Network Models and Standards
Network models and standards play an important role in the telecommunications industry. You have already seen how standards for services such as DSL, ATM, 802.11 wireless, Bluetooth, and others make it much easier for developers to design interoperable equipment, ease the burden of networking, and develop security solutions. Two of the most widely discussed network models are discussed in the following sections. In case you haven't guessed, these are the Open Systems Interconnect (OSI) model and the Transmission Control Protocol/Internet Protocol (TCP/IP) model.
OSI Model
The International Standards Organization (ISO) developed the Open Systems Interconnect (OSI) model in 1984. The model is based on a specific hierarchy in which each layer builds upon the output of each adjacent layer. It is described in ISO 7498. Today it is widely used as a guide in describing the operation of a networking environment. What was once considered the universal communications standard now serves as a teaching model for all other protocols.
The OSI model is designed so that control is passed down from layer to layer. Information is put into the application layer and ends at the physical layer. Then it is transmitted over the mediumwire, coax, wirelesstoward the target device and then back up the stack to the application. The seven layers of the OSI model are the application, presentation, session, transport, network, data link, and physical layers. Most people remember this order by using one of the many acronyms that have been thought up over the years. My favorite one is based on the popular television show American Idol: "People Don't Need To See Paula Abdul." For a better understanding of how the OSI model works, we'll start at the bottom of the stack and work our way up. The OSI model is shown on Figure 6.4.
Figure 6.4. OSI model.

Physical Layer
Layer 1 is known as the physical layer. At Layer 1, bit-level communication takes place. The bits have no defined meaning on the wire, but the physical layer defines how long each bit lasts and how it is transmitted and received. Physical-layer components include these:
- Copper cabling
- Fiber cabling
- Wireless system components
- Wall jacks and connectors
- Ethernet hubs
Data Link Layer
Layer 2 is known as the data link layer. It is focused on traffic within a single LAN. The data link layer is responsible for formatting and organizing the data before sending it to the physical layer. The data link layer organizes the data into frames. A frame is a logical structure in which data can be placed. When a frame reaches the target device, the data link layer is responsible for stripping off the data frame and passing the data packet up to the network layer. Data-linklayer components include these:
- Bridges
- Switches
- NIC cards
- MAC addresses
Network Layer
Layer 3 is known as the network layer. Whereas the bottom two layers of the OSI model are associated with hardware, the network layer is tied to software. This layer is concerned with how data moves from network A to network B; it makes sure frames from the data link layer reach the correct network. The network layer is the home of the Internet Protocol (IP), which acts as a postman in determining the best route from the source to the target network. Network-layer components include the following:
- Routers
- Firewalls/packet filters
Transport Layer
Layer 4 is known as the transport layer. Whereas the network layer routes information to its destination, the transport layer ensures completeness by handling end-to-end error recovery and flow control. Transport-layer protocols include these:
- TCP, a connection-oriented protocol. It provides reliable communication through the use of handshaking, acknowledgments, error detection, and session teardown.
- UDP (User Datagram Protocol), a connectionless protocol. It offers speed and low overhead as its primary advantage.
Session Layer
Layer 5 is known as the session layer. Its purpose is to allow two applications on different computers to establish and coordinate a session. A session is simply a name for a connection between two computers. When a data transfer is complete, the session layer is responsible for tearing down the session. Session-layer protocols include these:
- Remote Procedure Call
- Structured Query Language
Presentation Layer
Layer 6 is known as the presentation layer. The presentation layer performs a job similar to that of a waiter in a restaurant: Its main purpose is to deliver and present data to the application layer. In performing its job, the data must be formatted in a way that the application layer can understand and interpret the data. The presentation layer is skilled in translation because its duties include encrypting data, changing, or converting the character set and handling protocol conversion.
|
Encapsulation is the process of adding headers to user data as it is handed from each layer to the next lower layer. |
Application Layer
Layer 7 is known as the application layer. Recognized as the top layer of the OSI model, this layer serves as the window for application services. This is the layer we, as users, work with. We send email or surf the Web and many times never think about all the underling processes that make it possible. Layer 7 is not the application itself, but rather the channel through which applications communicate.
TCP/IP
TCP/IP is the foundation of the Internet as we know it today. Its roots can be traced back to standards adopted by the U.S. government's Department of Defense (DoD) in 1982. TCP/IP is similar to the OSI model, but it consists of only four layers: the network access layer, the Internet layer, the host-to-host layer, and the application layer.
It is of critical importance to remember that the TCP/IP model was originally developed as a flexible, fault-tolerant network. Security was not the driving concern. The network was designed to these specifications to withstand a nuclear strike that might destroy key routing nodes. The designers of this original network never envisioned the Internet we use today. Therefore, most of TCP/IP is insecure, and many of the security mechanisms in use today are add-ons to the original protocol suite.
Network Access Layer
The network access layer loosely corresponds to Layers 1 and 2 of the OSI model. Some literature separates this layer into two and references them as physical access and data link. Whether viewed as one layer or two, this portion of the TCP/IP network model is responsible for the physical delivery of IP packets via frames.
Ethernet is the most commonly used LAN frame type. Ethernet frames are addressed with MAC addresses, which identify the source and destination devices. MAC addresses are 6 bytes long and are unique to the NIC card in which they are burned. Programs are available that allow attackers to spoof MAC addresses.
Internet Layer
The Internet layer maps to OSI Layer 3. This layer contains the information needed to make sure that data can be routed through an IP network and that the network can differentiate hosts. Currently, most organizations use IPv4. IPv6 is its planned replacement, with better security and support for 128-bit IP addresses instead of the current 32-bit addresses. IPv4 uses a logical address scheme or IP address. Whereas MAC addresses are considered a physical address, an IP address is considered a logical address. IP addresses are laid out in dotted-decimal notation format. The IPv4 address format is four decimal numbers separated by decimal points. Each of these decimal numbers is 1 byte in length, to allow numbers to range from 0 to 255.
- Class A networks Consist of up to 16,777,214 client devices. Their address range can extend from 1 to 126.
- Class B networks Host up to 65,534 client devices. Their address range can extend from 128 to 191.
- Class C networks Can have a total of 245 devices. Their address range can extend from 192 to 223.
- Class D networks Reserved for multicasting. Their address range can extend from 224 to 239.
- Class E networks Reserved for experimental purposes. Their addresses range from 240 to 254.
Not all of the addresses shown can be used on the Internet. Some addresses are reserved for private use and are considered nonroutable. These addresses include the following:
- Class A: 10.0.0.0
- Class B: 172.16.0.0 to 172.31.0.0
- Class C: 192.168.0.0 to 192.168.255.0
IP security issues include fragmentation, source routing, and DoS attacks, such as a teardrop. The Internet layer contains not only the Internet Protocol (IP), but also Internet Control Message Protocol (ICMP), Address Resolution Protocol (ARP), and the Internet Group Management Protocol (IGMP). ICMP and IGMP are IP support, error, and diagnostic protocols that handle problems such as error messages and multicast messages. ARP is used to resolve unknown MAC addresses to known IP addresses.
|
IP addresses are required because physical addressees are tied to the physical topology used. Some LANs use Ethernet, but others are connected to ATM or Token Ring networks. Because no common format or structure exists, the IP protocol is used to bind these dissimilar networks together. |
Internet Control Message Protocol (ICMP)
One of the protocols residing at the Internet layer is ICMP. Its purpose is to provide feedback used for diagnostics or to report logical errors. Even though ICMP resides at the Internet layer, it is a separate protocol and is distinctly different from IP.
All ICMP messages follow the same basic format. The first byte of an ICMP header indicates the type of ICMP message. The following byte contains the code for each particular type of ICMP. Eight of the most common ICMP types are shown in Table 6.4.
|
Type |
Code |
Function |
|---|---|---|
|
0/8 |
0 |
Echo Response/Request (Ping) |
|
3 |
015 |
Destination Unreachable |
|
4 |
0 |
Source Quench |
|
5 |
03 |
Redirect |
|
11 |
01 |
Time Exceeded |
|
12 |
0 |
Parameter Fault |
|
13/14 |
0 |
Time Stamp Request/Response |
|
17/18 |
0 |
Subnet Mask Request/Response |
One of the most common ICMP types is a ping. Although ICMP can be very helpful, it is also valued by attackers and can be manipulated and used for a variety of attacks, including the ping of death, Smurf, timestamp query, netmask query, source routing, and redirects.
Address Resolution Protocol (ARP)
ARP's two-step resolution process is performed by first sending a broadcast message requesting the target's physical address. If a device recognizes the address as its own, it issues an ARP reply containing its MAC address to the original sender. The MAC address is then placed in the ARP cache and used to address subsequent frames. Proxy ARPs can be used to extend a network and allow one device to communicate with a device on an adjunct node. Attackers can manipulate ARP because it is a trusting protocol. Bogus ARP responses are accepted as valid, which can allow attackers to redirect traffic on a switched network. ARP attacks play a role in a variety of man-in-the middle attacks, spoofing, and session-hijack attacks.
|
Remember that ARP is unauthenticated. Therefore, an attacker can send unsolicited ARP replies, poison the ARP table, and spoof another host. |
Host-to-Host Layer
The host-to-host layer corresponds to OSI Layers 4 and 5. The host-to-host layer provides end-to-end delivery. Two primary protocols are located at the host-to-host layer: the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
TCP
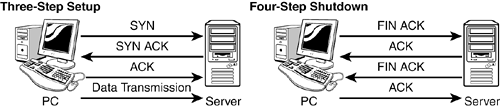
TCP enables two hosts to establish a connection and exchange data reliably. TCP does this by performing a three-step handshake before data is sent. During the data-transmission process, TCP guarantees delivery of data by using sequence and acknowledgment numbers. At the completion of the data-transmission process, TCP performs a four-step shutdown that gracefully concludes the session. At the heart of TCP is a 1-byte flag field. Flags help control the TCP process. Common flags include synchronize (SYN), acknowledgment (ACK), push (PSH), and finish (FIN). See Figure 6.5 for additional details on the flags and the startup/shutdown process. TCP security issues include TCP sequence number attacks, session hijacking, and SYN flood attacks.
Figure 6.5. TCP operation.
UDP
UDP performs none of the handshaking processes that we see performed with TCP. So although that makes it considerably less reliable than TCP, it does offer the benefit of speed. It is ideally suited for data that requires fast delivery and is not sensitive to packet loss but is easier to spoof by attackers because it does not use sequence and acknowledgment numbers. Figure 6.6 details the operation of UDP.
Figure 6.6. UDP operation.

Application Layer
The application layer sits at the top of the protocol stack and maps loosely to OSI Layers 6 and 7. This layer is responsible for application support. Applications are typically mapped not by name, but by their corresponding port. Ports are placed into TCP and UDP packets so the correct application can be passed to the required protocols. Although applications can be made to operate on nonstandard ports, the established port numbers serve as the de facto standard. There are approximately 65,000 ports, divided into well-known ports (01024), registered ports (102449151), and dynamic ports (4915265535). Some well-known applications and their associated ports are as follows:
- File Transfer Protocol (FTP) FTP is a TCP service and operates on ports 20 and 21. This application is used to move files from one computer to another. Port 20 is used for the data stream and transfers the data between the client and the server. Port 21 is the control stream and is used to pass commands between the client and the FTP server. Attacks on FTP target misconfigured directory permissions and compromised or sniffed clear-text passwords. FTP is one of the most commonly hacked services.
- Telnet Telnet is a TCP service that operates on port 23. Telnet enables a client at one site to establish a session with a host at another site. The program passes the information typed at the client's keyboard to the host computer system. Telnet can be configured to allow anonymous connections, but it should be configured to require usernames and passwords. Unfortunately, even then, Telnet sends them in clear text. When a user is logged in, he or she can perform any allowed task. Applications such as Secure Shell (SSH) should be considered as a replacement.
- Simple Mail Transfer Protocol (SMTP) This application is a TCP service that operates on port 25. It is designed for the exchange of electronic mail between networked systems. Messages sent through SMTP have two parts: an address header and the message text. All types of computers can exchange messages with SMTP. Spoofing and spamming are two of the vulnerabilities associated with SMTP.
- Domain Name Service (DNS) This application operates on port 53 and performs address translation. DNS converts fully qualified domain names (FQDNs) into numeric IP addresses, or IP addresses into FQDNs. This system works similar to a phone directory, which enables users to remember domain names (such as examcram2.com) instead of IP addresses (such as 114.112.18.23). DNS uses UDP for DNS queries and TCP for zone transfers. DNS is subject to poisoning and, if misconfigured, can be solicited to perform a full zone transfer.
- Trivial File Transfer Protocol (TFTP) TFTP operates on port 69. It is considered a down-and-dirty version of FTP because it uses UDP to cut down on overhead. It not only does so without the session management offered by TCP, but it also requires no authentication, which could pose a big security risk. It is used to transfer router-configuration files and to configure cable modems for cable companies.
- Hypertext Transfer Protocol (HTTP) HTTP is a TCP service that operates on port 80. This application is one of the most well known. HTTP has helped make the Web the popular protocol it is today. The HTTP connection model is known as a stateless connection. HTTP uses a request-response protocol in which a client sends a request and a server sends a response. Attacks that exploit HTTP can target the server, a browser, or scripts that run on the browser. Nimda is an example of code that targeted a web server.
- Simple Network Management Protocol (SNMP) SNMP is a UDP service and operates on ports 161 and 162. It was envisioned to be an efficient and inexpensive way to monitor networks. The SNMP protocol allows agents to gather information, including network statistics, and report back to their management stations. Most large corporations have implemented some type of SNMP management. Some of the security problems that plague SNMP are caused by the fact that community strings can be passed as clear text and that the default community strings (public/private) are well known. SNMP version 3 is the most current and offers encryption for more robust security.
The CISSP Cram Sheet
- PHYSICAL SECURITY
- SECURITY-MANAGEMENT PRACTICES
- ACCESS-CONTROL SYSTEMS AND METHODOLOGY
- SECURITY MODELS AND ARCHITECTURES
- TELECOMMUNICATIONS AND NETWORK SECURITY
- APPLICATION AND SYSTEMS-DEVELOPMENT SECURITY
- OPERATIONS SECURITY
- BUSINESS CONTINUITY PLANNING
- LAW, INVESTIGATIONS, AND ETHICS
- CRYPTOGRAPHY
A Note from Series Editor Ed Tittel
About the Author
Acknowledgments
We Want to Hear from You!
Introduction
- Introduction
- How to Prepare for the Exam
- Taking a Certification Exam
- Tracking Your CISSP Status
- About This Book
Self-Assessment
- Self-Assessment
- CISSPs in the Real World
- The Ideal CISSP Candidate
- Put Yourself to the Test
- After the Exam
The CISSP Certification Exam
- The CISSP Certification Exam
- Assessing Exam Readiness
- Taking the Exam
- Multiple-Choice Question Format
- Exam Strategy
- Question-Handling Strategies
- Mastering the Inner Game
Physical Security
- Physical Security
- Physical Security Risks
- Requirements for New Site Locations
- Building Defense in Depth
- Environmental Controls
- Electrical Power
- Equipment Life Cycle
- Fire Prevention, Detection, and Suppression
- Exam Prep Questions
- Answers to Exam Prep Questions
Security-Management Practices
- Security-Management Practices
- The Risk of Poor Security Management
- The Role of CIA
- Risk Assessment
- Policies, Procedures, Standards, Baselines, and Guidelines
- Implementation
- Training and Education
- Auditing Your Security Infrastructure
- Exam Prep Questions
- Answers to Exam Prep Questions
Access-Control Systems and Methodology
- Access-Control Systems and Methodology
- Threats Against Access Control
- Access-Control Types
- Identification, Authentication, and Authorization
- Single Sign-On
- Data Access Controls
- Intrusion-Detection Systems (IDS)
- Penetration Testing
- Honeypots
- Exam Prep Questions
- Answers to Exam Prep Questions
System Architecture and Models
- System Architecture and Models
- Common Flaws in the Security Architecture
- Computer System Architecture
- Security Mechanisms
- Security Models of Control
- Documents and Guidelines
- System Validation
- Exam Prep Questions
- Answers to Exam Prep Questions
Telecommunications and Network Security
- Telecommunications and Network Security
- Threats to Network Security
- LANs and Their Components
- WANS and Their Components
- Network Models and Standards
- Network Equipment
- Access Methods and Remote Connectivity
- Message Privacy
- Network Access Controls
- Exam Prep Questions
- Answers to Exam Prep Questions
Applications and Systems-Development Security
- Applications and Systems-Development Security
- Malicious Code
- Failure States
- The System Development Life Cycle
- Software-Development Methods
- Change Management
- Programming Languages
- Database Management
- Exam Prep Questions
- Answers to Exam Prep Questions
Operations Security
- Operations Security
- Hack Attacks
- Operational Security
- Auditing and Monitoring
- Categories of Control
- Fax Control
- Ethical Hacking
- Contingency Planning, Backup, and Recovery
- Exam Prep Questions
- Answers to Exam Prep Questions
Business Continuity Planning
- Business Continuity Planning
- The Risks of Poor Business Planning
- Business Continuity Management
- Business Continuity Plan (BCP)
- Disaster Recovery Planning (DRP)
- Exam Prep Questions
- Answers to Exam Prep Questions
Law, Investigations, and Ethics
- Law, Investigations, and Ethics
- Computer Crimes
- Common Attacks
- Ethics
- International Property Laws
- Parameters of Investigation
- Forensics
- Major Legal Systems
- Exam Prep Questions
- Answers to Exam Prep Questions
Cryptography
- Cryptography
- Cryptographic Basics
- History of Encryption
- Symmetric Encryption
- Asymmetric Encryption
- Integrity and Authentication
- Steganography
- Public Key Infrastructure (PKI)
- Cryptographic Services
- Cryptographic Attacks
- Exam Prep Questions
- Answers to Exam Prep Questions
Practice Exam 1
Answers to Practice Exam 1
Practice Exam 2
Answers to Practice Exam 2
