IDENTIFYING WIRELESS NETWORK DEFENSES AND COUNTERMEASURES
| | ||
| | ||
| | ||
Do not confuse this section with network hardening or a guide to locking down your access points. It is merely a section dedicated to identifying any implemented WLAN countermeasures and potentially leveraging those defenses. Just as with any other network or system target, it is imperative that you determine the types of systems, where they are located, and their configurations. WLANs, APs, and wireless clients are no different.
The information presented will provide you an overview to help you learn to identify systems and determine what type of security measures have been implemented. For instance, you will be able to quickly determine whether a system is without security and considered to be " Open System Authentication." You will also learn to determine the difference between a system with WEP implemented and the implemented bit-length for the shared secret key via analysis of the 802.11 header and initialization vector. In addition to infrastructure-based controls, you will be able to determine whether common vendor-implemented security features such as MAC-based access control lists (ACLs) have been defined on the access points, or if protocol or firmware upgrades have been made to the WEP algorithm or 802.11b. Lastly, we will cover methods for leveraging multiple layers of encryption, such as embedded PKI schemas, gateway-based IPSec, and application-layer VPNs, including SSL tunnels.
There are a few prerequisites for this section if you want to get the most out of it. In addition to packet analysis (covered in the previous section), you should be able to understand the basics of encryption technologies and cryptography key management.
Here's a list of basic encryption technology resources:
-
http://www.crypto.com Matt Blaze's cryptography resource page, an excellent source for research papers, cryptography algorithm analysis, and overall knowledge transfer.
-
http://developer.netscape.com/docs/manuals/security/pkin/contents.htm Sun has provided a good resource as an introduction to public-key cryptography.
-
http://www-cs.engr.ccny.cuny.edu/~csmma An excellent academia resource, provided by Professor Michael Anshel, that has links to nearly all types of cryptography technologies.
SSID
The SSID is the first piece of information required to connect to a wireless network. 802.11 networks use the SSID to distinguish BSSs from each other. By itself the SSID is not intended to be used as a password or access control measure, but users are often led to believe this by vendors . Gathering the SSID is simple; all war-driving software shown earlier in the chapter will report a network's SSID or "network name ." If the target access point responds to a Broadcast SSID Probe, most wireless card drivers configured with an SSID of ANY will be able to associate with the wireless network. Having the SSID set to ANY usually makes the driver send a probe request to the broadcast address with a zerolength SSID. This, in turn , causes any access point that will respond to these requests (most do by default) to issue a response with its SSID and info . In the intended case, this makes it easier on the user because the user doesn't have to remember the SSID to connect to the wireless LANbut, of course, it makes it much simpler for attackers to gather this data.
SSIDs can be found in a variety of 802.11 traffic:
-
Beacons By default, beacons are sent continually by the access point and can be observed with a wireless sniffer. The Ethereal filter string to see only beacons is
wlan.fc.type==0 and wlan.fc.subtype==8
If you would like to filter out the beacon 's frames (they are transmitted constantly and get in the way), just enclose the previous statement in !(), like so:
!(wlan.fc.type==0 and wlan.fc.subtype==8)
-
Probe Requests Probe Requests are sent by client systems wishing to connect to the wireless network. If the client is configured with an SSID, it will be shown in the request. A Probe Request with a null SSID likely indicates a network name of ANY configured for the card.
-
Probe Responses Probe Responses are sent in response to a Probe Request. The Probe Request can either have a blank SSID or the SSID of the network the client wishes to connect to.
-
Association and Reassociation Requests These requests are made by the client when joining or rejoining the network. Reassociation requests are meant to support wireless clients roaming from access point to access point within the same ESS, but they can also be issued if the clients wander out of a given AP's range and then back into range.
If the network you are monitoring has blocked the Broadcast Probe Responses or removed the SSID from beacon frames, you may need to wait until a client tries to reassociate to obtain the SSID. You can help this process along with the essid_jack tool from the Air-Jack toolkit (http://802.11ninja.net). essid_jack will send a deauthentication frame to the broadcast address that is spoofed to look like it's coming from the access point. This kicks off all the active clients for the given channel and causes them to try and reconnect to the WLAN. The client Probe Requests and AP Responses will contain the "hidden" SSID.
To use essid_jack, supply the BSSID address and channel of the wireless network you are trying to enumerate. By default, it will send the packet to the broadcast address affecting all active clients, but you can specify a single client MAC to target with the -d switch, as shown here:
[root@localhost tools]# ./essid_jack -b 00:40:96:54:1c:0b -d 00:02:2D:07:E2:E1 -c 11 -i aj0 Got it, the essid is (escape characters are c style): "sigma"
MAC Access Control
Although not defined in the 802.11 specification, MAC-level access controls have been implemented by most vendors to help beef up the inherently insecure nature of 802.11. When using MAC access control, the admin will define a list of "approved" client MAC addresses that are allowed to connect to the access point. Although this may be feasible on small networks, it does require the administrator to track the MAC addresses of all wireless clients and can become a burden in larger installations. Besides the administrative overhead, the MAC address does not provide a good security mechanism because it is both easily observable and reproducible. Any of the station MACs can be observed with a wireless sniffer, and the attacker's MAC address can be changed easily in most cases. Therefore, the attacker simply needs to monitor the network, note the clients that are connecting successfully to the access point, and then change their MAC address to match one of the working clients.
Because it's not defined in the 802.11 spec, there is no packet flag that says "I'm using MAC ACLs," but you can usually figure this out via deduction . If you have a correct SSID and WEP key but they still aren't able to associate, they may be using MAC filtering (or another scheme, such as 802.1x). AiroPeek NX provides an easy way to see the relationships of systems on the wireless network. Its Peer Map, shown in Figure 8-13, will show each system and the other stations it is in communication with. As shown, all the nodes are talking to the 00:07:0E:B9:94:32 station, so it is most likely the access point.
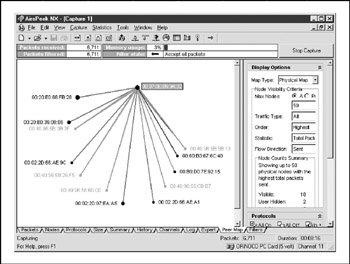
Figure 8-13: The Peer Map tab
gvoid11
| Popularity: | 7 |
| Simplicity: | 6 |
| Impact: | 8 |
| Risk Rating: | 7 |
WLSec's gvoid11 is a popular open-source tool that has implemented some basic 802.11b attacks. In general, the two types of attacks gvoid11 can execute are deauthentication and authentication. The authentication attacks can be utilized to denial of service (DoS) wireless access points by flooding them with authentication requests. This type of DoS is a CPU resource consumption attack. Deauthentication attacks are utilized to denial of service entire wireless networks. The most popular configuration for these death attacks is to spoof the BSSID field for seemingly valid packets, thereby dropping systems from the network.
The installation of gvoid11 is quite straightforward. First, you compile and install Linux HostAP-driver (http://hostap.epitest.fi) version 0.1.2 or greater. Once that is complete, you download and unpack the Linux HostAPD binary. Your system now has all the software necessary and is ready to be configured. Set your wireless Prism2 card to reside in master mode by running iwconfig wlan0 mode master , then enabling the HostAP daemon mode via iwpriv wlan0 hostapd 1 . Finally, you may start your tool with either gvoid11_penetration or gvoid11 .
The gvoid11 interface is shown in Figure 8-14. As you can see, it has the ability to channel hop, monitor wireless traffic in near real time, and execute attacks (via the Execute button). gvoid11 can be downloaded from http://www.wlsec.net/void11.
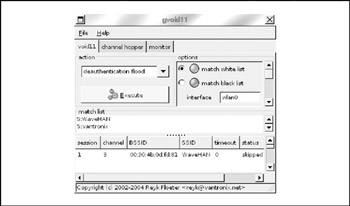
Figure 8-14: gvoid11 interface
WEP
Most war-driving tools will indicate whether or not a network is using WEP encryption. NetStumbler will show a small padlock in the network's icon and indicate "WEP" under the encryption column when WEP encryption is found. Kismet will show a "Y" under the W (for WEP) column when it finds encrypted networks.
Wireless sniffers will show WEP status as well. tcpdump uses the "PRIVACY" flag when WEP is in use and show the IV for each packet, when collected, as shown here:
00:30:36.943042 Beacon (Aironet_350) [1.0 2.0 5.5 11.0 Mbit] ESS CH: 6, PRIVACY 00:30:36.948759 Data IV:1aa7f6 Pad 0 KeyID 0 00:30:36.949722 Data IV:1ba7f6 Pad 0 KeyID 0 00:30:36.958387 Data IV:1ba7f6 Pad 0 KeyID 0 00:30:36.959349 Data IV:1ca7f6 Pad 0 KeyID 0 00:30:36.968942 Data IV:1ca7f6 Pad 0 KeyID 0 00:30:36.970242 Data IV:1da7f6 Pad 0 KeyID 0 00:30:36.978462 Data IV:1da7f6 Pad 0 KeyID 0 00:30:36.979718 Data IV:1ea7f6 Pad 0 KeyID 0 00:30:36.988863 Data IV:1ea7f6 Pad 0 KeyID 0 00:30:36.990004 Data IV:1fa7f6 Pad 0 KeyID 0 00:30:36.998934 Data IV:1fa7f6 Pad 0 KeyID 0 00:30:37.000148 Data IV:20a7f6 Pad 0 KeyID 0 00:30:37.008549 Data IV:20a7f6 Pad 0 KeyID 0 00:30:37.009741 Data IV:21a7f6 Pad 0 KeyID 0
EAN: N/A
Pages: 127