Network-Based Attacks
During recent years, the number of different types of network attacks has been on the rise. This section covers some of the major types of network attacks and their purpose, in relation to their perpetrators and victims. Several common types of attacks are discussed, such as the following:
- DoS attacks
- DDoS attacks
- Session hijacking (such as man-in-the-middle attacks)
It is extremely important to understand that everyone has the potential to be exploited by a network attack. Consequently, a full understanding of these threats is imperative.
DoS Attacks
DoS attacks are exercised to disrupt service to a single system or an entire network. An attacker uses this type of attack to overburden and overutilize system or network resources. DoS attacks can cause network devices to drop packets. They can also force applications to stop functioning properly. With a DoS attack, an attacker's goal is to prevent the system or network users from using its services.
Note
DoS attacks can also be used to degrade the performance of IDS and IPS devices. They are often used to add other attacks, like penetration attempts and reconnaissance.
Most frequently, DoS attacks try to damage network connectivity, while trying to open counterfeited TCP or UDP connections. The target device tries to handle the additional connections to the best of its extent, thus consuming all of its available resources. Three common types of DoS attacks are designed to disrupt network connectivity:
- TCP SYN flood attacks
- land.c attacks
- Smurf attacks
TCP SYN Flood Attacks
TCP SYN flood attacks are designed to take advantage of the methodology used in establishing a new TCP connection, referred as a TCP three-way handshake. Figure 1-4 illustrates how the TCP connections are established.
Figure 1-4. TCP Connection Establishment
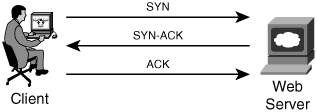
In the example presented in Figure 1-4, the client tries to establish a TCP connection to the web server. First, it sends out a SYN (synchronize) packet to the server to synchronize the sequence numbers. It stipulates its initial sequence number (ISN). To initialize a connection, the client and server must synchronize each other's sequence numbers. The Acknowledgment (ACK) field is set to 0 because this is the first packet of the three-way handshake and there are no acknowledgements thus far. In the second packet, the server sends an acknowledgment and its own SYN (SYN-ACK) back to the client. The server acknowledges the request from the client, but also sends its own request for synchronization. The server increments the client's sequence number by one and, in addition, uses it as the acknowledgment number. To conclude the connection, the client sends an acknowledgment (ACK) packet to the web server. The client uses the same methodology the server used by providing an acknowledgment number.
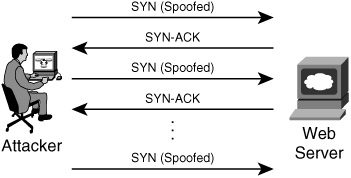
In TCP SYN flood attacks, the attacker generates spoofed packets to appear as valid new connection requests. These packets are received by the server, but the connection never completes. On the other hand, the server tries to reply without successfully completing the connections. After several of these packets are sent to the server, the server may quit responding to new connections until its resources are available to process the additional requests or when the attack stops attacking. Figure 1-5 shows how SYN flood attacks work. The attacker sends numerous spoofed SYN packets to the web server.
Figure 1-5. SYN Flood Attack
Note
Spoofing is the technique where the attacker sends IP packets with someone else's source address to hide their identity. Sometimes attackers use authorized external or internal IP addresses that are trusted by firewalls and other devices, in order to obtain access to internal resources.
Note
The server keeps all spoofed connections open until they time out. This causes substantial performance degradation.
land.c Attacks
Another primitive example of a DoS attack is the land.c attack. In this type of attack, an attacker sends numerous SYN packets with the same source and destination IP addresses and the identical source and destination ports to its victim. The purpose of this attack is to make the victim send the reply packet to itself. Because the attacker repeatedly sends these packets, the victim can run out of resources by replying to itself. Technically, the attacker uses the server's own resources against itself.
Smurf Attacks
Attackers can also consume bandwidth by directing unnecessary traffic to the victim's network. A classic example of this type of attack is the smurf attack. There are two major components in a smurf attack:
- The use of bogus Internet Control Message Protocol (ICMP) echo request packets
- The routing of packets to IP broadcast addresses
Normally, ICMP handles errors and barters control messages. For example, the popular tool called ping uses ICMP. It is used to verify that a specific system on the network is responding. It does this by sending an ICMP echo request packet to such a system. Consequently, it expects the system to return an ICMP echo reply packet.
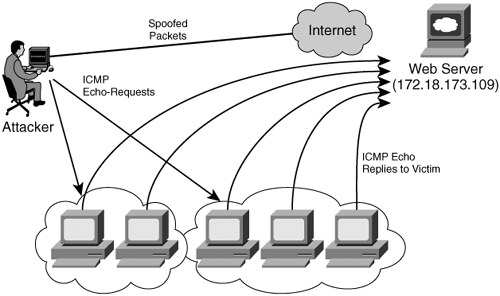
In smurf attacks, ICMP echo request packets are sent to IP broadcast addresses of remote subnets to degrade network performance. Figure 1-6 illustrates the essentials of smurf attacks. In smurf attacks, usually there is an attacker, an intermediary, and a victim (in this case, a web server). If the network is 192.168.1.0 with a 24-bit subnet mask of 255.255.255.0, the broadcast address will be 192.168.1.255. If the ICMP traffic is sent to the broadcast address, all the systems or nodes on the network will receive the ICMP echo request packets and, consequently, send ICMP echo reply packets in return. Additionally, the intermediary can also become the victim, because it receives an ICMP echo request packet sent to the IP broadcast address of its network. Attackers make this technique successful by using spoofed packets. By doing this, the victim responds with ICMP echo reply packets that consume available bandwidth.
Figure 1-6. Smurf Attack Example
DDoS Attacks
DoS attacks may be orchestrated collectively to structure a more sophisticated technique called distributed DoS (DDoS) attacks. DDoS attacks coordinate the use of several systems in different locations to attack a specific victim, making them very difficult to trace. In DDoS attacks, the attackers compromise numerous systems on the Internet by installing malicious code to launch coordinated attacks on victim sites. These compromised systems are often referred as bots (short for robots). These attacks characteristically deteriorate bandwidth and other network resources. Figure 1-7 explains how an attacker compromises numerous systems (agents) on the Internet and then launches a chained attack from them to a target system/network (victim).
Figure 1-7. DDoS Attacks
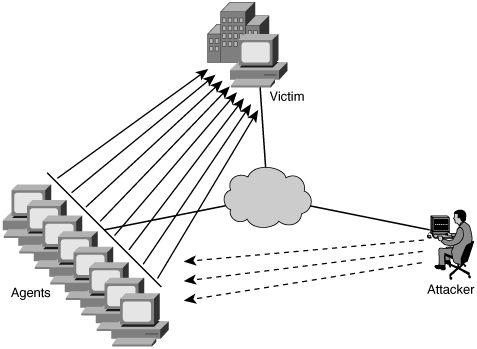
In general, attackers control the agents to generate these packets with spoofed source addresses.
Session Hijacking
Session hijacking occurs when an attacker intercepts a connection or session between two systems. The most common type of session hijacking attack uses TCP-based connections and source-routed packets. In other words, the hacker sits in on a given location on the network to take part in a session between two systems, routing all the TCP packets to pass through its system. Figure 1-8 shows a basic session hijacking example, which is known as a man-in-the-middle attack. An attacker sits in between the hosts and, by using a sniffer, intercepts and routes packets from Host A to Host B without them knowing that the information has been compromised by the attacker.
Figure 1-8. Session Hijacking Example

If an attacker is not able to use source routing, they can also use a method called blind hijacking. By using this technique, the attacker guesses the replies of the two hosts. The only disadvantage to the attacker is that they may send a command and never see its response. However, the attacker can impersonate the receiver of both devices.
Note
Source routing is a technique by which the sender can specify the route that a packet should take through the network.
Part I: Product Overview
Introduction to Network Security
- Introduction to Network Security
- Firewall Technologies
- Intrusion Detection and Prevention Technologies
- Network-Based Attacks
- Virtual Private Networks
- Summary
Product History
- Product History
- Cisco Firewall Products
- Cisco IDS Products
- Cisco VPN Products
- Cisco ASA All-in-One Solution
- Summary
Hardware Overview
Part II: Firewall Solution
Initial Setup and System Maintenance
- Initial Setup and System Maintenance
- Accessing the Cisco ASA Appliances
- Managing Licenses
- Initial Setup
- IP Version 6
- Setting Up the System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Network Access Control
- Network Access Control
- Packet Filtering
- Advanced ACL Features
- Content and URL Filtering
- Deployment Scenarios Using ACLs
- Monitoring Network Access Control
- Understanding Address Translation
- DNS Doctoring
- Monitoring Address Translations
- Summary
IP Routing
Authentication, Authorization, and Accounting (AAA)
- Authentication, Authorization, and Accounting (AAA)
- AAA Protocols and Services Supported by Cisco ASA
- Defining an Authentication Server
- Configuring Authentication of Administrative Sessions
- Authenticating Firewall Sessions (Cut-Through Proxy Feature)
- Configuring Authorization
- Configuring Accounting
- Deployment Scenarios
- Troubleshooting AAA
- Summary
Application Inspection
- Application Inspection
- Enabling Application Inspection Using the Modular Policy Framework
- Selective Inspection
- Computer Telephony Interface Quick Buffer Encoding Inspection
- Domain Name System
- Extended Simple Mail Transfer Protocol
- File Transfer Protocol
- General Packet Radio Service Tunneling Protocol
- H.323
- HTTP
- ICMP
- ILS
- MGCP
- NetBIOS
- PPTP
- Sun RPC
- RSH
- RTSP
- SIP
- Skinny
- SNMP
- SQL*Net
- TFTP
- XDMCP
- Deployment Scenarios
- Summary
Security Contexts
- Security Contexts
- Architectural Overview
- Configuration of Security Contexts
- Deployment Scenarios
- Monitoring and Troubleshooting the Security Contexts
- Summary
Transparent Firewalls
- Transparent Firewalls
- Architectural Overview
- Transparent Firewalls and VPNs
- Configuration of Transparent Firewall
- Deployment Scenarios
- Monitoring and Troubleshooting the Transparent Firewall
- Summary
Failover and Redundancy
- Failover and Redundancy
- Architectural Overview
- Failover Configuration
- Deployment Scenarios
- Monitoring and Troubleshooting Failovers
- Summary
Quality of Service
- Quality of Service
- Architectural Overview
- Configuring Quality of Service
- QoS Deployment Scenarios
- Monitoring QoS
- Summary
Part III: Intrusion Prevention System (IPS) Solution
Intrusion Prevention System Integration
- Intrusion Prevention System Integration
- Adaptive Inspection Prevention Security Services Module Overview (AIP-SSM)
- Directing Traffic to the AIP-SSM
- AIP-SSM Module Software Recovery
- Additional IPS Features
- Summary
Configuring and Troubleshooting Cisco IPS Software via CLI
- Configuring and Troubleshooting Cisco IPS Software via CLI
- Cisco IPS Software Architecture
- Introduction to the CIPS 5.x Command-Line Interface
- User Administration
- AIP-SSM Maintenance
- Advanced Features and Configuration
- Summary
Part IV: Virtual Private Network (VPN) Solution
Site-to-Site IPSec VPNs
- Site-to-Site IPSec VPNs
- Preconfiguration Checklist
- Configuration Steps
- Advanced Features
- Optional Commands
- Deployment Scenarios
- Monitoring and Troubleshooting Site-to-Site IPSec VPNs
- Summary
Remote Access VPN
- Remote Access VPN
- Cisco IPSec Remote Access VPN Solution
- Advanced Cisco IPSec VPN Features
- Deployment Scenarios of Cisco IPSec VPN
- Monitoring and Troubleshooting Cisco Remote Access VPN
- Cisco WebVPN Solution
- Advanced WebVPN Features
- Deployment Scenarios of WebVPN
- Monitoring and Troubleshooting WebVPN
- Summary
Public Key Infrastructure (PKI)
- Public Key Infrastructure (PKI)
- Introduction to PKI
- Enrolling the Cisco ASA to a CA Using SCEP
- Manual (Cut-and-Paste) Enrollment
- Configuring CRL Options
- Configuring IPSec Site-to-Site Tunnels Using Certificates
- Configuring the Cisco ASA to Accept Remote-Access VPN Clients Using Certificates
- Troubleshooting PKI
- Summary
Part V: Adaptive Security Device Manager
Introduction to ASDM
- Introduction to ASDM
- Setting Up ASDM
- Initial Setup
- Functional Screens
- Interface Management
- System Clock
- Configuration Management
- Remote System Management
- System Maintenance
- System Monitoring
- Summary
Firewall Management Using ASDM
- Firewall Management Using ASDM
- Access Control Lists
- Address Translation
- Routing Protocols
- AAA
- Application Inspection
- Security Contexts
- Transparent Firewalls
- Failover
- QoS
- Summary
IPS Management Using ASDM
- IPS Management Using ASDM
- Accessing the IPS Device Management Console from ASDM
- Configuring Basic AIP-SSM Settings
- Advanced IPS Configuration and Monitoring Using ASDM
- Summary
VPN Management Using ASDM
- VPN Management Using ASDM
- Site-to-Site VPN Setup Using Preshared Keys
- Site-to-Site VPN Setup Using PKI
- Cisco Remote-Access IPSec VPN Setup
- WebVPN
- VPN Monitoring
- Summary
Case Studies
EAN: 2147483647
Pages: 231
