Network Security Promotes Good Network Design
Although it happens far less often now, I still occasionally sit down with a customer who says, "OK, the network design is done, now we need to think about security. We're certain we need a firewall and have also heard something about IDS."
Designing secure networks in this manner puts you on a fast track to a network design in which the security is tacked on, interferes with the performance of the network, and is viewed by the rest of the Information Technology (IT) staff as a necessary evil and a burden to the operation of the network. Although it is true that security generally isn't "free" from a network design perspective, if you design it from the beginning, it can achieve a balance with the rest of the network infrastructure. This improves not only the security of your network but also its reliability and scalability.
Let's consider a very basic example. Suppose you must provide connectivity between a data center, a group of users, and a remote company accessing your network over an extranet connection. Without thought to security, your network design might resemble the network shown in Figure 1-2.
Figure 1-2. No Security Example
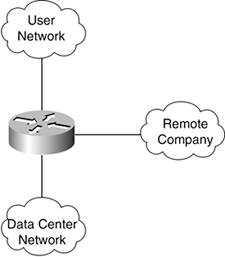
Along comes the information security (INFOSEC) representative who says, "Whoa! What are you doing connecting this other company right into our data center? We need some security here." So, you wind up adding a software firewall to the router with a series of ACLs to control traffic flows between the remote company and the data center. With the router taking on the added burden of software firewalling, its CPU starts to increase in utilization. This causes performance degradation not only between the remote company and the data center, but between the users and the data center as well. Here you see network security not promoting good network design but rather impacting the network design. Even if you fast-forward into the future of wire-speed firewalls and crypto in every device, the operational complexity introduced by having disparate systems connected through the same system is not trivial.
If you back up and redo the design while thinking about the security risks, you might wind up with a network resembling the one in Figure 1-3.
Figure 1-3. Design with Security
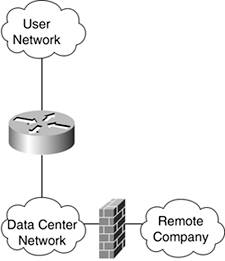
The network shown in Figure 1-3 is a gross oversimplification, of course, but hopefully it gets the point across. In this example, a separate firewall is installed between the remote company and the data center that can provide better controls with less performance impact, simplified operations, and, best of all, it in no way affects the communication between the users and the data center.
When you get further into the book, you will see much more complex examples of secure network designs. As you increase the number of variables from a security and networking standpoint, this problem only amplifies. The easiest way to ensure consistent and predictable security throughout your organization is to think about it right when you are in the design phase of the network as a whole. Unfortunately, if you've inherited an existing network that requires security improvements, this isn't always easy.
When you have a preexisting network that has little or no network security, the most effective way to improve its security is to logically divide the network into functional modules. Then improve each module individually, focusing on the area of greatest weakness. Don't be afraid to take a more comprehensive redesign of these smaller areas. Tacking on bits of security here and there to avoid readdressing IP ranges or other burdensome tasks usually creates more work in the long run once you determine that the tacked-on security isn't getting the job done. These topics receive much attention throughout the book.
To sum up, thinking about network security after you've designed the network impacts the network design. Considering security from the beginning promotes good network design. Finally, if you have an existing insecure network design, logically divide it into smaller modules and then improve the security of each area one at a time, starting with your area of greatest weakness.
Part I. Network Security Foundations
Network Security Axioms
- Network Security Axioms
- Network Security Is a System
- Business Priorities Must Come First
- Network Security Promotes Good Network Design
- Everything Is a Target
- Everything Is a Weapon
- Strive for Operational Simplicity
- Good Network Security Is Predictable
- Avoid Security Through Obscurity
- Confidentiality and Security Are Not the Same
- Applied Knowledge Questions
Security Policy and Operations Life Cycle
- Security Policy and Operations Life Cycle
- You Cant Buy Network Security
- What Is a Security Policy?
- Security System Development and Operations Overview
- References
- Applied Knowledge Questions
Secure Networking Threats
- Secure Networking Threats
- The Attack Process
- Attacker Types
- Vulnerability Types
- Attack Results
- Attack Taxonomy
- References
- Applied Knowledge Questions
Network Security Technologies
- Network Security Technologies
- The Difficulties of Secure Networking
- Security Technologies
- Emerging Security Technologies
- References
- Applied Knowledge Questions
Part II. Designing Secure Networks
Device Hardening
- Device Hardening
- Components of a Hardening Strategy
- Network Devices
- NIDS
- Host Operating Systems
- Applications
- Appliance-Based Network Services
- Rogue Device Detection
- References
- Applied Knowledge Questions
General Design Considerations
- General Design Considerations
- Physical Security Issues
- Layer 2 Security Considerations
- IP Addressing Design Considerations
- ICMP Design Considerations
- Routing Considerations
- Transport Protocol Design Considerations
- DoS Design Considerations
- References
- Applied Knowledge Questions
Network Security Platform Options and Best Deployment Practices
Common Application Design Considerations
- Common Application Design Considerations
- DNS
- HTTP/HTTPS
- FTP
- Instant Messaging
- Application Evaluation
- References
- Applied Knowledge Questions
Identity Design Considerations
- Identity Design Considerations
- Basic Foundation Identity Concepts
- Types of Identity
- Factors in Identity
- Role of Identity in Secure Networking
- Identity Technology Guidelines
- Identity Deployment Recommendations
- References
- Applied Knowledge Questions
IPsec VPN Design Considerations
- IPsec VPN Design Considerations
- VPN Basics
- Types of IPsec VPNs
- IPsec Modes of Operation and Security Options
- Topology Considerations
- Design Considerations
- Site-to-Site Deployment Examples
- IPsec Outsourcing
- References
- Applied Knowledge Questions
Supporting-Technology Design Considerations
- Supporting-Technology Design Considerations
- Content
- Load Balancing
- Wireless LANs
- IP Telephony
- References
- Applied Knowledge Questions
Designing Your Security System
- Designing Your Security System
- Network Design Refresher
- Security System Concepts
- Impact of Network Security on the Entire Design
- Ten Steps to Designing Your Security System
- Applied Knowledge Questions
Part III. Secure Network Designs
Edge Security Design
- Edge Security Design
- What Is the Edge?
- Expected Threats
- Threat Mitigation
- Identity Considerations
- Network Design Considerations
- Small Network Edge Security Design
- Medium Network Edge Security Design
- High-End Resilient Edge Security Design
- Provisions for E-Commerce and Extranet Design
- References
- Applied Knowledge Questions
Campus Security Design
- Campus Security Design
- What Is the Campus?
- Campus Trust Model
- Expected Threats
- Threat Mitigation
- Identity Considerations
- Network Design Considerations
- Small Network Campus Security Design
- Medium Network Campus Security Design
- High-End Resilient Campus Security Design
- References
- Applied Knowledge Questions
Teleworker Security Design
- Teleworker Security Design
- Defining the Teleworker Environment
- Expected Threats
- Threat Mitigation
- Identity Considerations
- Network Design Considerations
- Software-Based Teleworker Design
- Hardware-Based Teleworker Design
- Design Evaluations
- Applied Knowledge Questions
Part IV. Network Management, Case Studies, and Conclusions
Secure Network Management and Network Security Management
- Secure Network Management and Network Security Management
- Utopian Management Goals
- Organizational Realities
- Protocol Capabilities
- Tool Capabilities
- Secure Management Design Options
- Network Security Management Best Practices
- References
- Applied Knowledge Questions
Case Studies
- Case Studies
- Introduction
- Real-World Applicability
- Organization
- NetGamesRUs.com
- University of Insecurity
- Black Helicopter Research Limited
- Applied Knowledge Questions
Conclusions
- Conclusions
- Introduction
- Management Problems Will Continue
- Security Will Become Computationally Less Expensive
- Homogeneous and Heterogeneous Networks
- Legislation Should Garner Serious Consideration
- IP Version 6 Changes Things
- Network Security Is a System
References
Appendix A. Glossary of Terms
Appendix B. Answers to Applied Knowledge Questions
Appendix C. Sample Security Policies
INFOSEC Acceptable Use Policy
Password Policy
Guidelines on Antivirus Process
Index
EAN: 2147483647
Pages: 249
- Chapter IV How Consumers Think About Interactive Aspects of Web Advertising
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter XIV Product Catalog and Shopping Cart Effective Design
- Chapter XVIII Web Systems Design, Litigation, and Online Consumer Behavior
