Understanding Proxying Firewalls
Before the rise of application servers, distributed objects were deployed in a distributed environment across an organization's enterprise systems. An example of these objects is RMI, CORBA, and DCOM. These objects are not governed by a set of a few application servers, but can be distributed across many machines. Naming servers are required for distributed objects to resolve their location and interfaces. There can be multiple backups across an enterprise in case one of the naming servers goes down. For enterprise beans, the Java Naming and Directory Interface (JNDI) resembles a naming server. See Figure 21-15 for an example. 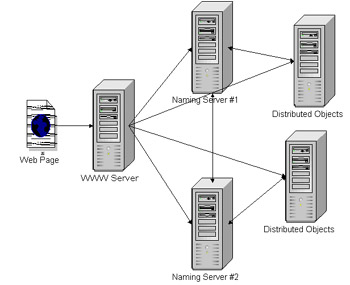 Figure 21-15: Distributed objects Figure 21-15 illustrates a Web server connecting to the distributed object after doing a lookup on the naming server. When distributed objects are created, they may require a new port. A newly created port is used as a location of the distributed object on a machine. The use of distributed object prohibits the use of a backend firewall because it may block a newly created port when an object is dynamically created. To counteract the issue, many application servers and distributed systems may have plug-ins for Web servers and proxy devices for firewalls. The purpose of many plug-ins is to act as an intermediate device between the Web server, the naming server, and the distributed objects. CORBA uses the General Inter-ORB Protocol (GIOP) proxy for tunneling through firewalls. The GIOP protocol resolves the objects into eight basic messages. GIOP works as the underlying message architecture that transports the objects on top of TCP/IP. See Figure 21-16 for an example of a GIOP proxy. 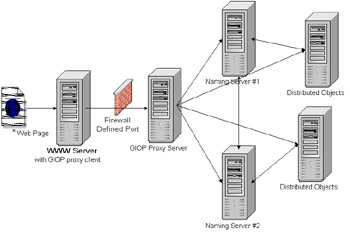 Figure 21-16: The GIOP proxy The figure displays a CORBA plug-in on the WWW server that will act as the CORBA naming server and distributed objects messaging to a GIOP server. The GIOP server will use the messages and act as the client communicating to enterprise environment. When the naming server or Object Request Broker (ORB) responds to the GIOP proxy server, the GIOP proxy server will pass these objects as messages through return path of the firewall, and the GIOP client proxy will respond to the WWW server as the naming server and objects. A more generic proxying device is to transmit a SOAP structure message through a firewall using HTTPS. The Simple Object Access Protocol (SOAP) provides a mapping of objects to XML. SOAP was built on top of XML for RPC, but XML for RPC provided the XML interface to methods instead of objects. The SOAP interface requires a client that maps the object calls into a SOAP message and a server side that will execute the distributed objects from the SOAP message and respond with the results. See Figure 21-17 for a SOAP proxy. 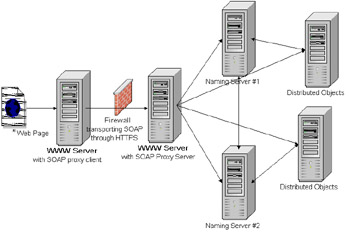 Figure 21-17: The SOAP proxy By using the SOAP proxy, instead of a GIOP messaging structure, the SOAP XML stream can be passed between two Java Servlets using HTTPS. Using Java Servlets can make the development cycle easier than defining a protocol. HTTPS could be used to provide extra security to ensure that the message derived from the SOAP proxy client and that the SOAP proxy server is authenticated. The SOAP document would have to be parsed out by the servlet and execute the distributed objects. The servlet would act a controller pattern to execute the correct objects based on the SOAP stream. Many application servers are shipped with proxy plug-ins for tunneling through firewalls. They may incorporate a multitude of means in order to narrow the ports through a firewall. If an application server executes only on a selected port, then the job of proxying is an easier task. Some plug-ins may require extra authentication such as HTTPS to ensure that a hacker is not simulating the client and server. If the enterprise system is not supporting a backend firewall, then any process being executed from the Web server farm may potentially access any port in the enterprise system. Limiting the traffic to only selected ports narrows the possibilities for potential attacks.
Java Security Solutions ISBN: 0764549286
EAN: 2147483647 Year: 2001
Pages: 222 Authors: Rich Helton, Johennie Helton
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |