Case Study 2: Large Enterprise Firewall, VPN, and IPS Deployment
Case Study 2 Large Enterprise Firewall, VPN, and IPS Deployment
This section demonstrates how Cisco ASA can provide multifunction solutions for large enterprise networks. Figure 22-4 shows how different Cisco ASAs are deployed within SecureMe's headquarters offices.
Figure 22-4. Network Topology for Regional Site Offices
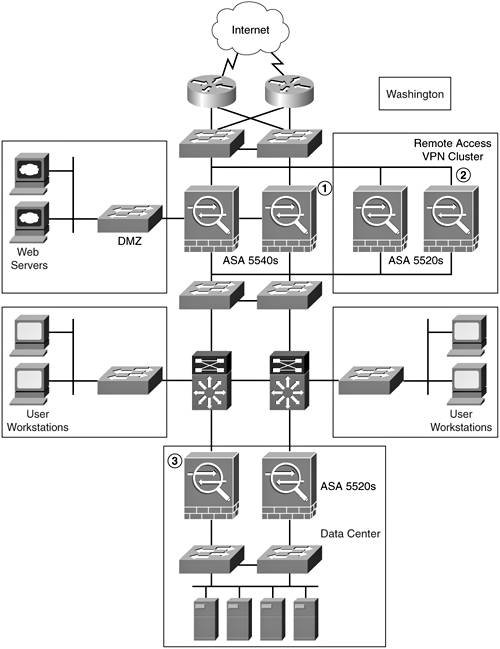
The Cisco ASA appliances are deployed as follows:
- The Cisco ASA 5540s at the Internet edge provide internal users connectivity to Internet services and provide external users access to information on public servers in a demilitarized zone (DMZ) network. These appliances are configured in failover mode. An AIP-SSM module is installed on each appliance to provide IPS services.
- A cluster of Cisco ASA 5520s is configured to provide remote-access VPN services to telecommuters and remote users.
- Two Cisco ASA 5520s (in failover mode) provide security services to servers at SecureMe's data center.
Internet Edge and DMZ
The Cisco ASA 5540s (5540-1 and 5540-2) at the Internet edge of SecureMe's main office network are configured in failover mode and are connected to two Catalyst switches on their outside (public) interface, as illustrated in Figure 22-5.
Figure 22-5. Regional Site Offices: Cisco ASA Deployment at the Internet Edge and DMZ
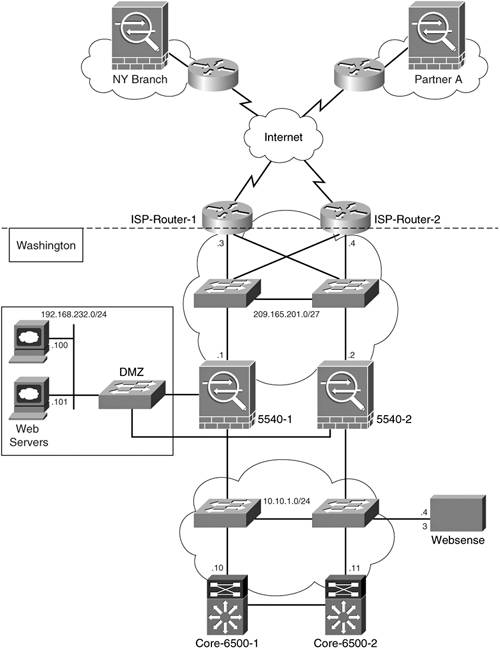
These two switches are connected to Cisco IOS routers (ISP-Router-1 and ISP-Router-2) connected to two different ISPs. These routers are configured with the Hot Standby Router Protocol (HSRP) to provide redundant links to the Internet.
The LAN switches are connected to each other via 100BASE-T trunk ports, and each LAN switch is, in turn, connected to the routers and the Cisco ASA 5540s (subnet 209.165.201.0/27). The HSRP virtual address of the routers is 209.165.201.5/27. The default gateway configuration at each of the Cisco ASA 5540s is set to the virtual address of the routers.
There are two web servers in a DMZ network (192.168.232.100 and 192.168.232.101). These servers are statically translated to two public IP addresses (209.165.201.25 and 209.165.201.26, respectively). Only HTTP and HTTPS communication is allowed to these servers from Internet users. These servers retrieve information from an internal database hosted at the 10.20.3.80 server running MySQL (an open-source database). The web servers use TCP port 3306 to communicate to the internal database. This is the only communication allowed from these servers to the internal network.
Example 22-4 includes the commands to configure Washington ASA 5540-1 to achieve these goals. The site-to-site tunnel configuration to the New York branch office and Partner-A is also included in Example 22-4. A crypto map called Washington_map is configured with two separate instances.
Example 22-4. Washington ASA 5540-1 Configuration
!Configuration of public interface facing the Internet routers interface GigabitEthernet0/0 description outside interface nameif outside security-level 0 ip address 209.165.201.1 255.255.255.224 ! !Configuration of the inside interface interface GigabitEthernet0/1 description inside interface nameif inside security-level 100 ip address 10.10.1.1 255.255.255.0 ! !DMZ Interface with security level 50 interface GigabitEthernet0/2 description DMZ interface nameif DMZ security-level 50 ip address 192.168.232.1 255.255.255.0 ! ! Interface used for failover communication interface GigabitEthernet0/3 description Failover Interface no nameif no security-level no ip address ! !Management interface configuration ASA and AIP-SSM management interfaces are in the !10.10.220.0/24 management network. interface Management0/0 nameif mgmt security-level 70 ip address 10.10.220.1 255.255.255.0 management-only ! ! hostname Washington5540-1 ! !Access control list to bypass NAT for the IPSec communication to the New York branch !office and Partner-A networks. access-list nonat extended permit ip host 10.20.2.70 192.168.144.0 255.255.255.0 access-list nonat extended permit ip 10.20.4.0 255.255.255.0 10.165.200.0 255.255.255.0 access-list nonat extended permit ip 10.20.1.0 255.255.255.0 10.165.200.0 255.255.255.0 access-list nonat extended permit ip 10.10.220.0 255.255.255.0 10.165.200.0 255.255.255.0 ! !Access control list to classify what traffic will be encrypted to the IPSec ! site-to-site tunnel to Partner-A access-list encryptPartA extended permit ip 10.20.2.0 255.255.255.0 192.168.144.0 255.255.255.0! !Access control list to classify what traffic will be encrypted to the IPSec site-to-site !tunnel to the New York branch office. access-list encryptNY extended permit ip 10.10.1.0 255.255.255.0 10.165.200.0 255.255.255.0 access-list encryptNY extended permit ip 10.20.2.0 255.255.255.0 10.165.200.0 255.255.255.0 access-list encryptNY extended permit ip 10.10.220.0 255.255.255.0 10.165.200.0 255.255.255.0 ! !Access control list applied to the DMZ interface to allow only communication from the !web servers to the 10.20.3.80 MySQL server over TCP port 3306 access-list dmzACL extended permit tcp host 192.168.232.100 host 10.20.3.80 eq 3306 access-list dmzACL extended permit tcp host 192.168.232.101 host 10.20.3.80 eq 3306 ! !NAT configuration a global pool of addresses (209.165.201.10 to 209.165.201.15) is !configured. After these addresses are allocated all connections will be port !address translated to 209.165.201.16. global (outside) 1 209.165.201.10-209.165.201.15 global (outside) 1 209.165.201.16 nat (inside) 0 access-list nonat nat (inside) 1 10.0.0.0 255.0.0.0 ! !Static NAT configuration for the web servers in the DMZ network. static (DMZ,outside) 209.165.201.25 192.168.232.100 netmask 255.255.255.255 static (DMZ,outside) 209.165.201.26 192.168.232.101 netmask 255.255.255.255 ! !Access group for dmzACL access-group dmzACL in interface DMZ ! !IPSec site-to-site tunnel configuration two crypto maps are configured (one for the !tunnel to the branch office in New York and a second for the tunnel to Partner-A). crypto ipsec transform-set myset esp-aes-256 esp-sha-hmac crypto map Washington_map 10 match address encryptPartA crypto map Washington_map 10 set peer 209.165.202.129 crypto map Washington_map 10 set transform-set myset crypto map Washington_map 20 match address encryptNY crypto map Washington_map 20 set peer 209.165.200.231 crypto map Washington_map 20 set transform-set myset crypto map Washington_map interface outside isakmp enable outside isakmp policy 10 authentication pre-share isakmp policy 10 encryption aes-256 isakmp policy 10 hash sha isakmp policy 10 group 2 !
Filtering Websites
There is a Websense server for URL filtering (10.10.1.43) in the inside interface of the Internet edge firewalls. The security administrator configures Cisco ASA to send all the user web requests to the 10.10.1.43 filtering server, except requests to the two web servers located in SecureMe's DMZ network (192.168.232.100 and 192.168.232.101). The goal is that, after an internal user accesses a site, the Cisco ASA will cache the address (if permitted by the Websense server).
The cache size configured is 64 KB. Therefore, when the same or another user accesses the cached website, the Cisco ASA will not query the Websense server again, increasing performance. The URL memory pool size is configured with 10 KB. An additional requirement the security administrator dictates is for Cisco ASA to allow long URLs of 4 KB in size. To increase performance, 128 blocks are kept in the Cisco ASA buffer. Example 22-5 includes the command the security administrator enters in Cisco ASA 5540-1 to achieve these goals.
Example 22-5. URL Filtering
!Specifying the Websense server url-server (inside) vendor websense host 10.10.1.43 ! !Filtering all URLs except for the two servers in the DMZ filter url except 0.0.0.0 0.0.0.0 192.168.232.101 255.255.255.255 filter url except 0.0.0.0 0.0.0.0 192.168.232.100 255.255.255.255 filter url http 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 ! !URL block memory pool is configured to 10KB url-block url-mempool 10 ! !Support for long URLs of up to 4KB in size url-block url-size 4 ! !The following command enables 128 blocks to be buffered in the Cisco ASA. url-block block 128 ! !URL cache size of 64KB based on both the source address initiating the URL request, as !well as the URL destination address url-cache src_dst 64
Note
For more information about Websense filtering server, go to http://www.websense.com.
Remote Access VPN Cluster
SecureMe has two Cisco ASA 5520s configured in a cluster for remote access VPN support. Figure 22-6 illustrates the design, including corresponding IP addresses.
Figure 22-6. Remote-Access VPN Cluster
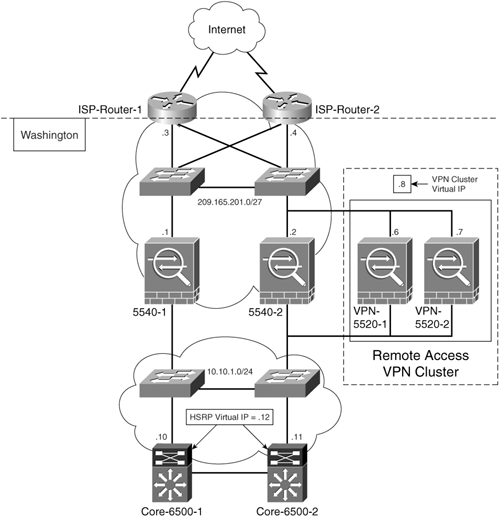
The two Cisco ASA 5520s are labeled VPN-5520-1 and VPN-5520-2. The goal is to have the VPN-5520-1 configured as the cluster master (with priority 10) and VPN-5520-2 as the cluster secondary (with priority 5). Load-balancing communication between both Cisco ASA 5520s must be encrypted. Example 22-6 shows the configuration of the cluster master (VPN-5520-1).
Example 22-6. Remote-Access VPN Cluster Master ASA Configuration
!Public/outside interface configuration interface GigabitEthernet0/0 nameif outside security-level 0 ip address 209.165.201.6 255.255.255.224 ! !Private/inside interface configuration interface GigabitEthernet0/1 nameif inside security-level 100 ip address 10.10.1.6 255.255.255.0 ! hostname VPN-5520-1 ! !IP Pool for remote access VPN clients ip local pool vpnpool 10.10.253.1-10.10.253.254 !Static Routing configuration. Default gateway is pointing to the Internet router HSRP !address and tunnel default gateway is pointing to the primary ASA 5540 Internet Firewall !IP address. route outside 0.0.0.0 0.0.0.0 209.165.201.5 1 route inside 10.20.0.0 255.255.0.0 10.10.1.12 1 route inside 10.10.0.0 255.255.0.0 10.10.1.12 1 route inside 0.0.0.0 0.0.0.0 10.10.1.1 tunneled ! !RADIUS Server configuration. The RADIUS server is located in SecureMe's Data Center. aaa-server Radius protocol radius aaa-server Radius host 10.20.1.40 key cisco123 ! !A VPN group called SecureMeGrp is configured. group-policy SecureMeGrp internal group-policy SecureMeGrp attributes banner value You have connected to VPN-5520-1. This is a restricted VPN system. dns-server value 10.20.4.98 10.20.4.99 vpn-simultaneous-logins 1 vpn-tunnel-protocol IPSec ipsec-udp enable ipsec-udp-port 10000 split-tunnel-policy tunnelall default-domain value securemeinc.com ! !IPSec transform-set configuration crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac ! !A dynamic crypto map is configured for the remote access VPN clients. crypto dynamic-map secureme_dyn_map 10 set transform-set ESP-3DES-SHA crypto map outside_map 100 ipsec-isakmp dynamic secureme_dyn_map crypto map outside_map interface outside ! ! isakmp configurationEnabled on the outside interface isakmp enable outside ! isakmp configurationEnabled on the inside interface for VPN LB isakmp enable inside ! !ISAKMP policy configuration for VPN Clients isakmp policy 10 authentication pre-share isakmp policy 10 encryption 3des isakmp policy 10 hash sha isakmp policy 10 group 2 isakmp policy 10 lifetime 86400 ! !Tunnel Group configuration for Remote Access VPN tunnel-group securemevpn type ipsec-ra ! !Tunnel group general attributes. The VPN Address pool vpnpool is mapped, the default !VPN group is SecureMeGrp, and authentication is set to RADIUS. tunnel-group securemevpn general-attributes address-pool vpnpool authentication-server-group Radius authentication-server-group (inside) Radius default-group-policy SecureMeGrp ! !Tunnel Group IPSec attributes tunnel-group securemevpn ipsec-attributes pre-shared-key * ! !Load-balancing configuration. Encryption for VPN load-balancing communication is !configured. The priority 10 will force this appliance to be the master. vpn load-balancing priority 10 cluster key cisco123 cluster ip address 209.165.201.8 cluster encryption participate
The master Cisco ASA (VPN-5520-1) is configured to assign IP addresses to VPN clients from a pool of addresses in the range of 10.10.253.1 through 10.10.253.254. A different IP address pool must be configured in the cluster secondary appliance (VPN-5520-2). The IP address pool range is 10.10.254.1 through 10.10.254.254. Example 22-7 shows the cluster secondary Cisco ASA configuration.
Example 22-7. Remote-Access VPN Cluster Secondary ASA Configuration
!Public/outside interface configuration interface GigabitEthernet0/0 nameif outside security-level 0 ip address 209.165.201.7 255.255.255.224 ! !Private/inside interface configuration interface GigabitEthernet0/1 nameif inside security-level 100 ip address 10.10.1.7 255.255.255.0 ! hostname VPN-5520-2 ! !IP Pool for remote access VPN clients ip local pool vpnpool 10.10.254.1-10.10.254.254 !Static Routing configuration. Default gateway is pointing to the Internet router HSRP !address and tunnel default gateway is pointing to the primary ASA 5540 Internet Firewall !IP address. route outside 0.0.0.0 0.0.0.0 209.165.201.5 1 route inside 10.20.0.0 255.255.0.0 10.10.1.12 1 route inside 10.10.0.0 255.255.0.0 10.10.1.12 1 route inside 0.0.0.0 0.0.0.0 10.10.1.1 tunneled ! ! RADIUS Server configuration. The RADIUS server is located in SecureMe's Data Center. aaa-server Radius protocol radius aaa-server Radius host 10.20.1.40 key cisco123 ! !A VPN group called SecureMeGrp is configured. group-policy SecureMeGrp internal group-policy SecureMeGrp attributes banner value You have connected to VPN-5520-2. This is a restricted VPN system. dns-server value 10.20.4.98 10.20.4.99 vpn-simultaneous-logins 1 vpn-tunnel-protocol IPSec ipsec-udp enable ipsec-udp-port 10000 split-tunnel-policy tunnelall default-domain value securemeinc.com ! !IPSec transform-set configuration crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac ! !A dynamic crypto map is configured for the remote access VPN clients. crypto dynamic-map secureme_dyn_map 10 set transform-set ESP-3DES-SHA crypto map outside_map 100 ipsec-isakmp dynamic secureme_dyn_map crypto map outside_map interface outside ! ! isakmp configuration Enabled on the outside interface isakmp enable outside ! isakmp configuration Enabled on the inside interface for VPN LB isakmp enable inside ! !ISAKMP policy configuration for VPN Clients isakmp policy 10 authentication pre-share isakmp policy 10 encryption 3des isakmp policy 10 hash sha isakmp policy 10 group 2 isakmp policy 10 lifetime 86400 ! !Tunnel Group configuration for Remote Access VPN tunnel-group securemevpn type ipsec-ra ! !Tunnel group general attributes. The VPN Address pool vpnpool is mapped, the default !VPN group is SecureMeGrp, and authentication is set to RADIUS. tunnel-group securemevpn general-attributes address-pool vpnpool authentication-server-group Radius authentication-server-group (inside) Radius default-group-policy SecureMeGrp ! !Tunnel Group IPSec attributes tunnel-group securemevpn ipsec-attributes pre-shared-key * ! !Load-balancing configuration. Encryption for VPN load-balancing communication is !configured. The priority 10 will force this appliance to be the master. vpn load-balancing priority 5 cluster key cisco123 cluster ip address 209.165.201.8 cluster encryption participate
Notice that the configuration is almost identical to the cluster master appliance with the exception of the IP addressing, IP address pool, and VPN load-balancing priority.
Application Inspection
The Washington security administrator received calls from many users complaining that they can't access streaming video with applications using the Real-Time Streaming Protocol (RTSP) (for example, Apple QuickTime 4, RealPlayer, and Cisco IP/TV). After researching the issue, the security administrator notices that RTSP inspection is not enabled on the Internet edge Cisco ASA. The configuration commands in Example 22-8 are appended to the Internet edge appliances.
Example 22-8. RTSP Inspection
!An ACL defining the RTSP traffic over the default TCP ports (554 and 8554) access-list rtsp_acl permit tcp any any eq 554 access-list rtsp_acl permit tcp any any eq 8554 ! !A class-map named rtsp_traffic is configured matching the previously configured ACL class-map rtsp_traffic match access-list rtsp_acl ! !A policy map called inbound_policy is configured to inspect all RTSP traffic and applied !to the inside interface policy-map inbound_policy class rtsp_traffic inspect rtsp service-policy inbound_policy interface inside
IPS
The Cisco ASA 5540s at the Internet edge are running IPS services in AIP-SSM modules. Each AIP-SSM is configured in promiscuous mode. The AIP-SSM inspects all packets that enter through the outside interface and are destined for the inside and DMZ networks. The configuration in Example 22-9 is appended to each Cisco ASA 5540.
Example 22-9. ASA IPS Redirection
!A class-map is configured to capture/match all traffic class-map IPSclass match any ! !A policy map is created associating the previously created class map. IPS is configured !in promiscuous mode and to for the Cisco ASA to continue to pass traffic if the AIP-SSM fails policy-map IPSpolicy class IPSclass ips promiscuous fail-open ! !IPS service policy is applied globally. service-policy IPSpolicy global
If the AIP-SSM fails, the Cisco ASA 5540 will continue to pass traffic normally. This is referred to as fail-open. In inline mode, if the security appliance is configured to fail-close, Cisco ASA will stop all traffic to be transmitted from and to any of its interfaces. However, in promiscuous mode the AIP-SSM will not cause the traffic passing through the Cisco ASA to stop. The fail-open or fail-close configuration only applies to inline mode.
The security administrator notices several events/alarms generated by signature 223344. After detailed analysis, the security administrator discovers that these are false positives. The goal is to disable signature 223344. It will still be processed by the AIP-SSM without generating any logs or events. Example 22-10 shows the AIP-SSM configuration to disable signature 223344.
Example 22-10. Disabling Signature 223344
WashingtonSSM-1# configure terminal WashingtonSSM-1(config)# service signature-definition sig0 WashingtonSSM-1(config-sig)# signatures 223344 0 WashingtonSSM-1(config-sig-sig)# status WashingtonSSM-1(config-sig-sig-sta)# enabled false WashingtonSSM-1(config-sig-sig-sta)# show settings status ----------------------------------------------- enabled: false default: false retired: false ----------------------------------------------- WashingtonSSM-1(config-sig-sig-sta)# exit WashingtonSSM-1(config-sig-sig)# exit WashingtonSSM-1(config-sig)# exit Apply Changes:?[yes]:yes
The tuning process is crucial for IPS management. After disabling signatures that generate false positives and making sure that the correct signatures are enabled, the security administrator can now determine threat origins and targets, and use this information to prevent attacks, protect resources, and reduce network downtime.
Note
The Cisco Security Monitoring, Analysis and Response System (CS-MARS) can collect IPS event information from the AIP-SSM. CS-MARS provides intelligent and sophisticated features that can help you during the IPS tuning process. You can get more information about CS-MARS at http://www.cisco.com/go/mars.
Part I: Product Overview
Introduction to Network Security
- Introduction to Network Security
- Firewall Technologies
- Intrusion Detection and Prevention Technologies
- Network-Based Attacks
- Virtual Private Networks
- Summary
Product History
- Product History
- Cisco Firewall Products
- Cisco IDS Products
- Cisco VPN Products
- Cisco ASA All-in-One Solution
- Summary
Hardware Overview
Part II: Firewall Solution
Initial Setup and System Maintenance
- Initial Setup and System Maintenance
- Accessing the Cisco ASA Appliances
- Managing Licenses
- Initial Setup
- IP Version 6
- Setting Up the System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Network Access Control
- Network Access Control
- Packet Filtering
- Advanced ACL Features
- Content and URL Filtering
- Deployment Scenarios Using ACLs
- Monitoring Network Access Control
- Understanding Address Translation
- DNS Doctoring
- Monitoring Address Translations
- Summary
IP Routing
Authentication, Authorization, and Accounting (AAA)
- Authentication, Authorization, and Accounting (AAA)
- AAA Protocols and Services Supported by Cisco ASA
- Defining an Authentication Server
- Configuring Authentication of Administrative Sessions
- Authenticating Firewall Sessions (Cut-Through Proxy Feature)
- Configuring Authorization
- Configuring Accounting
- Deployment Scenarios
- Troubleshooting AAA
- Summary
Application Inspection
- Application Inspection
- Enabling Application Inspection Using the Modular Policy Framework
- Selective Inspection
- Computer Telephony Interface Quick Buffer Encoding Inspection
- Domain Name System
- Extended Simple Mail Transfer Protocol
- File Transfer Protocol
- General Packet Radio Service Tunneling Protocol
- H.323
- HTTP
- ICMP
- ILS
- MGCP
- NetBIOS
- PPTP
- Sun RPC
- RSH
- RTSP
- SIP
- Skinny
- SNMP
- SQL*Net
- TFTP
- XDMCP
- Deployment Scenarios
- Summary
Security Contexts
- Security Contexts
- Architectural Overview
- Configuration of Security Contexts
- Deployment Scenarios
- Monitoring and Troubleshooting the Security Contexts
- Summary
Transparent Firewalls
- Transparent Firewalls
- Architectural Overview
- Transparent Firewalls and VPNs
- Configuration of Transparent Firewall
- Deployment Scenarios
- Monitoring and Troubleshooting the Transparent Firewall
- Summary
Failover and Redundancy
- Failover and Redundancy
- Architectural Overview
- Failover Configuration
- Deployment Scenarios
- Monitoring and Troubleshooting Failovers
- Summary
Quality of Service
- Quality of Service
- Architectural Overview
- Configuring Quality of Service
- QoS Deployment Scenarios
- Monitoring QoS
- Summary
Part III: Intrusion Prevention System (IPS) Solution
Intrusion Prevention System Integration
- Intrusion Prevention System Integration
- Adaptive Inspection Prevention Security Services Module Overview (AIP-SSM)
- Directing Traffic to the AIP-SSM
- AIP-SSM Module Software Recovery
- Additional IPS Features
- Summary
Configuring and Troubleshooting Cisco IPS Software via CLI
- Configuring and Troubleshooting Cisco IPS Software via CLI
- Cisco IPS Software Architecture
- Introduction to the CIPS 5.x Command-Line Interface
- User Administration
- AIP-SSM Maintenance
- Advanced Features and Configuration
- Summary
Part IV: Virtual Private Network (VPN) Solution
Site-to-Site IPSec VPNs
- Site-to-Site IPSec VPNs
- Preconfiguration Checklist
- Configuration Steps
- Advanced Features
- Optional Commands
- Deployment Scenarios
- Monitoring and Troubleshooting Site-to-Site IPSec VPNs
- Summary
Remote Access VPN
- Remote Access VPN
- Cisco IPSec Remote Access VPN Solution
- Advanced Cisco IPSec VPN Features
- Deployment Scenarios of Cisco IPSec VPN
- Monitoring and Troubleshooting Cisco Remote Access VPN
- Cisco WebVPN Solution
- Advanced WebVPN Features
- Deployment Scenarios of WebVPN
- Monitoring and Troubleshooting WebVPN
- Summary
Public Key Infrastructure (PKI)
- Public Key Infrastructure (PKI)
- Introduction to PKI
- Enrolling the Cisco ASA to a CA Using SCEP
- Manual (Cut-and-Paste) Enrollment
- Configuring CRL Options
- Configuring IPSec Site-to-Site Tunnels Using Certificates
- Configuring the Cisco ASA to Accept Remote-Access VPN Clients Using Certificates
- Troubleshooting PKI
- Summary
Part V: Adaptive Security Device Manager
Introduction to ASDM
- Introduction to ASDM
- Setting Up ASDM
- Initial Setup
- Functional Screens
- Interface Management
- System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Firewall Management Using ASDM
- Firewall Management Using ASDM
- Access Control Lists
- Address Translation
- Routing Protocols
- AAA
- Application Inspection
- Security Contexts
- Transparent Firewalls
- Failover
- QoS
- Summary
IPS Management Using ASDM
- IPS Management Using ASDM
- Accessing the IPS Device Management Console from ASDM
- Configuring Basic AIP-SSM Settings
- Advanced IPS Configuration and Monitoring Using ASDM
- Summary
VPN Management Using ASDM
- VPN Management Using ASDM
- Site-to-Site VPN Setup Using Preshared Keys
- Site-to-Site VPN Setup Using PKI
- Cisco Remote-Access IPSec VPN Setup
- WebVPN
- VPN Monitoring
- Summary
Case Studies
- Case Studies
- Case Study 1: Deploying the Cisco ASA at Branch Offices and Small Businesses
- Case Study 2: Large Enterprise Firewall, VPN, and IPS Deployment
- Summary
EAN: 2147483647
Pages: 231
