Site-to-Site VPN Setup Using PKI
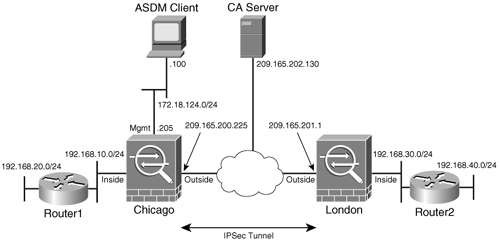
ASDM supports VPN tunnels using RSA signatures (PKI) for IKE authentication. Before a site-to-site tunnel can be set up, ASDM must have knowledge of the preinstalled certificates. If certificates are not installed on Cisco ASA, you need to follow the steps discussed in this section to retrieve both root and identity certificates from the certificate authority (CA). Figure 21-11 illustrates two Cisco ASA set up for a site-to-site tunnel using PKI. The CA server resides on the outside interfaces of Cisco ASA at 209.165.202.130.
Figure 21-11. Site-to-Site Tunnel Using PKI
Most steps in setting up a site-to-site tunnel using PKI are identical to those discussed in the previous section. The following steps are used to retrieve the certificates from a CA server:
|
Step 1. |
Generate the RSA keys. Figure 21-12. Generating the RSA Keys 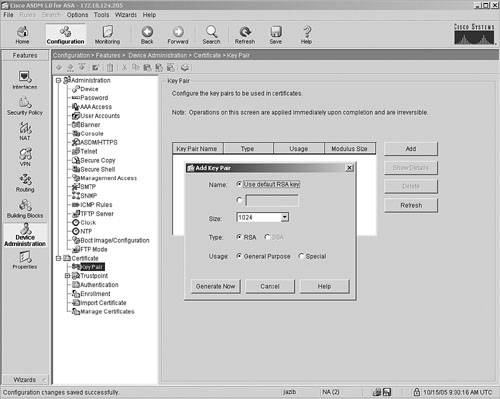
|
|
Step 2. |
Configure the trustpoint. Figure 21-13. Setting Up an Enrollment URL 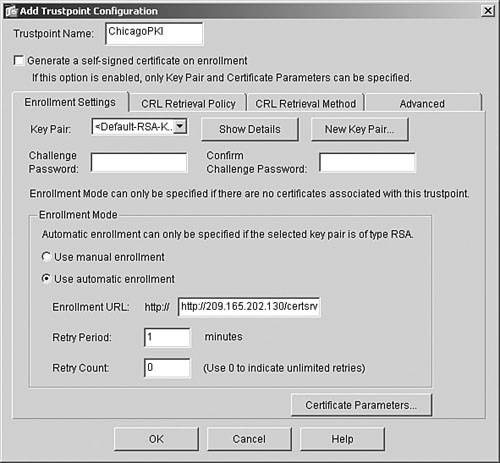
Note Each CA server vendor uses a different enrollment URL. Please consult the CA server documentation for the correct syntax. You can optionally set the Fully Qualified Domain Name (FQDN) and Distinguished Name (DN) for the certificates. Click the Certificate Parameters button to specify the FQDN or DN or both, as shown in Figure 21-14, where a DN with an attribute of Common Name (CN) Chicago is being configured.Figure 21-14. Specifying a DN 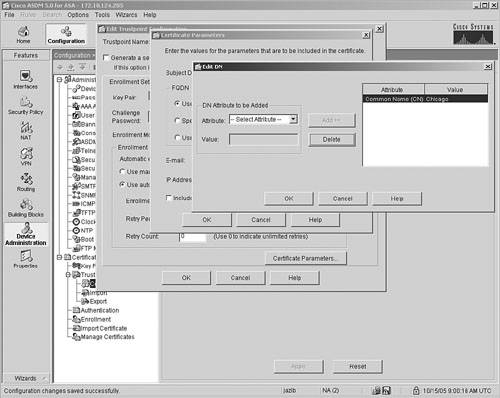
|
|
Step 3. |
Set up CRLs. Figure 21-15. Specifying the CDP 
Cisco ASA supports three protocols for retrieving the CRL from the CA servers: - LDAP - HTTP - SCEP Click the CRL Retrieval Method tab to select at least one of the protocols. In Figure 21-16, the administrator is using HTTP and SCEP as the CRL retrieval protocols.Figure 21-16. Specifying the CRL Retrieval Protocols 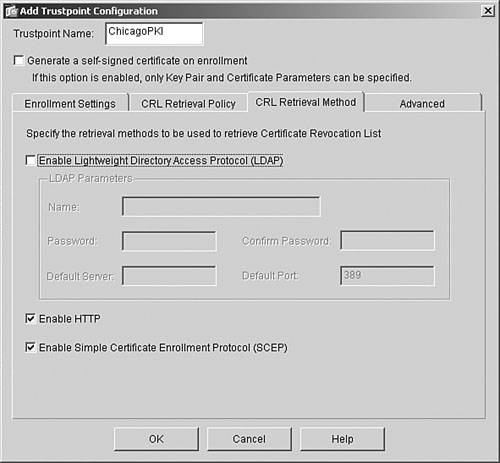
The Advanced tab enables you to specify the CRL checking and caching timers. You can choose to require CRL checking for all the received certificates, as shown in Figure 21-17. In this example, the administrator has also enabled Enforce Next CRL Update, which requires having a valid and nonexpired next update value. Figure 21-17. Setting Advanced Trustpoint Attributes 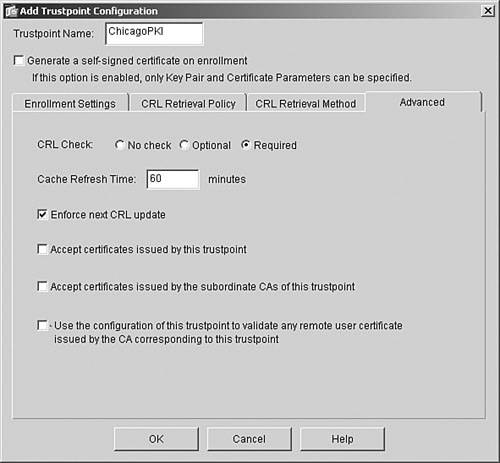
|
|
Step 4. |
Authenticate and enroll in the CA server. Figure 21-18. Requesting Root Certificate 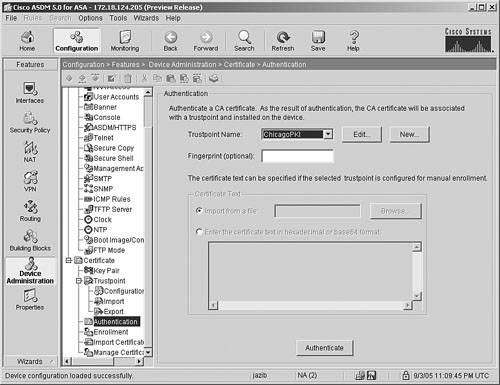
To request an identity certificate, choose Configuration > Features > Device Administration > Certificate > Enrollment and click Enroll, as shown in Figure 21-19. Figure 21-19. Requesting Identity Certificate 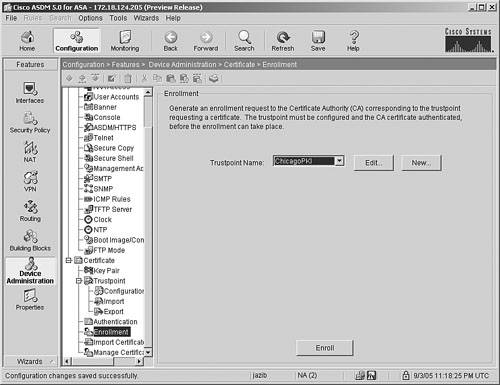
Note It is recommended to verify the fingerprint of the received CA certificate with the fingerprint on the CA server to ensure that the CA certificate has not been compromised. |
|
Step 5. |
Select a certificate for the site-to-site tunnel. Figure 21-20. Selecting Certificates for VPN Tunnels 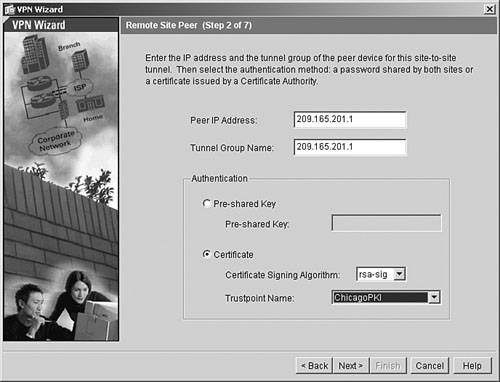
|
Part I: Product Overview
Introduction to Network Security
- Introduction to Network Security
- Firewall Technologies
- Intrusion Detection and Prevention Technologies
- Network-Based Attacks
- Virtual Private Networks
- Summary
Product History
- Product History
- Cisco Firewall Products
- Cisco IDS Products
- Cisco VPN Products
- Cisco ASA All-in-One Solution
- Summary
Hardware Overview
Part II: Firewall Solution
Initial Setup and System Maintenance
- Initial Setup and System Maintenance
- Accessing the Cisco ASA Appliances
- Managing Licenses
- Initial Setup
- IP Version 6
- Setting Up the System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Network Access Control
- Network Access Control
- Packet Filtering
- Advanced ACL Features
- Content and URL Filtering
- Deployment Scenarios Using ACLs
- Monitoring Network Access Control
- Understanding Address Translation
- DNS Doctoring
- Monitoring Address Translations
- Summary
IP Routing
Authentication, Authorization, and Accounting (AAA)
- Authentication, Authorization, and Accounting (AAA)
- AAA Protocols and Services Supported by Cisco ASA
- Defining an Authentication Server
- Configuring Authentication of Administrative Sessions
- Authenticating Firewall Sessions (Cut-Through Proxy Feature)
- Configuring Authorization
- Configuring Accounting
- Deployment Scenarios
- Troubleshooting AAA
- Summary
Application Inspection
- Application Inspection
- Enabling Application Inspection Using the Modular Policy Framework
- Selective Inspection
- Computer Telephony Interface Quick Buffer Encoding Inspection
- Domain Name System
- Extended Simple Mail Transfer Protocol
- File Transfer Protocol
- General Packet Radio Service Tunneling Protocol
- H.323
- HTTP
- ICMP
- ILS
- MGCP
- NetBIOS
- PPTP
- Sun RPC
- RSH
- RTSP
- SIP
- Skinny
- SNMP
- SQL*Net
- TFTP
- XDMCP
- Deployment Scenarios
- Summary
Security Contexts
- Security Contexts
- Architectural Overview
- Configuration of Security Contexts
- Deployment Scenarios
- Monitoring and Troubleshooting the Security Contexts
- Summary
Transparent Firewalls
- Transparent Firewalls
- Architectural Overview
- Transparent Firewalls and VPNs
- Configuration of Transparent Firewall
- Deployment Scenarios
- Monitoring and Troubleshooting the Transparent Firewall
- Summary
Failover and Redundancy
- Failover and Redundancy
- Architectural Overview
- Failover Configuration
- Deployment Scenarios
- Monitoring and Troubleshooting Failovers
- Summary
Quality of Service
- Quality of Service
- Architectural Overview
- Configuring Quality of Service
- QoS Deployment Scenarios
- Monitoring QoS
- Summary
Part III: Intrusion Prevention System (IPS) Solution
Intrusion Prevention System Integration
- Intrusion Prevention System Integration
- Adaptive Inspection Prevention Security Services Module Overview (AIP-SSM)
- Directing Traffic to the AIP-SSM
- AIP-SSM Module Software Recovery
- Additional IPS Features
- Summary
Configuring and Troubleshooting Cisco IPS Software via CLI
- Configuring and Troubleshooting Cisco IPS Software via CLI
- Cisco IPS Software Architecture
- Introduction to the CIPS 5.x Command-Line Interface
- User Administration
- AIP-SSM Maintenance
- Advanced Features and Configuration
- Summary
Part IV: Virtual Private Network (VPN) Solution
Site-to-Site IPSec VPNs
- Site-to-Site IPSec VPNs
- Preconfiguration Checklist
- Configuration Steps
- Advanced Features
- Optional Commands
- Deployment Scenarios
- Monitoring and Troubleshooting Site-to-Site IPSec VPNs
- Summary
Remote Access VPN
- Remote Access VPN
- Cisco IPSec Remote Access VPN Solution
- Advanced Cisco IPSec VPN Features
- Deployment Scenarios of Cisco IPSec VPN
- Monitoring and Troubleshooting Cisco Remote Access VPN
- Cisco WebVPN Solution
- Advanced WebVPN Features
- Deployment Scenarios of WebVPN
- Monitoring and Troubleshooting WebVPN
- Summary
Public Key Infrastructure (PKI)
- Public Key Infrastructure (PKI)
- Introduction to PKI
- Enrolling the Cisco ASA to a CA Using SCEP
- Manual (Cut-and-Paste) Enrollment
- Configuring CRL Options
- Configuring IPSec Site-to-Site Tunnels Using Certificates
- Configuring the Cisco ASA to Accept Remote-Access VPN Clients Using Certificates
- Troubleshooting PKI
- Summary
Part V: Adaptive Security Device Manager
Introduction to ASDM
- Introduction to ASDM
- Setting Up ASDM
- Initial Setup
- Functional Screens
- Interface Management
- System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Firewall Management Using ASDM
- Firewall Management Using ASDM
- Access Control Lists
- Address Translation
- Routing Protocols
- AAA
- Application Inspection
- Security Contexts
- Transparent Firewalls
- Failover
- QoS
- Summary
IPS Management Using ASDM
- IPS Management Using ASDM
- Accessing the IPS Device Management Console from ASDM
- Configuring Basic AIP-SSM Settings
- Advanced IPS Configuration and Monitoring Using ASDM
- Summary
VPN Management Using ASDM
- VPN Management Using ASDM
- Site-to-Site VPN Setup Using Preshared Keys
- Site-to-Site VPN Setup Using PKI
- Cisco Remote-Access IPSec VPN Setup
- WebVPN
- VPN Monitoring
- Summary
Case Studies
EAN: 2147483647
Pages: 231
- Chapter II Information Search on the Internet: A Causal Model
- Chapter V Consumer Complaint Behavior in the Online Environment
- Chapter VII Objective and Perceived Complexity and Their Impacts on Internet Communication
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter XII Web Design and E-Commerce
