An Overview of TrojansThe History of Trojans
|
Objective:
|
Trojans are programs that pretend to do one thing, but when loaded actually perform another more malicious act. Trojans gain their name from Homer's epic tale, The Iliad. To defeat their enemy, the Greeks built a giant wooden horse with a trapdoor in its belly. The Greeks tricked the Trojans into bringing the large wooden horse into the fortified city. However, unknown to the Trojans and under the cover of darkness, the Greeks crawled out of the wooden horse, opened the city's gate, and allowed the waiting solders in.
A software Trojan horse is based on this same concept. A user might think that a file looks harmless and is safe to run, but after the file is executed, it delivers a malicious payload. That payload might allow a hacker remote access to your system, start a keystroke logger to record your every keystroke, plant a backdoor on your system, cause a denial of service (DoS), or even disable your antivirus protection or software firewall.
Unlike a virus or worm, Trojans cannot spread themselves. They rely on the uninformed user.
Trojan Types
The EC-Council groups Trojans into seven primary types, which is simply their way of organizing them. In reality, it's hard to place some Trojans into a single type, as many have more that one function. To better understand what Trojans can do, these types are outlined in the following list:
- Remote access Remote access Trojans (RAT) allow the attacker full control over the system. SubSeven is an example of this type of Trojan. Remote access Trojans are usually set up as client/server programs so that the attacker can connect to the infected system and control it remotely.
- Data sending The idea behind this type of Trojan is to capture and redirect data. Eblaster is an example of this type of Trojan. These programs can capture keystrokes, passwords, or any other type of information and redirect it to a hidden file or even email it there as a predefined email account.
- Destructive These Trojans are particularly malicious. Hard Disk Killer is an example of this type of Trojan. The sole purpose of these types of programs is to destroy files or wipe out a system. Your only warning of an infection might be that you see excessive hard drive activity or hear your hard drive making noise. However, it is most likely that by the time you realize something is wrong, your files might already have been wiped out.
- Denial of service (DoS) These Trojans are designed to cause a DoS. They can be designed to knock out a specific service or to bring an entire system offline.
- Proxy These Trojans are designed to work as proxies. These programs can help a hacker hide and allow him to perform activities from the victim's computer, not his own. After all, the farther away the hacker is from the crime, the harder it becomes to trace.
- FTP These Trojans are specifically designed to work on port 21. They allow the hacker or others to upload, download, or move files at will on the victim's machine.
- Security software disablers These Trojans are designed to attack and kill antivirus or software firewalls. The goal of disabling these programs is to make it easier for the hacker to control the system.
Trojan Ports and Communication Methods
|
Objective:
|
Trojans can communicate in several different ways. Some use overt communications. These programs make no attempt to hide the transmission of data as it is moved onto or off of the victim's computer. Others use covert communications. This means that the hacker goes to lengths to hide the transmission of data to and from the victim. Many Trojans that open covert channels also function as backdoors. A backdoor is any type of program that will allow a hacker to connect to a computer without going through the normal authentication process. If a hacker can get a backdoor program loaded on an internal device, the hacker has the ability to come and go at will. Some of the programs spawn a connection on the victim's computer connecting out to the hacker. The danger of this type of attack is the traffic moving from inside out, which means from inside the organization to the outside Internet. This is typically the least restrictive, as companies are usually more concerned about what comes in the network as they are about what leaves the network.
Table 6.1 lists common Trojans, commercial tools, covert channels, and backdoor programs. It's a good idea to spend a minute looking at the ports and protocols that these programs use. While some of these programs are commercial they may be misused for malicious purposes. Knowing what to look for builds awareness and can help you spot these programs when they are encountered.
|
Name |
Default Protocol |
Default Port |
|---|---|---|
|
Back Orifice |
UDP |
31337 |
|
Back Orifice 2000 |
TCP/UDP |
54320/54321 |
|
Beast |
TCP |
6666 |
|
Citrix ICA |
TCP/UDP |
1494 |
|
Donald Dick |
TCP |
23476/23477 |
|
Loki |
ICMP (Internet Control Message Protocol) |
NA |
|
Masters Paradise |
TCP (Transmission Control Protocol) |
40421/40422/40426 |
|
Netmeeting Remote Desktop Control |
TCP (Transmission Control Protocol)/UDP (User Datagram Protocol) |
49608/49609 |
|
NetBus |
TCP |
12345 |
|
Netcat |
TCP/UDP |
Any |
|
pcAnywhere |
TCP |
5631/5632/65301 |
|
Reachout |
TCP |
43188 |
|
Remotely Anywhere |
TCP |
2000/2001 |
|
Remote |
TCP/UDP |
135-139 |
|
Timbuktu |
TCP/UDP |
407 |
|
VNC |
TCP/UDP |
5800/5801 |
Trojan Goals
|
Objective:
|
Not all Trojans were designed for the same purpose. Some are destructive and can destroy computer systems, whereas others seek only to steal specific pieces of information. Although not all of them make their presence known, Trojans are still dangerous because they represent a loss of confidentiality, integrity, and availability. Some common goals of Trojans are
- Credit card data Credit card data and personal information has become a huge target. After the hacker has this information, he can go on an online shopping spree or use the card to purchase services, such as domain name registration.
- Passwords Passwords are always a big target. Many of us are guilty of password reuse. Even if we are not, there is always the danger that a hacker can extract email passwords, dialup passwords, or other online account passwords.
- Insider information We have all had those moments in which we have said, "If only I had known this beforehand." That's what insider information is about. It can give the hacker critical information before it is made public or released.
- Data storage The goal of the Trojan might be nothing more than to use your system for storage space. It could be movies, music, illegal software (warez), or even pornography.
- Random acts of mischief It could be that the hacker has targeted you only for a random act of mischief. He is just having a little fun at your expense.
Trojan Infection Mechanisms
|
Objective:
|
After a hacker has written a Trojan, he will still need to spread it. The Internet has made this much easier than it used to be. There are a variety of ways to spread malware, including
- Peer-to-peer networks (P2P) Although users might think that they are getting the latest copy of a computer game or the Microsoft Office package, in reality, they might be getting much more. P2P networks such as Kazaa, imesh, aimster, and gnutella are generally unmonitored and allow anyone to spread any programs they want, legitimate or not.
- Instant messaging (IM) IM was not built with any security controls. So, you never know the real contents of a file or program that someone has sent you. IM users are at great risk of becoming targets for Trojans and other types of malware.
- Internet Relay Chat (IRC) IRC is full of individuals ready to attack the newbies who are enticed into downloading a free program or application.
- Email attachments Attachments are another common way to spread a Trojan. To get you to open them, these hackers might disguise the message to appear to be from a legitimate organization. It might also offer you a valuable price, a desired piece of software, or similar message to pique your interest. If you feel that you must investigate these programs, save them first and then run an antivirus on them.
Tip
Email attachments are the number one means of malware propagation.
- Physical access If a hacker has physical access to a victim's system, he can just copy the Trojan horse to the hard drive. The hacker can even take the attack to the next level by creating a Trojan that is unique to the system or network. It might be a fake logon screen that looks like the real one or even a fake database.
- Browser bugs Many users don't update their browsers as soon as updates are released. Web browsers often treat the content they receive as trusted. The truth is that nothing in a web page can be trusted to follow any guidelines. A website can send your browser data that exploits a bug in a browser, violates computer security, and might load a Trojan.
- Freeware Nothing in life is free, and that includes most software. Users are taking a big risk when they download freeware from an unknown source. Not only might the freeware contain a Trojan, but also freeware has become a favorite target for adware and spyware.
Effects of Trojans
The effects of Trojans can range from the benign to the extreme. Individuals whose systems become infected might never even know, whereas others might experience complete system failure. Most often, the victim might notice that something is just not right. Maybe programs seemly open by themselves, or the web browser opens pages the user didn't request. If the hacker wants, he can change your background, reboot the systems, or turn the volume up on the speakers to get your attention.
Trojan Tools
Now that you have a little background on Trojans, their means of transmission, and their purpose, it is time to take a look at some well-known Trojan tools.
Tini is a simple and small backdoor Trojan written for Windows. Coded in assembler language, it is about 3KB. It listens at TCP port 7777 and gives anybody who connects a remote command prompt. It can be downloaded at www.ntsecurity.nu/toolbox/tini. The disadvantage to the hacker is that the tool always listens on port 7777. Because the port cannot be changed, it is easy for a penetration tester to scan for and find this open port.
Qaz is another example of a backdoor Trojan. It works by searching for and renaming Notepad.exe to Note.com and then copies itself to the computer as Notepad.exe. Each time Notepad.exe is executed, the Qaz Trojan executes and calls up the original Notepad to avoid being noticed. The backdoor payload in the virus uses WinSock and awaits a connection at port 7597. Anyone who finds this port open can connect to the Trojaned computer. Qaz can be manually removed by editing the registry. After you open REGEDIT, go to
HKEY_LOCAL_MACHINE
Software
Microsoft
Windows
CurrentVersion
Run
Then search for any registry key that contains the data value of startIE=XXXXNotepad.exe. When found, highlight the registry key that loads the file and press the Delete key. After you have rebooted, use the Find tool under the Start menu to find and rename Note.com to Notepad.exe.
The next several Trojans discussed are examples of remote access Trojans. These are not a legitimate means of connecting to a computer. There are plenty of legitimate remote access programs that people use to access their systems remotely. For example, you might need to troubleshoot your Uncle Bob's computer remotely; a college student might need to access his home computer to retrieve a homework assignment while at school; or a salesman might need access while traveling. Popular remote access programs include pcAnywhere, Windows Terminal server, and GoToMyPC. Remote access Trojans are similar to these programs, except that they are used to sneak into a victim's computer and are covertly installed. Remote access Trojans typically have two components, which include a server and a client. The server executable runs on the victim's computer, whereas the client application runs on the hacker's computer. After a remote access Trojan has been installed on a victim's computer, it opens a predefined port on the victim's computer. That port is used to connect to the client software that the hacker runs.
Donald Dick is an example of a remote access Trojan. It enables a hacker to control the victim's computer and perform a host of activities. Donald Dick can use IP or SPX and has a default port of 23476 and 23477. A screenshot of the Trojan can be seen in Figure 6.1.
Figure 6.1. Donald Dick.
Donald Dick gives the hacker access to the local file system, as well as the ability to browse, create, and remove directories, and even edit the registry. It is usually installed by some form of trickery or by sending it as an email attachment. When installed on a 2000 or XP machine, it will add the following files to the system32 folder: Lsasup.exe, pmss.exe, samcfg.exe, and bootexec.exe. Once installed, the program will also embed itself into the registry so that it will restart upon reboot. Hackers have the ability to connect to servers through the client GUI and by command line interface. A complete list of commands appears in the readme file that accompanies the Trojan.
NetBus is the next tool on the list. It was written by Carl-Fredrik Neikter in the late 1990s. According to his stated goal, the tool was written to let people have some fun with their friends. In current versions of the program, such as 1.6 and 1.7, the server portion of the Trojan is named patch.exe and has a default size of 483KB. When executed by the victim, it copies itself to the Windows directory and creates the file called KeyHook.dll. The server then opens two TCP ports numbered 12345 and 12346. It uses 12345 to listen for a remote client and apparently responds to the client via port 12346. If you find port 12345 open during an ethical hacking engagement, you can Telnet to it and verify that it is NetBus. If it is NetBus, it will respond with its name and version number. Keep in mind that the default ports can be easily changed to use any other port from 1 to 65534.
When the server is contacted by the hacker, it creates two files named Hosts.txt and Memo.txt and places them in the same directory as the running server. These are usually found in the Windows folder. The functions of these files are as follows:
- Hosts.txt Lists hosts that have contacted the server if logging is enabled.
- Memo.txt The remote user can leave a memo here for himself.
NetBus can even be instructed to send an email when it runs for the first time to notify the hacker that it has been installed. NetBus is also capable of redirecting input to a specified port to another IP address via the server machine. This means that the remote user can do mischief on a third machine someplace on the Net and his connection will appear to come from the redirecting address. As an example, suppose that you open port 666 on the victim's NetBus server and redirect the traffic to www.microsoft.com on port 80. Now, any connections made to the victim's NetBus server on TCP port 666 will be forwarded to www.microsoft.com port 80, and the logs at the microsoft.com server would show the victim's NetBus machine's IP address as the connector! Redirection is discussed in more detail later in the Chapter, but be aware that there are few legitimate uses for such redirection techniques.
Back Orifice and Back Orifice 2000 (BO2K) represent the next generation of backdoor access tools that followed NetBus. BO2K allows greater functionality than Donald Dick or NetBus. It was designed to accept a variety of specially designed plug-ins. It was written by Cult of the Dead Cow (CDC). BO2K also supports encryption to perform all communication between client and server. To use the BO2K server, you need to step through a setup configuration as follows:
|
1. |
Start the BO2K Wizard and click Next when the Wizard's splash screen is presented. |
|
2. |
You are prompted by the Wizard to enter the server executable that will be edited. |
|
3. |
You have the choice to run BO2K over Transmission Control Protocol (TCP) or User Datagram Protocol (UDP). Typically, TCP is usually chosen, as it's a more robust protocol. UDP can be used if it's needed to traverse the firewall or security architecture. |
|
4. |
After choosing to use TCP to control the BO2K server, the next screen queries the port number that will be used. Port 80 is used, as it is usually open. |
|
5. |
In the next screen, you're given the choice to enter a password to access the server. Although using passwords is good, the fact that it will allow you to choose open authentication would mean that anyone can access without supplying credentials. |
|
6. |
The server configuration tool is loaded when the Wizard finishes. It will allow further customization. |
|
7. |
Make sure that the server is configured to be loaded on startup. This will prevent the BO2K server from being unavailable between reboots on the victim's machine. You will need to select the Startup folder in the lower-left Option Variables pane, and then choose the option to make the server load on startup in the Startup folder. |
|
8. |
Click Save Server when you are finished making any changes. |
Now that the server is configured, you still need to find a way to install it on the victim computer. Whatever method is chosen, the only file that needs to be run by the victim is the BO2K executable. After it has been executed, it will open the port you configured. It also writes the UMGR32 executable to the following location c:windowssystemumgr32.exe. BO2K is equipped with stealth capabilities and might not show up in your Windows Task Manager if configured as stealth. It hides itself by expanding the memory allocated to an existing thread, copying itself into this memory, and then creating a remote thread that runs in the process space of the first existing thread. The original program then terminates, and its process disappears from memory. If not in stealth mode, BO2K will show up as the UMGR32 task is running as a Remote Administration Service. In either case, the hacker has complete control of the victim's computer.
Note
Because BO2K provides the option of using UDP or TCP, it is a hacker's favorite.
Some of the BO2K client features include
- Address book style server list
- Plug-in extensibility
- Multiple server connections at once
- Customizable look and feel
- Session logging
Some of the BO2K server features include
- Keystroke logging
- HTTP file system browsing and transfer with optional restrictions
- Management of Microsoft Networking file sharing
- Direct registry editing
- Direct file browsing, transfer, and management
- Plug-in extensibility
- Remote upgrading, installation, and uninstallation
- Network redirection of TCP/IP connections
- Access console programs such as command shells through Telnet
- Multimedia support for audio/video capture and audio playback
- Passwords and screensaver password dumping
- Process control, start, stop, list ability
- GUI message prompts
- Proprietary file compression
- Remote shutdown and reboot ability
- DNS name resolution
Optional plug-ins include
- Cryptographically Strong Triple-DES encryption
- Encrypted flow control, which makes BO2K hard to detect
- ICMP tunneling
- Bo Peep, which provides streaming video
SubSeven was the next remote access Trojan to be released. Although widely used to infect systems, it failed to gain the press that BO2K did, even though at its time of release, it was considered the most advanced program of its type. One of these advanced features is that it can mutate, so its fingerprint appears to change. This can make it difficult for antivirus tools to detect. Similar to NetBus and BO2K, SubSeven is divided into two parts: a client program that the hacker runs on his machine and a server that must be installed onto a victim's computer. The victim usually receives the program as an email attachment, which installs itself onto the system when run. It can even display a fake error message to make it seem that the fake program failed to execute. When the infected file is run, the Trojan copies itself to the Windows directory with the original name of the file it was run from, and then it copies a DLL file named Watching.dll to WindowsSystem directory. After being activated, the server uses TCP ports 6711, 6712, and 6713 by default.
Tip
Be sure that you know the port numbers of the most common Trojans before attempting the exam.
SubSeven's user interface allows the attacker to easily monitor a victim's keystrokes, watch a computer's web cam, take screenshots, eavesdrop through the computer's microphone, control the mouse pointer, read and write files, and sniff traffic off the victim's local network. It can also be programmed to announce itself over I Seek You (ICQ) or IRC.
In the years since these groundbreaking remote access Trojans were released, many have followed in their tracks. Some of these include
- Let me rule Yet another remote access Trojan, this one was written in Delphi and uses TCP port 26097 by default.
- RECUB This Trojan gets its name from a UNIX tool named Remoted Encrypted Callback Unix Backdoor (RECUB). It has been ported to Windows and is designed to be used as a Trojan. It features RC4 encryption, code injection, and encrypted ICMP communication request; it can use Netcat for remote shell and is only 5.39KB.
- Phatbot A variant of Agobot, a big family of IRC bots. This Trojan can steal personal information, such as email addresses, credit card numbers, and software licensing codes. Rather than sending this information from one email address to an IRC channel, it forwards the information using a peer-to-peer (P2P) network. Phatbot can also kill many antivirus or software firewall products, which makes victims susceptible to secondary attacks.
- Amitis The Trojan opens TCP port 27551 and gives the hacker complete control of the victim's computer.
- Zombam.B This Trojan allows its hacker to use a Web browser to access your computer. It opens port 80 by default and was written with a Trojan generation tool, HTTPRat. It also attempts to terminate various antivirus and firewall processes.
- Beast One of the first of a new design of Trojans. It uses DLL injection. This means that it actually injects itself into an existing process. It is not visible with traditional process viewers, can be harder to detect, and can be harder to unload. Its default port is TCP 6666.
- Hard disk killer This is not your normal Trojan; this program was written for only one reason, and that is to destroy your system's hard drive. Upon execution, it will attack your hard drive and wipe out the hard drive in just a few seconds. This tool has no legitimate purpose.
Distributing Trojans
Just think about it; distributing Trojans is no easy task. Users are more alert, less willing to click on email attachments, and more likely to be running antivirus. On Windows computers, it used to be enough for the hacker to just include a lot of spaces between the program's name and suffix, such as important_message_text.txt.exe, or the hacker could choose program suffixes or names from those programs that would normally be installed and running on the victim's machine such as Notepad.exe. The problem is that the users' and administrators' levels of awareness about these techniques are greater than it used to be.
Wrappers offer hackers another, more advanced method to slip past a user's normal defenses. A wrapper is a program used to combine two or more executables into a single packaged program. The victim might think that he has downloaded the latest version of Microsoft Office or the great new game that he wanted but could not afford. Sadly, the sweet and innocent wrapped Trojan package is not so nice once installed. When installed, the malicious code is loaded along with the legitimate program. Figure 6.2 gives an example of how a hacker binds two programs together.
Figure 6.2. How wrappers work.
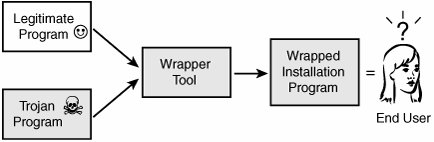
Wrappers are a favorite tool of the script kiddies, as wrappers allow script kiddies to take the Trojan programs and bind the Trojan program with legitimate applications. Even the most inexperienced hacker can use these tools. They are also referred to as binders, packagers, and EXE binders. Some wrappers enable only two programs to be joined, whereas others enable the binding of three, four, five, or more programs together. Basically, these programs perform installation builders and setup programs. Many of these programs are available to the hacker underground. Some of the more well-known are listed:
- EliteWrap Considered one of the premier wrapping tools, EliteWrap has a built-in capability to perform redundancy checks to verify that files have been properly wrapped and will install properly. It can perform a full install or create an install directory. EliteWrap can use a pack file to make the program wait to process the remaining files, and it can also perform a hidden install without user interaction.
- Saran Wrap A wrapper program designed to hide Back Orifice; it can wrap Back Orifice with another existing program into a standard "Install Shield" installer program.
- Trojan Man This wrapper combines two programs and also can encrypt the resulting package in an attempt to foil antivirus programs.
- Teflon Oil Patch This is another program used to bind Trojans to any files you specify in an attempt to defeat Trojan detection programs.
- Restorator Although Restorator is not designed as a hacking tool, you can use it to modify, add, and remove resources such as text, images, icons, sounds, videos, version, dialogs, and menus in almost all programs. It can be used to add a Trojan to a package, such as a screensaver, before it is forwarded to the victim.
- Firekiller 2000 This tool would most likely be used in combination with other tools when wrapped. Firekiller 2000 was designed to disable firewall and antivirus software. Programs such as Norton AntiVirus and McAfee VirusScan were susceptible before being patched.
Trojan Tool Kits
|
Objective:
|
The Trojans shown in this Chapter represent just a few of the many Trojans available in the wild. Some malicious code writers have taken these tools even further by creating construction kits to build new, unique Trojans. Trojan construction kits make it relatively easy for even script kiddies to build Trojans. Several of these tools are shown in the following:
- Trojan horse construction kit is one example of such a destructive tool. This command-line utility allows you to construct a Trojan horse with a multitude of destructive behavior, such as destroying the partition table, MBR, or even the entire hard drive.
- Senna Spy is another example of a Trojan generator. It requires Visual Basic to compile the generated source code. It is capable of many types of custom options, such as file transfer, executing DOS commands, keyboard control, and list and control processes.
- Stealth tool is not a Trojan construction kit, but it's close. Stealth tool is a program designed to make Trojans harder to detect. Its purpose is to change up the file by adding bytes, changing strings, or splitting and combining files. It includes a fake version of netstat to further help the hacker hide his deeds.
Covert Communications |
Part I: Exam Preparation
The Business Aspects of Penetration Testing
- The Business Aspects of Penetration Testing
- Study Strategies
- Security Fundamentals
- Security Testing
- Hacker and Cracker Descriptions
- Ethical Hackers
- Test PlansKeeping It Legal
- Ethics and Legality
- Summary
- Key Terms
- Apply Your Knowledge
The Technical Foundations of Hacking
- The Technical Foundations of Hacking
- Study Strategies
- The Attackers Process
- The Ethical Hackers Process
- Security and the Stack
- Summary
- Key Terms
- Apply Your Knowledge
Footprinting and Scanning
- Footprinting and Scanning
- Study Strategies
- Determining Assessment Scope
- The Seven-Step Information Gathering Process
- Summary
- Key Terms
- Apply Your Knowledge
Enumeration and System Hacking
- Enumeration and System Hacking
- Study Strategies
- The Architecture of Windows Computers
- Enumeration
- Windows Hacking
- Summary
- Key Terms
- Apply Your Knowledge
Linux and Automated Security Assessment Tools
- Linux and Automated Security Assessment Tools
- Study Strategies
- Linux
- Automated Assessment Tools
- Picking the Right Platform
- Summary
- Key Terms
- Apply Your Knowledge
Trojans and Backdoors
- Trojans and Backdoors
- Study Strategies
- An Overview of TrojansThe History of Trojans
- Covert Communications
- Trojan and Backdoor Countermeasures
- Summary
- Key Terms
- Apply Your Knowledge
Sniffers, Session Hijacking, and Denial of Service
- Sniffers, Session Hijacking, and Denial of Service
- Study Strategies
- Sniffers
- Session Hijacking
- Denial of Service
- Summary
- Key Terms
- Apply Your Knowledge
Web Server Hacking, Web Applications, and Database Attacks
- Web Server Hacking, Web Applications, and Database Attacks
- Study Strategies
- Web Server Hacking
- Web Application Hacking
- Database Overview
- Summary
- Key Terms
- Apply Your Knowledge
Wireless Technologies, Security, and Attacks
- Wireless Technologies, Security, and Attacks
- Study Strategies
- Wireless TechnologiesA Brief History
- Wireless LANs
- Wireless Hacking Tools
- Securing Wireless Networks
- Summary
- Key Terms
- Apply Your Knowledge
IDS, Firewalls, and Honeypots
- IDS, Firewalls, and Honeypots
- Study Strategies
- Intrusion Detection Systems
- Firewalls
- Honeypots
- Summary
- Key Terms
- Apply Your Knowledge
Buffer Overflows, Viruses, and Worms
- Buffer Overflows, Viruses, and Worms
- Study Strategies
- Buffer Overflows
- Viruses and Worms
- Summary
- Key Terms
- Apply Your Knowledge
Cryptographic Attacks and Defenses
- Cryptographic Attacks and Defenses
- Study Strategies
- Functions of Cryptography
- History of Cryptography
- Algorithms
- Hashing
- Digital Signatures
- Steganography
- Digital Certificates
- Public Key Infrastructure
- Protocols, Standards, and Applications
- Encryption Cracking and Tools
- Summary
- Key Terms
- Apply Your Knowledge
Physical Security and Social Engineering
- Physical Security and Social Engineering
- Study Strategies
- Physical Security
- Social Engineering
- Summary
- Key Terms
- Apply Your Knowledge
Part II: Final Review
- Fast Facts
- Ethics and Legality
- Footprinting
- Scanning
- Enumeration
- System Hacking
- Trojans and Backdoors
- Sniffers
- Denial of Service
- Social Engineering
- Session Hijacking
- Hacking Web Servers
- Web Application Vulnerabilities
- Web-Based Password Cracking Techniques
- SQL Injection
- Hacking Wireless Networks
- Virus and Worms
- Physical Security
- Linux Hacking
- Evading Firewalls, IDS, and Honeypots
- Buffer Overflows
- Cryptography
- Penetration Testing
- Certified Ethical Hacker
- Practice Exam Questions
- Answers to Practice Exam Questions
- Glossary
Part III: Appendixes
Appendix A. Using the ExamGear Special Edition Software
- Appendix A. Using the ExamGear Special Edition Software
- Exam Simulation
- Study Tools
- How ExamGear Special Edition Works
- Installing ExamGear Special Edition
- Using ExamGear Special Edition
- Contacting Que Certification
- License
- Software and Documentation
- License Term and Charges
- Title
- Updates
- Limited Warranty and Disclaimer
- Limitation of Liability
- Miscellaneous
- U.S. Government Restricted Rights
EAN: 2147483647
Pages: 247
