The Ethernet Header Offsets
Knowing the offsets of key fields is crucial in building really hot filters. Figure 6 shows an Ethernet header (Ethernet II frame type) with its offsets and data values. The offsets are listed in two formats - hexadecimal (indicated by a leading 0x) and decimal (indicated by a following 'd').
As mentioned earlier, to filter on all ARP packets, you'd need to build a filter that looks for the value 0x0806 in the Ethernet Type field exactly 12 bytes into the packet (offset 12d or 0xC.) In these packet diagrams, I have listed the offsets in both decimal and hexadecimal because analyzer manufacturers have not standardized on this offset representation format. You'll find that Sniffer wants offset values in hexadecimal - EtherPeek wants them in decimal format. Damn!
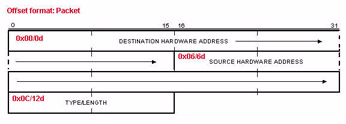
Figure 6: The Ethernet II frame format with field offsets in decimal (d) and hexadecimal (0x).
Let's say you wanted to filter on all packets sent to the broadcast address of 0xFF-FF-FF-FF-FF-FF. You would build a filter that looks for:
| Packet Offset | Value (in hexadecimal) |
|---|---|
| 0x00/0d (Destination Address field) | 0xFF-FF-FF-FF-FF-FF |
How about building a filter for all IPX traffic? Do you know the offset and value that you'd filter on?
| Packet | Offset Value (in hexadecimal) |
|---|---|
| 0xC/12d (EtherType field) | 0x8137 |
What about all traffic from Fred's machine (0x00-10-5A-23-12- A4)? If you are on the same network as Fred (not separated by a router), you could filter on Fred's hardware address right in the Ethernet header.
| Packet Offset | Value (in hexadecimal) |
|---|---|
| 0x06/6d (Source Address field) | 0x00-10-5A-23-12-A4 |
This filter would not catch any traffic sent to Fred, however, because you are only looking at offset 0x06/6d, the Source Address field. If you want to catch traffic to OR from Fred, you'd need to build a filter like this:
| Packet Offset | Value (in hexadecimal) |
|---|---|
| 0x00/0d (Destination Address field) | 0x00-10-5A-23-12-A4 |
OR
| 0x06/6d (Source Address field) | 0x00-10-5A-23-12-A4 |
EAN: 2147483647
Pages: 65