ping
ping tests network connectivity by sending an ICMP echo-request message to the remote machine. The remote machine must respond with an ICMP reply message. The ping command takes a single argument: the address or hostname of the remote system. It prints various statistics about the responses it receives:
Router>ping 10.10.1.2 Type escape sequence to abort Sending 5, 100-byte ICMP Echos to 10.10.1.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms Router>
Each exclamation point indicates that the router has successfully received a response from the remote host. On a local network, you would expect a success rate very close to 100%. Across the Internet, you would tolerate some failures, but they should still be relatively rare. Many sites configure their routers to block ICMP traffic because it has been used in a number of denial-of-service attacks. Therefore, you can't count on the ability to ping an arbitrary host on the Internet.
|
If you don't give the hostname on the command line, the router prompts you for it, and for other information. You can specify the number of packets to send, the number of seconds to wait for a response before assuming that the ping has failed, the amount of data to include in the packet, and more:
Router>ping Protocol [ip]: ip We are doing IP only Target IP address: 10.10.1.2 The host we want to ping Repeat count [5]: 10 Number of pings to be sent to the destination Datagram size [100]: The actual size of the packet in bytes Timeout in seconds [2]: Timeout value Extended commands [n]: See the Privileged Ping Commands Sweep range of sizes [n]: Changes the packet size as it pings Type escape sequence to abort. Sending 10, 100-byte ICMP Echos to 10.10.1.2, timeout is 2 seconds: !!!!!!!!!! Success rate is 100 percent (10/10), round-trip min/avg/max = 1/3/4 ms
Here we changed the repeat count to 10, which sent 10 ping packets to our destination.
16.1.1. Ping the Broadcast Address
If you want to discover what hosts are active on your subnet, you can ping the network's broadcast address. All nodes on the subnet should respond. Since this tool can be used for malicious purposes, it is available only from the privileged level. For example, if our ethernet0 interface were on the 192.168.1.0/24 subnet, we could ping the broadcast address of that network:
Router#ping 192.168.1.255
The output will show the responses from all the hosts on the subnet. Another way to find out which hosts the router knows about is to display its ARP table:
Router#show ip arp
This command lists all the machines from which the router has seen packets.
16.1.2. Extended ping
Extended ping provides more options than the basic ping command. These options can be used to better diagnose a network connectivity problem. To enter the extended ping mode, type the ping command, then type y at the "Extended commands" prompt:
Extended commands [n]: y Source address or interface: 192.168.1.1 Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/4 ms
The most useful of the extended commands is Source address or interface. This command lets you specify the source address that will be used in constructing the packet; you can specify either the IP address or the name of the interface from which the IP address will be taken. Normally, the router sets the packet's source IP address to the interface that was used to send the ICMP packet, based on the routing table.
16.1.2.1. What can we test with the source address?
Setting the source address of the ICMP packet allows you to test network connectivity more thoroughly. The host that receives the ICMP packet must reply to the source address given in the packet. This generally means that the remote host replies to the address of the interface through which the packet was sent. But by setting another source address, we can direct the ICMP reply to another address. Consider Figure 16-1.
Figure 16-1. Using the source address in extended pings
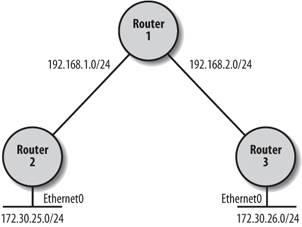
If Router 2 pings Router 3, the source address of the ICMP packet defaults to the address of the interface closest to Router 3i.e., the interface on the 192.168.1.0/24 network. If this ping succeeds, we know Router 3 can get to the 192.168.1.0 network. But what if we want to test whether Router 3 knows how to get to the 172.30.25.0/24 subnet? To execute this test, we perform an extended ping on Router 2 while using the source address on ethernet0:
Router#ping Protocol [ip]: Target IP address: 172.30.26.1 Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: ethernet0 Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.30.26.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/4 ms
This successful ping proves two things. First, the pings obviously made it to 172.30.26.1. This shows that routing is working on Router 2, at least to a minimal extent. If routing were not working, Router 2 wouldn't know how to send a packet to 172.30.26.1, to which it doesn't have a direct connection. Second, the pings also made it back to Router 2's ethernet0 interface, which is on the 172.30.25.0/24 subnet. This proves that some form of routing is working on Router 3otherwise, it wouldn't know how to get to the 172.30.25.0/24 subnet. If this test failed, it would indicate that either Router 2 did not know how to get to Router 3's network, or Router 3 did not know how to get to Router 2's network.
While this test is useful, it isn't perfect. Even if the packet returns, we really don't know how it made it back. In a more complex network, there may be many ways for a packet to make it from Router 3 back to Router 2. Using the source address doesn't actually prove that a certain network is up or down, but it's helpful as a quick test.
Getting Started
- Getting Started
- IOS User Modes
- Command-Line Completion
- Get to Know the Question Mark
- Command-Line Editing Keys
- Pausing Output
- show Commands
IOS Images and Configuration Files
- IOS Images and Configuration Files
- IOS Image Filenames
- The New Cisco IOS Packaging Model
- Loading Image Files Through the Network
- Using the IOS Filesystem for Images
- The Routers Configuration
- Loading Configuration Files
Basic Router Configuration
- Basic Router Configuration
- Setting the Router Name
- Setting the System Prompt
- Configuration Comments
- The Enable Password
- Mapping Hostnames to IP Addresses
- Setting the Routers Time
- Enabling SNMP
- Cisco Discovery Protocol
- System Banners
Line Commands
- Line Commands
- The line Command
- The Console Port
- Virtual Terminals (VTYs)
- Asynchronous Ports (TTYs)
- The Auxiliary (AUX) Port
- show line
- Reverse Telnet
- Common Configuration Items
Interface Commands
- Interface Commands
- Naming and Numbering Interfaces
- Basic Interface Configuration Commands
- The Loopback Interface
- The Null Interface
- Ethernet, Fast Ethernet, and Gigabit Ethernet Interfaces
- Token Ring Interfaces
- ISDN Interfaces
- Serial Interfaces
- Asynchronous Interfaces
- Interface show Commands
Networking Technologies
Access Lists
IP Routing Topics
- IP Routing Topics
- Autonomous System (AS) Numbers
- Interior and Exterior Gateway Protocols
- Distance-Vector and Link-State Routing Protocols
- Static Routes
- Split Horizon
- Passive Interfaces
- Fast Switching and Process Switching
Interior Routing Protocols
Border Gateway Protocol
- Border Gateway Protocol
- Introduction to BGP
- A Simple BGP Configuration
- Route Filtering
- An Advanced BGP Configuration
- Neighbor Authentication
- Peer Groups
- Route Reflectors
- BGP Confederacies
- BGP TTL Security
Quality of Service
- Quality of Service
- Marking
- Older Queuing Methods
- Modern IOS QoS Tools
- Congestion Avoidance
- Traffic Policing
- Traffic Shaping
- AutoQoS
- QoS Device Manager
Dial-on-Demand Routing
- Dial-on-Demand Routing
- Configuring a Simple DDR Connection
- Sample Legacy DDR Configurations
- Dialer Interfaces (Dialer Profiles)
- Multilink PPP
- Snapshot DDR
Specialized Networking Topics
- Specialized Networking Topics
- Bridging
- Hot Standby Routing Protocol (HSRP)
- Network Address Translation (NAT)
- Tunnels
- Encrypted Tunnels
- Multicast Routing
- Multiprotocol Label Switching (MPLS)
Switches and VLANs
- Switches and VLANs
- Switch Terminology
- IOS on Switches
- Basic Switch Configuration
- Trunking
- Switch Monitor Port for IDS or Sniffers
- Troubleshooting Switches
Router Security
- Router Security
- Securing Enable Mode Access
- Routine Security Measures
- Restricting Access to Your Router
Troubleshooting and Logging
Quick Reference
Appendix A Network Basics
Index
EAN: 2147483647
Pages: 1031

