Enumeration
|
Objective:
|
The Network Neighborhood might have given way to My Network Places; however, the same underlying insecure protocols exist, such as Server Message Block (SMB) and InterProcess Communication (IPC). SMB makes it possible for users to share files and folders, although IPC offers a default share on Windows systems. This share, the IPC$, is used to support named pipes that programs use for interprocess (or process-to-process) communications. Because named pipes can be redirected over the network to connect local and remote systems, they also enable remote administration. As you might think, this can be a problem Hopefully, you remember some basic Microsoft information that you learned when getting your first Microsoft certification. In the world of Windows, the $ syntax represents a hidden share. So, even though you may not see the IPC$ share when looking for shared drives and folders, that doesn't mean that it is not there. The IPC$ share exists so that commands can be sent back and forth between systems.
Years ago when protocols such as SMB were thought up, the mindset of the time was not on security, but on connectivity. After all, Microsoft's first networked OS was of a peer-to-peer design. While it's true that Linux runs similar services with the Samba suite of services, Windows remains the primary focus of these vulnerabilities. The most basic connection possible with IPC$ is the Null, or anonymous, connection, which is achieved by executing a net command. There's an entire host of Net commands. A few are discussed here, but for a more complete list, just type net from the command line and the /? syntax after any of the commands you see that you would like more information on. For example, if you have identified open ports of 135, 139, and 445 on some targeted systems, you might start with the net view /domain command.
C:>net view /domain Domain SALES MARKETING ACCOUNTING The command completed successfully.
Notice that these net commands are quite handy. They have identified the sales, marketing, and accounting groups. To query any specific domain group, just use the net command again in the form of net view /domain:domain_name.
C:>net view /domain:accounting Server Name Remark \Mickey \Pluto \Donald The command completed successfully.
You can take a closer look at any one system by using the net view \system_name command.
C: et view \donald Shared resources at \DONALD Sharename Type Comment ----------------------------------------------------- CDRW Disk D Disk Payroll Disk Printer Disk Temp Disk The command was completed successfully.
Hopefully you are starting to see the power of the net command. Next, you see how it can be exploited when used in combination with IPC$.
Exploiting IPC$
|
Objective:
|
Now that you have completed some basic groundwork, let's move on to enumerating user details, account information, weak passwords, and so on. IPC$ is further exploited for these activities. Specifically, you will need to set up a Null session. It is set up manually with the net command:
C:>net use \targetipc$ "" /u:""
Accessing the IPC$ share might not give you full administrator rights, but it will give you the ability to run the tools that are about to be discussed. There is a limit to how far this command will get; Table 4.3 shows its capabilities.
|
Operating System |
Enumerate Shares |
Enumerate Usernames |
Enumerate SIDs |
Enumerate Running Services |
|---|---|---|---|---|
|
Windows XP and 2003 |
Yes |
Yes |
Yes |
No |
|
Windows 2000 |
Yes |
Yes |
Yes |
No |
|
Windows NT |
Yes |
Yes |
Yes |
Yes |
Some of the mileage you will get out of the IPC$ share will depend on how the network is configured. If the network is configured with relaxed security, permission compatible with preWin2000, you will have few restrictions placed on your abilities. These will correspond to the settings shown in Table 4.3 for Windows NT. If the network is configured in native mode, you will be much more restricted, as shown in Table 4.3. Native mode means that the systems are only compatible with Windows 2000 or later domain controllers. A Windows 2003 default installation will reveal far less sensitive information than an older system. However, a Windows 2003 PDC might still divulge information, such a usernames and domain info. Let's start with looking at the looser permissions.
Enumeration Tools
With a net use \targetipc$ "" /u:"" command executed, you're primed to start hacking at the system.
Note
The tools discussed in this section, such as SID2USER, USER2SID, and DumpSec, require that you have a Null session established before you attempt to use them.
You'll probably want to go for the administrator account, but do you really know which one that is? That's where a set of tools called USER2SID and SID2USER will come in handy. The goal of these utility tools is to obtain a SID from the account name or account name from a SID. The guest account is a good target for the USER2SID tool.
C:>user2sid \192.168.13.10 guest S-1-5-21-1607980884-492894322-1202660629-501 Number of subauthorities is 5 Domain is SALES Length of SID in memory is 28 bytes Type of SID is SidTypeUser
Did you notice the second line of the previous code? It's the SID of the system, along with the RID. The RID of 501 tells you that you are looking at the guest account. The second tool in this set is SID2USER. The goal of SID2USER is to obtain the account name from SID. Therefore, the SID from the previous command is pasted in with a RID change from 501 to 500. Why 500? A RID of 500 should reveal the true administrator. Don't forget to drop the S-1.
C:>sid2user \192.168.13.10 5 21 1607980884 492894322 1202660629 500 Name is JACK Domain is SALES Type of SID is SidTypeUser
Look closely at the output. Notice that the RID of 500 corresponds to the Jack account. If the true administrator has tried to practice security by obscurity by renaming the administrator account, it has done him little good here. There are GUI tools that will provide more functionality, although this is a great command-line tool. You can script it and work your way up the user accounts; just start at a RID of 1000. If you're wondering where the GUI tools are that have this same type of functionality, you are going to like DumpSec.
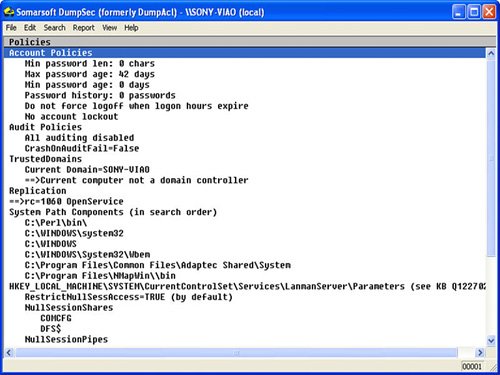
DumpSec is a Windows-based GUI enumeration tool from SomarSoft. It allows you to remotely connect to Windows machines and dump account details, share permissions, and user information. It is shown in Figure 4.2. Its GUI-based format makes it easy to take the results and port them into a spreadsheet so that holes in system security are readily apparent and easily tracked. It can provide you with usernames, SIDs, RIDs, account comments, account policies, and dial-in information.
Figure 4.2. DumpSec.
Enum is another command-line tool that can be used to display account settings. It was developed by BindView, and it provides just about every available command-line switch you can imagine. As with the preceding tools, a Null session is required for it to function. An example is shown in the following:
C:>enum -Pc 192.168.13.10 server: PLUTO setting up session... success. password policy: min length: none min age: none max age: 45 days lockout threshold: 3 lockout duration: 30 mins lockout reset: 30 mins
Many tools can be used for enumeration. The ones listed here should give you an idea of what this category of tool can do. Listed here are some other tools that perform the same type of enumeration:
- Userinfo Released by HammerofGod, this command-line tool retrieves all available information about any known user from any NT/Win2k/XP system.
- 4GetAcct Developed by SecurityFriday, this GUI tool also has the capability to enumerate vulnerable Windows systems.
- GetUserInfo Created by JoeWare, this command-line tool extracts user info from a domain or computer.
- Ldp This executable is what you will need if you're working with AD systems. After you find port 389 open and authenticate yourself using an accounteven guest will workyou will be able to enumerate all the users and built-in groups.
Other tools are available to enumerate a Windows system. For example, if you are local to the system, you can also use NBTStat. Microsoft defines NBTStat as a tool designed to help troubleshoot NetBIOS name resolution problems. It has options, such as local cache lookup, WINS server query, broadcast, LMHOSTS lookup, Hosts lookup, and DNS server query. Typing nbtstat at a Windows command prompt will tell you all about its usage:
C: btstat Displays protocol statistics and current TCP/IP connections using NBT(NetBIOS over TCP/IP). NBTSTAT [-a RemoteName] [-A IP address] [-c] [-n] [-r] [-R] [-s] [S] [interval] ]
One of the best ways to use NBTStat is with the -A option. Let's look at what that returns:
C:>NBTstat -A 192.168.13.10 NetBIOS Remote Machine Name Table Name Type Status --------------------------------------------- DONALD <00> UNIQUE Registered WORKGROUP <00> GROUP Registered DONALD <20> UNIQUE Registered WORKGROUP <1E> GROUP Registered WORKGROUP <1D> UNIQUE Registered ..__MSBROWSE__.<01> GROUP Registered MAC Address = 00-19-5D-1F-26-68
A name table that provides specific hex codes and tags of unique or group is returned. These codes identify the services running on this specific system. As an example, do you see the code of 1D UNIQUE? This signifies that the system Donald is the master browser for this particular workgroup. Other common codes include
|
domain |
1B |
U |
Domain Master Browser |
|
domain |
1C |
G |
Domain Controllers |
|
domain |
1D |
U |
Master Browser |
|
domain |
1E |
G |
Browser Service Elections |
A complete list of NetBIOS name codes can be found at www.cotse.com/nbcodes.htm, or by Googling NetBIOS name codes.
Countermeasures
|
Objective:
|
It's almost hard to believe the amount of information that you are able to retrieve with just a Null session. Usernames, account info, password policies, share information, system services, and more are all ripe for taking. What can be done? Responsible security professionals want to practice the principle of least privilege:
- Block ports
- Disable unnecessary services
- Use the RestrictAnonymous setting
Blocking ports 135, 137, 139, 389, and 445 is a good start. Many people still believe that only peers close by can access their shares if they have a valid username and password. The fact is that anyone who has access to these key ports can attempt to access the open shares or the IPC$ share. Access to the ports listed previously should be restricted at sensitive network gateways.
Disable services you do not need. As an example, you can disable File and Print sharing. Also, inside the network properties tab under advanced settings, disable NetBIOS over TCP/IP. Null sessions require access to ports 135139 or 445. Blocking access to these ports will deny access to what the attacker most desires.
Tightening the restrict anonymous setting is another powerful countermeasure. The restrict anonymous setting has been around since NT. Back then, it just had a setting of 0, which is off, or 1, which means restrict all access. Changing it to a 1 sometimes meant losing the functionality of certain programs. Starting with Windows 2000, a third setting was added. The three settings are
- 0No restrictions, relies on default permissions
- 1Does not allow enumeration of SAM accounts and names
- 2No access at all without explicit anonymous permissions
In Windows 2000, the setting still defaults to 0. You can find it under Settings, Control Panel, Administrative Tools, Local Security Policy, Local Policies, Security Options, Restrict Anonymous. Windows server 2003 defaults to a setting of 1. If you ratchet it up to a setting of 2, make sure and verify that there are no problems with older or custom applications that might require anonymous access.
Tip
Understanding the options to prevent enumeration is a potential test concept.
Simple Network Management Protocol (SNMP) Enumeration
Simple Network Management Protocol (SNMP) is a popular TCP/IP standard for remote monitoring and management of hosts, routers, and other nodes and devices on a network. It works through a system of agents and nodes. SNMP version 3 offers data encryption and authentication, although version 1 is still widely used. Version 1 is a clear text protocol and provides only limited security through the use of community strings. The default community strings are public and private and are transmitted in cleartext. If the community strings have not been changed or if someone can sniff the community strings, they have more than enough to launch an attack.
Tip
SNMP uses default community strings of public and private.
Devices that are SNMP enabled share a lot of information about each device that probably should not be shared with unauthorized parties. Even if RestrictAnonymous has been set to 2, SNMP will return plenty of account and share information. Some tools available for SNMP enumeration include
- SNMPUtil A Windows resource kit command-line enumeration tool that can be used to query computers running SNMP.
- IP Network Browser A GUI-based network discovery tool from www.solarwinds.net that allows you to perform a detailed discovery on one device or an entire subnet.
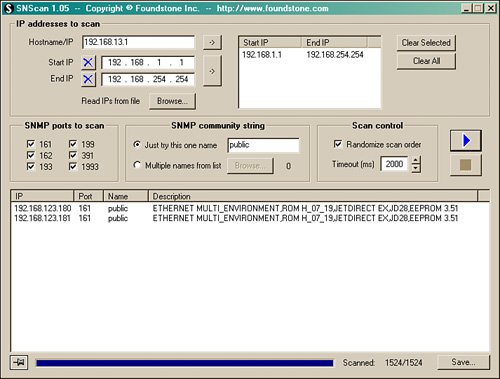
- SNScan A free GUI-based SNMP scanner from Foundstone, shown in Figure 4.3.
Figure 4.3. SNScan.
The best defense against SNMP enumeration is to turn it off if it's not needed. If it is required, make sure that you block port 161 at network chokepoints, and ensure that an upgrade to SNMP v3 is possible. Changing the community strings is another defensive tactic as is making them different in each zone of the network.
Windows Hacking |
Part I: Exam Preparation
The Business Aspects of Penetration Testing
- The Business Aspects of Penetration Testing
- Study Strategies
- Security Fundamentals
- Security Testing
- Hacker and Cracker Descriptions
- Ethical Hackers
- Test PlansKeeping It Legal
- Ethics and Legality
- Summary
- Key Terms
- Apply Your Knowledge
The Technical Foundations of Hacking
- The Technical Foundations of Hacking
- Study Strategies
- The Attackers Process
- The Ethical Hackers Process
- Security and the Stack
- Summary
- Key Terms
- Apply Your Knowledge
Footprinting and Scanning
- Footprinting and Scanning
- Study Strategies
- Determining Assessment Scope
- The Seven-Step Information Gathering Process
- Summary
- Key Terms
- Apply Your Knowledge
Enumeration and System Hacking
- Enumeration and System Hacking
- Study Strategies
- The Architecture of Windows Computers
- Enumeration
- Windows Hacking
- Summary
- Key Terms
- Apply Your Knowledge
Linux and Automated Security Assessment Tools
- Linux and Automated Security Assessment Tools
- Study Strategies
- Linux
- Automated Assessment Tools
- Picking the Right Platform
- Summary
- Key Terms
- Apply Your Knowledge
Trojans and Backdoors
- Trojans and Backdoors
- Study Strategies
- An Overview of TrojansThe History of Trojans
- Covert Communications
- Trojan and Backdoor Countermeasures
- Summary
- Key Terms
- Apply Your Knowledge
Sniffers, Session Hijacking, and Denial of Service
- Sniffers, Session Hijacking, and Denial of Service
- Study Strategies
- Sniffers
- Session Hijacking
- Denial of Service
- Summary
- Key Terms
- Apply Your Knowledge
Web Server Hacking, Web Applications, and Database Attacks
- Web Server Hacking, Web Applications, and Database Attacks
- Study Strategies
- Web Server Hacking
- Web Application Hacking
- Database Overview
- Summary
- Key Terms
- Apply Your Knowledge
Wireless Technologies, Security, and Attacks
- Wireless Technologies, Security, and Attacks
- Study Strategies
- Wireless TechnologiesA Brief History
- Wireless LANs
- Wireless Hacking Tools
- Securing Wireless Networks
- Summary
- Key Terms
- Apply Your Knowledge
IDS, Firewalls, and Honeypots
- IDS, Firewalls, and Honeypots
- Study Strategies
- Intrusion Detection Systems
- Firewalls
- Honeypots
- Summary
- Key Terms
- Apply Your Knowledge
Buffer Overflows, Viruses, and Worms
- Buffer Overflows, Viruses, and Worms
- Study Strategies
- Buffer Overflows
- Viruses and Worms
- Summary
- Key Terms
- Apply Your Knowledge
Cryptographic Attacks and Defenses
- Cryptographic Attacks and Defenses
- Study Strategies
- Functions of Cryptography
- History of Cryptography
- Algorithms
- Hashing
- Digital Signatures
- Steganography
- Digital Certificates
- Public Key Infrastructure
- Protocols, Standards, and Applications
- Encryption Cracking and Tools
- Summary
- Key Terms
- Apply Your Knowledge
Physical Security and Social Engineering
- Physical Security and Social Engineering
- Study Strategies
- Physical Security
- Social Engineering
- Summary
- Key Terms
- Apply Your Knowledge
Part II: Final Review
- Fast Facts
- Ethics and Legality
- Footprinting
- Scanning
- Enumeration
- System Hacking
- Trojans and Backdoors
- Sniffers
- Denial of Service
- Social Engineering
- Session Hijacking
- Hacking Web Servers
- Web Application Vulnerabilities
- Web-Based Password Cracking Techniques
- SQL Injection
- Hacking Wireless Networks
- Virus and Worms
- Physical Security
- Linux Hacking
- Evading Firewalls, IDS, and Honeypots
- Buffer Overflows
- Cryptography
- Penetration Testing
- Certified Ethical Hacker
- Practice Exam Questions
- Answers to Practice Exam Questions
- Glossary
Part III: Appendixes
Appendix A. Using the ExamGear Special Edition Software
- Appendix A. Using the ExamGear Special Edition Software
- Exam Simulation
- Study Tools
- How ExamGear Special Edition Works
- Installing ExamGear Special Edition
- Using ExamGear Special Edition
- Contacting Que Certification
- License
- Software and Documentation
- License Term and Charges
- Title
- Updates
- Limited Warranty and Disclaimer
- Limitation of Liability
- Miscellaneous
- U.S. Government Restricted Rights
EAN: 2147483647
Pages: 247
