1X on Wireless LANs
X on Wireless LANs
802.1X provides a framework for user authentication over any LANs, including wireless. For the purposes of this book, the "port" in 802.1X on wireless is an association between a wireless device and its access point. The successful exchange of Association Request and Association Response frames is reported to the 802.1X state engine as the link layer becoming active. Once associated, a station can exchange 802.1X frames in an attempt to become authorized. The completion of the 802.1X authentication exchange, including key distribution, is reported to the user as the interface coming up.
Sample 802.1X Exchange on 802.11
EAPOL exchanges look almost exactly like EAP exchanges. The main difference is that supplicants can issue EAPOL-Start frames to trigger the EAP exchange, and they can use EAPOL-Logoff messages to deauthorize the port when the station is done using the network. The examples in this section assume that a RADIUS server is used as the back-end authentication server, and therefore they show the authenticator performing translation from EAP on the front end to RADIUS on the back end. EAP authentication in RADIUS packets is specified in RFC 2869.
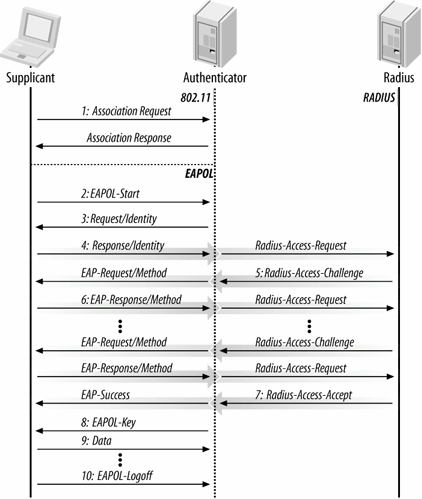
This example exchange also shows the use of EAPOL-Key frames to distribute key information for link layer security protocols. Figure 6-8 shows a sample EAPOL exchange on an 802.11 network. The figure shows a successful authentication, whose steps are:
- The supplicant associates with the 802.11 network. Association is a simple two-frame exchange which nearly always succeeds.
- The supplicant starts the 802.1X exchange with an EAPOL-Start message. This step is optional. Not all supplicants send EAPOL-Start messages, so this step may not be present.
- The "normal" EAP exchange begins. The authenticator (access point) issues an EAP-Request/Identity frame. Request/Identity frames may be sent without first having an EAPOL-Start if the access point only forwards frames for authenticated sessions. Unsolicited Request/Identity frames indicate to the supplicant that 802.1X authentication is required.
- The supplicant replies with an EAP-Response/Identity frame, which is passed on to the RADIUS server as a Radius-Access-Request packet.
- The RADIUS server determines the type of authentication that is required, and sends an EAP-Request for the method type. The EAP-Request is encapsulated in a Radius-Access-Challenge packet to the AP. When it reaches the AP, the EAP-Request is passed on to the supplicant. EAP Requests are are often denoted EAP-Request/Method, where the Method refers to the EAP method in use. If PEAP is in use, the return packet will be written as EAP-Request/PEAP.
- The supplicant gathers the reply from the user and sends an EAP-Response in return. The response is translated by the authenticator into a Radius-Access-Request with the response to the challenge as a data field.
Steps five and six repeat as many times as is necessary to complete the authentication. If it is an EAP method that requires certificate exchange, multiple steps are almost certainly required. Many EAP exchanges can require 10-20 round trips between the client and RADIUS server.
- The RADIUS server grants access with a Radius-Access-Accept packet, so the authenticator issues an EAP-Success frame and authorizes the port. Authorization may depend on parameters passed back from the RADIUS server.
- Immediately following receipt of the Access-Accept packet, the access point distributes keys to the supplicant using EAPOL-Key messages. Key distribution is discussed in the next chapter.
- Once keys are installed in the supplicant, it can begin sending data frames to access the network. It is quite common at this point for DHCP configuration to take place.
- When the supplicant is done accessing the network, it sends an EAPOL-Logoff message to put the port back into an unauthorized state.
Figure 6-8. Typical 802.1X exchange on 802.11
Exchanges similar to Figure 6-8 may be used at any point. It is not necessary for the user to begin an EAPOL exchange with the EAPOL-Start message. At any point, the authenticator can begin an EAPOL exchange by issuing an EAP-Request/Identity frame to refresh the authentication data. Re-authentications are often triggered by session timeout values to refresh keys.
Dynamic keying
The EAPOL-Key frame allows keys to be sent from the access point to the client and vice versa. Key exchange frames are sent only if the authentication succeeds; this prevents the compromise of key information. EAPOL-Key frames can be used periodically to update keys dynamically as well. Several of the weaknesses in WEP stem from the long lifetime of the keys. When it is difficult to rekey every station on the network, keys tend to be used for long periods of time. Several experts have recommended changing WEP keys on a regular basis, but no practical mechanism to do so existed until the development of 802.1X.
Introduction to Wireless Networking
- Introduction to Wireless Networking
- Why Wireless?
- What Makes Wireless Networks Different
- A Network by Any Other Name...
Overview of 802.11 Networks
- Overview of 802.11 Networks
- IEEE 802 Network Technology Family Tree
- 11 Nomenclature and Design
- 11 Network Operations
- Mobility Support
11 MAC Fundamentals
- 11 MAC Fundamentals
- Challenges for the MAC
- MAC Access Modes and Timing
- Contention-Based Access Using the DCF
- Fragmentation and Reassembly
- Frame Format
- Encapsulation of Higher-Layer Protocols Within 802.11
- Contention-Based Data Service
- Frame Processing and Bridging
11 Framing in Detail
- 11 Framing in Detail
- Data Frames
- Control Frames
- Management Frames
- Frame Transmission and Association and Authentication States
Wired Equivalent Privacy (WEP)
- Wired Equivalent Privacy (WEP)
- Cryptographic Background to WEP
- WEP Cryptographic Operations
- Problems with WEP
- Dynamic WEP
User Authentication with 802.1X
- User Authentication with 802.1X
- The Extensible Authentication Protocol
- EAP Methods
- 1X: Network Port Authentication
- 1X on Wireless LANs
11i: Robust Security Networks, TKIP, and CCMP
- 11i: Robust Security Networks, TKIP, and CCMP
- The Temporal Key Integrity Protocol (TKIP)
- Counter Mode with CBC-MAC (CCMP)
- Robust Security Network (RSN) Operations
Management Operations
- Management Operations
- Management Architecture
- Scanning
- Authentication
- Preauthentication
- Association
- Power Conservation
- Timer Synchronization
- Spectrum Management
Contention-Free Service with the PCF
- Contention-Free Service with the PCF
- Contention-Free Access Using the PCF
- Detailed PCF Framing
- Power Management and the PCF
Physical Layer Overview
- Physical Layer Overview
- Physical-Layer Architecture
- The Radio Link
- RF Propagation with 802.11
- RF Engineering for 802.11
The Frequency-Hopping (FH) PHY
- The Frequency-Hopping (FH) PHY
- Frequency-Hopping Transmission
- Gaussian Frequency Shift Keying (GFSK)
- FH PHY Convergence Procedure (PLCP)
- Frequency-Hopping PMD Sublayer
- Characteristics of the FH PHY
The Direct Sequence PHYs: DSSS and HR/DSSS (802.11b)
- The Direct Sequence PHYs: DSSS and HR/DSSS (802.11b)
- Direct Sequence Transmission
- Differential Phase Shift Keying (DPSK)
- The Original Direct Sequence PHY
- Complementary Code Keying
- High Rate Direct Sequence PHY
11a and 802.11j: 5-GHz OFDM PHY
- 11a and 802.11j: 5-GHz OFDM PHY
- Orthogonal Frequency Division Multiplexing (OFDM)
- OFDM as Applied by 802.11a
- OFDM PLCP
- OFDM PMD
- Characteristics of the OFDM PHY
11g: The Extended-Rate PHY (ERP)
- 11g: The Extended-Rate PHY (ERP)
- 11g Components
- ERP Physical Layer Convergence (PLCP)
- ERP Physical Medium Dependent (PMD) Layer
A Peek Ahead at 802.11n: MIMO-OFDM
11 Hardware
- 11 Hardware
- General Structure of an 802.11 Interface
- Implementation-Specific Behavior
- Reading the Specification Sheet
Using 802.11 on Windows
11 on the Macintosh
Using 802.11 on Linux
- Using 802.11 on Linux
- PCMCIA Support on Linux
- Linux Wireless Extensions and Tools
- Agere (Lucent) Orinoco
- Atheros-Based cards and MADwifi
- 1X on Linux with xsupplicant
Using 802.11 Access Points
- Using 802.11 Access Points
- General Functions of an Access Point
- Power over Ethernet (PoE)
- Selecting Access Points
- Cisco 1200 Access Point
- Apple AirPort
Logical Wireless Network Architecture
- Logical Wireless Network Architecture
- Evaluating a Logical Architecture
- Topology Examples
- Choosing Your Logical Architecture
Security Architecture
- Security Architecture
- Security Definition and Analysis
- Authentication and Access Control
- Ensuring Secrecy Through Encryption
- Selecting Security Protocols
- Rogue Access Points
Site Planning and Project Management
- Site Planning and Project Management
- Project Planning and Requirements
- Network Requirements
- Physical Layer Selection and Design
- Planning Access-Point Placement
- Using Antennas to Tailor Coverage
11 Network Analysis
11 Performance Tuning
Conclusions and Predictions
EAN: 2147483647
Pages: 179
