Physical (Environmental) Security
Overview
The Physical (Environmental) Security domain examines how elements of the surrounding physical environment and supporting infrastructure affect the confidentiality, integrity, and availability (C.I.A.) of information systems. We are not talking about logical controls here, but you will notice that some of the physical controls we describe are duplicated in some of the other domains, such as biometrics in the Operations and Access Control domain (Chapter 6). Natural disasters are an example of physical threats to security. Perimeter and facility access controls to prevent unauthorized entry or theft are elements of physical security. The area known as Industrial Security contains many of these concepts, such as closed-circuit television (CCTV), guards, fencing, lighting, and so forth.
To most engineers or security professionals, this domain is probably the least “sexy” of the 10 domains. Who cares how high perimeter fencing should be to protect critical buildings? But you need to know this stuff because (1) some of this information will be on the test, and (2) the best-configured firewall in the world will not stand up to a well-aimed brick.
A security practitioner needs to be aware of the elements that threaten the physical security of an enterprise and how controls can mitigate the risk incurred from those elements. In this chapter, we will examine threats to physical security and controls for physical security. Physical security addresses the physical protection of the resources of an organization, which include people, data, facilities, equipment, and information systems.
This domain addresses the threats, vulnerabilities, and countermeasures that can be utilized to physically protect an enterprise’s resources and sensitive information. These resources include personnel, the facility in which they work, and the data, equipment, support systems, and media with which they work. The term physical security often refers to the measures taken to protect systems, buildings, and the related supporting infrastructure against threats that are associated with the physical environment.
Physical computer security can also be defined as the process used to control personnel, the physical plant, equipment, and data involved in information processing. A CISSP candidate will be expected to understand the threats and controls that are related to physically protecting the enterprise’s sensitive information assets.
A CISSP professional should fully understand:
- The elements involved in choosing a secure site and its design and configuration
- The methods for securing a facility against unauthorized access
- The methods for securing the equipment against theft of either the equipment or its contained information
- The environmental and safety measures needed to protect personnel, the facility, and its resources
Threats to Physical Security
Before we can begin an investigation into the various ways an enterprise should implement proper physical security, we obviously need to know what aspects of our environment constitute a threat to the computing infrastructure. When a risk analysis or business impact assessment is performed, a list of all possible threats must be compiled. It does not matter whether the likelihood of any specific vulnerability is low or nonexistent (a tsunami in Ohio, for example); all possible threats must be compiled and examined. Many risk assessment methods and certification and accreditation processes have the practitioner compile these complete lists before making a determination as to their likelihood. The triad of confidentiality, integrity, and availability is at risk in the physical environment and must be protected.
Examples of risks to C.I.A. include:
- Interruptions in providing computer services (Availability)
- Physical damage (Availability)
- Unauthorized disclosure of information (Confidentiality)
- Loss of control over system (Integrity)
- Physical theft (Confidentiality, Integrity, and Availability)
Examples of threats to physical security are:
- Emergencies
- Fire and smoke contaminants
- Building collapse or explosion
- Utility loss (electrical power, air conditioning, heating)
- Water damage (pipe breakage)
- Toxic materials release
- Natural disasters
- Earth movement (such as earthquakes and mudslides)
- Storm damage (such as snow, ice, and floods)
- Human intervention
- Sabotage
- Vandalism
- War
- Strikes
Donn B. Parker has compiled a very comprehensive list that he calls “the seven major sources of physical loss” with examples provided for each:[*]
- Temperature. Extreme variations of heat or cold, such as sunlight, fire, freezing, and heat.
- Gases. War gases, industrial vapors, humidity, dry air, and suspended particles are included. Examples of these would be Sarin nerve gas; polychlorinated biphenyls (PCBs) from exploding transformers, smog, cleaning fluid, and fuel vapors; air conditioning failures; and smoke and paper dust.
- Liquids. Water and chemicals are included. Examples of these are floods, plumbing failures, precipitation, spilled drinks, fuel leaks, acid and base chemicals used for cleaning, and computer printer fluids.
- Organisms. Viruses, bacteria, people, animals, and insects are included. Examples of these are sickness of key workers, molds, contamination from skin oils and hair, contamination and electrical shorting from defecation and release of body fluids, consumption of cable insulation or information media such as paper, and shorting of microcircuits from cobwebs.
- Projectiles. Tangible objects in motion and powered objects are included. Examples of these are meteorites, falling objects, cars and trucks, airplanes, bullets and rockets, explosions, and wind.
- Movement. Collapse, shearing, shaking, vibration, liquefaction, flows, waves, separation, and slides are included. Examples of these are dropping or shaking of fragile equipment, earthquakes, mudslides, lava flows, sea waves, and adhesive failures.
- Energy anomalies. Types of energy anomalies are electric surges or failure, magnetism, static electricity, aging circuitry, nuclear radiation, sound, and light, radio, microwave, and other electromagnetic waves. Examples of these include electric utility failures, proximity of magnets and electromagnets, carpet static, decomposition of circuit materials, decomposition of paper and magnetic disks, electromagnetic pulse (EMP) from nuclear explosions, lasers, loudspeakers, high-energy radio frequency (HERF) guns, radar systems, cosmic radiation, and explosions.
[*]Fighting Computer Crime, D. B. Parker (Wiley, 1998).
Controls for Physical Security
In general, physical security controls should match up with the identified potential threats. In this chapter we have grouped the controls into two areas: Administrative Controls and Physical and Technical Controls.
Administrative Controls
Administrative controls, as opposed to physical or technical controls, can be thought of as the area of physical security protection that benefits from the proper administrative steps. These steps encompass proper emergency procedures, personnel control (in the area of Human Resources), planning, and policy implementation.
We will look at the following various elements of Administrative Controls:
- Facility Requirements Planning
- Secure Facility Management
- Administrative Personnel Controls
Facility Requirements Planning
Facility Requirements Planning describes the need for planning for physical security controls in the early stages of the construction of a data facility. There may be an occasion when security professionals are able to provide input at the construction phase of a building or data center. Some of the physical security elements involved at the construction stage include choosing and designing a secure site.
Choosing a Secure Site
The environmental placement of the facility is also a concern during initial planning. Security professionals need to consider such questions as:
- Visibility. What kind of neighbors will the proposed site have? Will the site have any external markings that will identify it as a sensitive processing area? Low visibility is the rule here.
- Local considerations. Is the proposed site near possible hazards (for example, a waste dump)? What is the local rate of crime (such as forced entry and burglary)?
- Natural disasters. Is it likely this location will have more natural disasters than other locations? Natural disasters can include weather-related problems (wind, snow, flooding, and so forth) and the existence of an earthquake fault.
- Transportation. Does the site have a problem due to excessive air, highway, or road traffic?
- Joint tenancy. Are access to environmental and HVAC controls complicated by a shared responsibility? A data center may not have full access to the systems when an emergency occurs.
- External services. Do you know the relative proximity of the local emergency services, such as police, fire, and hospitals or medical facilities?
Designing a Secure Site
Information Security processing areas are the main focus of physical control. Examples of areas that require attention during the construction planning stage are:
- Walls. Entire walls, from the floor to the ceiling, must have an acceptable fire rating. Closets or rooms that store media must have a high fire rating.
- Ceilings. Issues of concern regarding ceilings are the weight-bearing rating and the fire rating.
- Floors. The following are the concerns about flooring:
- Slab - If the floor is a concrete slab, the concerns are the physical weight it can bear (known as loading, which is commonly 150 pounds per square foot) and its fire rating.
- Raised - The fire rating, its electrical conductivity (grounding against static buildup), and that it employs a nonconducting surface material are concerns of raised flooring in the data center. Electrical cables must be enclosed in metal conduit, and data cables must be enclosed in raceways, with all abandoned cable removed. Openings in the raised floor must be smooth and nonabrasive, and they should be protected to minimize the entrance of debris or other combustibles.
- Windows. Windows are normally not acceptable in the data center. If they do exist, however, they must be translucent and shatterproof.
- Doors. Doors in the data center must resist forcible entry and have a fire rating equal to the walls. Emergency exits must be clearly marked and monitored or alarmed. To enable safe evacuation, electric door locks on emergency exits should revert to a disabled state if power outages occur. While this may be considered a security issue, personnel safety always takes precedence, and these doors should be manned in an emergency.
- Sprinkler system and fire resistance. The location and type of fire suppression system must be known. The fire-resistant rating of construction materials is a major factor in determining the fire safety of a computer operations room. The term fire-resistant refers to materials or construction that has a fire resistance rating of not less than the specified standard. For example, the computer room must be separated from other occupancy areas by construction with a fire-resistant rating of not less than one hour.
- Liquid or gas lines. Security professionals should know where the shut-off valves are to water, steam, or gas pipes entering the building. Also, water drains should be “positive” - that is, they should flow outward, away from the building, so that they do not carry contaminants into the facility.
- Air conditioning. AC units should have dedicated power circuits. Security professionals should know where the Emergency Power Off (EPO) switch is. As with water drains, the AC system should provide outward, positive air pressure and have protected intake vents to prevent air-carried toxins from entering the facility.
- Electrical requirements. The facility should have established backup and alternate power sources. Dedicated feeders and circuits are required in the data center. Security professionals should check for access controls to the electrical distribution panels and circuit breakers.
Secure Facility Management
Here we list audit trails and emergency procedures. These are elements of the Administrative Security Controls that are not related to the initial planning of the secure site but are implemented on an ongoing basis.
Audit Trails
An audit trail is a record of events. A computer system may have several audit trails, each focused on a particular type of activity, such as detecting security violations, performance problems, and design and programming flaws in applications. In the domain of Physical Security, access logs are vital audit trails because management needs to know where access attempts occurred and who attempted them.
The audit trails or access logs must record the following:
- The date and time of the access attempt
- Whether the attempt was successful or not
- Where the access was granted (which door, for example)
- Who attempted the access
- Who modified the access privileges at the supervisor level
Some audit trail systems can also send alarms or alerts to personnel whether multiple access failure attempts have been made.
Remember that audit trails are detective, rather than preventative. Access logs do not stop an intrusion, although knowing that an audit trail of the entry attempt is being compiled may influence the intruder to not attempt entry. Audit trails do help an administrator reconstruct the details of an intrusion post-event, however.
Emergency Procedures
The implementation of emergency procedures and the employee training and knowledge of these procedures is an important part of administrative physical controls. These procedures should be clearly documented, readily accessible (including copies stored off-site in the event of a disaster), and updated periodically.
Elements of emergency procedure administration should include the following:
- Emergency system shutdown procedures
- Evacuation procedures
- Employee training, awareness programs, and periodic drills
- Periodic equipment and systems tests
Administrative Personnel Controls
Administrative Personnel Controls encompass those administrative processes that commonly are implemented by the Human Resources department during employee hiring and firing. Examples of personnel controls implemented by HR often include the following:
- Pre-employment screening:
- Employment, references, or educational history checks
- Background investigation or credit rating checks for sensitive positions
- Ongoing employee checks:
- Security clearances - generated only if the employee is to have access to classified documents
- Ongoing employee ratings or reviews by their supervisor
- Postemployment procedures:
- Exit interview
- Removal of network access and change of passwords
- Return of computer inventory or laptops
Environmental and Life Safety Controls
Environmental and Life Safety Controls are considered to be those elements of physical security controls that are required to sustain either the computer’s operating environment or the personnel’s operating environment. The following are the three main areas of environmental control:
- Electrical power
- Fire detection and suppression
- Heating, Ventilation, and Air Conditioning (HVAC)
Electrical Power
Electrical systems are the lifeblood of computer operations. The continued supply of clean, steady power is required to maintain the proper personnel environment as well as to sustain data operations. Many elements can threaten power systems, the most common being noise, brownouts, and humidity.
Noise
The term noise in power systems refers not to audible sound but to the presence of electrical fluctuation in the system that is unintentional and interferes with the transmission of clean power. There are several types of noise, the most common being electromagnetic interference (EMI) and radio frequency interference (RFI). EMI and RFI are terms used to describe disruption or noise generated by electromagnetic waves. RFI refers to noise generated from radio waves, and EMI is the general term for all electromagnetic interference, including radio waves. EMI and RFI are often generated naturally, for example from sunspots or the earth’s magnetic field. Man-made sources of EMI and RFI - such as cell phones, laptops, and other computers - pose the largest threat to electronic equipment.
EMI is noise that is caused by the generation of radiation from the charge differences among the three electrical wires - the hot, neutral, and ground wires.
Two common types of EMI generated by electrical systems are:
- Common-mode noise. Noise from the radiation generated by the charge difference between the hot and ground wires
- Traverse-mode noise. Noise from the radiation generated by the charge difference between the hot and neutral wires
RFI is generated by the components of an electrical system, such as radiating electrical cables, fluorescent lighting, and electric space heaters. RFI can be so serious that it not only interferes with computer operations but also can permanently damage sensitive components.
Guidelines to prevent EMI and RFI interference in the computer room should be adopted, such as limiting the use and placement of magnets or cell phones around sensitive equipment. The United States government created the TEMPEST (Transient ElectroMagnetic Pulse Emanations Standard) standard to prevent EMI eavesdropping by employing heavy metal shielding.
Several protective measures for noise exist. Some of the ones that need to be noted are:
- Power line conditioning
- Proper grounding of the system to the earth
- Cable shielding
- Limiting exposure to magnets, fluorescent lights, electric motors, and space heaters
Table 10-1 lists various electrical power terms and descriptions.
|
ELEMENT |
DESCRIPTION |
|---|---|
|
Fault |
Momentary power loss |
|
Blackout |
Complete loss of power |
|
Sag |
Momentary low voltage |
|
Brownout |
Prolonged low voltage |
|
Spike |
Momentary high voltage |
|
Surge |
Prolonged high voltage |
|
Inrush |
Initial surge of power at the beginning |
|
Noise |
Steady interfering disturbance |
|
Transient |
Short duration of line noise disturbances |
|
Clean |
Nonfluctuating pure power |
|
Ground |
One wire in an electrical circuit must be grounded |
Brownouts
Unlike a sag, a brownout is a prolonged drop in supplied usable voltage that can do serious physical damage to delicate electronic components. The American National Standards Institute (ANSI) standards permit an 8 percent drop between the power source and the building’s meter and permit a 3.5 percent drop between the meter and the wall. In New York City, 15 percent fluctuations are common, and a prolonged brownout can lower the supplied voltage more than 10 percent.
In addition, surges and spikes occurring when the power comes back up from either a brownout or an outage can be damaging to the components. All computer equipment should be protected by surge suppressors, and critical equipment will need an uninterruptible power supply (UPS).
Humidity
The ideal operating humidity range is defined as 40 percent to 60 percent. High humidity, which is defined as greater than 60 percent, can produce a problem by causing condensation on computer parts. High humidity also creates problems with the corrosion of electrical connections. A process similar to electroplating occurs, causing silver atoms to migrate from the connectors onto the copper circuits, thus impeding the electrical efficiency of the components.
CHECK YOUR CARPETS
A major New York City legal client once brought one of the authors into an emergency situation. They were scheduled for a cutover to a major new computer system the next weekend and were having problems keeping their system online. They had been operating it successfully in parallel for a few weeks in the lab, but once the system was moved to the operations center, it would frequently abort and reset for no apparent reason. After examining every conceivable parameter of the configuration and scratching his head for a bit, the author noticed that he could cause a very small static discharge when he touched the case, thereby resetting the unit. Evidently the building contractor had run out of static-free carpet in the operations center and had finished the job with regular carpeting. Once the system was relocated, everything ran fine.
Low humidity of less than 40 percent increases the static electricity damage potential. A static charge of 4,000 volts is possible under normal humidity conditions on a hardwood or vinyl floor, whereas charges up to 20,000 volts or more are possible under conditions of very low humidity with non–static-free carpeting. Although you cannot control the weather, you certainly can control your relative humidity level in the computer room through your HVAC systems.
Some precautions you can take to reduce static electricity damage are:
- Use antistatic sprays where possible.
- Operations or computer centers should have antistatic flooring.
- Building and computer rooms should be grounded properly.
- Antistatic table or floor mats can be used.
- HVAC should maintain the proper level of relative humidity in computer rooms.
Fire Detection and Suppression
The successful detection and suppression of fire is an absolute necessity for the safe, continued operation of information systems. A CISSP candidate will need to know the classes, combustibles, detectors, and suppression methods of fire safety.
The National Fire Protection Association (NFPA) defines risk factors to consider when designing fire and safety protection for computing environments.[*] The factors to be used when assessing the impact of damage and interruption resulting from a fire, in priority order, are:
- The life safety aspects of the function, such as air traffic controls or safety processing controls
- The fire threat of the installation to the occupants or property of the computing area
- The economic loss incurred from the loss of computing function or loss of stored records
- The economic loss incurred from the loss of the value of the equipment
As in all evaluations of risk (not only fire risk), life safety is always the number one priority.
Fire Classes and Combustibles
Fire combustibles are rated as either Class A, B, C, or D based upon their material composition, thus determining which type of extinguishing system or agent is used. Table 10-2 lists the three main types of fires, what type of combustible gives the fire its class rating, and the recommended extinguishing agent.
|
CLASS |
DESCRIPTION |
SUPPRESSION MEDIUM |
|---|---|---|
|
A |
Common combustibles |
Water or soda acid |
|
B |
Liquid |
CO2, soda acid, or Halon |
|
C |
Electrical |
CO2 or Halon |
For rapid oxidation (a fire) to occur, three elements must be present: oxygen, heat, and fuel. Each suppression medium affects a different element and is therefore better suited for different types of fires.
- Water. Suppresses the temperature required to sustain the fire.
- Soda Acid. Suppresses the fuel supply of the fire.
- CO2. Suppresses the oxygen supply required to sustain the fire.
- Halon. A little different, it suppresses combustion through a chemical reaction that kills the fire.
Anyone who has made the mistake of throwing water on a grease fire in a skillet and suffered the resultant steam explosion will never need to be reminded that certain combustibles require very specific suppression methods.
The NFPA recommends that only the absolute minimum essential records, paper stock, inks, unused recording media, or other combustibles be housed in the computer room. Because of the threat of fire, these combustibles - including old, unused cabling - should not be stored in the computer room or under raised flooring. Underfloor abandoned cables can interfere with airflow and extinguishing systems. Cables that are not intended to be used should be removed from the room. It also recommends that tape libraries and record storage rooms be protected by an extinguishing system and separated from the computer room by wall construction fire-resistant rated for not less than one hour.
Table 10-3 shows the NFPA fire class ratings for various combustible materials.
|
FIRE CLASS |
COMBUSTIBLE MATERIALS |
|---|---|
|
A |
Wood, cloth, paper, rubber, most plastics, ordinary combustibles |
|
B |
Flammable liquids and gases, oils, greases, tars, oil-base paints and lacquers |
|
C |
Energized electrical equipment |
|
D |
Flammable chemicals such as magnesium and sodium |
Fire Detectors
Fire detectors respond to heat, flame, or smoke to detect thermal combustion or its by-products. Different types of detectors have various properties and use the different properties of a fire to raise an alarm.
- Heat-sensing. Heat-actuated sensing devices usually detect one of two conditions: (1) The temperature reaches a predetermined level, or (2) the temperature rises quickly regardless of the initial temperature. The first type, the fixed-temperature device, has a much lower rate of false positives (false alarms) than the second, the rate-of-rise detector.
- Flame-actuated. Flame-actuated sensing devices are fairly expensive, as they sense either the infrared energy of a flame or the pulsation of the flame and have a very fast response time. They are usually used in specialized applications for the protection of valuable equipment.
- Smoke-actuated. Smoke-actuated fire sensing devices are used primarily in ventilation systems where an early-warning device would be useful. Photoelectric devices are triggered by the variation in the light hitting the photoelectric cell as a result of the smoke condition. Another type of smoke detector, the radioactive smoke detection device, generates an alarm when the ionization current created by its radioactive material is disturbed by the smoke.
- Automatic dial-up fire alarm. This is a type of signal response mechanism that dials the local fire and/or police stations and plays a prerecorded message when a fire is detected. This alarm system is often used in conjunction with the previous fire detectors. These units are inexpensive but can easily be intentionally subverted.
Fire Extinguishing Systems
Most fire extinguishing systems come in two flavors: water sprinkler systems and gas discharge systems.
Water sprinkler systems come in four variations:
- Wet pipe. Wet pipe sprinkler systems always contain water and are also called a closed-head system. In the most common implementation, the fusible link in the nozzle melts in the event of a heat rise to 165° F, causing a gate valve to open and allowing water to flow. This is considered the most reliable sprinkler system; however, its main drawbacks are that nozzle or pipe failure can cause a water flood, and the pipe can freeze if exposed to cold weather.
- Dry pipe. In a dry pipe system, there is no water standing in the pipe; it is being held back by a clapper valve. Upon the previously described fire conditions arising, the valve opens, the air is blown out of the pipe, and the water flows. While this system is considered less efficient, it is commonly preferred over wet pipe systems for computer installations because a time delay may enable the computer systems to power down before the dry pipe system activates.
- Deluge. A deluge system is a type of dry pipe, but the volume of water discharged is much larger. Unlike a sprinkler head, a deluge system is designed to deliver a large amount of water to an area quickly. It is not considered appropriate for computer equipment, however, because of the time required to get back on-line after an incident.
- Preaction. This is currently the most recommended water system for a computer room. It combines both the dry and wet pipe systems by first releasing the water into the pipes when heat is detected (dry pipe) and then releasing the water flow when the link in the nozzle melts (wet pipe). This feature enables manual intervention before a full discharge of water on the equipment occurs.
Gas discharge systems employ a pressurized inert gas and are usually installed under the computer room raised floor. The fire detection system typically activates the gas discharge system to quickly smother the fire either under the floor in the cable areas or throughout the room. Typical agents of a gas discharge system are carbon dioxide (CO2) or Halon. Halon 1211 does not require the sophisticated pressurization system of Halon 1301 and is used in self-pressurized portable extinguishers. Of the various replacements for Halon, FM-200 is now the most common.
Suppression Mediums
- Carbon Dioxide (CO2). CO2 is a colorless and odorless gas commonly used in gas discharge fire suppression systems. It is very effective in fire suppression, because it quickly removes any oxygen that can be used to sustain the fire. This oxygen removal also makes it very dangerous for personnel, and it is potentially lethal. It is primarily recommended for use in unmanned computer facilities. If used in manned operations centers, the fire detection and alarm system must enable personnel ample time to either exit the facility or to cancel the release of the CO2.
- Portable fire extinguishers commonly contain CO2 or Soda Acid and should be:
- Commonly located at exits
- Clearly marked with their fire types
- Checked regularly by licensed personnel
- Halon. At one time, Halon was considered the perfect fire suppression method in computer operations centers because it is not harmful to the equipment, mixes thoroughly with the air, and spreads extremely fast. The benefits of using Halons are that they do not leave liquid or solid residues when discharged. Therefore, they are preferred for sensitive areas, such as computer rooms and data storage areas.
- Several issues arose with the deployment of Halon, however. For example, it cannot be breathed safely in concentrations greater than 10 percent, and when deployed on fires with temperatures greater than 900 degrees, it degrades into seriously toxic chemicals - hydrogen fluoride, hydrogen bromide, and bromine. Implementation of halogenated extinguishing agents in computer rooms must be extremely well designed to enable personnel to evacuate immediately when deployed, whether Halon is released under the flooring or overhead in the raised ceiling.
- At the Montreal Protocol of 1987, Halon was designated an ozone-depleting substance because of its use of chlorofluorocarbon compounds (CFCs). Halon has an extremely high ozone-depleting potential (three to ten times more than CFCs), and its intended use results in its release into the environment.
- Current federal regulations prohibit the production of Halons and the import and export of recovered Halons except by permit. There are federal controls on the uses, releases, and mandatory removal of Halon prior to decommissioning equipment, and reporting Halon releases, accidental or not, is mandatory.
- There are alternatives to Halon. Many large users of Halon are taking steps to remove Halon-containing equipment from all but the most critical areas. Most Halon 1211 in commercial and industrial applications is being replaced and recovered. Halon 1301 is being banked for future use.
- The two types of Halon used are:
- Halon 1211 - A liquid steaming agent that is used in portable extinguishers
- Halon 1301 - A gaseous agent that is used in fixed total flooding systems
- No new Halon 1301 installations are allowed, and existing installations are encouraged to replace Halon with a nontoxic substitute. Some common EPA-acceptable Halon replacements are:
- FM-200 (HFC-227ea)
- CEA-410 or CEA-308
- NAF-S-III (HCFC Blend A)
- FE-13 (HFC-23)
- Argon (IG 55) or Argonite (IG 01)
- Inergen (IG 541)
- Low-pressure water mists
- Either halocarbon agents or inert gas agents can be replacements for Halon 1301 and Halon 1211 in gas-discharge fire extinguishing systems. Halocarbon agents contain one or more organic compounds as primary components in chemical combination with one or more of the elements fluorine, chlorine, bromine, and iodine. Halocarbon agents are hydrofluorocarbons (HFCs), hydrochlorofluorocarbons (HCFCs), perfluorocarbons (PFCs or FCs), or fluoroiodocarbons (FICs).
- Inert gas agents contain as primary components one or more of the gases helium, neon, argon, and nitrogen. Some inert gas agents also contain carbon dioxide as a secondary component. Common inert gas agents for fire extinguishing systems are IG-01, IG-100, IG -55, and IG-541.
Because Halon was banned for use in fire suppression systems, many different chemical agents have been used. Some of these agents are called clean agents because they do not leave a residue on electronic parts after evaporation. CO2 (carbon dioxide) does leave a corrosive residue, and it is therefore not recommended for computer facility fire suppression systems. A clean agent is defined as an electrically nonconducting, nonvolatile fire extinguishant that does not leave a residue upon evaporation. IG-55 and IG-01 are inert gas agents that do not decompose measurably or leave corrosive decomposition products and are, therefore, considered clean agents.
Contamination
Environmental contamination resulting from the fire (or its suppression) can cause damage to the computer systems by depositing conductive particles on the components.
The following are some examples of fire contaminants:
- Smoke
- Water
- Suppression medium contamination (Halon or CO2)
Immediate smoke exposure to electronic equipment does little damage. However, the particulate residue left after the smoke has dissipated contains active by-products that corrode metal contact surfaces in the presence of moisture and oxygen. Removal of the contaminant from the electrical contacts, such as printed circuit boards and backplanes, should be implemented as soon as possible, because much of the damage is done during this corrosion period. Also, power should be immediately disconnected to the affected equipment, because continuing voltage can plate the contaminants into the circuitry permanently.
The order of steps to be taken after electronic equipment or media has been exposed to smoke contaminants are:
- Turn off power to equipment.
- Move equipment into an air-conditioned and humidity-controlled environment.
- Spray connectors, backplanes, and printed circuit boards with Freon or Freon-alcohol solvents.
- Spray corrosion-inhibiting aerosol to stabilize metal contact surfaces.
Water Damage
Water-based emergencies can include pipe breakage or damage to sensitive electronic equipment through the proper use of water fire sprinklers. The first order of business is shutting down the power to the affected equipment to prevent shock hazards, shorting, or further damage. Any visible standing water should be removed and allowed to drain from around and inside the unit. Because the room may still be extremely humid, move the equipment, if possible, to a humidity-controlled environment, and then wipe the parts and use water displacement sprays. If corrective action is initiated immediately, the damage done to the computer equipment can be greatly reduced and the chances of recovering the data are increased.
The proper order of steps to be taken after electronic equipment or media has been exposed to water are:
- Turn off all electrical power to the equipment.
- Open cabinet doors and remove panels and covers to allow water to run out.
- Place all affected equipment or media in an air-conditioned area, if portable.
- Wipe with alcohol or Freon-alcohol solutions or spray with water-displacement aerosol sprays.
Table 10-4 lists the temperatures required to damage various computer parts.
|
ITEM |
TEMPERATURE |
|---|---|
|
Computer hardware |
175º F |
|
Magnetic storage |
100º F |
|
Paper products |
350º F |
Heating, Ventilation, and Air Conditioning
HVAC is sometimes referred to as HVACR for the addition of refrigeration. HVAC systems can be quite complex in modern high-rise buildings, and they are the focal point for environmental controls. An IT manager needs to know who is responsible for HVAC, and clear escalation steps need to be defined well in advance of an environment-threatening incident. The same department is often responsible for fire, water, and other disaster response, all of which impact the availability of the computer systems.
Underfloor ventilation, as is true of all computer room ventilation, should not vent to any other office or area. HVAC air ducts serving other rooms should not pass through the computer room unless an automatic damping system is provided. A damper is activated by fire and smoke detectors and prevents the spread of computer room smoke or toxins through the building HVAC.
Physical and Technical Controls
Under this general grouping, we discuss those elements of physical security that are not considered specifically administrative solutions, although they obviously have administrative aspects. Here we have the areas of environmental controls, fire protection, electrical power, guards, and locks.
We will discuss the elements of control as they relate to the areas of:
- Facility perimeter control
- Access control devices
- Intrusion detection and alarms
- Computer inventory control
- Media storage requirements
Facility Perimeter Control
Several elements are required to maintain physical site security for perimeter control:
Guards
Guards are the oldest form of security surveillance. Guards still have a very important and primary function in the physical security process, particularly in perimeter control. Because of a human’s ability to adjust to rapidly changing conditions, to learn and alter recognizable patterns, and to respond to various conditions in the environment, a guard can make determinations that hardware or other automated security devices cannot make. Guards provide deterrent, response, and control capabilities, in addition to receptionist and escort functions. Guards are also the best resource during periods of personnel safety risks (they maintain order, crowd control, and evacuation) and are better at making value decisions at times of incidents. They are appropriate whenever immediate, discriminating judgment is required by the security entity.
Guards have several drawbacks, however, such as the following:
- Availability. They cannot exist in environments that do not support human intervention.
- Reliability. The pre-employment screening and bonding of guards is not foolproof.
- Training. Guards can be socially engineered or may not always have up-to-date lists of access authorization.
- Cost. Maintaining a guard function, either internally or through an external service, is expensive.
Dogs
Using guard dogs is almost as old a concept as using people to guard something. Dogs are loyal, are reliable (they rarely have substance abuse issues), and have a keen sense of smell and hearing. However, a guard dog is primarily acceptable for perimeter physical control and is not as useful as a human guard for making judgment calls. Some additional drawbacks include cost, maintenance, and insurance/liability issues.
Fencing
Fencing is the primary means of perimeter/boundary facility access control. The category of fencing includes fences, gates, turnstiles, and mantraps.
Fencing and other barriers provide crowd control and help deter casual trespassing by controlling access to entrances. Drawbacks to fencing include its cost, its appearance (it might be ugly), and its inability to stop a determined intruder. Table 10-5 is a very important table; a CISSP candidate should know these heights.
|
HEIGHT |
PROTECTION |
|---|---|
|
3′ to 4′ high |
Deters casual trespassers |
|
6′ to 7′ high |
Too hard to climb easily |
|
8′ high with 3 strands of barbed wire |
Deters most intruders |
Mantrap
A mantrap is a physical access control method in which the entrance to a facility or area is routed through a set of double doors. One door must be closed for the next door to open. It may or may not be monitored by a guard.
The term piggybacking describes an unauthorized person entering a facility through a carded or controlled door by following an authorized person who has opened the door. A mantrap is intended to control physical personnel entrance to the facility by piggybacking. Of course, the best protection from this type of intrusion is through security awareness training to prevent employees from holding the door open or allowing unauthorized intruders to enter.
PIDAS FENCING
Perimeter Intrusion Detection and Assessment System (PIDAS) fencing has intrusion detection sensors on the fence, and attempts to detect an intruder scaling the fence or cutting through it. By initiating an alarm when the cable vibrates, however, PIDAS’s sensitivity can cause a high rate of false alarms, because the alarm is often triggered by animals or weather elements such as high wind.
Lighting
Lighting is also one of the most common forms of perimeter or boundary protection. Extensive outside protective lighting of entrances or parking areas can discourage prowlers or casual intruders. Critical protected buildings should be illuminated up to 8 feet high with 2 feet candlepower. Common types of lighting include floodlights, streetlights, Fresnel lights, and searchlights.
Bollards
Bollards are small concrete pillars designed to deter vehicles being driven into and through an exterior wall of a buildings. Often doing double duty as exterior lighting, many government and military facilities have installed them post 9/11. Bollards come in a variety of types and sizes.
Locks
After the use of guards, locks are probably one of the oldest access control methods ever used. Locks can be divided into two types: preset and programmable.
- Preset locks. These are your typical door locks. The combinations to enter cannot be changed except by physically removing them and replacing the internal mechanisms. There are various types of preset locks, including key-in-knob, mortise, and rim locks. These all consist of variations of latches, cylinders, and deadbolts.
- Programmable locks. These locks can be either mechanically or electronically based. A mechanical programmable lock is often a typical dial combination lock, like the kind used on a gym locker. Another type of mechanical programmable lock is the common five-key pushbutton lock that requires the user to enter a combination of numbers. An electronic programmable lock requires the user to enter a pattern of digits on a numerical-style keypad, and it may display the digits in random order each time to prevent shoulder surfing for input patterns. It is also known as a cipher lock or keypad access control.
Closed-Circuit Television (CCTV)
Visual surveillance or recording devices such as closed-circuit television are used in conjunction with guards in order to enhance their surveillance ability and to record events for future analysis or prosecution. These devices can be either photographic in nature (as in still or movie film cameras) or electronic in nature (the closed-circuit TV camera). CCTV can be used to monitor live events occurring in an area remote to the guard, or they can be used in conjunction with a VCR for a cost-effective method of recording these events.
Access Control Devices
This access includes personnel access control to the facility and general operations centers, in addition to specific data center access control.
Security Access Cards
Security access cards are a common method of physical access control. There are two common card types: photo-image and digitally encoded cards. These two groups are also described as dumb and smart cards. Dumb cards require a guard to make a decision as to their validity, whereas smart cards make the entry decision electronically:
- Photo-image cards. Photo-image cards are simple identification cards with the photo of the bearer for identification. These are your standard photo ID cards, like a driver’s license or employee ID badge. These cards are referred to as dumb cards because they have no intelligence imbedded in them, so they require an active decision to be made by the entry personnel as to their authenticity.
- Digitally encoded cards. Digitally encoded cards contain chips or magnetically encoded strips (possibly in addition to a photo of the bearer). The card reader may be programmed to accept or deny an entry based upon an online access control computer that can also provide information about the date and time of entry. These cards may also be able to create multilevel access groupings. There are two common forms of digitally encoded cards, which are referred to as smart and smarter cards.
- Such smart entry cards can have either a magnetic stripe or a small integrated circuit (IC) chip imbedded in them. This card may require knowledge of a password or personal identification number (PIN) to enable entry. A bank ATM card is an example of this card type. These cards may contain a processor encoded with the host system’s authentication protocol, read-only-memory storage of programs and data, and even some kind of user interface.
- Wireless proximity readers. A proximity reader does not require the user to physically insert the access card. This card may also be referred to as a wireless security card. The card reader senses the card in possession of a user in the general area (proximity) and enables access. There are two general types of proximity readers - user-activated and system sensing:
- A user-activated proximity card transmits a sequence of keystrokes to a wireless keypad on the reader. The keypad on the reader contains either a fixed preset code or a programmable unique key pattern.
- A system-sensing proximity card recognizes the presence of the coded device in the reader’s general area. The following are the three common types of system-sensing cards, which are based upon the way the power is generated for these devices:
- Passive devices. These cards contain no battery or power on the card but sense the electromagnetic field transmitted by the reader and transmit at different frequencies using the power field of the reader.
- Field-powered devices. They contain active electronics, a radio frequency transmitter, and a power supply circuit on the card.
- Transponders. Both the card and the reader each contain a receiver, transmitter, active electronics, and a battery. The reader transmits an interrogating signal to the card, which in turn causes it to transmit an access code. These systems are often used as portable devices for dynamically assigning access control.
A smart card or access token can be part of a complete Enterprise Identity Management system, used to track the location of employees and manage secure access. A smart card can be coupled with an authentication token that generates a one-time or challenge-response password or PIN. While two-actor (or dual-factor) authentication is most often used for logical access to network services, it can be combined with an intelligent card reader to provide extremely strong facility access control.
Table 10-6 lists the various types of security access cards.
|
TYPE OF CARD |
DESCRIPTION |
|---|---|
|
Photo ID |
Facial photograph |
|
Optical-coded |
Laser-burned lattice of digital dots |
|
Electric circuit |
Printed IC on the card |
|
Magnetic stripe |
Stripe of magnetic material |
|
Magnetic strip |
Rows of copper strips |
|
Passive electronic |
Electrically tuned circuitry read by RF |
|
Active electronic |
Badge transmitting encoded electronics |
Over the last few years, especially after 9/11, the market has seen an explosion of offerings of various types and styles of smart facility access control cards. From wallet-sized, to key fobs, to vehicle stickers, smart cards are available in a huge variety of types and operating and many frequencies. The cards can be used for diverse applications such as public transportation, access control, paying tolls, park and rides, airline ticketing, customer loyalty cards, and ID cards. Figure 10-1 shows a common HID-style proximity card with an embedded chip.

Figure 10-1: HID proximity card with embedded chip. Photo courtesy of the HID Corporation.
Figure 10-2 shows a style of card reader for the HID-style cards.

Figure 10-2: HID-style proximity card reader. Photo courtesy of the HID Corporation.
Biometric Devices
Biometric access control devices and techniques, such as fingerprinting or retinal scanning, are discussed thoroughly in Chapter 2. Keep in mind that because they constitute a physical security control, biometric devices are also considered a physical access security control device.
Intrusion Detectors and Alarms
Intrusion detection refers to the process of identifying attempts to penetrate a system or building to gain unauthorized access. Chapter 3 details ID systems that detect logical breaches of the network infrastructure, but here we are talking about devices that detect physical breaches of perimeter security, such as a burglar alarm.
Perimeter Intrusion Detectors
The two most common types of physical perimeter detectors are based on either photoelectric sensors or dry contact switches.
- Photoelectric sensors. Photoelectric sensors receive a beam of light from a light-emitting device, creating a grid of either visible white light or invisible infrared light. An alarm is activated when the beams are broken. The beams can be physically avoided if seen; therefore, invisible infrared light is often used. Also, employing a substitute light system can defeat the sensor.
- Dry contact switches. Dry contact switches and tape are probably the most common types of perimeter detection. This can consist of metallic foil tape on windows or metal contact switches on door frames. This type of physical intrusion detection is the cheapest and easiest to maintain, and it is very commonly used for shop front protection.
Motion Detectors
In addition to the two types of intrusion detectors previously mentioned, motion detectors are used to sense unusual movement within a predefined interior security area. They can be grouped into three categories: wave pattern motion detectors, capacitance detectors, and audio amplification devices.
- Wave pattern. Wave pattern motion detectors generate a frequency wave pattern and send an alarm if the pattern is disturbed as it is reflected back to its receiver. These frequencies can either be in the low (sonic), ultrasonic, or microwave range. Table 10-7 shows the relative frequency of each of these detectors. Figure 10-3 shows a motion detector in the infrared spectrum, which detects changes in ambient temperature as well as wave disruption.
Table 10-7: Motion Detection System Frequencies
 Open table as spreadsheet
Open table as spreadsheetDETECTOR TYPE
FREQUENCY
Sonic
1500–2000 Hz
Ultrasonic
19,000–20,000 Hz
Microwave
400 MHz–10 GHz
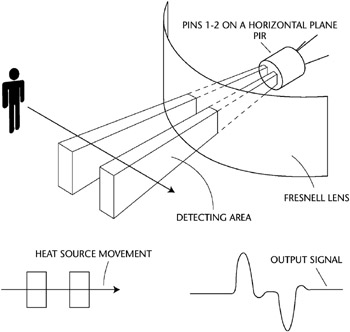
Figure 10-3: Infrared motion detector. - Capacitance. Capacitance detectors monitor an electrical field surrounding the object being monitored. They are used for spot protection within a few inches of the object rather than for overall room security monitoring, for which wave detectors are used. Penetration of this field changes the electrical capacitance of the field enough to generate an alarm.
- Audio detectors. Audio detectors are passive in that they do not generate any fields or patterns as the previous two methods do. Audio detectors simply monitor a room for any abnormal sound wave generation and trigger an alarm. This type of detection device generates a higher number of false alarms than the other two methods and should be used only in areas that have controlled ambient sound.
Alarm Systems
The detection devices previously listed monitor and report on a specific change in the environment. These detectors can be grouped together to create alarm systems. There are four general types of alarm systems:
- Local alarm systems. A local alarm system rings an audible alarm on the local premises that it protects. This alarm must be protected from tampering and must be audible for at least 400 feet. It also requires guards to respond locally to the intrusion.
- Central station systems. Private security firms operate these systems, which are monitored around the clock. The central stations are signaled by detectors over leased lines. These stations typically offer many additional features, such as CCTV monitoring and printed reports, and the customers’ premises are commonly less than 10 minutes travel time away from the central monitoring office.
- Proprietary systems. These systems are similar to the central station systems, except that the monitoring system is owned and operated by the customer. They are like local alarms, except that a sophisticated computer system provides many of the features in-house that a third-party firm would provide with a central station system.
- Auxiliary station systems. Any of the previous three systems may have auxiliary alarms that ring at the local fire or police stations. Most central station systems include this feature, which requires permission from the local authorities before implementation.
Two other terms related to alarms are:
- Line supervision. Line supervision is a process where an alarm-signaling transmission medium is monitored to detect any line tampering to subvert its effectiveness. The Underwriters Laboratories (UL) standard 611-1968 states, “the connecting line between the central station and the protection shall be supervised so as to automatically detect a compromise attempt by methods of resistance substitution, potential substitution, or any single compromise attempt.” Secure detection and alarm systems require line supervision.
- Power supplies. Alarm systems require separate circuitry and backup power with 24 hours minimum discharge time. These alarms help reduce the probability of an alarm system’s failure due to a power failure.
Computer Inventory Control
Computer Inventory Control is the control of computers and computer equipment from physical theft and protection from damage. The two main areas of concern are computer physical control and laptop control.
PC Physical Control
Due to the proliferation of distributed computing and the proliferation of laptops, inventory control at the microcomputer level is a major headache. Some groups estimate that 40 percent of computer inventory shrinkage is due to microcomputer parts “walking out the door.” Several physical controls must be taken to minimize this loss:
- Cable locks. A cable lock consists of a vinyl-covered steel cable anchoring the PC or peripherals to the desk. They often consist of screw kits, slot locks, and cable traps.
- Port controls. Port controls are devices that secure data ports (such as a floppy drive or a serial or parallel port) and prevent their use.
- Switch controls. A switch control is a cover for the on/off switch, which prevents a user from switching off the file server’s power.
- Peripheral switch controls. These types of controls are lockable switches that prevent a keyboard from being used.
- Electronic security boards. These boards are inserted into an expansion slot in the PC and force a user to enter a password when the unit is booted. This is also a standard part of the Basic Input Output System (BIOS) of many off-the-shelf PCs. They may also be called cryptographic locks.
Laptop Control
The proliferation of laptops and portables is the next evolution of distributed computing and constitutes a challenge to security practitioners. Now the computing resources can be strewn all over the globe, and physical inventory control is nearly impossible for an organization without a substantive dedication of IT resources. A laptop theft is a very serious issue because it creates a failure of all three elements of C.I.A.: confidentiality, because the data can now be read by someone outside of a monitored environment; availability, because the user has lost the unit’s computing ability; and integrity, because the data residing on the unit and any telecommunications from it are now suspect.
Media Storage Requirements
The ongoing storage of data media and the proper disposal of unneeded media and reports are serious concerns to security practitioners. Sometimes an organization will devote a large amount of resources to perimeter protection and network security and then will dispose of reports improperly. Or they will reuse laptops or diskettes without fully and appropriately wiping the data.
Because laptop theft is rampant, encryption of any sensitive data on a portable is also an absolute necessity. An associate of one of the authors was recently lent a laptop while working at a top brokerage firm, only to discover that the hard drive had not been reformatted and contained dozens of sensitive e-mails pertaining to the 1996 presidential election (the previous owner had worked as an advisor to the Republican campaign).
The following types of media commonly require storage, destruction, or reuse:
- Data backup tapes
- CDs
- Diskettes
- Hard drives
- Paper printouts and reports
The common storage areas for such media are:
- On-site. Areas within the facility, such as operations centers, offices, desks, storage closets, cabinets, safes, and so on.
- Off-site. Areas outside of the facility, such as data backup vault services, partners and vendors, and disposal systems. Transportation to or from an external data vault services vendor is a security concern, and it should be examined for problems relating to theft, copying, alteration, or destruction of data.
DISKETTE STORAGE TIPS
A few basic controls should be put in place to protect diskettes (or other magnetic media) from damage or loss, such as
- Keep the disks in locked cases.
- Don’t bend the diskettes.
- Maintain the proper temperature and humidity.
- Avoid external magnetic fields (such as TVs or radios).
- Don’t write directly on the jacket or sleeve.
THE JOY OF DUMPSTER DIVING
New York is the capital of ticker-tape parades. New Yorkers never seem to tire of trying to find some reason to throw large volumes of paper out of high-story office windows. Sometimes, however, the enthusiasm for the moment overrides the immediate availability of shredded reports, and some office workers will begin to toss out unshredded, full-page printed pages. Local reporters who have begun to collect these documents before they are swept up by sanitation have reported that the information contained is considerable (especially given that the parades are often down Broadway, past Wall Street). These pages often contain credit card account numbers, bank account numbers and balances, credit rating details, and so forth.
The following resources and elements are available to protect the media:
- Physical access control to the storage areas
- Environmental controls, such as fire and water protections
- Diskette inventory controls and monitoring
- Audits of media use
Data Destruction and Reuse
Data that is no longer needed or used must be destroyed. Information on magnetic media is typically destroyed by degaussing or overwriting. Formatting a disk once does not completely destroy all data, so the entire media must be overwritten or formatted seven times to conform to standards for object reuse.
Personnel with the proper level of security clearance should shred paper reports. Some shredders cut in straight lines or strips, whereas others crosscut or disintegrate the material into pulp. Care must be taken to limit access to the reports prior to disposal and to those stored for long periods. Reports should never be disposed of without shredding, such as by being placed in a dumpster intact. Burning is also sometimes used to destroy paper reports, especially in the Department of Defense and military.
Object Reuse and Data Remanence
Object reuse is the concept of reusing data storage media after its initial use. Data remanence is the problem of residual information remaining on the media after erasure, which may be subject to restoration by another user, thereby resulting in a loss of confidentiality. Diskettes, hard drives, tapes, and any magnetic or writable media are susceptible to data remanence. Retrieving the bits and pieces of data that have not been thoroughly removed from storage media is a common method of computer forensics, and law enforcement personnel often use it to preserve evidence and to construct a trail of misuse.
Any time a storage medium is reused (and also when it is discarded), there is the potential for the media’s information to be retrieved. Methods must be employed to properly destroy the existing data to ensure that no residual data is available to new users. The Orange Book standard recommends that magnetic media be formatted seven times before discard or reuse.
Terminology relative to the various stages of data erasure is:
- Clearing. This term refers to the overwriting of data media (primarily magnetic) intended to be reused in the same organization or monitored environment.
- Purging. This term refers to degaussing or overwriting media intended to be removed from a monitored environment, such as during resale (laptops) or donations to charity.
- Destruction. This term refers to completely destroying the media, and therefore the residual data. Paper reports, diskettes, and optical media (CD-ROMs) need to be physically destroyed before disposal.
The following are the common problems with magnetic media erasure that may cause data remanence:
- Erasing the data through an operating system does not remove the data; it just changes the File Allocation Table and renames the first character of the file. This is the most common way computer forensics investigators can restore files.
- Damaged sectors of the disk may not be overwritten by the format utility. Degaussing may need to be used. Formatting seven times is also recommended.
- Rewriting files on top of the old files may not overwrite all data areas on the disk because the new file may not be as long as the older file, and data may be retrieved past the file end control character.
- Degausser equipment failure or operator error may result in an inadequate erasure.
- There may be an inadequate number of formats. Magnetic media containing sensitive information should be formatted seven times or more.
WALK-THROUGH SECURITY LIST
The simplest way to get a handle on your office’s state of physical security is to do a minimal “walkabout.” This consists of an after-hours walk-through of your site, checking for these specific things:
- Sensitive company information is not lying open on desks or in traffic areas.
- Workstations are logged out and turned off.
- Offices are locked and secured.
- Stairwell exits are not propped open. (One of the authors has seen them propped open with fire extinguishers so that folks wouldn’t have to use the elevators!)
- Files, cabinets, and desks are locked and secured.
- Diskettes and data tapes are put away and secured.
[*]Source: NFPA 75 “Standard for the Protection of Electronic Computer/Data Processing Equipment,” National Fire Protection Association, 1999 Edition.
Assessment Questions
You can find the answers to the following questions in Appendix A.
|
1. |
Which of the following is not a type of motion-detection system?
|
|
|
2. |
Which of the following is a type of personnel control that helps prevent piggybacking?
|
|
|
3. |
Which of the following choices most accurately describes the prime benefit of using guards?
|
|
|
4. |
The recommended optimal relative humidity range for computer operations is:
|
|
|
5. |
How many times should a diskette be formatted to comply with TCSEC Orange Book object reuse recommendations?
|
|
|
6. |
Which of the following more closely describes the combustibles in a Class B-rated fire?
|
|
|
7. |
Which of the following is not the proper suppression medium for a Class B fire?
|
|
|
8. |
What does an audit trail or access log usually not record?
|
|
|
9. |
A brownout can be defined as a:
|
|
|
10. |
Which of the following statements is not accurate about smoke damage to electronic equipment?
|
|
|
11. |
A surge can be defined as a(n):
|
|
|
12. |
Which is not a type of a fire detector?
|
|
|
13. |
Which of the following is not considered an acceptable replacement for Halon discharge systems?
|
|
|
14. |
Which type of fire extinguishing method contains standing water in the pipe and therefore generally does not enable a manual shutdown of systems before discharge?
|
|
|
15. |
Which of the following types of control is not an example of a physical security access control?
|
|
|
16. |
Which is not a recommended way to dispose of unwanted used data media?
|
|
|
17. |
According to the NFPA, which of the following choices is not a recommended risk factor to consider when determining the need for protecting the computing environment from fire?
|
|
|
18. |
Which of the following choices is not an example of a halocarbon agent?
|
|
|
19. |
Which of the following statements most accurately describes a dry pipe sprinkler system?
|
|
|
20. |
The theft of a laptop poses a threat to which tenet of the C.I.A. triad?
|
|
|
21. |
Which is a benefit of a guard over an automated control?
|
|
|
22. |
Which is not considered a preventative security measure?
|
|
|
23. |
Which is not a PC security control device?
|
|
|
24. |
Which of the following is not an example of a clean fire-extinguishing agent?
|
|
|
25. |
What is the recommended height of perimeter fencing to keep out casual trespassers?
|
|
|
26. |
Why should extensive exterior perimeter lighting of entrances or parking areas be installed?
|
|
|
27. |
Which of the following is not a form of data erasure?
|
|
|
28. |
Which is not considered a physical intrusion detection method?
|
|
|
29. |
Which of the following statements represents the best reason to control the humidity in computer operations areas?
|
|
|
30. |
Which of the following terms refers to a standard used in determining the fire safety of a computer room?
|
|
|
31. |
Which of the following choices is not a common use for a proximity smart card?
|
|
|
32. |
Which of the following is the best description of PIDAS fencing?
|
|
|
33. |
Which of the following statements about bollards is incorrect?
|
|
Answers
|
1. |
Answer: c Host-based intrusion-detection systems are used to detect unauthorized logical access to network resources, not the physical presence of an intruder. |
|
2. |
Answer: a The other three answers are not personnel or physical controls but are technical threats or vulnerabilities. Back doors (answer b) commonly refers to Trojan horses used covertly to give an attacker backdoor network access. Hackers install back doors to gain network access at a later time. Brute force (answer c) is a cryptographic attack attempting to use all combinations of key patterns to decipher a message. Maintenance hooks (answer d) are undocumented openings into an application to assist programmers with debugging. Although intended innocently, these can be exploited by intruders. |
|
3. |
Answer: b The prime advantage to using human guards is that they can exercise discretionary judgment when the need arises. For example, during an emergency guards can switch roles from access control to evacuation support, something guard dogs or automated systems cannot. |
|
4. |
Answer: c 40% to 60% relative humidity is recommended for safe computer operations. Too low humidity can create static discharge problems, and too high humidity can create condensation and electrical contact problems. |
|
5. |
Answer: c Most computer certification and accreditation standards recommend that diskettes be formatted seven times to prevent any possibility of data remanence. |
|
6. |
Answer: c Paper is described as a common combustible and is therefore rated a class A fire. An electrical fire is rated Class C. Gas is not defined as a combustible. |
|
7. |
Answer: d Water is not a proper suppression medium for a class B fire. The other three are commonly used. |
|
8. |
Answer: a The other three answers are common elements of an access log or audit trail. |
|
9. |
Answer: c Answer a, prolonged power loss, is a blackout; answer b, momentary low voltage, is a sag; and d, momentary high voltage, is a spike. |
|
10. |
Answer: d Immediate smoke exposure to electronic equipment does little damage. However, the particulate residue left after the smoke has dissipated contains active by-products that corrode metal contact surfaces in the presence of moisture and oxygen. |
|
11. |
Answer: a Answer b, initial surge of power at start or power on, is called an inrush; c, momentary power loss, is a fault; and d, a steady interfering disturbance, is called noise. |
|
12. |
Answer: b Gas-discharge is a type of fire extinguishing system, not a fire detection system. |
|
13. |
Answer: c Existing installations are encouraged to replace Halon 1301 with one of the substitutes listed. |
|
14. |
Answer: b The other three are variations on a dry pipe discharge method with the water not standing in the pipe until a fire is detected. |
|
15. |
Answer: d |
|
16. |
Answer: d While this method might overwrite the older files, recoverable data might exist past the file end marker of the new file if the new data file is smaller than the older data file. |
|
17. |
Answer: c Although the distance of the computing facility from a fire station should be considered when initially determining the physical location of a computing facility (as should police and hospital proximity), it is not considered a primary factor in determining the need for internal fire suppression systems. |
|
18. |
Answer: c IG-541 is an inert gas agent, not a halocarbon agent. |
|
19. |
Answer: b In a dry pipe system, air pressure is maintained until the sprinkler head seal is ruptured. Answer a is incorrect because wet pipe is the most commonly used sprinkler system, dry pipe is second. Answer c describes a preaction pipe, which sounds an alarm and delays the water release. A preaction pipe may or may not be a dry pipe, but not all dry pipes are preaction. Answer d is incorrect because a dry pipe is a water release system. |
|
20. |
Answer: d Confidentiality, because the data can now be read by someone outside of a monitored environment; availability, because the user has lost the computing ability provided by the unit; and integrity, because the data residing on and any telecommunications from the portable are now suspect. |
|
21. |
Answer: a Guards can use discriminating judgment. Guards are typically more expensive than automated controls, need training as to the protection requirements of the specific site, and need to be screened and bonded. |
|
22. |
Answer: c Audit trails are detective rather than preventative, because they are used to piece together the information of an intrusion or intrusion attempt after the fact. |
|
23. |
Answer: d A cable lock is used to attach the PC to a desk; a switch control is used to prevent powering a unit off; and a port control (such as a diskette drive lock) is used to prevent data from being downloaded from the PC. |
|
24. |
Answer: a CO2, carbon dioxide, leaves a corrosive residue and is therefore not recommended for computer facility fire suppression systems. |
|
25. |
Answer: b 3′ to 4′-high fencing is considered minimal protection, for restricting only casual trespassers. Answers c and d are better protection against intentional intruders. |
|
26. |
Answer: c The other answers have nothing to do with lighting. |
|
27. |
Answer: b Remanance is what data erasure is intended to prevent. Clearing (answer a) refers to the overwriting of data media intended to be reused in the same organization. Purging (answer c) refers to degaussing or overwriting media intended to be removed from the organization. Destruction (answer d) refers to completely destroying the media. |
|
28. |
Answer: d Line supervision is the monitoring of the alarm signaling transmission medium to detect tampering. Audio detectors (answer a) monitor a room for any abnormal soundwave generation. Photoelectric sensors (answer b) receive a beam of light from a light-emitting device. Wave pattern motion detectors (answer c) generate a wave pattern and send an alarm if the pattern is disturbed. |
|
29. |
Answer: b Electrostatic discharges from static electricity can damage sensitive electronic equipment, even in small amounts. |
|
30. |
Answer: b Answer a, noncombustible, means material that will not aid or add appreciable heat to an ambient fire. Answer c, fire retardant, describes material that lessens or prevents the spread of a fire. Fire retardant coatings are designed to protect materials from fire exposure damage. Answer d, nonflammable, describes material that will not burn. |
|
31. |
Answer: a A proximity smart card is not commonly used for verifying on-line pur-chases. The other answers are all common uses of a proximity smart card. |
|
32. |
Answer: b Perimeter Intrusion Detection and Assessment System (PIDAS) fencing has intrusion detection sensors on the fence and attempts to detect an intruder scaling the fence or cutting through it. By initiating an alarm when the cable vibrates, however, PIDAS’s sensitivity can cause a high rate of false alarms, as the alarm is often triggered by animals or weather elements such as high wind. |
|
33. |
Answer: c Bollards are concrete pillars designed to deter drivers from driving vehicles into a building, and may contain exterior lighting to make them more functional and decorative. |
Part One - Focused Review of the CISSP Ten Domains
- Information Security and Risk Management
- Access Control
- Telecommunications and Network Security
- Cryptography
- Security Architecture and Design
- Operations Security
- Application Security
- Business Continuity Planning and Disaster Recovery Planning
- Legal, Regulations, Compliance, and Investigations
- Physical (Environmental) Security
Part Two - The Certification and Accreditation Professional (CAP) Credential
- Understanding Certification and Accreditation
- Initiation of the System Authorization Process
- The Certification Phase
- The Accreditation Phase
- Continuous Monitoring Process
- Appendix A Answers to Assessment Questions
- Appendix B Glossary of Terms and Acronyms
- Appendix C The Information System Security Architecture Professional (ISSAP) Certification
- Appendix D The Information System Security Engineering Professional (ISSEP) Certification
- Appendix E The Information System Security Management Professional (ISSMP) Certification
- Appendix F Security Control Catalog
- Appendix G Control Baselines
EAN: 2147483647
Pages: 239
- Chapter VII Objective and Perceived Complexity and Their Impacts on Internet Communication
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites
- Chapter XII Web Design and E-Commerce
- Chapter XVI Turning Web Surfers into Loyal Customers: Cognitive Lock-In Through Interface Design and Web Site Usability