11g Components
g Components
802.11g is really several physical layer specifications in one. It adds one umbrella clause for the Extended Rate PHY (ERP). However, there are several different "flavors" of ERP:
ERP-DSSS and ERP-CCK
These modes are backwards compatible with the original direct sequence specification (1 Mbps and 2 Mbps) described in Chapter 11, as well as the 802.11b enhancements (5.5 Mbps and 11 Mbps) described in Chapter 12. To retain backwards compatibility, a few minor changes are required.
ERP-OFDM
This is the major mode of 802.11g. It is essentially running 802.11a in the ISM frequency band (2.4 GHz), with a few minor changes to provide backwards compatibility. It supports the same speeds as 802.11a: 6, 9, 12, 18, 24, 36, 48, and 54 Mbps. Speeds of 6, 12, and 24 Mbps are mandatory.
ERP-PBCC
This is an optional extension to the PBCC standard provided in 802.11b, and provides data rates of 22 Mbps and 33 Mbps. Although it is part of the standard, it is not implemented by most major chipsets in the market, and is not widely used.
DSSS-OFDM
This a hybrid scheme, which encodes packet data using the DSSS headers, and OFDM encoding of the payload. Part of the reason for developing this implementation was for backwards compatibility. Although the body is OFDM-modulated and unintelligible to 802.11b, information in the headers is able to provide information on the duration of the packet. It is optional, and not widely implemented.
Any device that implements 802.11g is required to support a few mandatory modes. For backwards compatibility, 802.11g devices must support DSSS modulation (802.11) at 1 and 2 Mbps, and CCK modulation (802.11b) at 5.5 and 11 Mbps. Basic OFDM support is required, and all 802.11g stations are further required to support OFDM modulation at 6, 12, and 24 Mbps.
Compatibility Changes
The mandatory modes in 802.11g are slight modifications of existing physical layers, with a few minor alterations made for backwards compatibility. The modifications required of 802.11g stations assist coexistence with older implementations. They are not changes to the existing specifications. An 802.11b card will work as it always has. The only difference is that an 802.11g card will have a few features not present in 802.11b.
802.11b devices implement two different specifications: the original, slow direct sequence (DSSS) from the initial 802.11 standard, and the high-rate complementary code keying (CCK) PHY from 802.11b. 802.11g adopts both of those standards, and makes only a few minor changes. Naturally, any 802.11g station must be able to hear not only older stations but other 802.11g stations, so any 802.11g-compliant station must support all the preambles and synchronization found in 802.11g. More significantly, 802.11g stations must support the short preamble because it helps a great deal in maintaining high throughput. 802.11g radios are required to be more sensitive to signals as well.
802.11g devices must also implement ERP-OFDM, which is based heavily on 802.11a. In fact, it looks almost exactly like 802.11a, with a few obvious changes. Most notably, 802.11g adopts the frequency plan of 802.11b, so there are still only three ostensibly nonoverlapping channels for use. (See Chapter 13 for the adjacent-channel overlap map; the same note about three mostly nonoverlapping channels applies to 802.11g as well.) It also uses interframe spacing and slot times that are compatible with older ISM-band 802.11 stations. Regulatory structures may be different around 802.11g and 802.11b, however. Japan allows 802.11b operation in channels 1-14, but 802.11g is only allowed on channels 1-13.
Protection
One of the major differences between 802.11b and 802.11g is protection, which is required because of an asymmetry between the chipsets that implement the specifications. One of the problems faced by the designers of 802.11g is that it uses a different modulation scheme than 802.11b. 802.11g chips are built with backwards compatibility, and have no problem receiving and decoding an 802.11b signal. As is normally the case in technology, the converse is not true. 802.11b chipsets have no way of making sense of the higher-speed 802.11g transmissions. Part of the solution is to require that 802.11g stations transmit at a rate supported by all stations in basic service set. If an AP is to serve both 802.11b and 802.11g stations, it will need to send Beacon frames at a frame data rate of no higher than 11 Mbps.
The second part of the solution is to avoid interference between 802.11g and 802.11b networks. To ensure that 802.11b stations are aware of 802.11g transmissions, 802.11g specifies a protection mechanism to "protect" 802.11b stations from interference. The basic operation of the protection mechanism is shown in Figure 14-1. To avoid interference during the transmission of the OFDM frame and its acknowledgment, a slower frame is sent to update the NAV. There are two main protection modes. More commonly, 802.11g stations will use CTS-to-self protection, as shown in Figure 14-1 (a). When a station has a frame for transmission that needs protection, it will transmit a CTS frame with a receiver address of its own MAC address; that is, the destination of the CTS frame is the station itself. In the CTS, it will update the Network Allocation Vector (NAV) to tell other stations using the physical medium that it will be using the radio link for the time necessary to transmit the CTS, the OFDM-modulated frame, and an OFDM-modulated acknowledgment. Although the station sends the CTS to itself, all stations on the network are required to listen to CTS frames and update the NAV accordingly. The CTS frame is sent at the maximum speed it can be, using a modulation that can be received by all stations. Throughput may suffer a significant hit as a result of this exchange. A maximum Ethernet-size data frame and its acknowledgment require 294 microseconds at the highest speed, but the CTS to clear out the network requires at least 107 microseconds, and possibly more than 200 microseconds if long preambles are in use.
Figure 14-1 (b) shows the second mechanism, which is a full RTS/CTS exchange. Full RTS/CTS exchanges are more robust against hidden nodes, but come with a cost in network capacity. As in the CTS-to-self case, the compatibility frames used to reserve the medium may be have a transmission time comparable to or longer than the data. Both the RTS and CTS frames will take 100 microseconds, while a maximum-size data frame and its ACK only require 300 microseconds. Based on calculations of the time required for the extra RTS, I estimate that the use of full RTS/CTS exchanges versus CTS-to-self to be a reduction of approximately one third in overall data throughput.[*]
[*] See "When is 54 Not Equal to 54: An Analysis of 802.11g Throughput" at http://www.oreillynet.com/pub/a/wireless/2003/08/08/wireless_throughput.html.
Figure 14-1. Basic overview of protection mechanism
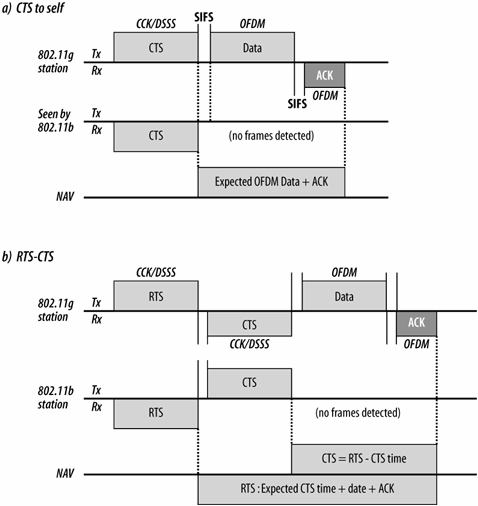
To ensure that the protection frames are received and processed by all stations on the network, protection frames are transmitted using 802.11b rules. They may be transmitted using phase shift keying at 1 Mbps or 2 Mbps, or CCK at 5.5 Mbps or 11 Mbps. Any 802.11b station will be able to understand these modulations, and can update its virtual carrier sense accordingly. Figure 14-1 shows this by labeling the transmission modulation, and only showing the compatible modulations as received by an 802.11b station.
|
Protection is activated whenever there is a need to ensure 802.11g stations do not interfere with 802.11b stations. One obvious case in which this happens is when an 802.11b station associates with an AP. All the 802.11g stations associated with the AP will then start using protection to ensure that the 802.11b station does not suffer from or cause interference. Protection is also activated in the less obvious case of a co-channel AP with 802.11b-only traffic. Because the two co-channel APs share the same physical medium, an 802.11b station using the same channel on a different AP also triggers protection.
Protection is controlled through the ERP information element in Beacon frames. 802.11g adds a Use Protection bit in to an information element in the Beacon. When the bit is set, stations must use protection. When a non-802.11g-capable station associates to a wireless LAN, the protection bit will be set. The station responsible for sending the Beacon is also responsible for deciding whether to activate protection. In infrastructure networks, the protection activation is handled by the access points; in independent networks, it is the Beacon generator. Protection is activated when a non-802.11g station associates with the network, as well as when non-802.11g-capable stations are transmitting in the area. Non-802.11g-capable stations may be deduced by the reception of a management frames, including Beacons and Probe Responses, from an overlapping network that does not indicate the data rates supported by 802.11g.
Beacons in 802.11g networks can also control the preamble length for protection purposes. In the ERP information element, the Barker Preamble Mode bit can be used to tell associated stations whether to use the long preamble or short preamble. If all the stations associated to a network are capable of short preambles, the Barker Preamble Mode bit will be set to zero, and all stations will use short preambles for efficiency. Once a station that is not capable of short preambles associates with the network, however, the bit will be set to one, and all protection frames will use long preambles.
As with most other technology that is required to be backwards compatible, 802.11g can suffer for it. If protection is not enabled, 802.11a and 802.11g throughput is identical. Once protection is activated, however, my calculations showed it to be very roughly 50%, depending on the ratio of TCP data segments to TCP ACKs. Transmitting a full-size 1,500 byte Ethernet frame over 802.11 requires 428 microseconds for both the frame and the 802.11 acknowledgment. When CTS-to-self protection is used, the transmission time jumps to 557 microseconds; RTS/CTS adds further bloat, and requires 774 microseconds for the same transmission. Avoiding the need for protection is one of the reasons that many 802.11g access points offer the ability to accept associations from 802.11g-capable stations only. By shunning stations that are not capable of 802.11g speeds, there is an increased probability that protection can remain disabled. Of course, a station that is shunned may very well find a different network that can accommodate it on the same channel, which would still trigger the activation of protection.
|
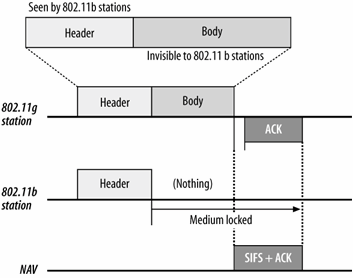
Protection is not required for the ERP-PBCC and DSSS-OFDM physical layers. As shown in Figure 14-2, both of them begin with an 802.11b-compatible header, and therefore the virtual carrier sense and NAV are updated without needing to send extra frames. An 802.11b station will receive the header and update the virtual carrier sensing mechanism based on the contents of the header. No transmissions will be allowed until the medium lock expires. Although the 802.11b station cannot detect the body of the frame, it is prevented from interference by the header. There is a cost to using ERP-PBCC or DSSS-OFDM. In a sense, they are always using protection because they use a much slower header. Both ERP-PBCC and DSSS-OFDM have, at minimum, 96 microsecond headers that can never be dropped. In contrast, the common ERP-OFDM mode must use the same header on a CTS frame that takes 107 microseconds to transmit, plus a 10 microsecond SIFS gap. However, ERP-OFDM needs to pay the penalty only when protection is required, while the optional modes always need to suffer the hit.
Figure 14-2. ERP-PBCC and DSSS-OFDM frame format
Introduction to Wireless Networking
- Introduction to Wireless Networking
- Why Wireless?
- What Makes Wireless Networks Different
- A Network by Any Other Name...
Overview of 802.11 Networks
- Overview of 802.11 Networks
- IEEE 802 Network Technology Family Tree
- 11 Nomenclature and Design
- 11 Network Operations
- Mobility Support
11 MAC Fundamentals
- 11 MAC Fundamentals
- Challenges for the MAC
- MAC Access Modes and Timing
- Contention-Based Access Using the DCF
- Fragmentation and Reassembly
- Frame Format
- Encapsulation of Higher-Layer Protocols Within 802.11
- Contention-Based Data Service
- Frame Processing and Bridging
11 Framing in Detail
- 11 Framing in Detail
- Data Frames
- Control Frames
- Management Frames
- Frame Transmission and Association and Authentication States
Wired Equivalent Privacy (WEP)
- Wired Equivalent Privacy (WEP)
- Cryptographic Background to WEP
- WEP Cryptographic Operations
- Problems with WEP
- Dynamic WEP
User Authentication with 802.1X
- User Authentication with 802.1X
- The Extensible Authentication Protocol
- EAP Methods
- 1X: Network Port Authentication
- 1X on Wireless LANs
11i: Robust Security Networks, TKIP, and CCMP
- 11i: Robust Security Networks, TKIP, and CCMP
- The Temporal Key Integrity Protocol (TKIP)
- Counter Mode with CBC-MAC (CCMP)
- Robust Security Network (RSN) Operations
Management Operations
- Management Operations
- Management Architecture
- Scanning
- Authentication
- Preauthentication
- Association
- Power Conservation
- Timer Synchronization
- Spectrum Management
Contention-Free Service with the PCF
- Contention-Free Service with the PCF
- Contention-Free Access Using the PCF
- Detailed PCF Framing
- Power Management and the PCF
Physical Layer Overview
- Physical Layer Overview
- Physical-Layer Architecture
- The Radio Link
- RF Propagation with 802.11
- RF Engineering for 802.11
The Frequency-Hopping (FH) PHY
- The Frequency-Hopping (FH) PHY
- Frequency-Hopping Transmission
- Gaussian Frequency Shift Keying (GFSK)
- FH PHY Convergence Procedure (PLCP)
- Frequency-Hopping PMD Sublayer
- Characteristics of the FH PHY
The Direct Sequence PHYs: DSSS and HR/DSSS (802.11b)
- The Direct Sequence PHYs: DSSS and HR/DSSS (802.11b)
- Direct Sequence Transmission
- Differential Phase Shift Keying (DPSK)
- The Original Direct Sequence PHY
- Complementary Code Keying
- High Rate Direct Sequence PHY
11a and 802.11j: 5-GHz OFDM PHY
- 11a and 802.11j: 5-GHz OFDM PHY
- Orthogonal Frequency Division Multiplexing (OFDM)
- OFDM as Applied by 802.11a
- OFDM PLCP
- OFDM PMD
- Characteristics of the OFDM PHY
11g: The Extended-Rate PHY (ERP)
- 11g: The Extended-Rate PHY (ERP)
- 11g Components
- ERP Physical Layer Convergence (PLCP)
- ERP Physical Medium Dependent (PMD) Layer
A Peek Ahead at 802.11n: MIMO-OFDM
11 Hardware
- 11 Hardware
- General Structure of an 802.11 Interface
- Implementation-Specific Behavior
- Reading the Specification Sheet
Using 802.11 on Windows
11 on the Macintosh
Using 802.11 on Linux
- Using 802.11 on Linux
- PCMCIA Support on Linux
- Linux Wireless Extensions and Tools
- Agere (Lucent) Orinoco
- Atheros-Based cards and MADwifi
- 1X on Linux with xsupplicant
Using 802.11 Access Points
- Using 802.11 Access Points
- General Functions of an Access Point
- Power over Ethernet (PoE)
- Selecting Access Points
- Cisco 1200 Access Point
- Apple AirPort
Logical Wireless Network Architecture
- Logical Wireless Network Architecture
- Evaluating a Logical Architecture
- Topology Examples
- Choosing Your Logical Architecture
Security Architecture
- Security Architecture
- Security Definition and Analysis
- Authentication and Access Control
- Ensuring Secrecy Through Encryption
- Selecting Security Protocols
- Rogue Access Points
Site Planning and Project Management
- Site Planning and Project Management
- Project Planning and Requirements
- Network Requirements
- Physical Layer Selection and Design
- Planning Access-Point Placement
- Using Antennas to Tailor Coverage
11 Network Analysis
11 Performance Tuning
Conclusions and Predictions
EAN: 2147483647
Pages: 179

