Configuring the VPN 3000 Concentrator
Now that I've explained how to configure the Microsoft client, I'll focus on things you need to configure on Cisco VPN 3000 concentrators to support Windows client access. I covered many of these screens in Chapter 8, "Concentrator Remote Access Connections with PPTP, L2TP, and WebVPN," so I'll briefly explain the items that you must create or change to support Microsoft connections in the following sections. Here are the basic items you need to configure or add to your concentrator's configuration:
- IKE Proposals
- IPsec SAs
- Group Configuration: Specific and/or Base Group
- Address Management
- User Configuration
IKE Proposals
First, on your concentrator you need to ensure that you either have created or activated an IKE proposal that will work with the Microsoft L2TP/IPsec client (assuming that you're not using plain L2TP or PPTP). On the concentrator, go to Configuration > Tunneling and Security > IPsec > IKE Proposals.
Proposal names beginning with "CiscoVPNClient" will not work with Microsoft's L2TP/ IPsec clientthe Microsoft client doesn't understand the concept of groups and XAUTH. Therefore, you need to choose a proposal that doesn't do XAUTH authentication, like those beginning with "IKE."
IKE proposals that will work include these properties:
- Authentication mode Pre-shared keys and RSA and DSA certificates
- Authentication algorithm MD5 or SHA1
- Encryption algorithm DES or 3DES
- Diffie-Hellman Group Group 1 or 2
If you'll be using pre-shared keys, two of the included concentrator proposals that will work are IKE-DES-MD5 and IKE-3DES-MD5just make sure you haven't deactivated these security policies for your L2TP/IPsec client (see the "Creating a Security Policy" section earlier in the chapter). Refer to Figures 7-18 and 7-19 in Chapter 7, "Concentrator Remote Access Connections with IPsec" for examples of these screens.
Note
I've experienced a lot of headaches with customizing Microsoft's L2TP/IPsec client. In many instances, I've had to use an IKE Policy that had only DES for encryption, DH group 1 keys, and either MD5 or SHA for an HMAC function because of the quirks in Microsoft's software.
IPsec SAs
Next, on the VPN 3000 concentrator, create an IPsec SA transform that will be used to protect the ISAKMP/IKE Phase 2 data connections for the Windows client. To do this, go to Configuration > Policy Management > Traffic Management > SAs. Click the Add button to add a new SA, and then enter the following for the SA parameters:
- SA Name "ESP-L2TP-Transport," or something similar
- Authentication Algorithm ESP with MD5 or SHA
- Encryption Algorithm DES or 3DES
- Encapsulation Mode Transport
- Perfect Forward Secrecy Disabled (this can be enabled if you enabled it on the Windows client)
- Lifetime Measurement Time
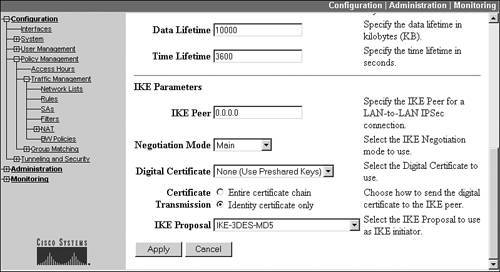
- IKE Peer 0.0.0.0
- Negotiation Mode Main
- Digital Certificate Either the name of the certificate to use, if certificates will be used for authentication, or "None (Use Preshared Keys)"
- IKE Proposal The name of the IKE proposal you created in the last section.
Click the Add button to add your new SA. Figures 13-19 and 13-20 show an example IPsec SA that is used by L2TP/IPsec clients.
Figure 13-19. SA Configuration: Top of Screen
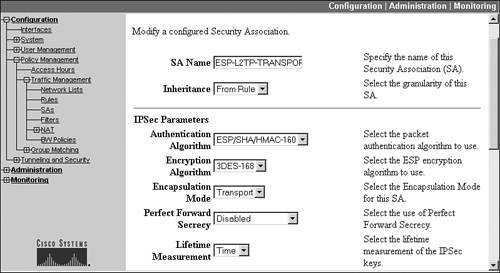
Figure 13-20. SA Configuration: Bottom of Screen
Note
I'd like to point out two important pieces of information regarding the setup of your data SA for L2TP/IPsec clients. First, the encapsulation mode must be set to transport mode, not tunnel. Second, I've experienced with some Windows platforms that in some cases, no matter what IKE Proposal you choose from this screen, the only one that the L2TP/IPsec client will use is one with DES and either MD5 or SHA. Even if you don't specify it here, this IKE Proposal must be activated in the IKE Proposal screen on the concentratorthis never made any sense to me because the concentrator basically ignores what you have configured on this screen for the IKE Proposal!
Group Configuration
If your L2TP/IPsec clients are using pre-shared keys, the concept of a group is nonexistent; therefore, you'll need to configure these clients' remote access properties in the concentrator's Base Group. Otherwise, if the clients are using certificates, whatever name appears in the OU (Organizational Unit) field is the name of the group you'll need to configure on the concentrator; then configure this group for these users.
Note
You can also use the certificate/group matching feature of the concentrator to examine other certificate fields, and based on the matching rules you create, put a user into a specific, or even a default, group.
In this section, assume that pre-shared keys are being used and that you'll need to configure the Base Group (the configuration is the same for the Base Group versus a specific group). To configure the Base Group, go to Configuration > User Management > Base Group and then perform the following:
|
1. |
Click the General Tab and choose the Tunneling Protocols you want these users to use, such as L2TP over IPsec, L2TP, or PPTP, depending on the security protocol(s) your Microsoft clients will be using. Deselect the ones you won't be using. If the clients will be sending the Windows domain name with their authentication, and the concentrator will be performing internal authentication, select the check box for Strip Realm. |
|
2. |
Click the IPsec tab. For the IPsec SA parameter, use the pull-down selector and choose the name of the SA you created in the last section, such as "ESP-L2TP-Transport." If you'll be defining the users on the concentrator, then select "Internal" for the Authentication parameter. In most cases, you'll probably use "NT Domain" or "Kerberos Active Directory," because these are Microsoft users; if this is the case, then you'll need to add these servers to the concentrator by going to Configuration > System > Servers > Authentication. If you're using pre-shared keys for device authentication, set the Default Preshared Key parameter under the IPsec tab to match the pre-shared key the L2TP/IPsec clients will use. |
|
3. |
Click the PPTP/L2TP tab. If clients will be using their own internally assigned address (which I wouldn't recommend), click the Use Client Address check box. If you'll be using PPTP, select the correct protocols for the PPTP Authentication Protocols parameter. To ensure that encryption is used for PTTP, select "Required" for PPTP Encryption and both 40-bit and 128-bit encryption if you're not sure which of the two clients will use. By using encryption, PPTP will only use MS-CHAPv1 or v2 for authentication (this is also true of L2TP). For L2TP or L2TP/IPsec clients, choose the correct L2TP Authentication Protocols and the correct L2TP Encryption algorithms. |
The screens and their contents discussed above are found throughout Chapter 7, "Concentrator Remote Access Connections with IPsec," and Chapter 8, "Concentrator Remote Access Connections with PPTP, L2TP, and WebVPN."
Caution
If you are using pre-shared keys, then because all clients are placed in the Base Group, they all must use the same pre-shared key, which might introduce security risks. A better approach would be to use certificates for authentication. Your IPsec SA and IKE proposal would have to reflect this configuration, though.
Address Management
If the concentrator will be assigning addresses to the Windows client for the VPN connection, you'll need to create an address pool. For the Base Group (pre-shared key authentication), go to Configuration > System > Address Management > Address Pools. Click the Add button to add a new address pool. In the Range Start text box, enter the beginning IP address in the pool; in the Range End text box, enter the ending address in the pool; and in the Subnet Mask text box, enter the subnet mask associated with the pool of addresses. Click the Add button when done.
For certificate authentication, if you choose to use specific groups, you can create an address pool per group. First, create the group from the Configuration > User Management > Groups screen and configure the group. Once you have configured it (as discussed in the last section), from the specific group listing screen, click the name of the group, and then click the Address Pools button. Click the Add button to add a new address pool for the group, and follow the instructions in the last paragraph.
Note
Please note that you can also use an external DHCP or AAA server to assign addresses to the Windows clients, as discussed in Chapter 7. If clients always need to have the same IP address assigned to them, instead of manually assigning it on the client, I would use AAA RADIUS for authentication and have the AAA server assign the address to the client.
User Configuration
If you'll be defining the PPTP, L2TP, or L2TP/IPsec users locally on the concentrator, go to Configuration > User Management > Users and click the Add button. Refer to Chapters 7 and 8, for snapshots of the following screens. Under the Identity tab, enter the name of the users along with their passwords. For the Group parameter, specify the name of the group the users belong to (for pre-shared key authentication, this must be the Base Group). If you always want to assign the same IP address to a user, enter the IP address and subnet mask under this tab (I recommend not letting the users assign their own addresses on the client). There are also General, IPsec, and PPTP/L2TP tabs, where you can override the properties of group the users belong to: otherwise, the users' accounts will inherit the configuration properties from the group name you specified under the Identity tab. Click the Add button at the bottom of the screen to add the users.
Part I: VPNs
Overview of VPNs
- Overview of VPNs
- Traffic Issues
- VPN Definition
- VPN Components
- VPN Designs
- VPN Implementations
- VPNs: Choosing a Solution
- Summary
VPN Technologies
IPsec
PPTP and L2TP
SSL VPNs
Part II: Concentrators
Concentrator Product Information
- Concentrator Product Information
- Concentrator Models
- Concentrator Modules
- Concentrator Features
- Introduction to Accessing a Concentrator
- Summary
Concentrator Remote Access Connections with IPsec
- Concentrator Remote Access Connections with IPsec
- Controlling Remote Access Sessions to the Concentrator
- IPsec Remote Access
- Network Access Control (NAC) for IPsec and L2TP/IPsec Users
- Summary
Concentrator Remote Access Connections with PPTP, L2TP, and WebVPN
- Concentrator Remote Access Connections with PPTP, L2TP, and WebVPN
- PPTP and L2TP Remote Access
- WebVPN Remote Access
- Summary
Concentrator Site-to-Site Connections
- Concentrator Site-to-Site Connections
- L2L Connectivity Example
- ISAKMP/IKE Phase 1 Preparation
- Adding Site-to-Site Connections
- Address Translation and L2L Sessions
- Summary
Concentrator Management
- Concentrator Management
- Bandwidth Management
- Routing on the Concentrator
- Chassis Redundancy
- Administration Screens
- Summary
Verifying and Troubleshooting Concentrator Connections
- Verifying and Troubleshooting Concentrator Connections
- Concentrator Tools
- Troubleshooting Problems
- Summary
Part III: Clients
Cisco VPN Software Client
- Cisco VPN Software Client
- Cisco VPN Client Overview
- Cisco VPN Client Interface
- IPsec Connections
- VPN Client GUI Options
- VPN Client Software Updates
- VPN Client Troubleshooting
- Summary
Windows Software Client
- Windows Software Client
- Windows Client
- Configuring the Windows VPN Client
- Configuring the VPN 3000 Concentrator
- Microsoft Client Connections
- Troubleshooting VPN Connections
- Summary
3002 Hardware Client
- 3002 Hardware Client
- Overview of the 3002 Hardware Client
- Initial Access to the 3002
- Authentication and Connection Options
- Connection Modes
- Administrative Tasks
- Summary
Part IV: IOS Routers
Router Product Information
Router ISAKMP/IKE Phase 1 Connectivity
- Router ISAKMP/IKE Phase 1 Connectivity
- IPsec Preparation
- ISAKMP/IKE Phase 1 Policies
- ISAKMP/IKE Phase 1 Device Authentication
- Monitoring and Managing Management Connections
- Routers as Certificate Authorities
- Summary
Router Site-to-Site Connections
- Router Site-to-Site Connections
- ISAKMP/IKE Phase 2 Configuration
- Viewing and Managing Connections
- Issues with Site-to-Site Connections
- Summary
Router Remote Access Connections
- Router Remote Access Connections
- Easy VPN Server
- Easy VPN Remote
- IPsec Remote Access and L2L Sessions on the Same Router
- WebVPN
- Summary
Troubleshooting Router Connections
- Troubleshooting Router Connections
- ISAKMP/IKE Phase 1 Connections
- ISAKMP/IKE Phase 2 Connections
- New IPsec Troubleshooting Features
- Fragmentation Problems
- Summary
Part V: PIX Firewalls
PIX and ASA Product Information
- PIX and ASA Product Information
- PIX Deployment Scenarios
- PIX and ASA Feature and Product Overview
- Summary
PIX and ASA Site-to-Site Connections
- PIX and ASA Site-to-Site Connections
- ISAKMP/IKE Phase 1 Management Connection
- ISAKMP/IKE Phase 2 Data Connections
- L2L Connection Examples
- Summary
PIX and ASA Remote Access Connections
- PIX and ASA Remote Access Connections
- Easy VPN Server Support for 6.x
- Easy VPN Remote Support for 6.x
- Easy VPN Server Support for 7.0
- Summary
Troubleshooting PIX and ASA Connections
- Troubleshooting PIX and ASA Connections
- ISAKMP/IKE Phase 1 Connections
- ISAKMP/IKE Phase 2 Connections
- Summary
Part VI: Case Study
Case Study
Index
EAN: 2147483647
Pages: 178
