6.6 Becoming Familiar with Your PC
6.6 Becoming Familiar with Your PC To understand, detect, and prevent malicious mobile code, you must know what runs in the background on a Windows PC. You must understand what is normal for a PC, and the PCs under your control. You need to get a baseline understanding about what programs and services should be running in memory, what TCP/IP port numbers are used, and what programs and services should be automatically starting. If you take the time to understand these concepts and become familiar with what should be running on a PC before its attacked , you can detect the culprit sooner. In security circles, this process is known as intrusion detection. There are lots of security programs you can buy that automate these tasks (and we'll talk about them in Chapter 14), but learning to do manual intrusion detection will benefit you even more. 6.6.1 Startup ProgramsWhen Windows starts, even if you do not start a single application, dozens of programs, processes, and services are started each time your PC boots up. The operating system boot code loader is the first program to load something into memory. Next , as your operating system loads, it loads software drivers and services to manage the hardware and other software on your machine. In NT, the dots on the blue bootup screen each represent a different (device) driver or process starting. After the operating system has booted , it checks several startup areas, such as the AUTOEXEC.BAT , CONFIG.SYS , WIN.INI , SYSTEM.INI , DOSSTART.BAT , WINSTART.BAT , the registry, and Startup folders, for programs that have been requested to automatically start. Taken together, you can easily have 50 different software processes active in memory before you've launched your first application. We will discuss this in more detail later on. 6.6.2 IP PortsTo understand, detect, and prevent Trojans you must understand the concept of TCP/IP ports. The Transmission Control Protocol/Internet Protocol (TCP/IP) suite of network protocols underlies all data sent across the Internet. A protocol is a predefined set of rules used to exchange data between all involved parties. Using TCP/IP, data from one machine is split up into smaller individual data packets and sent to other computers. Every machine on the Internet must have a TCP/IP address (e.g., 192.168.123.204) to identify itself during communications. Every type of service (email, WWW, FTP, etc.) running on each computer that communicates across the Internet has a software-based port number as well. Port numbers can range from 0 to 65,535. The Internet Assigned Number Authority (IANA) (http://www.iana.org) has set aside the first 1,024 numbers and assigned most of them to a particular type of service. Thus port 25 is reserved for SMTP, port 21 is assigned to FTP, and Telnet is assigned to port 23. Table 6-1 shows some popular, legitimate , TCP/IP port numbers. Table 6-1. Some Popular TCP/IP port numbers
Ports higher than 1,024 can be used by any software that wishes to use it, although some port numbers have been officially recognized as belonging to a particular service. For example, IRC servers use port numbers between 6660 and 6669. Usually two different services cannot run at the same time and use the same TCP or UDP port number without causing problems. For that reason, regular programmers and Trojan writers usually try to use previously unassigned ports. When two computers communicate across the Internet, they must send packets back and forth using each other's IP address and request a particular port number(s) to communicate on. For example, when a PC with a Telnet program attempts to contact a Telnet server, it must request to communicate using port 23 in order for the request to even begin to be successful. The PC with the Telnet client can be contacted back by the Telnet server over the port it was originally sent from (see Figure 6-1). In order for any computer to communicate with a web server, it must usually send its data packets to port 80 of the web server, or else it will be rejected. If you are using a SMTP mail client, like Outlook, the client sends email to port 25 of the mail server. 6.6.3 TCP and UDPCommunication between two TCP/IP services is usually done using either TCP or User Datagram Protocol (UDP) packets. The TCP protocol is a connection-oriented protocol and provides reliable end-to-end communication. It can break up large amounts of data into smaller packets, send them across the Internet, reassemble them, and ensure that they arrive at their expected destination in the correct order. UDP, on the other hand, is connectionless. It tries its best, but does not guarantee that any data packets will arrive at their destination. UDP is popular because it has less overhead, and thus, is quicker. Even though UDP is not guaranteed , most UDP packets end up going where they are expected. All TCP and UDP packets must have a source and destination port number. Figure 6-1. TCP/IP port number example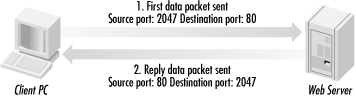
6.6.4 NetStat CommandIf you are serious about detecting and preventing Trojans, you must get familiar with port numbers, and especially with what port numbers should be running on a particular machine. You can use the NETSTAT -A command to list what ports are currently active on any Windows machine. Like many of Windows TCP/IP command-line utilities, NETSTAT is a carryover from the Unix world, and is used on many platforms. NETSTAT -A will show you the protocol being used (TCP or UDP), the local port number, the destination IP address (foreign address), the destination port number, and its current activity state. NETSTAT -AN gives more detail and will display port numbers instead of common names for protocols and machines. Example 6-1 shows the results of a NETSTAT -A command taken from my home machine, which is connected to the Internet via a cable modem. Example 6-1. Netstat example outputProto Local Address Foreign Address State TCP roger:5679 ROGER:0 LISTENING TCP roger:137 ROGER:0 LISTENING TCP roger:138 ROGER:0 LISTENING TCP roger:nbsession ROGER:0 LISTENING UDP roger:nbname *:* UDP roger:nbdatagram *:* In the example you can see there are port numbers active even when my browser or email clients are not started. My word processor is the only application I have open. But using NetStat, I can see that there are other processes running in the background waiting for something to occur (listening). In this particular case, roger is my desktop's identification name . I know that port 5679 is waiting for my Windows CE handheld computer to link up. The next two ports, 137 and 138, and the last three services are related to NETBIOS (port 139 is common, too.) and are normal for any networked Windows machine. While my firewall prevents ports 137, 138, and 139 from being broadcast onto the Internet, most Internet-connected Windows machines are vulnerable to hacker probes from these ports. Hackers can easily learn your PC's name, drive volumes , logged-in users, printers, and drive shares. In Example 6-2, I started Outlook. It has established connections to pick up my email from the two email servers I use. Example 6-2. Netstat -Output while Outlook is runningProto Local Address Foreign Address State TCP roger:5679 ROGER:0 LISTENING TCP roger:3381 gateway.visinet.com:pop3 TIME_WAIT TCP roger:3382 lh1.rdc1.va.home.com:pop3 TIME_WAIT TCP roger:137 ROGER:0 LISTENING TCP roger:138 ROGER:0 LISTENING TCP roger:nbsession ROGER:0 LISTENING UDP roger:nbname *:* UDP roger:nbdatagram *:* In Example 6-3, I plugged in my handheld computer. It was automatically configured with a valid IP address, without any prompting on my part, and Windows is using all the associated new ports to send information back and forth. Example 6-3. Netstat -Output with Windows CE handheld device linked to my PCProto Local Address Foreign Address State TCP roger:5678 ROGER:0 LISTENING TCP roger:5679 ROGER:0 LISTENING TCP roger:999 ROGER:0 LISTENING TCP roger:3831 ROGER:0 LISTENING TCP roger:5678 192.168.55.2:1113 ESTABLISHED TCP roger:5678 192.168.55.2:1114 ESTABLISHED TCP roger:5679 192.168.55.2:1112 ESTABLISHED TCP roger:137 ROGER:0 LISTENING TCP roger:138 ROGER:0 LISTENING TCP roger:nbsession ROGER:0 LISTENING TCP roger:3831 192.168.55.2:990 ESTABLISHED TCP roger:137 ROGER:0 LISTENING TCP roger:138 ROGER:0 LISTENING TCP roger:nbsession ROGER:0 LISTENING UDP roger:nbname *:* UDP roger:nbdatagram *:* UDP roger:nbname *:* UDP roger:nbdatagram *:* In Example 6-4, I started Internet Explorer and connected to www.microsoft.com. Lots of new source ports have been opened (they increment each time a page is requested), each with the destination port of 80. Example 6-4. Netstat -Output while using Internet ExplorerProto Local Address Foreign Address State TCP roger:5679 ROGER:0 LISTENING TCP roger:3437 ROGER:0 LISTENING TCP roger:3438 ROGER:0 LISTENING TCP roger:3440 ROGER:0 LISTENING TCP roger:3441 ROGER:0 LISTENING TCP roger:3442 ROGER:0 LISTENING TCP roger:3443 ROGER:0 LISTENING TCP roger:3405 ROGER:0 LISTENING TCP roger:3398 lh1.rdc1.va.home.com:pop3 TIME_WAIT TCP roger:3437 207.46.131.30:80 ESTABLISHED TCP roger:3438 207.46.131.30:80 ESTABLISHED TCP roger:3440 207.46.130.26:80 ESTABLISHED TCP roger:3441 207.46.130.26:80 ESTABLISHED TCP roger:3442 207.46.131.30:80 ESTABLISHED TCP roger:3443 207.46.131.30:80 ESTABLISHED TCP roger:137 ROGER:0 LISTENING TCP roger:138 ROGER:0 LISTENING TCP roger:nbsession ROGER:0 LISTENING UDP roger:3405 *:* UDP roger:nbname *:* UDP roger:nbdatagram *:* While it's not important to understand each and every port, and what it does, you should be familiar with common destination port numbers, and what they do. If I suspect a remote access Trojan on a particular PC, I will close all applications to end their connections to the Internet. Then I will run NETSTAT and look for connection activity where there should not be any. For example, when exploring a client's machine recently after he complained of sudden slowness, I found his PC was connecting to an unknown destination with port 21 (FTP) active. Since I knew we were not actively downloading files at the time, I immediately suspected a Trojan. I rummaged around and found a back door Trojan loading from his WIN.INI file. It had complete access to his machine for months and was in the middle of downloading some of his files. Later I'll provide a list of Trojans and their default port numbers. That way, when you find a machine opening port number 31337, you'll be alerted to a possible Back Orifice Trojan. And from NetStat, you'll learn the hacker's IP address and client port number. You can then report the hacker to his ISP or send an email message directly to the hacker. Recently, I was reviewing a customer's Windows NT server and noticed that it was running port 6666, an IRC server port number. Since I knew he wasn't intentionally trying to connect his server to an IRC network, I was able to confirm that his server was compromised and advertising its status to hackers worldwide. |
| | |
| Team-Fly |
| Top |
EAN: 2147483647
Pages: 176
- A Detailed Examination of MPLS Layer 3 VPNs
- Supporting IPv6 Traffic Transport in MPLS Layer 3 VPNs Using 6VPE
- Designing and Deploying IPsec Remote Access and Teleworker VPNs
- Understanding IKE in an IPsec Remote Access VPN Environment
- Strengthening SSL Remote Access VPNs Security by Implementing Cisco Secure Desktop
