Domain 6 Basic Networking
CompTIA A+ Exam Objectives Covered in This Chapter
- 6.1 Identify the common types of network cables, their characteristics and connectors.
- 6.2 Identify basic network concepts including how a network works.
- 6.3 Identify common technologies available for establishing Internet connectivity and their characteristics.
The A+ exam will test your basic networking skills—those skills needed to effectively troubleshoot and repair desktop PCs in a corporate environment. To pass the test and be effective in your troubleshooting, you need to understand the basic concepts and terminology in this chapter. This objective has been greatly expanded in the latest exam revision and has been split into three subobjectives, whereas it had previously been a single one.
Identifying Network Cables
The latest revision of the A+ exam increases the number of cable and connector types that it specifically lists in the objective. You should be able to identify various connector types by sight and specify which cable should be used with which network systems.
Critical Information
When data travels between network nodes, it uses cable (or wireless infrared or radio frequency [RF] signal). The cabling you choose must support both the network architecture and topology. There are three main types of cabling methods: twisted-pair cable, coaxial cable, and fiber optic cable.
Twisted-Pair
Twisted-pair is one of the most popular methods of cabling because of its flexibility and low costs. It consists of several pairs of wire twisted around each other within an insulated jacket, as shown in Figure 6.1. Twisted-pair is most often found in 10/100BaseT Ethernet networks, although other systems can use it.
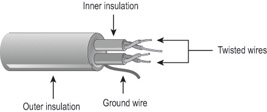
Figure 6.1: Twisted-pair cable
Twisted-pair cable can be unshielded (UTP) or shielded (STP). This refers to its level of protection against electromagnetic interference (EMI). STP has a braided foil shield around the twisted wires, whereas UTP does not.
Unshielded Twisted-Pair (UTP)
UTP comes in several grades to offer different levels of protection against electrical interference:
- Category 1—For voice-only transmissions. Used in most phone systems today. It contains two twisted pairs.
- Category 2—Transmits data at speeds up to 4Mbps. It contains four twisted pairs of wires.
- Category 3—Transmits data at speeds up to 10Mbps. It contains four twisted pairs of wires with three twists per foot.
- Category 4—Transmits data at speeds up to 16Mbps. It contains four twisted pairs of wires.
- Category 5—Transmits data at speeds up to 100Mbps. It contains four twisted pairs of copper wire to give the most protection.
- Category 5e—Transmits data at speeds up to 1Gbps. It also contains four twisted pairs of copper wire, but they are physically separated and contain more twists per foot than Category 5 to provide maximum interference protection.
- Category 6—Transmits data at speed up to 2Gbps. It contains four twisted pairs of copper wire.
Most network UTP cable uses RJ-45 connectors, which are like fat versions of telephone connectors. Instead of two or four metal tabs on the connector like a phone cable has, the RJ-45 connector has eight.
Shielded Twisted Pair (STP)
STP cable is differentiated by type, rather than category, and uses an IBM Data Connector (IDC) or Universal Data Connector (UDC) connector on one end for connecting to the Token Ring network. The types for STP cable are:
- Type 1—The most common STP cable type. Contains two pairs.
- Type 2—Like Type 1 but adds two pairs of voice wires.
- Type 3—Contains four pairs.
- Type 6—Patch cable, used for connecting token ring hubs.
- Type 8—A flat type of STP cable used for running under carpets.
- Type 9—A two-pair, high-grade type of STP.
Coaxial
The next choice of cable for most LANs is coaxial cable. The cable consists of a copper wire surrounded by insulation and a metal foil shield, as shown in Figure 6.2. It is very similar to the cable used to connect cable television.
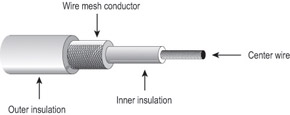
Figure 6.2: Coaxial cable
Another name for coaxial cable is RG. Coaxial cable comes in many thicknesses and types, including these:
- RG-58—50-ohm cable. Used for 10Base2 (Thinnet) Ethernet.
- RG-59—75-ohm cable. Used for broadband transmission such as cable TV.
- RG-6—Used for satellites. A double- or quad-shielded cable that offers superior performance and minimal signal leakage.
- RG-8—50-ohm cable. Used for 10Base5 (Thicknet) Ethernet.
The connectors on coaxial cable are usually BNC (Bayonet Neil Connector or British Naval Connector), a connector that may be familiar to cable television users. It consists of a metal wire core in the center with a threaded metal ring around it. An exception: 10Base5 (Thicknet) coaxial cable uses an AUI (Attachment Unit Interface) connector to connect to the PC network card.
Fiber Optic
Fiber optic cabling consists of a thin, flexible glass fiber surrounded by a rubberized outer coating (see Figure 6.3). It provides transmission speeds from 100Mbps up to 1Gbps and a maximum distance of several miles. Because it uses pulses of light instead of electric voltages to transmit data, it is completely immune from electric interference and from wiretapping.
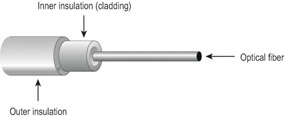
Figure 6.3: Fiber optic cable
Fiber optic cable has not become a standard in networks, however, because of its high cost of installation. Networks that need extremely fast transmission rates, transmissions over long distances, or have had problems with electrical interference in the past often use fiber optic cabling.
There are several types of fiber optic cable, differentiated by their fiber thickness, coating thickness, and mode (single or multi). A single-mode cable uses injection laser diodes (ILDs) to send data. It is a high-bandwidth, expensive cable. Multimode cable uses light-emitting diodes (LEDs).
Fiber optic cable can use either ST or SC connectors. ST is a barrel-shaped connector; SC is a newer, squared type that is easier to connect in a cramped space.
Summary of Cabling Types
Each type of cabling has its own benefits and drawbacks. Table 6.1 details the most common types of cabling in use today. As you look at this table, pay particular attention to the cost, length, and maximum transmission rates of each cabling type.
|
Characteristics |
Unshielded Twisted-Pair |
Shielded Twisted-Pair |
Coaxial |
Fiber Optic |
|---|---|---|---|---|
|
Cost |
Least expensive |
Moderate |
Moderate |
Expensive |
|
Maximum Length |
100m (328ft) |
100m (328ft) |
185m (607ft) to 500m (1640ft) |
>10 miles |
|
Transmission Rates |
10Mbps to 2Gbps |
10Mbps to 2Gbps for Ethernet, Fast Ethernet and Gigabit Ethernet. 16Mbps for Token Ring |
10Mbps |
100Mbps or more |
|
Flexibility |
Most flexible |
Fair |
Fair |
Fair |
|
Ease of Installation |
Very easy |
Very easy |
Easy |
Difficult |
|
Interference |
Susceptible |
Not susceptible |
Moderate |
Not susceptible |
|
Special Features |
Various categories; must choose the right kind for the job |
Various types; must choose the right kind for the job |
Supports voice, data, and video at highest transmission speeds |
|
|
Preferred Uses |
10/100/1000BaseT |
10/100/1000BaseT or Token Ring |
10Base2, 10Base5 |
Network segments requiring high-speed transmission |
|
Connector |
RJ-45 |
RJ-45 for Ethernet; IDC/UDC for Token Ring |
BNC or AUI |
ST/SC |
|
Physical Topology |
Star |
Star or ring |
Bus |
Star (typically) |
Exam Essentials
Know the cable types for Ethernet networks.Given the task of cabling a 100BaseT, 10Base5, or 10Base2 network, you should be able to specify the types of cable you would need and their connectors.
Know the UTP categories.Understand the situations for which Cat3, Cat5, Cat5e, and Cat6 cable would be required.
Understanding Basic Network Concepts
This objective tests your knowledge of basic networking terms and concepts such as networking models and protocols, as well as practical skills like installing a NIC and physically connecting a network.
Critical Information
A network links two or more computers together to communicate and share resources. A computer network allows computers to link to each other’s resources. For example, in a network every computer does not need a printer connected locally to print. Instead, one computer can have a printer connected to it and allow the other computers to access this resource. Because they allow users to share resources, networks offer an increase in performance as well as a decrease in the outlay for new hardware and software.
LANs vs. WANs
A local area network (LAN) is a network within a limited area, such as a single office. Wide area networks (WANs) expand the LANs to include networks outside of the local environment and also to distribute resources across distances.
Network Types
There are two basic network types: client/server and peer-to-peer:
Client/ServerA network that has one or more computers dedicated for use as a server, with a special server operating system and responsibilities. Can be any size, but typically has 10 or more client computers. See Figure 6.4.
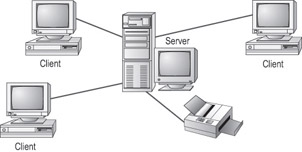
Figure 6.4: The server-based model
Peer-to-PeerA network in which all computers are clients, or equal participants, with no server. Usually limited to 10 or fewer computers. See Figure 6.5.

Figure 6.5: The peer-to-peer model
Servers
The server is a core component of a client/server network, providing a link to the resources necessary to perform a task. For example, a server might route requests between clients, deliver centrally stored files, provide Internet access, or deliver a print job to a printer.
Servers offer networks the capability of centralizing the control of resources and can thus reduce administrative difficulties. They can be used to distribute processes for balancing the load on the computers, thereby increasing speed and performance. They can also departmentalize files for improved reliability. That way, if one server goes down, not all of the files are lost.
Servers perform several tasks. For example, servers that provide files to the users on the network are called file servers. Likewise, servers that host printing services for users are called print servers. (There are other tasks as well, such as remote access services, administration, mail, and so on.) Servers can be multipurpose or single-purpose. If they are multipurpose, they can be, for example, both a file server and a print server at the same time. If the server is a single-purpose server, it is a file server only or a print server only.
Clients
Clients are the computers on which the users on a network do their work, such as word processing, database design, graphic design, e-mail, and other office or personal tasks. Clients are regular computers, except for the fact that they are connected to a network that offers additional resources. As clients, they are allowed to communicate with the servers in the network in order to use the network’s resources.
In some companies, thin clients are used to save expenses. A thin client is a computer that lacks some component, such as disk storage, such that it can’t function very well as a stand-alone model. It relies on the network server to make up for its deficiency.
A network client must have a network interface card (NIC), a special expansion card that allows the PC to talk on a network. The NIC is then connected to the network via cable (see Objective 6.1). And you must install some special software, called client software, which allows the computer to talk to the network. Once you’ve accomplished all this, the computer will be on the network.
The purpose of a client being connected to the network is to participate in the pool of shared resources available there. A resource (as far as the network is concerned) is any item that can be used on a network. Resources can include a broad range of items, including printers, files, applications, and disk storage space.
Network Topologies
A topology is a way of laying out the network. Topologies can be either physical or logical. Physical topologies describe how the cables are run. Logical topologies describe how the network messages travel. Deciding which type of topology to use is the next step when designing your network.
You must choose the appropriate topology in which to arrange your network. Each type differs by its cost, ease of installation, fault tolerance (how the topology handles problems like cable breaks), and ease of reconfiguration (like adding a new workstation to the existing network).
There are five primary topologies (some of which can be both logical and physical):
- Bus (can be both logical and physical)
- Star (physical only)
- Ring (can be both logical and physical)
- Mesh (can be both logical and physical)
- Hybrid (usually physical)
Each topology has advantages and disadvantages. At the end of this section, check out the table that summarizes the advantages and disadvantages of each topology.
Bus
A bus is the simplest physical topology. It consists of a single cable that runs to every workstation, as shown in Figure 6.6. This topology uses the least amount of cabling but also covers the shortest distance. Each computer shares the same data and address path. With a logical bus topology, messages pass through the trunk, and each workstation checks to see if the message is addressed to itself. If the address of the message matches the workstation’s address, the network adapter copies the message to the card’s on-board memory.
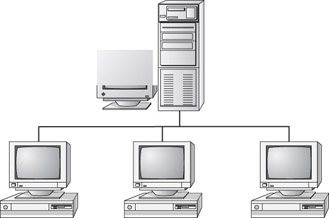
Figure 6.6: The bus topology
Cable systems that use the bus topology are easy to install. You run a cable from the first computer to the last computer. All the remaining computers attach to the cable somewhere in between. Because of the simplicity of installation, and because of the low cost of the cable, bus topology cabling systems (such as 10Base2 and 10Base5 Ethernet) are the cheapest to install.
Although the bus topology uses the least amount of cabling, it is difficult to add a workstation to this configuration. If you want to add another workstation, you have to completely reroute the cable and possibly run two additional lengths of it. Also, if any one of the cables breaks, the entire network is disrupted. Therefore, it is very expensive to maintain.
Star
A physical star topology branches each network device off a central device called a hub, making it very easy to add a new workstation. Also, if any workstation goes down, it does not affect the entire network. (But, as you might expect, if the central device goes down, the entire network goes down.) Modern Ethernet (10BaseT, 100BaseT, and Gigabit Ethernet) uses a physical star topology, as does Token Ring. Figure 6.7 gives an example of the organization of the star network.
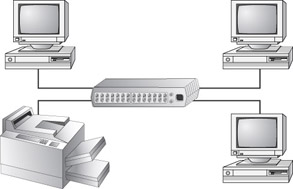
Figure 6.7: The star topology
Star topologies are easy to install. A cable is run from each workstation to the hub. The hub is placed in a central location in the office (for example, a utility closet). Star topologies are more expensive to install than bus networks because several more cables need to be installed, in addition to the cost of the hubs that are required.
Ring
A physical ring topology is a unique topology. Each computer connects to two other computers, joining them in a circle, creating a unidirectional path where messages move from workstation to workstation. Each entity participating in the ring reads a message, then regenerates it and hands it to its neighbor on a different network cable. See Figure 6.8 for an example of a ring topology.
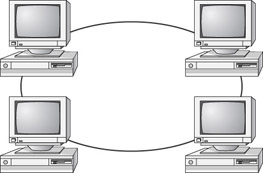
Figure 6.8: The ring topology
The ring makes it difficult to add new computers. Unlike a star topology network, the ring topology network will go down if one entity is removed from the ring. Few physical ring topology systems still exist, mainly because the hardware involved was fairly expensive and the fault tolerance was very low. However, one type of logical ring still exists: IBM’s Token Ring technology. We’ll discuss this technology later in the “Network Architectures” section.
Mesh
The mesh topology is the simplest logical topology, in terms of data flow, but it is the most complex in terms of physical design. In this physical topology, each device is connected to every other device, as shown in Figure 6.9. This topology is rarely found in LANs, mainly because of the complexity of the cabling. If there are x computers, there will be (x (x–1)) 2 cables in the network. For example, if you have five computers in a mesh network, it will use 5 (5 – 1) 2, which equals 10 cables. This complexity is compounded when you add another workstation. For example, your 5-computer, 10-cable network will jump to 15 cables just by adding one more computer. Imagine how the person doing the cabling would feel if you told them you had to cable 50 computers in a mesh network—they’d have to come up with 50 (50 – 1) 2 = 1,225 cables!
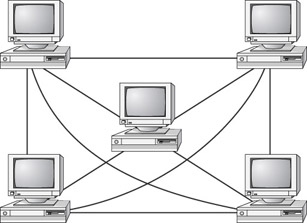
Figure 6.9: The mesh topology
Because of its design, the physical mesh topology is very expensive to install and maintain. Cables must be run from each device to every other device. The advantage you gain from it is high fault tolerance. With a logical mesh topology, there will always be a way of getting the data from source to destination. It may not be able to take the direct route, but it can take an alternate, indirect route. For this reason, the mesh topology is still found in WANs to connect multiple sites across WAN links. It uses devices called routers to search multiple routes through the mesh and determine the best path. However, the mesh topology does become inefficient with five or more entities.
Hybrid
The hybrid topology is simply a mix of the other topologies. It would be impossible to illustrate it, because there are many combinations. Most networks today are not only hybrid, but heterogeneous (by heterogeneous I mean they include a mix of components of different types and brands). The hybrid network may be more expensive than some types of network topologies, but, on the other hand, it takes the best features of all the other topologies and exploits them.
Summary of Topologies
Table 6.2 summarizes the advantages and disadvantages of each type of network topology. This table is a good study aid for the A+ exam. (In other words, memorize it!)
|
Topology |
Advantages |
Disadvantages |
|---|---|---|
|
Bus |
Cheap. Easy to install. |
Difficult to reconfigure. A break in the bus disables the entire network. |
|
Star |
Cheap. Easy to install. Easy to reconfigure. Fault tolerant. |
More expensive than bus. |
|
Ring |
Efficient. Easy to install. |
Reconfiguration is difficult. Very expensive. |
|
Mesh |
Simplest. Most fault tolerant. |
Reconfiguration is extremely difficult. Extremely expensive. Very complex. |
|
Hybrid |
Combines the best features of each topology used. |
Complex (less so than mesh, however). |
Network Protocols
You have chosen the type of network and arrangement (topology). Now the computers need to understand how to communicate. Network communications use protocols. A protocol is a set of rules that govern communications. Protocols detail which language the computers are speaking when they talk over a network. If two computers are going to communicate, they both must be using the same protocol.
TCP/IP
The most common protocol used today is Transmission Control Protocol/Internet Protocol (TCP/IP). It is used for Microsoft networking and also for the Internet. This is actually not one single protocol, but rather a suite of interrelated protocols and standards.
TCP/IP uses IP addresses to uniquely identify each computer on the network. An IP address is a string of four numbers (between 1 and 255) separated by periods, like this: 192.168.2.200. It is a single 64-bit binary string of digits, but is broken up and converted to decimal for ease of use.
A portion of the IP address represents the domain (group) that the resource belongs to, much like an area code in a phone number; this is called its network address. Another portion represents its unique address within that group; this is called its host address.
Unlike in a phone number, however, the dividing point between the network address and the host address is not a fixed point. It varies depending on the subnet mask that is used. The subnet mask specifies where the dividing line is between the network and host portions of the IP address. For example, in the IP address 192.168.2.200, if the subnet mask was 255.255.0.0, then 192.168 would be the network portion of the IP address and 2.200 would be the host address.
IP addresses may be assigned to a PC statically (that is, manually entered at each PC), or dynamically through a Dynamic Host Configuration Protocol (DHCP) server. This is a server utility that assigns IP addresses to each client as it logs on to the network according to assignment rules that the network administrator configures.
IPX/SPX
Stands for Internet Packet eXchange/Sequenced (or Sequential) Packet eXchange. This protocol is for Netware networks, and is seldom used anymore because most networking is Microsoft-based. Windows provides an IPX/SPX-compatible protocol that enables a PC to connect to a Novell Netware network, but it does not install it by default in the newer Windows versions.
AppleTalk
This protocol enables a computer to connect to a Macintosh-based network. It is not installed by default, and the necessary software does not come with Windows, so it must be obtained from Apple. We’ll discuss AppleTalk more in the “Network Architectures” section later in this chapter.
NetBEUI/NetBIOS
NetBIOS Extended User Interface (NetBEUI) is an older protocol for Windows networking. It has some limitations, such as being unable to work with routers, that make it unsuitable for large-scale networking, but it is a very fast and efficient protocol.
With NetBEUI, each computer is known by a NetBIOS name rather than an IP address. This is a plain-text name. When you enter a computer name in the networking properties in Windows, it will use that name as a NetBIOS name when communicating through a NetBEUI-enabled network.
Network Architectures
Network architectures define the structure of the network, including hardware, software, and layout. We differentiate each architecture by the hardware and software required to maintain optimum performance levels. The major architectures in use today are Ethernet, Token Ring, and AppleTalk.
Ethernet
Ethernet has several specifications, each one specifying the speed, communication method, and cable. The original Ethernet was given a designation of 10Base5. The 10 in Ethernet 10Base5 stands for the 10Mbps transmission rate, Base stands for the baseband communications used, and 5 stands for the maximum distance of 500 meters. This method of identification soon caught on, and as vendors changed the specifications of the Ethernet architecture, they followed the same pattern in the way they identified them.
After the 10Base5 came 10Base2 and 10BaseT. These quickly became standards in Ethernet technology. Many other standards (including 100BaseF, 10BaseF, and 100BaseT) have developed since then, but those three are the most popular.
Ethernet 10Base2 uses thin coaxial cables (1/4-inch) and bus topology and transmits at 10Mbps, with a maximum distance of 185 meters. Ethernet 10BaseT uses twisted-pair cabling (T stands for twisted), transmitting at 10Mbps, with a maximum distance of 100 meters, and physical star topology with a logical bus topology. 100BaseT Ethernet is the same except that it works at 100Mbps.
Token Ring
Token Ring uses a physical star, logical ring topology. All workstations are cabled to a central device, called a multistation access unit (MAU). The ring is created within the MAU by connecting every port together with special circuitry. Token Ring can use shielded or unshielded cable and can transmit data at either 4Mbps or 16Mbps.
AppleTalk
AppleTalk is a proprietary network architecture for Macintosh computers. It uses a bus and either shielded or unshielded cable. There are a few things to note about AppleTalk.
AppleTalk uses a Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) technology to put data on the cable. Unlike Ethernet, which uses a Carrier Sense Multiple Access with Collision Detection (CSMA/CD) method, this technology uses “smart” interface cards to detect traffic before it tries to send data. A CSMA/CA card listens to the wire. If there is no traffic, it sends a small amount of data. If no collisions occur, it follows that amount of data with the data it wants to transmit. In either case, if a collision happens, it backs off for a random amount of time and tries to transmit again.
Another interesting point about AppleTalk is that it’s fairly simple. Most Macintosh computers already include AppleTalk, so it is relatively inexpensive. It assigns itself an address. In its first revision (Phase I), it allowed a maximum of 32 devices on a network. With its second revision (Phase II), it supports faster speeds and multiple networks with EtherTalk and TokenTalk. EtherTalk allows AppleTalk network protocols to run on Ethernet coaxial cable (used for Mac II and above.) TokenTalk allows the AppleTalk protocol to run on a Token Ring network.
The Network Interface Card
The network interface card (NIC) provides the physical interface between computer and cabling. It prepares data, sends data, and controls the flow of data. It can also receive and translate data into bytes for the CPU to understand. It communicates at the Physical layer of the OSI model and comes in many shapes and sizes.
Installation
The physical installation of a NIC is the same as with any other internal circuit board. It fits into an ISA or PCI expansion slot in the motherboard.
When choosing a NIC, use one that fits the bus type of your PC. If you have more than one type of bus in your PC (for example, a combination ISA/PCI), use a NIC that fits into the fastest type (PCI, in this case). This is especially important in servers, because the NIC can quickly become a bottleneck if this guideline isn’t followed.
Configuration
The NIC’s configuration includes such things as a manufacturer’s hardware address, IRQ address, base I/O port address, and base memory address. Some NICs may also use DMA channels to offer better performance.
Each card has a unique hardware address, called a media access control (MAC) address, which is hard-wired into the card during its manufacture. It consists of six two-digit hexadecimal numbers; the first three represent the manufacturer and the second three are the unique serial number of the card. The MAC address is separate from any logical address that might be assigned to the PC by the networking system, such as an IP address.
Configuring a NIC is similar to configuring any other type of expansion card. The NIC usually needs a unique IRQ channel and I/O address, and possibly a DMA channel. Token Ring cards often have two memory addresses that must be allocated in reserved memory for them to work properly.
Drivers
For the computer to use the NIC, it is very important to install the proper device drivers. These drivers communicate directly with the network redirector and adapter. They operate in the Media Access Control sublayer of the Data Link layer of the OSI model.
Media Access Methods
You have put the network together in a topology. You have told the network how to communicate and send the data, and you have told it how to send the data to another computer. You also have the communications medium in place. The next problem you need to solve is how to put the data on the cable. What you need now are the cable access methods, which define a set of rules for how computers put data on and retrieve it from a network cable. The four methods of data access are shown here:
- Carrier Sense Multiple Access with Collision Detection (CSMA/CD)
- Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA)
- Token passing
- Polling
Carrier Sense Multiple Access with Collision Detection
As we’ve already discussed, NICs that use CSMA/CD listen to, or “sense,” the cable to check for traffic. They compete for a chance to transmit. Usually, if access to the network is slow, it means that too many computers are trying to transmit, causing traffic jams.
Carrier Sense Multiple Access with Collision Avoidance
Instead of monitoring traffic and moving in when there is a break, CSMA/CA allows the computers to send a signal that they are ready to transmit data. If the ready signal transmits without a problem, the computer then transmits its data. If the ready signal is not transmitted successfully, the computer waits and tries again. This method is slower and less popular than CSMA/CD.
Token Passing
As previously discussed, token passing is a way of giving every NIC equal access to the cable. A special packet of data is passed from computer to computer. Any computer that wants to transmit has to wait until it has the token. It can then transmit its data.
Polling
Polling is an old method of media access that is still in use. Not many topologies support polling anymore, mainly because it has special hardware requirements. This method requires a central, intelligent device (meaning that the device contains either hardware or software intelligence to enable it to make decisions) that asks each workstation in turn if it has any data to transmit. If the workstation answers “yes,” the controller allows the workstation to transmit its data.
The polling process doesn’t scale very well—that is, you can’t take this method and simply apply it to any number of workstations. In addition, the high cost of the intelligent controllers and cards has made the polling method all but obsolete.
Wireless Networks
One of the most fascinating cabling technologies today—actually, it doesn’t really use cable— is wireless. Wireless networks offer the ability to extend a LAN without the use of traditional cabling methods. Wireless transmissions are made through the air by infrared light, laser light, narrow-band radio, microwave, or spread-spectrum radio.
Wireless LANs are becoming increasingly popular as businesses are becoming more mobile and less centralized. You can see them most often in environments where standard cabling methods are not possible or wanted.
Wireless networking requires much the same type of equipment as traditional networking; the main difference is that the special versions of each item rely on RF signals or infrared instead of cables. So, for example, each node needs a NIC that has a transceiver in it instead of a cable jack; and there needs to be a central wireless access point (WAP), the equivalent of a hub, with which the wireless NICs communicate.
The first wireless networking standard to become commercially popular was IEEE 802.11b, which could send and receive at up to 11Mbps. At this writing a newer standard, IEEE 802.11a, has extended that to 54Mbps and will reach over 100Mbps in the next two years.
BlueTooth is an infrared wireless standard that uses light rather than radio waves. It is limited to about 35 feet in range and requires a clear line of sight, so it has not become widespread in use except for communications between notebook PCs and PDAs.
Connectivity Devices
In addition to clients, servers, and the cables between them, certain other “boxes” are required to help manage and facilitate connections. The following sections discuss some of them.
Repeaters
Repeaters are simple devices. They allow a cabling system to extend beyond its maximum allowed length by amplifying the network voltages so they travel farther. Repeaters are nothing more than amplifiers and, as such, are very inexpensive.
The main disadvantage of repeaters is that they just amplify signals. These signals include not only the network signals, but any noise on the wire as well. Eventually, if you used enough repeaters, you could possibly drown out the signal with the amplified noise. For this reason, repeaters are used only as a temporary fix.
Hubs
Hubs are devices used to link several computers together. They are most often used in 10/100BaseT Ethernet networks. They are essentially just multiport repeaters. They repeat any signal that comes in on one port and copy it to the other ports (a process that is also called broadcasting).
There are two types of hubs: active and passive. Passive hubs connect all ports together electrically and are usually not powered. Active hubs use electronics to amplify and clean up the signal before it is broadcast to the other ports. The category of active hubs also includes a class called intelligent hubs, which are hubs that can be remotely managed on the network.
Bridges
Bridges join similar topologies and are used to divide network segments. Bridges keep traffic on one side from crossing to the other. For this reason, they are often used to increase performance on a high-traffic segment.
For example, with 200 people on one Ethernet segment, performance would be mediocre, because of the design of Ethernet and the number of workstations fighting to transmit. If you divided the segment into two segments of 100 workstations each, the traffic would be much lower on either side and performance would increase.
Bridges cannot distinguish one protocol from another. If a bridge is aware of the destination address, it is able to forward packets; otherwise, a bridge forwards the packets to all segments. Bridges are more intelligent than repeaters but are unable to move data across multiple networks simultaneously. Unlike repeaters, bridges can filter out noise.
The main disadvantage of bridges is that they can’t connect dissimilar network types or perform intelligent path selection. For that function, you need a router.
Routers
Routers are highly intelligent devices that connect multiple network types and determine the best path for sending data. They can route packets across multiple networks and use routing tables to store network addresses to determine the best destination.
The advantage of using a router over a bridge is that routers can determine the best path data can take to get to its destination. Like bridges, they can segment large networks and filter out noise. However, they are slower than bridges because they are more intelligent devices; as such, they analyze every packet, causing packet-forwarding delays. Because of this intelligence, they are also more expensive.
Routers are normally used to connect one LAN to another. Typically, when a WAN is set up, at least two routers are used.
Switches
Like hubs, switches are devices used to link several computers together. They differ from hubs in a few important ways. Switches repeat signals to the ports like hubs do, with one exception: Rather than send network traffic to all ports, switches have enough intelligence to send the traffic directly to the port the packet was intended for. All switches are active, and some are manageable. Manageable hubs allow remote management and in higher-end devices can also act similarly to a router. This feature can be used to logically divide the network into segments and reduce network traffic.
Brouters
Brouters are truly an ingenious idea because they combine the best of both worlds—bridges and routers. They are used to connect dissimilar network segments and also to route only one specific protocol. The other protocols are bridged instead of being dropped. Brouters are used when only one protocol needs to be routed or where a router is not cost-effective (as in a branch office).
Gateways
Gateways connect dissimilar network environments and architectures. Some gateways can use all levels of the OSI model, but they are frequently found in the Application layer. It is there that gateways convert data and repackage it to meet the requirements of the destination address. This makes gateways slower and more costly than other connectivity devices. An example of a gateway is the NT Gateway Service for NetWare, which, when running on a Windows NT Server, can connect a Microsoft Windows NT network with a Novell NetWare network.
Exam Essentials
Understand local area networks (LANs) and wide area networks (WANs).LANs are small in area, such as a single office. WANs encompass a large geographic area, possibly even among cities or countries.
Understand peer-to-peer and client/server.In a peer-to-peer network, the computers act as both workstations and servers, and there is no dedicated server with special server software. A client/server network contains at least one server, such as a file server, print server, DHCP server, and so on.
Know the role of TCP/IP in networking.TCP/IP is the protocol used for the Internet and most Ethernet networks these days. It assigns each PC a unique IP address.
Establishing Internet Connectivity
This is a brand-new objective on the A+ Core Hardware exam; previously the Internet was covered only on the OS Technologies exam. It is still covered there, but this new objective deals with the hardware side of Internet connectivity. A good PC technician should be able to select appropriate Internet connectivity methods for a given situation and install and configure that technology.
Critical Information
For each of the following technologies, you should be able to provide a definition, identify the speed range, identify advantages and disadvantages, and explain how the connection functions.
Dial-Up
Dial-up Internet uses a modem and dial-up networking (DUN) in Windows to establish a connection between a PC and an Internet Service Provider (ISP). A dial-up connection is not always on; it is established when needed and disconnected when not needed. It uses standard telephone lines and ties up the phone while it is operating.
Dial-up speed is limited to between 52Kbps and 56Kbps. Its primary disadvantages are its low speed and the inconvenience of tying up the phone line. Its advantage is price; it is the cheapest type of Internet connection.
To configure a modem dial-up connection, install the modem in the PC, make sure dial-up networking is installed in Windows, and then create a new DUN connection for the ISP’s phone number.
ISDN
Integrated Services Digital Network (ISDN) is a special digital type of phone line that is able to carry data faster than a regular dial-up. An ISDN phone line can carry two channels of data at once, at up to 64Kbps each, for a total of about 128Kbps maximum. It also has a separate voice channel, so you can place voice calls while connected to the Internet. It requires special phone lines from the phone company.
ISDN is a dial-up connection, so it uses dial-up networking. However, it establishes the connection much more quickly than a standard dial-up, usually within 5 seconds.
ISDN’s advantage over regular dial-up is its speed and the ability to use the phone for voice calls simultaneously with the Internet. Its disadvantage is that better, faster Internet options currently exist at lower prices than ISDN, such as ADSL and cable. It is not very popular anymore.
To configure ISDN access, install the ISDN terminal adapter in Windows as you would any new piece of hardware. Connect it to the ISDN telephone line, and then create a new DUN connection for the ISP’s phone number. Your ISP must specifically support ISDN for this to work, and you may need a special type of ISP account.
DSL
Digital Subscriber Line (DSL) is a technology that uses regular telephone lines to carry high-speed Internet. Like ISDN, it allows voice calls to take place while you’re connected to the Internet.
DSL is much faster than ISDN. Its top speed can reach 2Mbps or higher, although there are many different types of DSL and not all of them are that fast.
The two major types of DSL are Asynchronous (ADSL) and Synchronous (SDSL). ADSL is cheaper and more common. It provides faster download speeds than upload speeds. SDSL has the same speed in both directions.
The advantages of DSL are its convenience, its always-on nature (no dialing up), its ability to use standard telephone lines, and its attractive price in relation to its speed. The disadvantage is that it is not available in all areas, especially rural areas, because of the limitation in distance between the PC and the local telephone switching station.
To configure DSL access, connect the DSL terminal adapter to your phone line and then connect it to the PC. This may be a USB connection, or it may be an Ethernet networking connection. If it’s the latter, you need a 10BaseT or 100BaseT Ethernet card in the PC to connect it to. From that point, the PC will see the Internet connect as a LAN connection.
Cable
Cable Internet access is available in most areas that have digital cable TV. It has nothing to do with the phone lines, so it does not require telephone service. Its speed is roughly equivalent to ADSL (1Mbps or more in most cases), and its price is also comparable to ADSL. It is an always-on connection.
The advantages of cable are convenience, always-on access, attractive pricing for the speed provided, and independence from telephone lines. The disadvantage is that it is not available in all areas, and usually is not available to businesses.
Configuring cable is much like configuring DSL. Connect the terminal adapter to your cable TV connection. You may need to install a splitter (see your cable company for details). Then connect the terminal adapter to the PC, either via Ethernet network card or USB connection. The PC will see the Internet connection as a LAN connection.
| Note |
When you use a broadband Internet connection such as cable or DSL, your computer is participating in a LAN owned by the ISP. In a large company, there may be a full-time broadband connection to the Internet, such as a T1 line, that all the computers in the company share. If that is the case, Internet connectivity is provided through the LAN and no special setup is needed. |
Satellite
Satellite Internet service has the advantage of near-global availability, making it a good choice for users in areas not serviced by cable or DSL providers. Its speed ranges from 300Kbps to 1Mbps for downloads and around 128Kbps for uploads, so it is inferior to other broadband choices in speed. It is also more expensive than most cable and DSL plans.
There are two types: one-way and two-way. One-way satellite uses a satellite dish for downloading but a dial-up account with an ISP for uploading. Two-way satellite has no relationship to the telephone; it uses satellite in both directions.
The advantage of satellite is that is can be used virtually anywhere that has a clear view of the southern sky. It is also faster than dial-up. The disadvantage is that it is not as good a value in terms of bandwidth for the money as DSL or cable. The speed is also not as good.
Two-way satellite installation requires a professional installer. Professional installers are also recommended for one-way systems. Installation involves running coaxial cable from the satellite dish to an external terminal adapter, and then connecting the terminal adapter to the PC via USB and running setup software. Two-way satellite requires two separate terminal adapters—one for sending and one for receiving.
Wireless Connectivity
Wireless Internet uses the wireless telephone network to provide service. It is primarily for use with mobile computers and PDAs, but it can also be used for desktop PCs, especially in areas that offer no other broadband options. Its primary advantage is that it can be used anywhere the wireless phone network covers. The disadvantage is the price for the bandwidth you get.
Exam Essentials
Know the broadband options.Given a scenario, you should be able to make a recommendation as to the best broadband Internet option available in that situation.
Understand how cable, DSL, and satellite operate.Be familiar with the basics of each technology, including what equipment and connectivity are required, its approximate speed, and its availability issues.
Review Questions
|
1. |
What does STP cable have that UTP cable does not? |
|
|
2. |
Which category of cable is the minimum required for 100BaseT networking? |
|
|
3. |
What common household connector does an RJ-45 connector most resemble? |
|
|
4. |
Which type of cable would be used for a 10Base2 (Thinnet) Ethernet network? |
|
|
5. |
Which type of cable has either an ST or SC connector? |
|
|
6. |
In which type of network are all computers equal participants? |
|
|
7. |
Which physical topology connects all nodes to a hub? |
|
|
8. |
Which type of server dynamically assigns IP addresses to network nodes? |
|
|
9. |
Which type of network uses a multistation access unit (MAU)? |
|
|
10. |
Which type of Internet connectivity does not require a telephone? |
|
Answers
|
1. |
The S in STP stands for shielded, referring to shielding from electromagnetic interference (EMI). |
|
2. |
Cat5 cable can transmit data at up to 100Mbps, which is the maximum speed of 100BaseT. |
|
3. |
An RJ-45 connector is essentially a wider version of the RJ-11, the common household telephone connector. |
|
4. |
RG-58 is 50ohm cable designed for use with 10Base2 Ethernet. RG-59 is for television signals, RG-6 is for satellites, and RG-8 is for 10Base5 Ethernet. |
|
5. |
ST and SC are two types of fiber optic cable connectors. |
|
6. |
A peer-to-peer network does not have any computers set aside to be servers; all are equal. |
|
7. |
A star consists of several nodes that all connect to a central hub. |
|
8. |
A Dynamic Host Configuration Protocol (DHCP) server dynamically assigns IP addresses. |
|
9. |
Token Ring networks connect all nodes with an MAU in the center. It is a physical star, although it is a logical ring. |
|
10. |
Cable and two-way satellite do not require a telephone. |
Part I - A+: Core Hardware Service Technician Exam
- Domain 1 Installation, Configuration, and Upgrading
- Domain 2 Diagnosing and Troubleshooting
- Domain 3 Preventive Maintenance
- Domain 4 Motherboard/Processors/Memory
- Domain 5 Printers
- Domain 6 Basic Networking
Part II - A+ Operating System Technologies Exam