Configuration of Transparent Firewall
Deployment Scenarios
The robust transparent firewall solution can be deployed in different ways. This section covers two design scenarios for ease of understanding:
- SMTF deployment
- MMTF deployment using security contexts
Note
These design scenarios are discussed here to enforce learning and thus they should be used for reference only.
SMTF Deployment
SecureMe has a remote location in Brussels that uses IP as the Layer 3 protocol. SecureMe wants to deploy an ASA in transparent firewall mode so that it does not have to modify the existing network addresses. Figure 10-6 shows SecureMe's new topology in Brussels after setting up an ASA.
Figure 10-6. SecureMe Brussels Network Topology
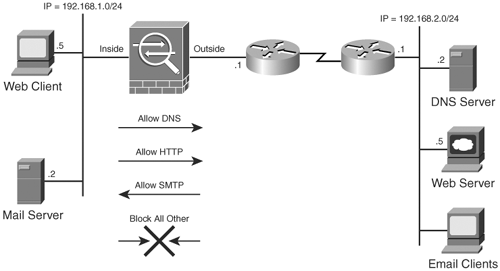
Additionally, SecureMe wants to achieve the following goals:
- Allow DNS traffic to query the DNS server
- Allow HTTP clients to talk to the remote web server
- Allow access to an email server for the remote client
- Protect the email server from TCP SYN attacks by setting the embryonic connections to 200 and maximum connections to 300
- Deny all other traffic
Example 10-11 shows the relevant configuration for the Cisco ASA in Brussels. SecureMe has set up an ACL that is applied to the inside interface to allow inbound DNS and HTTP traffic and filter out everything else. The security appliace is also configured with an ACL applied on the outside interface to allow SMTP traffic.
Example 10-11. ASA Relevant Configuration to Allow IP Traffic
Brussels# show running-config ! transparent firewall mode is enabled firewall transparent ! outside interface interface GigabitEthernet0/0 nameif outside security-level 0 ! inside interface interface GigabitEthernet0/1 nameif inside security-level 100 ! hostname Brussels ! Access-list entry to allow DNS packets to pass through the ASA. access-list inside_in extended permit udp 192.168.1.0 255.255.255.0 host 192.168.2.2 eq 53 ! Access-list entry to allow HTTP packets to pass through the ASA. access-list inside_in extended permit tcp 192.168.1.0 255.255.255.0 host 192.168.2.5 eq 80 ! Access-list entry to deny and log all other packets. access-list inside_in extended deny ip any any log ! Access-list entry to allow SMTP traffic. access-list outside_in extended permit tcp 192.168.2.0 255.255.255.0 host 192.168.1.2 eq 25 ! Global IP address ip address 192.168.1.10 255.255.255.0 ! Static command is used to specify the maximum and embryonic connection limit static (inside,outside) 192.168.1.2 192.168.1.2 netmask 255.255.255.255 tcp 300 200 ! Access-list is applied to the inside interface of the ASA access-group inside_in in interface inside ! Access-list is applied to the outside interface of the ASA access-group outside_in in interface outside ! Default gateway. It is used by the ASA for the traffic originating from it route outside 0.0.0.0 0.0.0.0 192.168.1.1 1
MMTF Deployment with Security Contexts
SecureMe plans to provide firewall services to two different organizations at its Brussels office. These organizations not only use different Layer 3 protocols but also have unique sets of requirements that SecureMe needs to account for. Figure 10-7 shows SecureMe's new topology in Brussels to provide these services.
Figure 10-7. SecureMe Brussels Multimode Topology
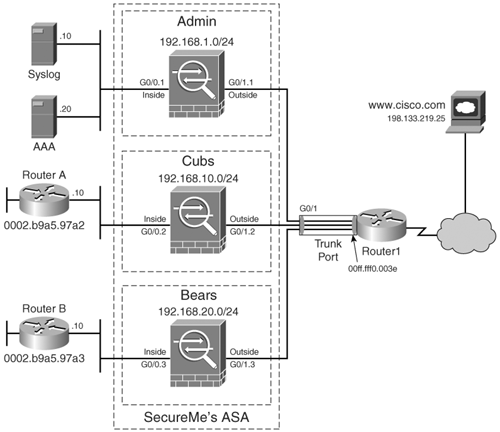
Both customersCubs and Bearshave provided SecureMe with a list of requirements:
Cubs
- Allow all IPX traffic to pass
- Allow all BPDUs to pass
- Deny all other traffic
- Set L2F table timeout of 20 minutes
Bears
- Allow Enhanced Interior Gateway Routing Protocol (EIGRP) updates to pass
- Allow Virtual Router Redundancy Protocol (VRRP) updates to pass
- Deny and log all other inbound traffic on the outside interface
- Deny learning dynamic MAC address on the outside interface
Example 10-12 shows ASA's relevant configuration with three security contexts. The system execution space has been set up to allocate interfaces to customers' contexts. An admin context is configured to do the following:
- Use a AAA server for SSH and telnet user authentication
- Log all the system-generated messages to a syslog server
Additionally, there are two other contexts: Cubs and Bears. These security contexts are set up to meet the requirements of SecureMe's customers.
Example 10-12. ASA's Relevant Configuration in Transparent Mode with Multiple Contexts
System Execution Space Brussels# show run ! transparent firewall mode is enabled in the system context firewall transparent ! Main GigabitEthernet0/0 interface interface GigabitEthernet0/0 ! Sub-interface assigned to the admin context as the inside interface. A VLAN ID is ! assigned to the interface interface GigabitEthernet0/0.1 vlan 5 ! Sub-interface assigned to the Cubs context as the inside interface. A VLAN ID is ! assigned to the interface interface GigabitEthernet0/0.2 vlan 10 ! Sub-interface assigned to the Bears context as the inside interface. A VLAN ID is ! assigned to the interface interface GigabitEthernet0/0.3 vlan 20 ! Main GigabitEthernet0/1 interface interface GigabitEthernet0/1 ! Sub-interface assigned to the admin context as the outside interface. A VLAN ID is ! assigned to the interface interface GigabitEthernet0/1.1 vlan 101 ! Sub-interface assigned to the Cubs context as the outside interface. A VLAN ID is ! assigned to the interface interface GigabitEthernet0/1.2 vlan 110 ! Sub-interface assigned to the Bears context as the outside interface. A VLAN ID is ! assigned to the interface interface GigabitEthernet0/1.3 vlan 120 hostname Brussels ! context named "admin" is the designated Admin context admin-context admin ! "admin" context definition along with the allocated interfaces. context admin description admin Context for admin purposes allocate-interface GigabitEthernet0/0.1 allocate-interface GigabitEthernet0/1.1 config-url disk0:/admin.cfg ! "Cubs" context definition along with the allocated interfaces. context Cubs description Cubs Customer Context allocate-interface GigabitEthernet0/0.2 allocate-interface GigabitEthernet0/1.2 config-url disk0:/Cubs.cfg ! "Bears" context definition along with the allocated interfaces. context Bears description Bears Customer Context allocate-interface GigabitEthernet0/0.3 allocate-interface GigabitEthernet0/1.3 config-url disk0:/Bears.cfg _____________________________________________________________________________ Admin Context Brussels/admin# show running ! transparent firewall mode is enabled in all contexts firewall transparent ASA Version 7.0(1) ! inside interface of the admin context with security level set to 100 interface GigabitEthernet0/0.1 nameif inside security-level 100 ! outside interface of the admin context with security level set to 0 interface GigabitEthernet0/1.1 nameif outside security-level 0 ! hostname admin ! Global IP address ip address 192.168.1.10 255.255.255.0 ! configuration of a syslog server with logging level set to emergencies with timestamp logging enable logging timestamp logging trap emergencies logging host inside 192.168.1.100 ! route outside 0.0.0.0 0.0.0.0 192.168.1.1 ! configuration of a AAA server using RADIUS for authentication aaa-server uauth protocol radius aaa-server uauth host 192.168.1.20 key cisco123 !Telnet and SSH using RADIUS for authentication aaa authentication telnet console uauth aaa authentication ssh console uauth ! Telnet to the admin context is allowed from the inside interface telnet 192.168.1.0 255.255.255.0 inside telnet timeout 5 ! SSH to the admin context is allowed from the outside interface ssh 0.0.0.0 0.0.0.0 outside ssh timeout 5 _____________________________________________________________________________ Security Context for Cubs Brussels/Cubs# show running ! transparent firewall mode is enabled in all contexts firewall transparent ASA Version 7.0(1) !inside interface of the Cubs context with security level set to 100 interface GigabitEthernet0/0.2 nameif inside security-level 100 !outside interface of the Cubs context with security level set to 0 interface GigabitEthernet0/1.2 nameif outside security-level 0 ! hostname Cubs ! Access-list entry to allow IPX and BPDU traffic access-list layer2_acl ethertype permit ipx access-list layer2_acl ethertype permit bpdu access-list layer2_acl ethertype deny any ! Access-list is applied to the inside interface access-group layer2_acl in interface inside ! Access-list is also applied to the outside interface access-group layer2_acl in interface outside ! Management IP address ip address 192.168.10.10 255.255.255.0 ! Default route for management traffic route outside 0.0.0.0 0.0.0.0 192.168.10.1 1 ! L2F timeout is set to 20 minutes mac-address-table aging-time 20 ______________________________________________________________________________ Security Context for Bears Brussels/Bears# show running ! transparent firewall mode is enabled in all contexts firewall transparent ASA Version 7.0(1) !inside interface of the Bears context with security level set to 100 interface GigabitEthernet0/0.3 nameif inside security-level 100 !outside interface of the Bears context with security level set to 0 interface GigabitEthernet0/1.3 nameif outside security-level 0 ! enable password 8Ry2YjIyt7RRXU24 encrypted passwd 2KFQnbNIdI.2KYOU encrypted hostname Bears ! Access-list entry to allow all IP traffic on the inside interface access-list inside_in extended permit ip any any ! Access-list entry to only allow EIGRP and VRRP traffic on the outside interface access-list outside_in extended permit eigrp any any access-list outside_in extended permit 112 any any access-list outside_in extended deny ip any any log ! ! Global IP address ip address 192.168.20.10 255.255.255.0 ! Access-list is applied to the inside interface access-group inside_in in interface inside ! Access-list is applied to the outside interface access-group outside_in in interface outside route outside 0.0.0.0 0.0.0.0 192.168.20.1 1 ! learning MAC address on the outside interface is not allowed mac-learn outside disable ! Static L2F entry of outside router as dynamic learning is not allowed mac-address-table static outside 00ff.fff0.003e
Part I: Product Overview
Introduction to Network Security
- Introduction to Network Security
- Firewall Technologies
- Intrusion Detection and Prevention Technologies
- Network-Based Attacks
- Virtual Private Networks
- Summary
Product History
- Product History
- Cisco Firewall Products
- Cisco IDS Products
- Cisco VPN Products
- Cisco ASA All-in-One Solution
- Summary
Hardware Overview
Part II: Firewall Solution
Initial Setup and System Maintenance
- Initial Setup and System Maintenance
- Accessing the Cisco ASA Appliances
- Managing Licenses
- Initial Setup
- IP Version 6
- Setting Up the System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Network Access Control
- Network Access Control
- Packet Filtering
- Advanced ACL Features
- Content and URL Filtering
- Deployment Scenarios Using ACLs
- Monitoring Network Access Control
- Understanding Address Translation
- DNS Doctoring
- Monitoring Address Translations
- Summary
IP Routing
Authentication, Authorization, and Accounting (AAA)
- Authentication, Authorization, and Accounting (AAA)
- AAA Protocols and Services Supported by Cisco ASA
- Defining an Authentication Server
- Configuring Authentication of Administrative Sessions
- Authenticating Firewall Sessions (Cut-Through Proxy Feature)
- Configuring Authorization
- Configuring Accounting
- Deployment Scenarios
- Troubleshooting AAA
- Summary
Application Inspection
- Application Inspection
- Enabling Application Inspection Using the Modular Policy Framework
- Selective Inspection
- Computer Telephony Interface Quick Buffer Encoding Inspection
- Domain Name System
- Extended Simple Mail Transfer Protocol
- File Transfer Protocol
- General Packet Radio Service Tunneling Protocol
- H.323
- HTTP
- ICMP
- ILS
- MGCP
- NetBIOS
- PPTP
- Sun RPC
- RSH
- RTSP
- SIP
- Skinny
- SNMP
- SQL*Net
- TFTP
- XDMCP
- Deployment Scenarios
- Summary
Security Contexts
- Security Contexts
- Architectural Overview
- Configuration of Security Contexts
- Deployment Scenarios
- Monitoring and Troubleshooting the Security Contexts
- Summary
Transparent Firewalls
- Transparent Firewalls
- Architectural Overview
- Transparent Firewalls and VPNs
- Configuration of Transparent Firewall
- Deployment Scenarios
- Monitoring and Troubleshooting the Transparent Firewall
- Summary
Failover and Redundancy
- Failover and Redundancy
- Architectural Overview
- Failover Configuration
- Deployment Scenarios
- Monitoring and Troubleshooting Failovers
- Summary
Quality of Service
- Quality of Service
- Architectural Overview
- Configuring Quality of Service
- QoS Deployment Scenarios
- Monitoring QoS
- Summary
Part III: Intrusion Prevention System (IPS) Solution
Intrusion Prevention System Integration
- Intrusion Prevention System Integration
- Adaptive Inspection Prevention Security Services Module Overview (AIP-SSM)
- Directing Traffic to the AIP-SSM
- AIP-SSM Module Software Recovery
- Additional IPS Features
- Summary
Configuring and Troubleshooting Cisco IPS Software via CLI
- Configuring and Troubleshooting Cisco IPS Software via CLI
- Cisco IPS Software Architecture
- Introduction to the CIPS 5.x Command-Line Interface
- User Administration
- AIP-SSM Maintenance
- Advanced Features and Configuration
- Summary
Part IV: Virtual Private Network (VPN) Solution
Site-to-Site IPSec VPNs
- Site-to-Site IPSec VPNs
- Preconfiguration Checklist
- Configuration Steps
- Advanced Features
- Optional Commands
- Deployment Scenarios
- Monitoring and Troubleshooting Site-to-Site IPSec VPNs
- Summary
Remote Access VPN
- Remote Access VPN
- Cisco IPSec Remote Access VPN Solution
- Advanced Cisco IPSec VPN Features
- Deployment Scenarios of Cisco IPSec VPN
- Monitoring and Troubleshooting Cisco Remote Access VPN
- Cisco WebVPN Solution
- Advanced WebVPN Features
- Deployment Scenarios of WebVPN
- Monitoring and Troubleshooting WebVPN
- Summary
Public Key Infrastructure (PKI)
- Public Key Infrastructure (PKI)
- Introduction to PKI
- Enrolling the Cisco ASA to a CA Using SCEP
- Manual (Cut-and-Paste) Enrollment
- Configuring CRL Options
- Configuring IPSec Site-to-Site Tunnels Using Certificates
- Configuring the Cisco ASA to Accept Remote-Access VPN Clients Using Certificates
- Troubleshooting PKI
- Summary
Part V: Adaptive Security Device Manager
Introduction to ASDM
- Introduction to ASDM
- Setting Up ASDM
- Initial Setup
- Functional Screens
- Interface Management
- System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Firewall Management Using ASDM
- Firewall Management Using ASDM
- Access Control Lists
- Address Translation
- Routing Protocols
- AAA
- Application Inspection
- Security Contexts
- Transparent Firewalls
- Failover
- QoS
- Summary
IPS Management Using ASDM
- IPS Management Using ASDM
- Accessing the IPS Device Management Console from ASDM
- Configuring Basic AIP-SSM Settings
- Advanced IPS Configuration and Monitoring Using ASDM
- Summary
VPN Management Using ASDM
- VPN Management Using ASDM
- Site-to-Site VPN Setup Using Preshared Keys
- Site-to-Site VPN Setup Using PKI
- Cisco Remote-Access IPSec VPN Setup
- WebVPN
- VPN Monitoring
- Summary
Case Studies
EAN: 2147483647
Pages: 231
