Before Installing New Hardware or Software
|
|
Before you add a new hardware component to a network, upgrade the operating system, install a new application, or make any other such change, you need a clear picture of the current condition of the network. Additionally, you need to have an understanding of how a network behaves when it is functioning normally so that you will be able to tell when the network is malfunctioning. This includes an understanding of standard operating procedures and how they are being implemented and an awareness of any environmental issues that affect the way the network is set up. You also need to take a close look at error messages and log files, which will give you a lot of information about the health of the network, and be sure you are familiar with the current configuration and baselines. In addition, don’t forget to review the manufacturers’ documentation that you should have at hand. A 15-minute perusal of the documentation beforehand could save you hours of work later.
Standard Operating Procedures
Standard operating procedures (SOPs) are part of company policy and typically cover everything from sick-day accrual to how the computer systems are used. In particular, network administrators need to be aware of company policies regarding the following:
-
Internet access
-
Printing
-
Storage allocation
-
E-mail usage
-
User administration
Policies about these issues will be reflected in the network’s naming conventions, protocol standards, and workstation configuration, and will affect the location of network devices.
Naming Conventions
Naming conventions specify how network entities are named, within the guidelines of the network operating system being used. Each entity name must be unique on the network, including the names you give to the following:
-
Servers
-
Printers
-
User accounts
-
Group accounts
-
Test and service accounts
Naming Servers
In general, you name servers according to their location or function; sometimes it makes sense to use a combination. For example, a server located in Seattle might be named SEATTLE, or a server in the sales department might be named SALES. Or you might name a server that stores data DATA1, a server that stores applications APPS1, a server that stores a database DB1, and so on.
Another common practice is to name file servers FS followed by a number, such as FS1, FS2, FS3, and so on. Unfortunately, this naming convention doesn’t provide the user with any information about what the server stores.
It is important for the Network+ exam, and for your life as a network technician, that you understand where the directory services that you use today come from. Novell Directory Service (NDS) and Active Directory (included with Windows 2000 Server) are modeled after a standard known as X.500. X.500 is a type of global phone book. The period (.) is the delimiter for NDS, Active Directory, and X.500 entries. Suppose, for example, a user’s name is Bob. Bob works in the accounts department of the finance division, at a company known as YourCo. His full address would be Bob.Accounts.Finance.YourCo.
In NDS and Active Directory, each name is known as an object . A graphical tree displays each object. Thus, it is efficient to begin at a higher level and administer policies to an entire network, for example, at YourCo. Furthermore, it is possible to drill down and work on a smaller unit level. Additional policy information can be applied to the Finance level.
Using periods as the delimiter, NDS and Active Directory look similar to DNS, or the Domain Name Service.
DNS is an Internet standard. This standard is like NDS in that it is based on X.500 and the period is used as a delimiter. But it’s time to put one misconception to rest here and now: Not all Internet addresses need www. Try http://research.Microsoft.com to prove this to yourself.
Another point needs to be made about DNS entries. All URLs don’t end with .com, .org, or .edu . Country codes are common final entries in a URL . Here are some of them:
-
TW (Taiwan)
-
TZ (Tanzania)
-
UA (Ukraine)
-
UG (Uganda)
-
UK (United Kingdom)
-
UM (U.S. Minor Outlying Islands)
-
US (United States of America)
-
UY (Uruguay)
-
UZ (Uzbekistan)
-
VA (Vatican City State)
As you use the Internet, NDS, and Active Directory, notice the commonalities between them. When you do, you will see how their common lineage ties them together.
The most common naming convention in use today is a combination of location and function. Using this approach, you might specify that the first four characters of the name identify the server’s location; the next two, the server’s function; and the last two, the server’s rank for that type of server. For example, the FRGOFS02 server is located in Fargo, it’s a file server, and it is the second server of that type in Fargo.
Naming Printers
As with server names, printer names are often derived from their function, location, or both. Naming a printer after its function or location makes the printer easier to locate for the users. If, for example, your dot-matrix printer is used to print multiple-part forms, you might name it Forms. If you have more than one forms printer, you might need to use two-word names, such as Forms-Ship or Forms-Finance. You might name high-quality printers Laser or Laser-Legal, indicating that this printer is always loaded with legalsize paper.
| Note | This is not intended to reflect a right or a wrong way to address naming conventions. There is only one right way for any organization—the method it follows. |
Naming User Accounts
Generally speaking, the simplest username is the user’s first name. This method works well in a company with only a few users and fits the informality often found in a small office. It is fairly insecure, however, because hackers could easily guess a username. It also won’t work in a larger organization that could easily include two people with the same first name.
The user-naming convention you use should allow for unique IDs and ensure that there are no duplicates. Larger firms typically use a first initial followed by part of or the entire last name. For example, Tim Catura-Houser would be TCaturaHouser. This is still a long username and might even cause a problem with maximum character lengths allowed in some operating systems. In this example, Tcat might be used as a short, yet unique, login name.
Naming Groups
Groups are network entities that logically associate users by function. They are designed to make network administration easier: You can assign rights to a group of users all at once, rather than to each individual. Because the group of users is organized by function, it would stand to reason that groups should be named by function. Additionally, the names should be short, fewer than 15 characters if possible. For example, if you have a group of users from the sales department that all use the same printer, you might name the group SALES_PRN. On the other hand, if you just want a general group for security and rights assignment purposes, you might name that group of users SALES.
| Note | We’ll discuss groups in detail in Chapter 8, “Network Access and Security.” |
Naming Test and Service Accounts
When you install new services on the network, such as printers, applications, and so on, it is always a good idea to test the functionality of these services first. It is not good practice to do this testing while logged in using an administrative account, because administrative accounts usually have allencompassing rights to the network. Thus, problems related to accessing the service are more likely to occur when an administrative account is not used for testing. It is better to use a user account that is equivalent to one who will be using the service. For this reason, it makes sense to create test accounts that you can use to test access to and the functionality of new services.
Service accounts , on the other hand, give outside network maintenance personnel the ability to perform administrator-level functions on your network. This is necessary whenever you must call in outside personnel.
The naming conventions document should also specify naming conventions for these accounts and define their security rights.
Protocol Standards
You have already learned that protocols have different properties. If your firm has nothing but NetWare servers that are either version 3.x or 4.x , using IPX (Internet Packet eXchange) as the standard protocol would make sense. Alternatively, suppose there is a small group called New Product Development. Because of the sensitive nature of this group’s work and because data should not leave the department, a routable protocol might be forbidden. In this case, NetBEUI (NetBIOS Extended User Interface) would be a wise choice, since it cannot be routed and serves a small group without much maintenance. Today, because of its prevalence and to reduce training and operational expenses, a great number of companies are standardizing on TCP/IP (Transmission Control Protocol/Internet Protocol).
Regardless of the protocol you choose, you must obtain all network addresses before installing or upgrading a network device. This brings its own set of considerations. As you saw in Chapter 4, “TCP/IP Utilities,” using TCP/IP as an example, each IP address must be unique, and just guessing at one is bound to create havoc. Clearly, you need a well-documented IP address and associated parameters, such as where the IP address comes from. Your SOPs should specify how network addresses are to be formatted and distributed.
Workstation Configuration
A standardized workstation configuration serves a company well for a couple of reasons:
-
You can narrow the scope of problems at a client station.
-
You can more easily troubleshoot if everyone uses the same operating system, network client, and productivity software.
This is not to say that everyone in the office has to have the exact same software. The engineering group would most likely need a CAD ( computeraided design) program, along with the appropriate horsepower and RAM. Giving everyone in the company a CAD program, however, would not only waste resources, it would be difficult for the accounting department to use a CAD program to create a paycheck for each employee. Therefore, a standard for workstation configuration is usually mandated by a group’s function. However, once an application is chosen, only that application (preferably the same version) should be used by anyone who requires access to that type of program. Which applications and which versions of each application can be used on the network should be documented in your SOPs.
| Tip | Some network management applications simplify the process of distributing unique applications to those users who need them, while maintaining the same basic workstation software configuration. Examples of these include Microsoft’s Systems Management Server (SMS) and Novell’s ZENworks. |
It is also important to define minimum workstation hardware standards. Typically, the minimum requirement is one or two generations behind what is considered the hottest, fastest new system. A standards document might specify the following:
-
Type, brand, and speed of CPU
-
Minimum RAM
-
Minimum hard-disk size
-
Type and brand of NIC
-
Minimum monitor size (14”, 15”, or 17”)
Network Device Placement
The network SOP may also specify where network devices are to be placed. Many of these specifications relate to safety—for example, where cables are to be run and where to place network devices so that they are immune to sources of extreme heat or cold. Also, critical network components (such as servers and routers) should be placed in a room away from “busy fingers.”
You should also consider the needs of users when you are deciding where to place network devices. For example, although placing a printer in the middle of the office might seem logical, it probably makes more sense to place it near the employees who use it the most.
Environmental Issues
Environmental conditions, as they relate to installing or upgrading a network and its components, are important. Just like human beings, computers require a proper environment in order to function correctly. If the environment is harsh, the device will not function at peak efficiency. Surprisingly, environmental conditions and their consequences may be the most overlooked topic in the entire industry of networking. Often problems that seem to appear out of nowhere and appear to make no sense are caused by environmental conditions. Let’s examine the frequently elusive challenges that we all face at one time or another, including:
-
Power problems
-
ESD problems
-
EMI problems
-
RFI problems
-
Climate problems
Power Problems
Alternating current (AC), which is “food” to PCs and other network devices, is normally 110 volts and changes polarity 60 times a second (or 60 Hertz). These values are referred to as line voltage. Any deviation from these values can create problems for a PC or other network device. Power problems fall into three categories:
-
Overage
-
Underage
-
Quality
Power Overage Problems
During a power overage, too much power is coming into the computer. Power overage can take two forms:
-
A power spike occurs when the power level rises above normal levels and then drops back to normal in less than one second.
-
A power surge occurs when the power level rises above normal levels and stays there for more than one or two seconds.
Typically, power surges last longer than a second or two, and they may last for several minutes. For this reason, surges are usually more damaging than spikes (although a very large spike can damage a computer’s power supply just as much as a surge). Figure 6.1 shows the difference between a spike and a surge.
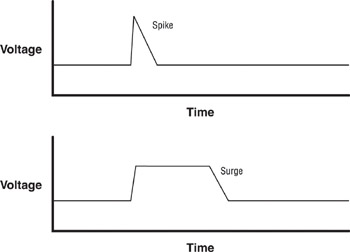
Figure 6.1: Comparing a power spike and a power surge
Two types of devices are used to protect computers and other network devices from power overage problems:
-
Surge protectors
-
Line conditioners
A surge protector contains a special electronic circuit that monitors the incoming voltage level and trips a circuit breaker when the overvoltage reaches a certain level (called the overvoltage threshold). The problem with surge protectors is that the threshold is set too high to be safe. By the time the circuit breaker trips, some overvoltage has gotten to the power supply of the computer, possibly damaging it. Nor does a surge protector protect against power surges and spikes that are lower than the threshold. For the most part, a surge protector is better than nothing, but not by much. It is really only a multiple-outlet strip and should not be considered anything more.
| Tip | Surge protectors with a very low overvoltage threshold cost upward of $50. They sacrifice themselves in the event of any significant overvoltage but are smart enough not to trip for just a small amount over the standard power levels. Additionally, most of these protectors contain electronic circuits that can “shave off” any overvoltage and ensure that the powered devices receive only the voltage they need. |
Line conditioners are a much better choice for protecting against surges and spikes. Line conditioners use several electronic methods to “clean” all power coming into the line conditioner. The best models can be prohibitively expensive, but there is a way to get a kind of “natural” line conditioner. An uninterruptible power supply (UPS) uses a battery and power inverter to run the computer equipment that plugs into it. A battery charger continuously charges the battery. The battery charger is the only thing that runs off line voltage. The computer itself runs off steady voltage supplied by the UPS. When power problems occur, the battery charger stops operating, and the equipment continues to run off the battery. The power coming from the UPS is always a continuous 110 volts, 60 Hertz. Because the AC power from the wall never crosses over the battery charger to run the computer components, it’s considered a “natural” line conditioner. As you will see, the UPS is the solution for a number of power problems.
Power Underage Problems
Power underages occur when power levels drop below the standard, and they are almost as common as power overages. There are three types of power underages:
-
A sag is an inverted spike. Sags occur when power levels drop below normal and rise back to normal within a brief period of time (usually less than one second). It is doubtful that you would be aware of sags (you might see a light flicker off and then on), although your computer might reboot.
-
A brownout, on the other hand, occurs when power drops below normal levels for several seconds or longer. In other words, a brownout is an inverted surge. The lights in the room will dim for a short period of time and then come back to full brightness.
-
A blackout is a total loss of power for several seconds, several minutes, or several hours.
Any one of these problems will cause your computers and other network devices to malfunction. Figure 6.2 contrasts these power problems.
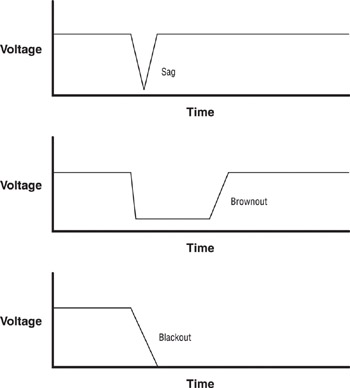
Figure 6.2: Comparing power underage problems
To ward off power underage problems, you need only one device: a UPS, which allows network devices to continue to function even in the complete absence of power. Some are intelligent and can shut down your computer in the case of a blackout.
Power Quality Problems
Power quality problems generally indicate that stray frequencies have entered the power supply through the power cord. Stray frequencies can cause strange problems (such as intermittent reboots or hangs) and can damage a device’s power supply. You can detect problems in power quality only with an oscilloscope. If you’re having power quality problems, you need either a UPS or a line conditioner.
Electrostatic Discharge (ESD) Problems
ESD occurs when two items with dissimilar static electrical charges are brought together. Nature doesn’t like things to be unequal, so static electrical charges will “jump” from the item with more electrons. This jump is seen as an electrical spark and thus is called an electrostatic discharge. ESD can damage electronic components because the several thousand electrons moving through delicate circuit junctions of silicon chips render the chips useless.
Static can be damaging to equipment and uncomfortable for users at the same time. For example, one worker had the habit of walking around the office without shoes. Walking across a nylon carpet in cotton socks created an immense static charge. When he got within 15 centimeters (not a typo) of the keyboard, the static charge jumped from his fingers to the keyboard. This not only caused him considerable pain, but it also burned out one of the horizontal scan rows on the keyboard, destroying it forever. Fortunately, the computer was properly grounded; otherwise, much more damage could have been done.
| Tip | Properly grounding equipment can prevent static, as can maintaining room humidity in the 40–60 percent range. |
Electromagnetic Interference (EMI) Problems
EMI occurs when magnetic fields intersect network or computer cables, causing interference in that cable. Motors and transformers, which are ubiquitous in an office (in air conditioners, heaters, and so on), are a typical source of EMI. A common mistake is to run network cable through an elevator shaft or through a ceiling that hides a bank of transformers in fluorescent lights.
Finding the source of EMI can be a challenge. The best approach is to follow a cable with an inexpensive compass, noting strong, odd needle movement. When you find the source of the EMI, you can protect the cable against it by either replacing the cable with a shielded cable (or fiber-optic cable, which is immune to both EMI and RFI) or by moving the cable far away from the source of the EMI.
Radio Frequency Interference (RFI) Problems
RFI occurs when radio signals interfere with the normal operation of electronic circuits (computers in particular). Everyday sources of RFI include television and radio transmitters, which by nature create a specific radio frequency as part of the transmission process. Other sources are two-way radios and cellular phones.
The only way to protect against both EMI and RFI is to use shielded network cables. Shielded cable, as used in shielded twisted-pair (STP) and coaxial cable, can reduce the effects of RFI. You could also use fiber-optic cable, which is immune to EMI and RFI, throughout your entire network, although this option can get a little pricey.
In one of the strangest cases of RFI I have ever seen, a server was resetting almost every night, right about 3 AM, while doing a tape backup. Changing the tape drive, the power supply, and other components were of no avail. The log files showed that the tape drive was operating normally and that the server would simply go down and restart, returning to normal operation.
Frustrated with dead-ends, an engineer was on-site at 3 AM to observe the failure. He noticed that a police patrol car was parked nearby, radioing in status reports. Separated only by a wall, the server didn’t have a chance with 25 watts of VHF radio signal being transmitted from only a few meters away. The radio signal was resetting the server, and once the policeman was done filing reports, the RFI was gone and the server restarted.
Climate Problems
Network devices (including computers and servers) are very sensitive to temperature extremes and can fail prematurely if subjected to them. The environment for network devices should be roughly the same as that for human beings. Keep the temperature consistently at 70 degrees Fahrenheit, and keep the relative humidity between 40 and 60 percent. Maintaining consistent temperature and humidity can be a challenge, because every computer constantly generates heat. Larger companies usually place network equipment in a special room that is climate controlled.
| Tip | Even if your company can’t provide a climate-controlled server room, you can do at least one thing to avoid climate problems: Never put servers in a network closet without ventilation. It is better to put servers out in the open, locked to a desk, than to lock them up in an unventilated closet. Also, never put an electronic device of any kind directly in front of a heat source, such as a space heater. This can cause the components to fail prematurely because excessive heat can damage electronic components. |
Error Messages and Log Files
A careful perusal of error messages and log files can give you a good sense of the health of a network. This is important because you may not want to add a new network device to a network that is experiencing problems. Log files record every action that occurs on a computer. For example, a log file can contain a record of who logged in to the network when, from which machine, and at what time. Figure 6.3 shows a sample log file.
Each network operating system includes special tools for creating and maintaining log files. In Windows NT, for example, you use Event Viewer (as shown in Figure 6.3) to display System Logs, Security Logs, and Application Logs. NetWare tracks events in the ABEND.LOG, SYS$LOG.ERR, and CONSOLE.LOG files. In Chapter 10, "Network Troubleshooting," we’ll look at log files and error messages in detail.
Figure 6.3: A sample log file from the Windows NT Event Viewer
Current Configuration and Baselines
Of particular value when you are upgrading a network or installing new hardware or software are the server and client configuration documents. If these have been properly maintained, they include information about the current hardware configuration (including I/O address, IRQ, DMA, and memory address), the installed software, any patches, and any special settings.
Configuration documentation should also include cable maps that indicate each network cable’s source (workstation/server) and destination ( typically, a port in a hub), as well as where each network cable runs. (We’ll discuss cabling in detail in Chapter 10.)
Baseline documentation indicates how the network normally runs. It includes network traffic statistics, server utilization trends, and processor performance statistics. Baselines indicate how things currently are, not how they should be. Creating and maintaining these types of documents provides a valuable reference point should a client or server fail or malfunction after an upgrade.
Other Documentation
You have at your disposal three more resources that can be of value before, during, and after upgrading or installing new hardware or software:
-
README files
-
The manufacturer’s technical support CD-ROM
-
The manufacturer’s technical support website
We discuss all of these in detail in Chapter 10.
| Note | All three of these resources can come in handy when you are unable to get through to technical support phone numbers. But some people feel that talking with a human is worth the effort it sometimes takes. Be aware that this is not necessarily free. See Chapter 10 for more information. |
|
|
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites
- Chapter XII Web Design and E-Commerce
- Chapter XIV Product Catalog and Shopping Cart Effective Design
- Chapter XVII Internet Markets and E-Loyalty
- Chapter XVIII Web Systems Design, Litigation, and Online Consumer Behavior