Protocols, Standards, and Applications
|
Objective:
|
Many types of cryptographic solutions can be applied from the Application layer all the way down to the Physical layer. Often, a pen test will uncover the use of protocols that are blatantly insecure. Examples include File Transfer Protocol (FTP), Simple Mail Transfer Protocol (SMTP), Hypertext Transfer Protocol (HTTP), and Telnet. All these applications pass information in cleartext. The applications and protocols discussed here are all solutions that the ethical hacker can recommend to clients to help them build a more secure infrastructure.
- Secure MIME (S/MIME) S/MIME adds two valuable components to standard email, digital signatures, and public key encryption. S/MIME supports X.509 digital certificates and RSA encryption.
- Pretty Good Privacy (PGP) PGP is similar to PKI but does not have a CA. PGP builds a web of trust because the users must determine who they trust. Users sign and issue their own keys. PGP stores the public key in a file named pubring.pkr; keys located here can be shared with anyone. The user's secret key is in the file named secring.skr. Loss of this file exposes the secret key and allows a hacker to gain access or spoof the user. PGP can be used to secure email and to encrypt data. It was developed to provide high level encryption to the average user.
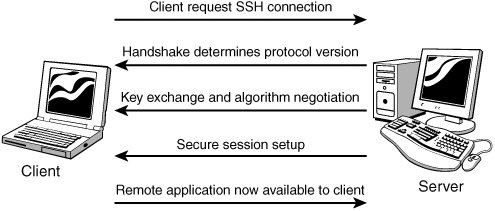
- Secure Shell (SSH) A protocol that permits secure remote access over a network from one computer to another. SSH negotiates and establishes an encrypted connection between an SSH client and an SSH server on port 22 by default. The steps needed to set up an SSH session are shown in Figure 12.12.
Figure 12.12. SSH Handshake.
- Secure Sockets Layer (SSL) Netscape Communications Corp. initially developed SSL to provide security and privacy between clients and servers over the Internet. It's considered application independent and can be used with Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), and Telnet to run on top of it transparently. SSL uses RSA public key cryptography. It is capable of client authentication, server authentication, and encrypted SSL connection.
- IPSec The most widely used standard for protecting IP datagrams is IPSec. Because IPSec can be applied below the Application layer, it can be used by any or all applications and is transparent to end users. It can be used in tunnel and transport mode.
- Point-to-point tunneling protocol (PPTP) Developed by a group of vendors that included: Microsoft, 3Com, and Ascend. PPTP is composed of two components: the transport, which maintains the virtual connection, and the encryption, which ensures confidentiality. It is widely used for virtual private networks (VPNs).
- Encrypted File System (EFS) Microsoft developed EFS as a built-in encryption system. EFS allows users to encrypt NTFS files, folders, and directories. These files remain encrypted if moved or renamed. EFS does have a backdoor, as it allows a person designated as the recovery agent to unencrypt or recover the information. This backdoor can be useful because it enables access to the data without having to go through any type of password cracking process. On Windows 2000, the administrator was the recovery agent by default; in Windows 2003, you must define a recovery agent. There's another great method to bypass EFS if files are encrypted while not residing within an encrypted folder. When a standalone file is encrypted with EFS, the file is not encrypted directly. A backup copy of the file is created and moved into the temp directory. It is named efs0.tmp. Next, the data in the temp file is encrypted and moved back into the original file. Finally, the temporary file is deleted just as a normal file is. This means that the entry is removed from the FAT and the clusters on the disk are marked available for use. Unless the clusters have been wiped or overwritten, you could take a hex editor or a tool, such as Diskprobe, and search for efs0.tmp. From there, you can easily view any remaining data that hasn't been overwritten.
Note
Enabling EFS file system encryption at the folder level will prevent attacks against the efs0.tmp file. A good place to start would be the MyDocuments folder, as it would encrypt documents on-the-fly when they are saved to the folder.
Encryption Cracking and Tools |
Part I: Exam Preparation
The Business Aspects of Penetration Testing
- The Business Aspects of Penetration Testing
- Study Strategies
- Security Fundamentals
- Security Testing
- Hacker and Cracker Descriptions
- Ethical Hackers
- Test PlansKeeping It Legal
- Ethics and Legality
- Summary
- Key Terms
- Apply Your Knowledge
The Technical Foundations of Hacking
- The Technical Foundations of Hacking
- Study Strategies
- The Attackers Process
- The Ethical Hackers Process
- Security and the Stack
- Summary
- Key Terms
- Apply Your Knowledge
Footprinting and Scanning
- Footprinting and Scanning
- Study Strategies
- Determining Assessment Scope
- The Seven-Step Information Gathering Process
- Summary
- Key Terms
- Apply Your Knowledge
Enumeration and System Hacking
- Enumeration and System Hacking
- Study Strategies
- The Architecture of Windows Computers
- Enumeration
- Windows Hacking
- Summary
- Key Terms
- Apply Your Knowledge
Linux and Automated Security Assessment Tools
- Linux and Automated Security Assessment Tools
- Study Strategies
- Linux
- Automated Assessment Tools
- Picking the Right Platform
- Summary
- Key Terms
- Apply Your Knowledge
Trojans and Backdoors
- Trojans and Backdoors
- Study Strategies
- An Overview of TrojansThe History of Trojans
- Covert Communications
- Trojan and Backdoor Countermeasures
- Summary
- Key Terms
- Apply Your Knowledge
Sniffers, Session Hijacking, and Denial of Service
- Sniffers, Session Hijacking, and Denial of Service
- Study Strategies
- Sniffers
- Session Hijacking
- Denial of Service
- Summary
- Key Terms
- Apply Your Knowledge
Web Server Hacking, Web Applications, and Database Attacks
- Web Server Hacking, Web Applications, and Database Attacks
- Study Strategies
- Web Server Hacking
- Web Application Hacking
- Database Overview
- Summary
- Key Terms
- Apply Your Knowledge
Wireless Technologies, Security, and Attacks
- Wireless Technologies, Security, and Attacks
- Study Strategies
- Wireless TechnologiesA Brief History
- Wireless LANs
- Wireless Hacking Tools
- Securing Wireless Networks
- Summary
- Key Terms
- Apply Your Knowledge
IDS, Firewalls, and Honeypots
- IDS, Firewalls, and Honeypots
- Study Strategies
- Intrusion Detection Systems
- Firewalls
- Honeypots
- Summary
- Key Terms
- Apply Your Knowledge
Buffer Overflows, Viruses, and Worms
- Buffer Overflows, Viruses, and Worms
- Study Strategies
- Buffer Overflows
- Viruses and Worms
- Summary
- Key Terms
- Apply Your Knowledge
Cryptographic Attacks and Defenses
- Cryptographic Attacks and Defenses
- Study Strategies
- Functions of Cryptography
- History of Cryptography
- Algorithms
- Hashing
- Digital Signatures
- Steganography
- Digital Certificates
- Public Key Infrastructure
- Protocols, Standards, and Applications
- Encryption Cracking and Tools
- Summary
- Key Terms
- Apply Your Knowledge
Physical Security and Social Engineering
- Physical Security and Social Engineering
- Study Strategies
- Physical Security
- Social Engineering
- Summary
- Key Terms
- Apply Your Knowledge
Part II: Final Review
- Fast Facts
- Ethics and Legality
- Footprinting
- Scanning
- Enumeration
- System Hacking
- Trojans and Backdoors
- Sniffers
- Denial of Service
- Social Engineering
- Session Hijacking
- Hacking Web Servers
- Web Application Vulnerabilities
- Web-Based Password Cracking Techniques
- SQL Injection
- Hacking Wireless Networks
- Virus and Worms
- Physical Security
- Linux Hacking
- Evading Firewalls, IDS, and Honeypots
- Buffer Overflows
- Cryptography
- Penetration Testing
- Certified Ethical Hacker
- Practice Exam Questions
- Answers to Practice Exam Questions
- Glossary
Part III: Appendixes
Appendix A. Using the ExamGear Special Edition Software
- Appendix A. Using the ExamGear Special Edition Software
- Exam Simulation
- Study Tools
- How ExamGear Special Edition Works
- Installing ExamGear Special Edition
- Using ExamGear Special Edition
- Contacting Que Certification
- License
- Software and Documentation
- License Term and Charges
- Title
- Updates
- Limited Warranty and Disclaimer
- Limitation of Liability
- Miscellaneous
- U.S. Government Restricted Rights
EAN: 2147483647
Pages: 247
