RIP
RIP is a fairly old Interior Gateway Protocol (IGP), but it is still deployed in many networks. It is typically used in small and homogeneous networks. RIP is a distance-vector routing protocol, and it is defined in RFC 1058, "Routing Information Protocol." Its second version is defined in RFC 2453, "RIP Version 2."
RIP uses broadcast or multicast packetsdepending on the versionto communicate with its neighbors and exchange routing information. It uses the hop-count methodology to calculate its metric. Hop count is the number of routing devices that the packets forwarded by a router or a Cisco ASA (in this case) will traverse. RIP has a limit of 15 hops. A route to a network that is directly connected to the Cisco ASA has a metric of 0. However, a route with a metric reaching or exceeding 16 is considered unreachable.
Two versions of the RIP routing protocol are available (Cisco ASA supports both versions):
- RIP version 1 (RIPv1) Does not support classless interdomain routing (CIDR) and variable-length subnet masks (VLSMs). VLSMs enable routing protocols to define different subnet masks for the same major network. For example, 10.0.0.0 is a Class A network. Its mask is 255.0.0.0. VLSM provides the ability to divide this network into smaller segments (i.e., 10.1.1.0/24, 10.1.2.0/24, etc.) Because RIPv1 does not support VLSM, no subnet mask information is present in its routing updates. RIP uses different techniques, such as holddowns, count-to-infinity, split horizon, and poison reverse, to prevent loops.
- RIP version 2 (RIPv2) Supports CIDR and VLSMs. RIPv2 also converges faster than its predecessor. It also supports peer or neighbor authentication (plain-text or MD5 authentication), which provides additional security.
Configuring RIP
The configuration of the Cisco ASA is simple, but somewhat limited. Figure 6-3 illustrates the first example topology.
Figure 6-3. Basic RIP Configuration
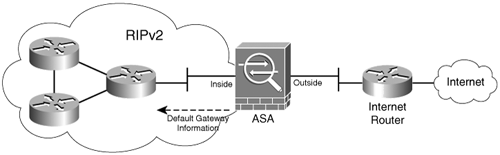
In the example shown in Figure 6-3, the Cisco ASA is connected to a router running RIPv2. This router is learning routes from two other routers. Subsequently, routes to all these networks are being advertised by the router connected to the Cisco ASA. The Cisco ASA is also injecting a default route to the inside router. Example 6-1 shows the necessary commands to configure RIPv2 on the Cisco ASA and to advertise a default route to the internal router.
Example 6-1. Basic RIP Configuration
Chicago# configure terminal Chicago(config)# rip inside passive version 2 Chicago(config)# rip inside default version 2 Chicago(config)# exit
The rip command enables RIP on the Cisco ASA. The interface on which RIP will be enabled is also specified. The desired result is to learn the internal routes and advertise default route information. To do this, the default keyword is used. The version keyword specifies what RIP version is used. With the passive keyword, the Cisco ASA interface listens for RIP routing packets and uses that information to update its routing table, but it does not advertise any routing updates through the specified interface.
Note
Use the clear configure rip command to remove all the RIP related commands from the Cisco ASA.
The example shown in Figure 6-4 demonstrates how RIPv2 and RIPv1 are configured on two separate interfaces (inside and outside, in this example).
Figure 6-4. Configuring RIPv1 and RIPv2 on Two Different Interfaces
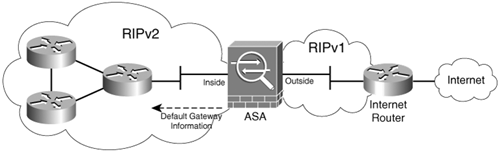
In the example shown in Figure 6-4, the inside interface is configured for RIPv2, as previously explained. Additionally, the Cisco ASA is learning RIPv1 routes on its outside interface from the Internet router. The commands needed for this configuration are shown in Example 6-2.
Example 6-2. Configuring RIPv1 and RIPv2 on Two Different Interfaces
Chicago# configure terminal Chicago(config)# rip inside passive version 2 Chicago(config)# rip inside default version 2 Chicago(config)# rip outside passive version 1 Chicago(config)# exit
RIPv1 does not support authentication. Cisco ASA supports two modes of RIPv2 authentication: plain-text authentication and Message Digest 5 (MD5) authentication.
Tip
A best practice is to use MD5 instead of plain-text authentication, because MD5 authentication provides a higher level of security.
RIP authentication using MD5 is added in Figure 6-5. Example 6-3 shows the necessary commands to make this possible.
Figure 6-5. RIPv2 MD5 Authentication
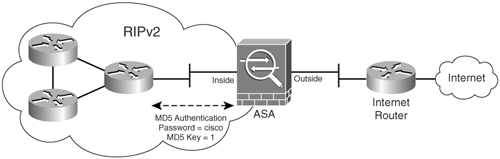
Example 6-3. Configuring RIPv2 MD5 Authentication
Chicago# configure terminal Chicago(config)# rip inside default version 2 authentication md5 cisco 1 Chicago(config)# exit
The word cisco is the MD5 password in this example. The number 1 is the RIPv2 authentication key identification value. This key ID can be configured with a number from 0 to 255, but it must match the one in use on the peer router.
Verifying the Configuration
As mentioned earlier in this chapter, the show route command displays the routing table. With this command, you can also verify that the correct routes are being learned by the Cisco ASA via RIP. Example 6-4 shows the output of the Cisco ASA routing table while learning several routes via RIP from its peers.
Example 6-4. Output of the Routing Table Showing Routes Learned via RIP
Chicago# show route R 0.0.0.0 0.0.0.0 [1/0] via 209.165.200.226, outside C 192.168.10.0 255.255.255.0 is directly connected, inside R 192.168.20.0 255.255.255.0 [1/0] via 192.168.10.2, inside R 192.168.13.0 255.255.255.0 [2/0] via 192.168.10.2, inside C 209.165.200.224 255.255.255.224 is directly connected, outside
Notice the letter R or C by each route entry. The letter R indicates that the route is learned via RIP; C indicates that it is directly connected.
Troubleshooting RIP
This section includes several commands and techniques that you can use while trouble-shooting different issues that may arise throughout your deployment of RIP. A number of scenarios are provided to exemplify these troubleshooting techniques.
Scenario 1: RIP Version Mismatch
Using the topology illustrated in Figure 6-5, the internal router was intentionally configured with the incorrect RIP version. The Cisco ASA was configured with RIPv2 on the inside interface (as previously shown) and the internal router was configured with RIPv1. The output of the show route command does not display any routes learned via RIP. Example 6-5 shows the output of this command.
Example 6-5. Output of show route Command Missing RIP Routes
Chicago# show route C 192.168.10.0 255.255.255.0 is directly connected, inside C 209.165.200.224 255.255.255.224 is directly connected, outside
The command debug rip is used as a troubleshooting tool for this problem, as demonstrated in Example 6-6.
Example 6-6. Output of debug rip Showing Incorrect RIP Version During Negotiation
Chicago# debug rip debug rip enabled at level 1 Chicago# RIP: interface inside sending v2 update to 224.0.0.9 RIP: received packet from interface inside [pif=2] (192.168.10.2:520) RIP: interface inside received v1 update from 192.168.10.2
In the highlighted line, the router sends the incorrect RIP version. The solution to this problem is to configure RIP version 2 on the internal router.
Scenario 2: RIP Authentication Mismatch
The topology shown in Figure 6-5 is also used in this example. The internal router and the Cisco ASA were configured to perform RIP authentication using MD5. The MD5 password was configured incorrectly in the Cisco ASA. The router is configured with an MD5 password of cisco and the Cisco ASA was configured with cisco123. Example 6-7 shows the output of debug ip rip on the router, which shows that there is a problem with MD5 authentication.
Example 6-7. Output of debug ip rip on the Router While the Incorrect MD5 Password Was Configured
Router# debug ip rip 2d09h: RIP: received packet with MD5 authentication 2d09h: RIP: ignored v2 packet from 192.168.10.1 (invalid authentication)
This message also appears if the incorrect authentication method or mode is selected.
Scenario 3: Multicast or Broadcast Packets Blocked
RIPv1 uses broadcast packets and RIPv2 uses multicast packets, as previously discussed. If broadcast or multicast packets (respectively) are blocked, the Cisco ASA will never be able to successfully establish a RIP neighbor relationship with its peers. The debug rip command is also useful to troubleshoot this problem. Example 6-8 shows the output of debug rip while RIPv2 multicast packets were being blocked.
Example 6-8. Output of debug rip While Multicast Packets Are Being Dropped or Blocked
Chicago# debug rip debug rip enabled at level 1 RIP: interface inside sending v2 update to 224.0.0.9 RIP: interface inside sending v2 update to 224.0.0.9 RIP: interface inside sending v2 update to 224.0.0.9 RIP: interface inside sending v2 update to 224.0.0.9
As you can see from this example, the Cisco ASA is sending the RIPv2 packets to the address 224.0.0.9 without receiving anything back from its peers. You will also see this behavior when RIP is not enabled on any routing device on that segment.
Tip
You can also ping the multicast address of 224.0.0.9 to verify that packets are not blocked.
Scenario 4: Correct Configuration and Behavior
It is impossible to troubleshoot a problem if you are not familiar with the behavior of the device(s) to determine whether or not they are configured correctly. Example 6-9 includes the output of debug rip when all devices are configured correctly. Again, the Cisco ASA is configured to support RIPv1 on its outside interface; support RIPv2 on its inside interface; broadcast a default route to the inside router; and use MD5 authentication for RIPv2 learned routes.
Example 6-9. Output of debug ripCorrect Configuration
Chicago# debug rip Chicago# RIP: received packet from interface inside [pif=2] (192.168.10.2:520) RIP: interface inside received v2 update from 192.168.10.2 RIP: update contains 2 routes RIP: interface inside sending v2 update to 224.0.0.9
The highlighted line shows that a RIPv2 update was received on the Cisco ASA and it contained two routes from the router 192.168.10.2. Example 6-10 shows the complete routing table, showing the routes learned via both peers.
Example 6-10. Routing TableCorrect Configuration
Chicago# show route R 0.0.0.0 0.0.0.0 [1/0] via 209.165.200.226, outside C 192.168.10.0 255.255.255.0 is directly connected, inside R 192.168.20.0 255.255.255.0 [1/0] via 192.168.10.2, inside R 192.168.13.0 255.255.255.0 [2/0] via 192.168.10.2, inside C 209.165.200.224 255.255.255.224 is directly connected, outside
Part I: Product Overview
Introduction to Network Security
- Introduction to Network Security
- Firewall Technologies
- Intrusion Detection and Prevention Technologies
- Network-Based Attacks
- Virtual Private Networks
- Summary
Product History
- Product History
- Cisco Firewall Products
- Cisco IDS Products
- Cisco VPN Products
- Cisco ASA All-in-One Solution
- Summary
Hardware Overview
Part II: Firewall Solution
Initial Setup and System Maintenance
- Initial Setup and System Maintenance
- Accessing the Cisco ASA Appliances
- Managing Licenses
- Initial Setup
- IP Version 6
- Setting Up the System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Network Access Control
- Network Access Control
- Packet Filtering
- Advanced ACL Features
- Content and URL Filtering
- Deployment Scenarios Using ACLs
- Monitoring Network Access Control
- Understanding Address Translation
- DNS Doctoring
- Monitoring Address Translations
- Summary
IP Routing
Authentication, Authorization, and Accounting (AAA)
- Authentication, Authorization, and Accounting (AAA)
- AAA Protocols and Services Supported by Cisco ASA
- Defining an Authentication Server
- Configuring Authentication of Administrative Sessions
- Authenticating Firewall Sessions (Cut-Through Proxy Feature)
- Configuring Authorization
- Configuring Accounting
- Deployment Scenarios
- Troubleshooting AAA
- Summary
Application Inspection
- Application Inspection
- Enabling Application Inspection Using the Modular Policy Framework
- Selective Inspection
- Computer Telephony Interface Quick Buffer Encoding Inspection
- Domain Name System
- Extended Simple Mail Transfer Protocol
- File Transfer Protocol
- General Packet Radio Service Tunneling Protocol
- H.323
- HTTP
- ICMP
- ILS
- MGCP
- NetBIOS
- PPTP
- Sun RPC
- RSH
- RTSP
- SIP
- Skinny
- SNMP
- SQL*Net
- TFTP
- XDMCP
- Deployment Scenarios
- Summary
Security Contexts
- Security Contexts
- Architectural Overview
- Configuration of Security Contexts
- Deployment Scenarios
- Monitoring and Troubleshooting the Security Contexts
- Summary
Transparent Firewalls
- Transparent Firewalls
- Architectural Overview
- Transparent Firewalls and VPNs
- Configuration of Transparent Firewall
- Deployment Scenarios
- Monitoring and Troubleshooting the Transparent Firewall
- Summary
Failover and Redundancy
- Failover and Redundancy
- Architectural Overview
- Failover Configuration
- Deployment Scenarios
- Monitoring and Troubleshooting Failovers
- Summary
Quality of Service
- Quality of Service
- Architectural Overview
- Configuring Quality of Service
- QoS Deployment Scenarios
- Monitoring QoS
- Summary
Part III: Intrusion Prevention System (IPS) Solution
Intrusion Prevention System Integration
- Intrusion Prevention System Integration
- Adaptive Inspection Prevention Security Services Module Overview (AIP-SSM)
- Directing Traffic to the AIP-SSM
- AIP-SSM Module Software Recovery
- Additional IPS Features
- Summary
Configuring and Troubleshooting Cisco IPS Software via CLI
- Configuring and Troubleshooting Cisco IPS Software via CLI
- Cisco IPS Software Architecture
- Introduction to the CIPS 5.x Command-Line Interface
- User Administration
- AIP-SSM Maintenance
- Advanced Features and Configuration
- Summary
Part IV: Virtual Private Network (VPN) Solution
Site-to-Site IPSec VPNs
- Site-to-Site IPSec VPNs
- Preconfiguration Checklist
- Configuration Steps
- Advanced Features
- Optional Commands
- Deployment Scenarios
- Monitoring and Troubleshooting Site-to-Site IPSec VPNs
- Summary
Remote Access VPN
- Remote Access VPN
- Cisco IPSec Remote Access VPN Solution
- Advanced Cisco IPSec VPN Features
- Deployment Scenarios of Cisco IPSec VPN
- Monitoring and Troubleshooting Cisco Remote Access VPN
- Cisco WebVPN Solution
- Advanced WebVPN Features
- Deployment Scenarios of WebVPN
- Monitoring and Troubleshooting WebVPN
- Summary
Public Key Infrastructure (PKI)
- Public Key Infrastructure (PKI)
- Introduction to PKI
- Enrolling the Cisco ASA to a CA Using SCEP
- Manual (Cut-and-Paste) Enrollment
- Configuring CRL Options
- Configuring IPSec Site-to-Site Tunnels Using Certificates
- Configuring the Cisco ASA to Accept Remote-Access VPN Clients Using Certificates
- Troubleshooting PKI
- Summary
Part V: Adaptive Security Device Manager
Introduction to ASDM
- Introduction to ASDM
- Setting Up ASDM
- Initial Setup
- Functional Screens
- Interface Management
- System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Firewall Management Using ASDM
- Firewall Management Using ASDM
- Access Control Lists
- Address Translation
- Routing Protocols
- AAA
- Application Inspection
- Security Contexts
- Transparent Firewalls
- Failover
- QoS
- Summary
IPS Management Using ASDM
- IPS Management Using ASDM
- Accessing the IPS Device Management Console from ASDM
- Configuring Basic AIP-SSM Settings
- Advanced IPS Configuration and Monitoring Using ASDM
- Summary
VPN Management Using ASDM
- VPN Management Using ASDM
- Site-to-Site VPN Setup Using Preshared Keys
- Site-to-Site VPN Setup Using PKI
- Cisco Remote-Access IPSec VPN Setup
- WebVPN
- VPN Monitoring
- Summary
Case Studies
EAN: 2147483647
Pages: 231
