Frame Processing and Bridging
At the core, a wireless access point is a glorified bridge that translates frames between a wireless medium and a wired medium. Although 802.11 does not place any constraint on the wired medium's technology, I am not aware of an access point that does not use Ethernet. Most access points are designed as 802.11-to-Ethernet bridges, so it is important to understand the way that frames are transferred between the two media. See Figure 3-22.
Figure 3-22. Translating frames between a wireless and a wired medium
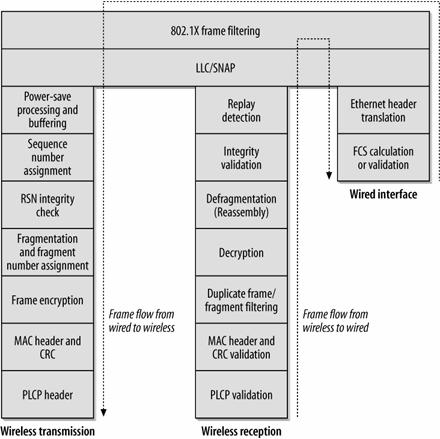
Wireless Medium to Wired Medium (802.11 to Ethernet)
When a frame is received on the wireless interface of an access point bound for the wired network, the access point must bridge the frame between the two media. Informally, this is the series of tasks performed by the access point:
- When a frame is received at the access point, it first checks for basic integrity. Physical layer headers that are discussed in the chapters for their respective physical layers are checked, and the FCS on the 802.11 frame is validated.
- After verifying that the frame was likely received without error, the access point checks whether it should process the frame further.
- Frames sent to an access point have the MAC address of the AP (the BSSID) in the Address 1 field of the 802.11 MAC header. Frames that do not match the BSSID of the AP should be discarded. (This step is not implemented by many products.)
- The 802.11 MAC detects and removes duplicate frames. Frames may be duplicated for a variety of reasons, but one of the most common is that the 802.11 acknowledgment is lost or corrupted in transit. To simplify higher-level processing, the 802.11 MAC is responsible for filtering out duplicate frames.
- Once the access point determines the frame should be processed further, it must decrypt frames protected by a link layer security algorithm. Details of the decryption can be found in subsequent chapters on security.
- Once the frame is successfully decrypted, it is checked to see if it is a constituent fragment of a larger frame that requires reassembly. Reassembled frames are subject to integrity protection on the whole reassembled unit, rather than the individual components.
- If the AP should bridge the frame, as determined by the BSSID check in step 2a, the relatively complex wireless MAC header is translated into the simple Ethernet MAC header.
- The destination address, which is found in the Address 3 field of the 802.11 MAC header, is copied to the Ethernet destination address.
- The source address, which is found in the Address 2 field of the 802.11 MAC header, is copied to the Ethernet source address.
- The Ethernet type code is copied from the SNAP header in the 802.11 Data field to the Type code in the Ethernet frame. If the Ethernet frame uses SNAP as well, the entire SNAP header can be copied.
- Sequence information is used in fragmentation reassembly, but is discarded when the frame is bridged.
- When quality of service processing is standardized, the QoS mapping from the wireless interface to the wired interface will occur here. For the moment, though, it sufficies to say that it may take the form of an 802.1p prioritization bit on the wired frame, or some other form of control.
- The FCS is recalculated. Both Ethernet and 802.11 use the same algorithm to calculate the FCS, but the 802.11 frame has several extra fields that are protected by the FCS.
- The new frame is transmitted on the Ethernet interface.
Wired Medium to Wireless Medium (Ethernet to 802.11)
Bridging frames from the wired side of an access point to the wireless medium is quite similar to the reverse process:
- After validating the Ethernet FCS, the access point first checks that a received frame should be processed further by checking that the destination address belongs to a station currently associated with the access point.
- The SNAP header is prepended to the data in the Ethernet frame. The higher-level packet is encapsulated within a SNAP header whose Type code is copied from the Ethernet type code. If the Ethernet frame uses SNAP as well, the entire SNAP header can be copied.
- The frame is scheduled for transmission. 802.11 includes complex powersaving operations that may cause an access point to hold the frame in a buffer before placing it on the transmit queue. Powersaving operations are described in Chapter 8.
- Once a frame has been queued for transmission, it is assigned a sequence number. The resulting data is protected by an integrity check, if required. If fragmentation is required, the frame will be split according to the configured fragmentation threshold. If the frame is fragmented, fragment numbers in the Sequence Control field will also be assigned.
- If frame protection is required, the body of the frame (or each fragment) is encrypted.
- The 802.11 MAC header is constructed from the Ethernet MAC header.
- The Ethernet destination address is copied to the Address 1 field of the 802.11 MAC header.
- The BSSID is placed in the Address 2 field of the MAC header, as the sender of the frame on the wireless medium.
- The source address of the frame is copied to the Address 3 field of the MAC header.
- Other fields in the 802.11 MAC header are filled in. The expected transmission time will be placed in the Duration field and the appropriate flags are filled in in the Frame Control field.
- The FCS is recalculated. Both Ethernet and 802.11 use the same algorithm to calculate the FCS, but the 802.11 frame has several extra fields that are protected by the FCS.
- The new frame is transmitted on the 802.11 interface.
Quality of Service Extensions
Quality of service extensions may affect the order in which frames are transmitted, but it does not alter the basic path that a frame takes through the 802.11 MAC. Rather than using a single transmit queue, the 802.11e quality of service extensions will have multiple transmit queues operating at steps 4, 5, and 7 of the wired-to-wireless bridging procedure described above. At each of those steps, frames are processed in a priority order that can be affected by the contents of the frame and locally configured prioritization rules.
Introduction to Wireless Networking
- Introduction to Wireless Networking
- Why Wireless?
- What Makes Wireless Networks Different
- A Network by Any Other Name...
Overview of 802.11 Networks
- Overview of 802.11 Networks
- IEEE 802 Network Technology Family Tree
- 11 Nomenclature and Design
- 11 Network Operations
- Mobility Support
11 MAC Fundamentals
- 11 MAC Fundamentals
- Challenges for the MAC
- MAC Access Modes and Timing
- Contention-Based Access Using the DCF
- Fragmentation and Reassembly
- Frame Format
- Encapsulation of Higher-Layer Protocols Within 802.11
- Contention-Based Data Service
- Frame Processing and Bridging
11 Framing in Detail
- 11 Framing in Detail
- Data Frames
- Control Frames
- Management Frames
- Frame Transmission and Association and Authentication States
Wired Equivalent Privacy (WEP)
- Wired Equivalent Privacy (WEP)
- Cryptographic Background to WEP
- WEP Cryptographic Operations
- Problems with WEP
- Dynamic WEP
User Authentication with 802.1X
- User Authentication with 802.1X
- The Extensible Authentication Protocol
- EAP Methods
- 1X: Network Port Authentication
- 1X on Wireless LANs
11i: Robust Security Networks, TKIP, and CCMP
- 11i: Robust Security Networks, TKIP, and CCMP
- The Temporal Key Integrity Protocol (TKIP)
- Counter Mode with CBC-MAC (CCMP)
- Robust Security Network (RSN) Operations
Management Operations
- Management Operations
- Management Architecture
- Scanning
- Authentication
- Preauthentication
- Association
- Power Conservation
- Timer Synchronization
- Spectrum Management
Contention-Free Service with the PCF
- Contention-Free Service with the PCF
- Contention-Free Access Using the PCF
- Detailed PCF Framing
- Power Management and the PCF
Physical Layer Overview
- Physical Layer Overview
- Physical-Layer Architecture
- The Radio Link
- RF Propagation with 802.11
- RF Engineering for 802.11
The Frequency-Hopping (FH) PHY
- The Frequency-Hopping (FH) PHY
- Frequency-Hopping Transmission
- Gaussian Frequency Shift Keying (GFSK)
- FH PHY Convergence Procedure (PLCP)
- Frequency-Hopping PMD Sublayer
- Characteristics of the FH PHY
The Direct Sequence PHYs: DSSS and HR/DSSS (802.11b)
- The Direct Sequence PHYs: DSSS and HR/DSSS (802.11b)
- Direct Sequence Transmission
- Differential Phase Shift Keying (DPSK)
- The Original Direct Sequence PHY
- Complementary Code Keying
- High Rate Direct Sequence PHY
11a and 802.11j: 5-GHz OFDM PHY
- 11a and 802.11j: 5-GHz OFDM PHY
- Orthogonal Frequency Division Multiplexing (OFDM)
- OFDM as Applied by 802.11a
- OFDM PLCP
- OFDM PMD
- Characteristics of the OFDM PHY
11g: The Extended-Rate PHY (ERP)
- 11g: The Extended-Rate PHY (ERP)
- 11g Components
- ERP Physical Layer Convergence (PLCP)
- ERP Physical Medium Dependent (PMD) Layer
A Peek Ahead at 802.11n: MIMO-OFDM
11 Hardware
- 11 Hardware
- General Structure of an 802.11 Interface
- Implementation-Specific Behavior
- Reading the Specification Sheet
Using 802.11 on Windows
11 on the Macintosh
Using 802.11 on Linux
- Using 802.11 on Linux
- PCMCIA Support on Linux
- Linux Wireless Extensions and Tools
- Agere (Lucent) Orinoco
- Atheros-Based cards and MADwifi
- 1X on Linux with xsupplicant
Using 802.11 Access Points
- Using 802.11 Access Points
- General Functions of an Access Point
- Power over Ethernet (PoE)
- Selecting Access Points
- Cisco 1200 Access Point
- Apple AirPort
Logical Wireless Network Architecture
- Logical Wireless Network Architecture
- Evaluating a Logical Architecture
- Topology Examples
- Choosing Your Logical Architecture
Security Architecture
- Security Architecture
- Security Definition and Analysis
- Authentication and Access Control
- Ensuring Secrecy Through Encryption
- Selecting Security Protocols
- Rogue Access Points
Site Planning and Project Management
- Site Planning and Project Management
- Project Planning and Requirements
- Network Requirements
- Physical Layer Selection and Design
- Planning Access-Point Placement
- Using Antennas to Tailor Coverage
11 Network Analysis
11 Performance Tuning
Conclusions and Predictions
EAN: 2147483647
Pages: 179
- ERP System Acquisition: A Process Model and Results From an Austrian Survey
- Context Management of ERP Processes in Virtual Communities
- Distributed Data Warehouse for Geo-spatial Services
- Healthcare Information: From Administrative to Practice Databases
- Development of Interactive Web Sites to Enhance Police/Community Relations
