Operating System Hardening
One of the most important steps in securing an IP telephony server is installing all the applicable product or component security updates and then making sure that they are kept up to date. Cisco provides three types of updates for the Cisco IP Telephony Operating System:
- Operating system upgrade Comprehensive upgrade to all components of the operating system that is released two to three times a year, including Microsoft Windows 2000 SPs, Internet Explorer SPs, BIOS, firmware, drivers, Microsoft hot fixes, security configuration changes, third-party software that is installed in the base operating system, and configuration changes to match the currently shipping operating system version.
- Operating system service releases Primarily a comprehensive roll-up of security hot fixes that are released the third Tuesday of each month when needed to deliver new security hot fixes. The operating system service release occasionally contains nonsecurity hot fixes or configuration changes needed to resolve a defect in the operating system.
- Critical hot fixes When Microsoft releases a hot fix that is critical for Cisco IP telephony products, Cisco tests the hot fix and posts it to Cisco.com within one business day of the release by Microsoft.
An IP telephony server must be used for IP telephony purposes only. The server should not be used as a common file server that stores user data or has user applications, such as Microsoft Office products, installed on it. File-share access has to be limited to the absolute minimum needed (for instance, to access log files and generate reports). Strict file access control has to be deployed, and auditing of network file access should be enabled. This practice also eliminates the need to add user accounts to the server; only administrator and auditor accounts should exist. If network file access is not needed at all, it should be disabled to enhance the security of the server.
The more services that are running on a server, the more likely it is that vulnerabilities can be exploited by an attacker. To minimize this risk, only the services that are needed should be activated. Many services that are not needed have already been disabled in the Cisco hardened version of the Microsoft Windows 2000 Server operating system.
To make Cisco CallManager even more secure, Cisco provides additional security scripts and information on how to protect the Cisco IP Telephony Operating System against common threats.
Do not install any other application on the servers unless it is approved software, such as Cisco Security Agent or antivirus products. A hardened IP telephony server has to be stripped down to run only the services and applications that are needed for its operation.
IP Telephony Operating System Security Scripts
Cisco IP Telephony Operating System 2.6 and later includes scripts and information guides on additional security settings. These security guides and scripts provide additional security settings beyond those that are installed by default in the Cisco IP Telephony Operating System. The settings in the optional security script have not been included by default and are not intended for all customers to use. When planning to use the optional security script, consider these points:
- The optional security script settings are supported only for Windows 2000 servers that are running Cisco CallManager Release 3.3(2) and later.
- The optional security script settings might have an adverse impact on some of the other Cisco IP telephony applications that use this operating system, on the interaction between Cisco CallManager servers and some other Cisco IP telephony applications, and on some supported third-party software.
- Because these settings are not installed by default, they receive only a limited amount of testing.
- Only experienced Windows administrators should apply the optional security script or manual settings.
Caution
Applying the optional security script can destroy collocated applications, such as Cisco IPCC Express, Cisco IP IVR, and Cisco IP Queue Manager (IP QM)!
As shown in Figure 20-2, the optional security script and some additional information are available in the C:utilsSecurityTemplates folder.
Figure 20-2. CallManager Security Script Templates
The script file is a batch job that can be started by clicking the CCM-OS-OptionalSecurity.cmd file. Before doing so, read the CCM-OS-OptionalSecurity-Readme.htm file to identify possible issues with applications running on the operating system:
- The CCM-OS-OptionalSecurity-Readme.htm file contains information on what the CCM-OS-OptionalSecurity script is changing in the operating system and provides additional security settings that can be configured manually.
- Some of the optional security settings cause upgrades to fail. Therefore, if the Cisco IP Telephony Operating System optional security settings have been installed on the server and you want to upgrade the server, read the "Before CallManager Upgrade" guide. It includes a checklist of all settings to which you must revert for the upgrade to work.
In addition, Cisco has provided an additional security script in the C:utils directory, shown in Figure 20-3. This script is called the IP security filter and will block the fixed Windows 2000 and SQL ports. Read the IPSec-W2KSQL-Readme.htm file for instructions on how to use the IP security filter.
Figure 20-3. CallManager SQL Security Script Template
The security script provides the following benefits:
- Blocking the fixed Windows 2000 and SQL ports adds an extra layer of protection from viruses, worms, and hackers. A provided script eases the creation of the IP security filter. You must customize the script with the IP addresses that the organization wants to allow through the filter. For example, the Cisco CallManager uses SQL ports allowing every IP address to connect to these port numbers. The IPSec-W2KSQL script would allow SQL connections only from the IP addresses defined in the script. These consist mostly of the other Cisco CallManager servers in the cluster and applications that need direct access to the database, for example, to the call detail record (CDR) tables.
- Using this IP security filter increases the management overhead of the servers. If the IP infrastructure changes or additional servers are added to the Cisco IP telephony solution, the permit lists on all the servers will need to be updated.
Note
The name of the IPSec-W2kSQL file has nothing to do with the IPsec virtual private network (VPN) umbrella standard.
File-Sharing Considerations
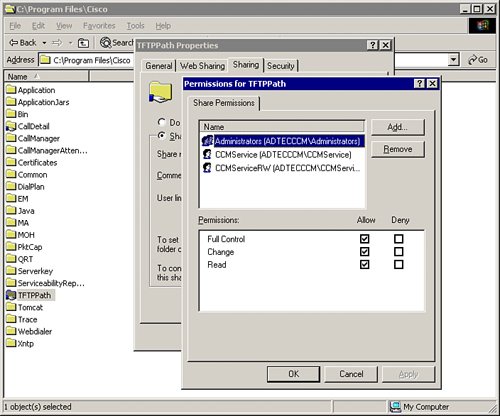
To secure the access to file shares, limit access to the absolute minimum number of users who need it, as shown in Figure 20-4. Check the share permissions on all shared folders, for example, the CDR and TFTPPath folders. Avoid assigning share permissions for the Everyone group. You can find detailed information on how to secure file shares in the CCM-OS-OptionalSecurity-Readme guide, located in the folder C:UtilsSecurityTemplates.
Figure 20-4. Managing CallManager Share Permissions
Part I: Cisco CallManager Fundamentals
Introduction to Cisco Unified Communications and Cisco Unified CallManager
Cisco Unified CallManager Clustering and Deployment Options
- Cisco Unified CallManager Clustering and Deployment Options
- The Two Sides of the Cisco Unified CallManager Cluster
- Cluster Redundancy Designs
- Call-Processing Deployment Models
- Summary
- Review Questions
Cisco Unified CallManager Installation and Upgrades
- Cisco Unified CallManager Installation and Upgrades
- Cisco Unified CallManager 4.x Clean Installation Process
- Upgrading Prior Cisco Unified CallManager Versions
- Summary
- Review Questions
Part II: IPT Devices and Users
Cisco IP Phones and Other User Devices
Configuring Cisco Unified CallManager to Support IP Phones
- Configuring Cisco Unified CallManager to Support IP Phones
- Configuring Intracluster IP Phone Communication
- IP Phone Configuration
- Case Study: Device Pool Design
- Summary
- Review Questions
Cisco IP Telephony Users
- Cisco IP Telephony Users
- Cisco CallManager User Database
- Cisco CallManager User Configuration
- User Logon and Device Configuration
- Summary
- Review Questions
Cisco Bulk Administration Tool
- Cisco Bulk Administration Tool
- The Cisco Bulk Administration Tool
- Using the Tool for Auto-Registered Phone Support
- Summary
- Review Questions
Part III: IPT Network Integration and Route Plan
Cisco Catalyst Switches
- Cisco Catalyst Switches
- Catalyst Switch Role in IP Telephony
- Powering the Cisco IP Phone
- Data and Voice VLANs
- Configuring Class of Service
- Summary
- Review Questions
Configuring Cisco Gateways and Trunks
- Configuring Cisco Gateways and Trunks
- Cisco Gateway Concepts
- Configuring Access Gateways
- Cisco Trunk Concepts
- Configuring Intercluster Trunks
- SIP and Cisco CallManager
- Summary
- Review Questions
Cisco Unified CallManager Route Plan Basics
- Cisco Unified CallManager Route Plan Basics
- External Call Routing
- Route Plan Configuration Process
- Summary
- Review Questions
Cisco Unified CallManager Advanced Route Plans
- Cisco Unified CallManager Advanced Route Plans
- Route Filters
- Discard Digit Instructions
- Transformation Masks
- Translation Patterns
- Route Plan Report
- Summary
- Review Questions
Configuring Hunt Groups and Call Coverage
- Configuring Hunt Groups and Call Coverage
- Call Distribution Components
- Configuring Line Groups, Hunt Lists, and Hunt Pilots
- Summary
- Review Questions
Implementing Telephony Call Restrictions and Control
- Implementing Telephony Call Restrictions and Control
- Class of Service Overview
- Partitions and Calling Search Spaces Overview
- Time-of-Day Routing Overview
- Configuring Time-of-Day Routing
- Time-of-Day Routing Usage Scenario
- Summary
- Review Questions
Implementing Multiple-Site Deployments
- Implementing Multiple-Site Deployments
- Call Admission Control
- Survivable Remote Site Telephony
- Summary
- Review Questions
Part IV: VoIP Features
Media Resources
- Media Resources
- Introduction to Media Resources
- Conference Bridge Resources
- Media Termination Point Resources
- Annunciator Resources
- Transcoder Resources
- Music on Hold Resources
- Media Resource Management
- Summary
- Review Questions
Configuring User Features, Part 1
- Configuring User Features, Part 1
- Basic IP Phone Features
- Softkey Templates
- Enhanced IP Phone Features
- Barge and Privacy
- IP Phone Services
- Summary
- Review Questions
Configuring User Features, Part 2
- Configuring User Features, Part 2
- Cisco CallManager Extension Mobility
- Client Matter Codes and Forced Authentication Codes
- Call Display Restrictions
- Malicious Call Identification
- Multilevel Precedence and Preemption
- Summary
- Review Questions
Configuring Cisco Unified CallManager Attendant Console
- Configuring Cisco Unified CallManager Attendant Console
- Introduction to Cisco CallManager Attendant Console
- Call Routing and Call Queuing
- Server and Administration Configuration
- Cisco Attendant Console Features
- Summary
- Review Questions
Configuring Cisco IP Manager Assistant
- Configuring Cisco IP Manager Assistant
- Cisco IP Manager Assistant Overview
- Cisco IP Manager Assistant Architecture
- Configuring Cisco IPMA for Shared-Line Support
- Summary
- Review Questions
Part V: IPT Security
Securing the Windows Operating System
- Securing the Windows Operating System
- Threats Targeting the Operating System
- Security and Hot Fix Policy
- Operating System Hardening
- Antivirus Protection
- Cisco Security Agent
- Administrator Password Policy
- Common Windows Exploits
- Security Taboos
- Summary
- Review Questions
Securing Cisco Unified CallManager Administration
- Securing Cisco Unified CallManager Administration
- Threats Targeting Remote Administration
- Securing CallManager Communications Using HTTPS
- Multilevel Administration
- Summary
- Review Questions
Preventing Toll Fraud
- Preventing Toll Fraud
- Toll Fraud Exploits
- Preventing Call Forward and Voice-Mail Toll Fraud Using Calling Search Spaces
- Blocking Commonly Exploited Area Codes
- Using Time-of-Day Routing
- Using FAC and CMC
- Restricting External Transfers
- Dropping Conference Calls
- Summary
- Review Questions
Hardening the IP Phone
Understanding Cryptographic Fundamentals
- Understanding Cryptographic Fundamentals
- What Is Cryptography?
- Symmetric Encryption
- Asymmetric Encryption
- Hash Functions
- Digital Signatures
- Summary
- Review Questions
Understanding the Public Key Infrastructure
- Understanding the Public Key Infrastructure
- The Need for a PKI
- PKI as a Trusted Third-Party Protocol
- PKI Entities
- PKI Enrollment
- PKI Revocation and Key Storage
- PKI Example
- Summary
- Review Questions
Understanding Cisco IP Telephony Authentication and Encryption Fundamentals
- Understanding Cisco IP Telephony Authentication and Encryption Fundamentals
- Threats Targeting the IP Telephony System
- How CallManager Protects Against Threats
- PKI Topologies in Cisco IP Telephony
- PKI Enrollment in Cisco IP Telephony
- Keys and Certificate Storage in Cisco IP Telephony
- Authentication and Integrity
- Encryption
- Summary
- Review Questions
Configuring Cisco IP Telephony Authentication and Encryption
- Configuring Cisco IP Telephony Authentication and Encryption
- Authentication and Encryption Configuration Overview
- Enabling Services Required for Security
- Using the CTL Client
- Working with Locally Significant Certificates
- Configuring the Device Security Mode
- Negotiating Device Security Mode
- Generating a CAPF Report
- Summary
- Review Questions
Part VI: IP Video
Introducing IP Video Telephony
- Introducing IP Video Telephony
- IP Video Telephony Solution Components
- Video Call Concepts
- Video Protocols Supported in Cisco CallManager
- Bandwidth Management
- Call Admission Control Within a Cluster
- Call Admission Control Between Clusters
- Summary
- Review Questions
Configuring Cisco VT Advantage
- Configuring Cisco VT Advantage
- Cisco VT Advantage Overview
- How Calls Work with Cisco VT Advantage
- Configuring Cisco CallManager for Video
- Configuring Cisco IP Phones for Cisco VT Advantage
- Installing Cisco VT Advantage on a Client
- Summary
- Review Questions
Part VII: IPT Management
Introducing Database Tools and Cisco Unified CallManager Serviceability
- Introducing Database Tools and Cisco Unified CallManager Serviceability
- Database Management Tools
- Cisco CallManager Serviceability Overview
- Tools Overview
- Summary
- Review Questions
Monitoring Performance
- Monitoring Performance
- Performance Counters
- Microsoft Event Viewer
- Microsoft Performance Monitor
- Real-Time Monitoring Tool Overview
- Summary
- Review Questions
Configuring Alarms and Traces
- Configuring Alarms and Traces
- Alarm Overview
- Alarm Configuration
- Trace Configuration
- Trace Analysis
- Trace Collection
- Bulk Trace Analysis
- Additional Trace Tools
- Summary
- Review Questions
Configuring CAR
- Configuring CAR
- CAR Overview
- CAR Configuration
- Report Scheduling
- System Database Configuration
- User Report Configuration
- Summary
- Review Questions
Using Additional Management and Monitoring Tools
- Using Additional Management and Monitoring Tools
- Remote Management Tools
- Dependency Records
- Password Changer Tool
- Cisco Dialed Number Analyzer
- Quality Report Tool
- Summary
- Review Questions
Part VIII: Appendix
Appendix A. Answers to Review Questions
Index
EAN: 2147483647
Pages: 329
