Adventures of the ObjectSID Attribute
|
|
Adventures of the ObjectSID Attribute
Alteration of an Active Directory object's domain membership results in the changing of the object security identifier (SID). Windows 2000-based native mode domains as well as Windows .NET-based Windows 2000 native and Windows .NET (version 2002) functional level domains have a mechanism permitting users and other security principals to retain access to network resources after they have been moved to another location in the domain structure. Let us discuss this mechanism in an example using ClonePrincipal.
Every security principal object in non-Windows 2000 mixed mode domains has a multi-valued sIDHistory attribute. This attribute, as well as the object SID (the objectSid attribute), is used in an object's access token for granting access to network resources. If any SID value is presented in the ACL of a network resource, the object is granted access to this resource (provided that the granted access permission is Allow rather than Deny). This process is outlined in Fig. 13.1.
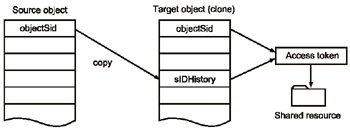
Fig. 13.1: The sIDHistory attribute allows a new object to retain the access permissions granted to the source object
After either ClonePrincipal or MoveTree creates a new object, it adds the source object's SID value to the new object's sIDHistory list. As a result, the new object will have access to all resources available to the source object (Fig. 13.2).
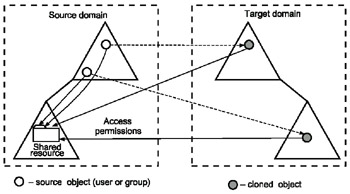
Fig. 13.2: The cloned (or moved) object inherits the access rights of the source object
In addition, the sIDHistory list of the source object — if the list is not empty — is added to the sIDHistory of the target object.
|
|
EAN: 2147483647
Pages: 154