Try This
Try This!
Go grab this trace file from www.packet-level.com > Trace Files > 127guy.cap and perform the following steps:
-
Filter the trace file for all packets to or from 127.0.0.1.
-
Save the new, filtered set of data by the name "Just127.cap."
-
On the Sniffer, look at the matrix view of Just127.cap. What do you notice when you view the matrix screen using the IP or MAC view. Cool, eh? You'll see that there are a whole bunch of devices using the source IP address 127.0.0.1.
-
Now go lookup that port number - 2301. What service is this traffic destined to? Yipes - that's right! Compaq Insight Manager - ugh… a bit buggy folks. I should let you know that I did just look at some of this traffic recently and did not see this bizarre type of behavior. Whew!
Build IP address based filters when you are just focused in on IP traffic. You can filter on the IP broadcast address, multicast addresses, or unicast addresses. Consider putting together another "Fred" filter based on his IP address (as long as it is statically assigned). Also build a set of 'key device' filters so you're ready when you need to watch those key boxes. For example, build an IP address filter on all traffic to or from your web server, file servers, accounting servers, backup servers, print servers, etc. You might also want to build an IP address filter for the boss's traffic to ensure you are always ready to start grabbing his/her traffic when a problem arises.
Remember, it’s OK to use the IP address filters when you know the IP address of the device you are monitoring - if you are using DHCP, be careful to ensure you are catching the traffic to and from the right device.
What if you are only interested in filtering on a portion of an IP address? Now you'll have to build a pattern-based filter. Even though I'm covering this in Chapter 4, I'll put a quick shot of the pattern up here.
For example, let's say you want to know how many Compaq devices are on your network. You can filter on the first three bytes of the hardware address - these three bytes are the Organizational Unit Identifier (OUI) that identifies the vendor of the network interface card.
| Note | Download the OUI list from http://standards.ieee.org/ regauth/oui/oui.txt. -- Laura |
Figure 15 shows how you can set up a filter to look for packets that use one of the Compaq OUIs (0x00104B). This is a pattern filter, however. I’ll cover pattern filtering in greater in detail in Chapter 4.
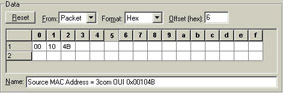
Figure 15: The filter to catch all traffic from systems using the Compaq OUI 0x00104B
Now let's assume we want to capture all traffic to devices with IP addresses that start with 10.2.4.x. Figure 16 shows the pattern we'll build here. Remember that we need to translate the address into hexadecimal - which is 0x0a.02.04.

Figure 16: When you define filter patterns you only need to define the first bytes of the address.
Certainly, this is pretty simplistic here. There are a bunch o' networks out there that use Variable Length Subnet Masks (VLSM), which mean the network portion may not end on a nice 8-bit boundary. We'll work with these sticky matters further in Chapter 4.
What other IP address filters should you build? Certainly you should have an IP broadcast filter (255.255.255.255d) and subnet broadcast filters (for example, 10.2.4.255d).
Just as we talked about before, you can fill in multiple lines to add more addresses that should be OR'd together in the filter.
EAN: 2147483647
Pages: 65