Introduction to XACML
| eXtensible Access Control Markup Language (XACML) version 2.0 (refer to [XACML2] for details) is an approved security policy management standard under OASIS (http://www.oasis-open.org/committees/tc_home.php?wg_abbrev=xacml). It is both a policy language and an access-control decision request/response language encoded in XML. It defines a standard format for the expression of authorization rules and policies along with a standard way of evaluating rules and policies to produce authorization decisions. In addition, XACML defines an optional format for making authorization decision requests and responses. There are many similarities between XACML and the other policy management initiatives discussed previously. XACML can handle both XML documents and non-XML systems, though it can also handle non-XML objects using a custom context handler. It uses a declarative data model similar to CIM policy. It is generic to all industry sectors, but flexible enough to include new functionalities. XACML is complementing SAML 2.0 by providing functionality that handles complex policy sets and rules. There are a few business problems related to security access control today. Many customer environments have their own security policy governing which resources a service requester can access. To be flexible and adaptive to customer IT security requirements, commercial off-the-shelf vendor products intend to be "generic" enough to support different security access control requirements in heterogeneous or customized environments. For example, some vendor products choose to provide "maximum possible privilege" by default for accessing data and executing business functions and actions. In other words, every user can access all functions unless the access control policies are customized. Once these vendor products are implemented, customers can customize local administrative security policy and configure policy enforcement points. Unfortunately, customized security access control implementations are fairly expensive, and they are unreliable for modifying security policies manually due to their complexity. In addition, they are not scalable and timely if the number of applications or policy enforcement points is large. Thus, a flexible policy system for access control is required to address these problems. Isn't SAML authorization decision assertion used in determining access rights for a service request? SAML provides a very basic assertion format and protocol between policy enforcement point and policy decision point. However, it does not specify any action or how a policy decision point should get information on which its decision will depend. One major technology driver for creating XACML is the need to access partial content of XML documents. The current security method is to use encryption to control access to the entire XML document. Users are either authorized to view the entire XML document or denied access to any part of it. An example is an XML document containing a credit card payment transaction, where user A (call center personnel) is authorized to access the entire payment transaction except the full credit card number, while user B (claims department) is able to read the entire payment transaction. This is undesirable and very often this access control mechanism does not meet local business requirements. In a typical application environment, a user wants to make request to access certain resources. The Policy Enforcement Point (PEP) is a system or application that protects the resources. The PEP needs to check whether the service requester is eligible to access the resources. It sends the resources request to the Policy Decision Point (PDP), which looks up the security access control policies. XACML provides both a policy language and an access-control decision request/response language to meet the security access control requirements. With XACML, the PEP forms a query language to ask the PDP whether or not a given action should be allowed. The PDP responds by returning the value of either Permit, Deny, Indeterminate (decision cannot be made due to some errors or missing values), or Not Applicable (the request cannot be answered by this service). XACML provides a rich policy language data model that is able to define sophisticated and flexible security policies. Figure 7-7 shows the full hierarchy of components of an XACML policy extracted from the XACML schema, which may be too complex for novice readers. The following are the key components that may be of interest to most readers:
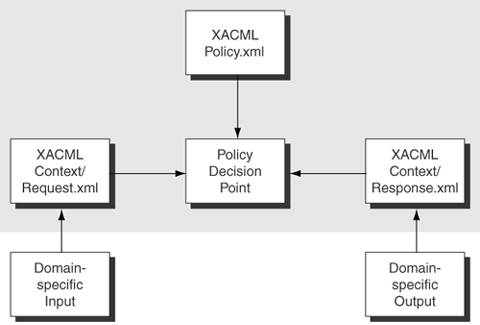
Figure 7-7. XACML policy language model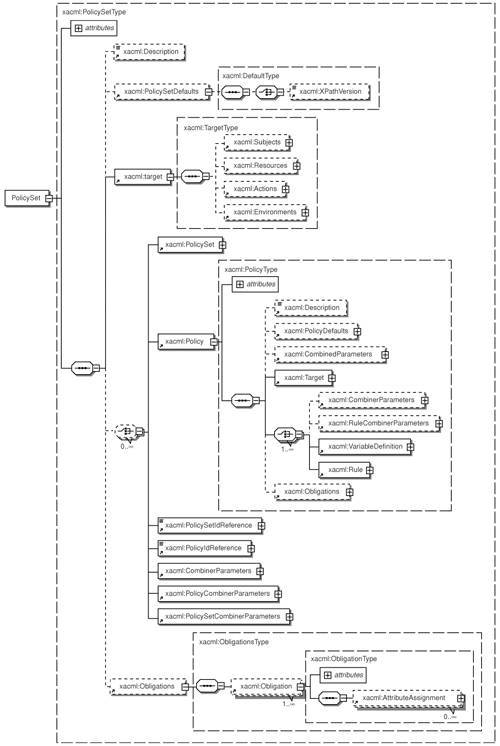 The XML Schema definition for XACML describes the input and output of policy decision points in an XACML context. A context denotes a canonical representation of a decision request and an authorization decision. Figure 7-8 shows the XACML context [XACML11] where a policy decision point makes reference to the attributes of a policy or identifies the attribute by subject, resource, action, or environment. The XACML context handler for requests converts the input format from domain-specific input, say, using XPath or any XSLT transformation mechanism. Upon processing the policy rules by the policy decision point, the XACML context handler for responses converts the authorization decision to a domain-specific output format. The shaded area that covers the XACML policy, policy decision point, and the XACML context handlers are the scope of XACML. Figure 7-8. XACML context Sun's XACML kit (http://sunxacml.sourceforge.net) is an open source implementation of XACML 1.1. There is also a C# implementation of XACML under http://mvpos.sourceforge.net/. Parthenon Computing's JiffyXACML (http://www.parthenoncomputing.com) is a free binary release that provides some specific functionality. A list of XACML implementations appears on the OASIS XACML TC home page (http://www.oasis-open.org/committees/tc_home.php?wg_abbrev=xacml), along with an XACML reference list that includes publicly announced adoptions of XACML. XACML 2.0XACML 2.0 [XACML2] does not have major functional changes. There are a few syntactic changes to make the policy language more flexible in its support of complex security requirements. Apart from the syntactic changes, the major change in XACML 2.0 is the introduction of six profiles:
There are some new features to the policy language. For details, refer to [XACML2]. The following are new features that allow more flexibility in expressing policies and rules.
Some changes in XACML 2.0 are syntactical. They do not have a major impact on the core policy definition functionality. However, some changes are semantic changes. The following highlight the major syntactic changes in the context schema and the policy schema. For details, refer to [XACML2changes].
|
EAN: 2147483647
Pages: 204
- Step 1.1 Install OpenSSH to Replace the Remote Access Protocols with Encrypted Versions
- Step 3.3 Use WinSCP as a Graphical Replacement for FTP and RCP
- Step 3.4 Use PuTTYs Tools to Transfer Files from the Windows Command Line
- Step 4.5 How to use OpenSSH Passphrase Agents
- Step 5.2 Troubleshooting Common OpenSSH Errors/Problems