSM)
Cisco ASA supports the Adaptive Inspection Prevention Security Service Module (AIP-SSM) running Cisco Intrusion Prevention System (CIPS) software version 5.0 or later. One of the major features of CIPS 5.x is its ability to process and analyze traffic inline. This qualifies Cisco ASA to be classified as an IPS. The system image file is similar to the ones that run on the Cisco IPS 4200 Series sensors, Cisco IDS Services Module-2 (IDSM-2) for Cisco Catalyst 6500, and Cisco IDS Network Module for Cisco IOS routers.
Cisco ASA also provides basic IPS support if an AIP-SSM module is not present. This capability is achieved with the cuse of the IP audit feature, which is the traditional IP audit feature supported by the Cisco Secure PIX Firewall. The IP audit feature supports a basic list of signatures. It allows the appliance to perform one or more actions on traffic that matches such signatures. This feature is discussed later in the chapter, in the section "IP Audit."
Two different AIP-SSM modules exist:
- AIP-SSM-10
- AIP-SSM-20
Note
Cisco ASA 5510 supports the AIP-SSM-10 only. Cisco ASA 5520 support both the AIP- SSM10 and AIP-SSM-20. The Cisco ASA 5540 supports the AIP-SSM-20.
The AIP-SSM is a diskless (Flash-based) module. The CIPS software runs in the Flash of the module to provide more flexibility and reliability. The module includes an Fast Ethernet port designed for out-of-band management. Figure 13-1 illustrates the front of the AIP-SSM module.
Figure 13-1. AIP-SSM Module Front View
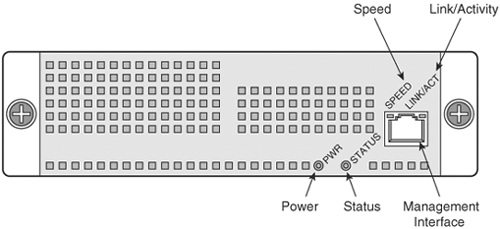
The AIP-SSM has four LED indicators that are visible to the end user. Table 13-1 describes the function of each indicator.
|
LED Indicator |
Color |
Description |
|---|---|---|
|
Power |
Green |
Indicates that the AIP-SSM card is on. |
|
Status |
Green/yellow |
Green indicates that software-driven tests have passed and the card is operational. Yellow indicates that the unit is under test or indicates the proper time to remove the AIP-SSM from the ASA chassis. |
|
Link/Activity |
Green |
Indicates 10/100/1000 Ethernet link and activity. |
|
Speed |
Green/orange |
Green indicates that it is operating at 100 Mbps. Orange indicates that it is operating at 1000 Mbps. |
AIP-SSM Management
The AIP-SSM can be managed from the management interface port, which is illustrated in Figure 13-1, by using Telnet, SSH, or Cisco Adaptive Security Device Manager (ASDM). It can also be managed from the ASA's backplane by using the session command:
session module-number
where module-number is the slot number in the Cisco ASA. Because there is only one available slot, the module number is always 1. Example 13-1 demonstrates how to open a command session to the AIP-SSM module. The AIP-SSM module prompts the user for authentication credentials.
Example 13-1. session Command
Chicago# session 1 Opening command session with slot 1. Connected to slot 1. Escape character sequence is 'CTRL-^X'. login: cisco Password:
Once the user session is connected to the AIP-SSM, the configuration steps are the same as for any other system running CIPS 5.x or later software.
Note
Chapter 14, "Configuring and Troubleshooting Cisco IPS Software via CLI," covers CIPS software configuration.
To view the module statistics, use the show module command from the ASA CLI, as demonstrated in Example 13-2.
Example 13-2. Output of show module Command
Chicago# show module Mod Card Type Model Serial No. --- -------------------------------------------- ------------------ ----------- 0 ASA 5540 Adaptive Security Appliance ASA5540 P0000000227 1 ASA 5500 Series Security Services Module-20 ASA-SSM-20 01234567890 Mod MAC Address Range Hw Version Fw Version Sw Version --- --------------------------------- ------------ ------------ --------------- 0 000b.fcf8.c6d2 to 000b.fcf8.c6d6 1.0 1.0(6)5 7.0(1) 1 000b.fcf8.012c to 000b.fcf8.012c 1.0 1.0(7)2 5.0(2)S152.0 Mod Status --- ------------------ 0 Up Sys 1 Up
The first highlighted line shows the card type. In this case, the Chicago ASA 5540 is running an AIP-SSM-20 with serial number 01234567890. The second highlighted line shows the MAC address of the card and the software version it is running. The third highlighted line shows the status of the module, Up, meaning it is operational.
Inline Versus Promiscuous Mode
Cisco ASA supports both inline and promiscuous IPS modes. When configured as an inline IPS, the AIP-SSM module can drop malicious packets, generate alarms, or reset a connection, allowing the ASA to respond immediately to security threats and protect the network. Inline IPS configuration forces all traffic to be directed to the AIP-SSM. The ASA will not forward any traffic out to the network without the AIP-SSM first inspecting it.
Figure 13-2 shows the traffic flow when the Cisco ASA is configured in inline IPS mode.
Figure 13-2. Inline IPS Traffic Flow
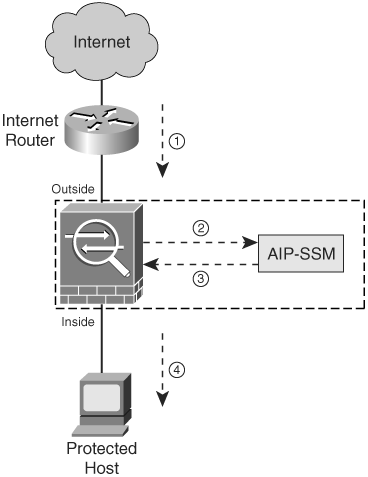
The following is the sequence of events illustrated in Figure 13-2:
- The Cisco ASA receives an IP packet from the Internet.
- Because the Cisco ASA is configured in inline IPS mode, it forwards the packet to the AIP-SSM for analysis.
- The AIP-SSM analyzes the packet and, if it determines that the packet is not malicious, forwards the packet back to the Cisco ASA.
- The Cisco ASA forwards the packet to its final destination (the protected host).
Note
Inline IPS mode is the most secure configuration because every packet is inspected by the AIP-SSM; however, this may affect the overall throughput. The impact depends on the type of attack, signatures enabled on the system, and amount of traffic passing through the appliance.
When the Cisco ASA is set up to use the AIP-SSM in promiscuous mode, the ASA sends a duplicate stream of traffic to the AIP-SSM. This mode has less impact on the overall throughput. Promiscuous mode is considered to be less secure than inline mode because the IPS module can only block traffic by forcing the ASA to shun the malicious traffic or sending a TCP-RST (reset) message to terminate a TCP connection.
Note
Promiscuous mode has less impact on performance because the AIP-SSM is not in the traffic path. A copy of the packet is sent to the AIP-SSM. If a packet is dropped, there is no effect on the ASA.
Figure 13-3 illustrates an example of how traffic flows when the AIP-SSM is configured in promiscuous mode.
Figure 13-3. Promiscuous Mode Traffic Flow
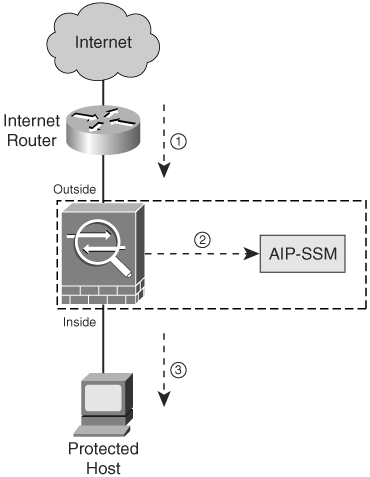
The following is the sequence of events illustrated in Figure 13-3:
- The Cisco ASA receives an IP packet from the Internet.
- Because the Cisco ASA is configured in promiscuous IPS mode, the AIP-SSM silently snoops the packet.
- The ASA forwards the packet to its final destination (protected host) if the packet conforms to security policies (i.e., it does not match any of the configured signatures).
Note
If the ASA firewall policies deny any inbound packet at the interface, the packet will not be inspected by the AIP-SSM. This applies to both inline and promiscuous IPS modes.
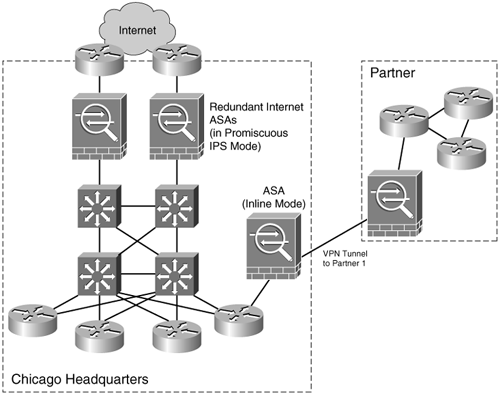
In the example illustrated in Figure 13-4, SecureMe's Chicago headquarters has two redundant Cisco ASAs as Internet firewalls configured in promiscuous IPS mode. It also has an ASA configured with a site-to-site IPSec tunnel to a partner company. In this case, the ASA is configured in inline IPS mode. The traffic that this ASA inspects depends on SecureMe's security policy's site-to-site VPNs.
Figure 13-4. SecureMe IPS Example
Part I: Product Overview
Introduction to Network Security
- Introduction to Network Security
- Firewall Technologies
- Intrusion Detection and Prevention Technologies
- Network-Based Attacks
- Virtual Private Networks
- Summary
Product History
- Product History
- Cisco Firewall Products
- Cisco IDS Products
- Cisco VPN Products
- Cisco ASA All-in-One Solution
- Summary
Hardware Overview
Part II: Firewall Solution
Initial Setup and System Maintenance
- Initial Setup and System Maintenance
- Accessing the Cisco ASA Appliances
- Managing Licenses
- Initial Setup
- IP Version 6
- Setting Up the System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Network Access Control
- Network Access Control
- Packet Filtering
- Advanced ACL Features
- Content and URL Filtering
- Deployment Scenarios Using ACLs
- Monitoring Network Access Control
- Understanding Address Translation
- DNS Doctoring
- Monitoring Address Translations
- Summary
IP Routing
Authentication, Authorization, and Accounting (AAA)
- Authentication, Authorization, and Accounting (AAA)
- AAA Protocols and Services Supported by Cisco ASA
- Defining an Authentication Server
- Configuring Authentication of Administrative Sessions
- Authenticating Firewall Sessions (Cut-Through Proxy Feature)
- Configuring Authorization
- Configuring Accounting
- Deployment Scenarios
- Troubleshooting AAA
- Summary
Application Inspection
- Application Inspection
- Enabling Application Inspection Using the Modular Policy Framework
- Selective Inspection
- Computer Telephony Interface Quick Buffer Encoding Inspection
- Domain Name System
- Extended Simple Mail Transfer Protocol
- File Transfer Protocol
- General Packet Radio Service Tunneling Protocol
- H.323
- HTTP
- ICMP
- ILS
- MGCP
- NetBIOS
- PPTP
- Sun RPC
- RSH
- RTSP
- SIP
- Skinny
- SNMP
- SQL*Net
- TFTP
- XDMCP
- Deployment Scenarios
- Summary
Security Contexts
- Security Contexts
- Architectural Overview
- Configuration of Security Contexts
- Deployment Scenarios
- Monitoring and Troubleshooting the Security Contexts
- Summary
Transparent Firewalls
- Transparent Firewalls
- Architectural Overview
- Transparent Firewalls and VPNs
- Configuration of Transparent Firewall
- Deployment Scenarios
- Monitoring and Troubleshooting the Transparent Firewall
- Summary
Failover and Redundancy
- Failover and Redundancy
- Architectural Overview
- Failover Configuration
- Deployment Scenarios
- Monitoring and Troubleshooting Failovers
- Summary
Quality of Service
- Quality of Service
- Architectural Overview
- Configuring Quality of Service
- QoS Deployment Scenarios
- Monitoring QoS
- Summary
Part III: Intrusion Prevention System (IPS) Solution
Intrusion Prevention System Integration
- Intrusion Prevention System Integration
- Adaptive Inspection Prevention Security Services Module Overview (AIP-SSM)
- Directing Traffic to the AIP-SSM
- AIP-SSM Module Software Recovery
- Additional IPS Features
- Summary
Configuring and Troubleshooting Cisco IPS Software via CLI
- Configuring and Troubleshooting Cisco IPS Software via CLI
- Cisco IPS Software Architecture
- Introduction to the CIPS 5.x Command-Line Interface
- User Administration
- AIP-SSM Maintenance
- Advanced Features and Configuration
- Summary
Part IV: Virtual Private Network (VPN) Solution
Site-to-Site IPSec VPNs
- Site-to-Site IPSec VPNs
- Preconfiguration Checklist
- Configuration Steps
- Advanced Features
- Optional Commands
- Deployment Scenarios
- Monitoring and Troubleshooting Site-to-Site IPSec VPNs
- Summary
Remote Access VPN
- Remote Access VPN
- Cisco IPSec Remote Access VPN Solution
- Advanced Cisco IPSec VPN Features
- Deployment Scenarios of Cisco IPSec VPN
- Monitoring and Troubleshooting Cisco Remote Access VPN
- Cisco WebVPN Solution
- Advanced WebVPN Features
- Deployment Scenarios of WebVPN
- Monitoring and Troubleshooting WebVPN
- Summary
Public Key Infrastructure (PKI)
- Public Key Infrastructure (PKI)
- Introduction to PKI
- Enrolling the Cisco ASA to a CA Using SCEP
- Manual (Cut-and-Paste) Enrollment
- Configuring CRL Options
- Configuring IPSec Site-to-Site Tunnels Using Certificates
- Configuring the Cisco ASA to Accept Remote-Access VPN Clients Using Certificates
- Troubleshooting PKI
- Summary
Part V: Adaptive Security Device Manager
Introduction to ASDM
- Introduction to ASDM
- Setting Up ASDM
- Initial Setup
- Functional Screens
- Interface Management
- System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Firewall Management Using ASDM
- Firewall Management Using ASDM
- Access Control Lists
- Address Translation
- Routing Protocols
- AAA
- Application Inspection
- Security Contexts
- Transparent Firewalls
- Failover
- QoS
- Summary
IPS Management Using ASDM
- IPS Management Using ASDM
- Accessing the IPS Device Management Console from ASDM
- Configuring Basic AIP-SSM Settings
- Advanced IPS Configuration and Monitoring Using ASDM
- Summary
VPN Management Using ASDM
- VPN Management Using ASDM
- Site-to-Site VPN Setup Using Preshared Keys
- Site-to-Site VPN Setup Using PKI
- Cisco Remote-Access IPSec VPN Setup
- WebVPN
- VPN Monitoring
- Summary
Case Studies
EAN: 2147483647
Pages: 231
- ERP Systems Impact on Organizations
- Enterprise Application Integration: New Solutions for a Solved Problem or a Challenging Research Field?
- Context Management of ERP Processes in Virtual Communities
- Intrinsic and Contextual Data Quality: The Effect of Media and Personal Involvement
- Relevance and Micro-Relevance for the Professional as Determinants of IT-Diffusion and IT-Use in Healthcare
