Services (as Web services)
In Chapter 3 we introduced the concept of services and how they provide a means of encapsulating various extents of logic. Manifesting services in real world automation solutions requires the use of a technology capable of preserving fundamental service-orientation, while implementing real world business functionality.
Web services provide the potential of fulfilling these primitive requirements, but they need to be intentionally designed to do so. This is because the Web services framework is flexible and adaptable. Web services can be designed to duplicate the behavior and functionality found in proprietary distributed systems, or they can be designed to be fully SOA-compliant. This flexibility has allowed Web services to become part of many existing application environments and has been one of the reasons behind their popularity. It also reveals the fact that Web services are not necessarily inherently service-oriented.
Note
We use the terms "Web services" and "services" interchangeably throughout this book.
Let's start with an overview of the most basic Web services design concepts. Fundamentally, every Web service can be associated with:
- a temporary classification based on the roles it assumes during the runtime processing of a message
- a permanent classification based on the application logic it provides and the roles it assumes within a solution environment
We explore both of these design classifications in the following two sections:
- service roles (temporary classifications)
- service models (permanent classifications)
5.2.1. Service roles
A Web service is capable of assuming different roles, depending on the context within which it is used. For example, a service can act as the initiator, relayer, or the recipient of a message. A service is therefore not labeled exclusively as a client or server, but instead as a unit of software capable of altering its role, depending on its processing responsibility in a given scenario.
It is not uncommon for a Web service to change its role more than once within a given business task. It is especially not uncommon for a Web service within an SOA to assume different roles in different business tasks.
Provided here are descriptions of the fundamental service roles.
Service provider
The service provider role is assumed by a Web service under the following conditions:
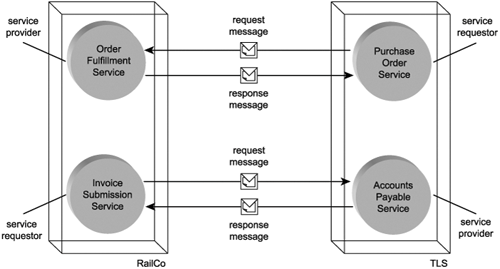
- The Web service is invoked via an external source, such as a service requestor (Figure 5.2).
Figure 5.2. As the recipient of a request message, the Web service is classified as a service provider.
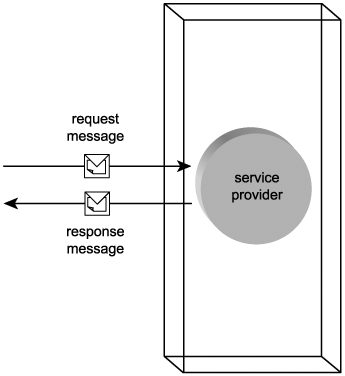
- The Web service provides a published service description offering information about its features and behavior. (Service descriptions are explained later in this chapter.)
The service provider role is synonymous with the server role in the classic client-server architecture. Depending on the type of message exchange used when invoking a service provider, the service provider may reply to a request message with a response message. (Types of message exchanges are categorized as "message exchange patterns," which are explained in the next chapter.)
The term "service provider" also is used to identify the organization (or individual) responsible for actually providing the Web service. To help distinguish the service role from the service's actual provider, the following, more qualified terms are sometimes used:
- service provider entity (the organization or individual providing the Web service)
- service provider agent (the Web service itself, acting as an agent on behalf of its owner)
It is, however, most common to simply refer to the service being invoked as the service provider.
Note
A service provider agent is different from a service agent, which is a small runtime program used to perform generic processing tasks in support of Web services. Service agents are explained in Chapter 18.
Service requestor
Any unit of processing logic capable of issuing a request message that can be understood by the service provider is classified as a service requestor. A Web service is always a service provider but also can act as a service requestor.
Note
Almost all of the service requestors discussed in this book are classified as Web services and are referenced and depicted as such. Chapter 18 provides platform-specific details about how Web services are implemented and how the physical parts of a Web service interact in service provider and service requestor roles.
A Web service takes on the service requestor role under the following circumstances:
- The Web service invokes a service provider by sending it a message (Figure 5.3).
Figure 5.3. The sender of the request message is classified as a service requestor.
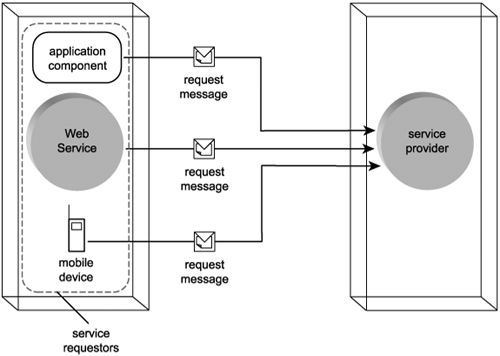
- The Web service searches for and assesses the most suitable service provider by studying available service descriptions. (Service descriptions and service registries are covered in the Service descriptions (with WSDL) section.)
The service requestor is the natural counterpart to the service provider, comparable to the client in a typical client-server environment. It is important to note that a service provider is not acting as a service requestor when it sends a message in response to a request message. A service requestor is best viewed as a software program that initiates a conversation with a service provider.
As with "service provider," this term is subject to some ambiguity. A service requestor can represent both the Web service itself as well as the Web service owner. Therefore, the following extended terms are available (but not really used that often):
- service requestor entity (the organization or individual requesting the Web service)
- service requestor agent (the Web service itself, acting as an agent on behalf of its owner)
Note
Another term frequently used instead of service requestor is service consumer.
Intermediaries
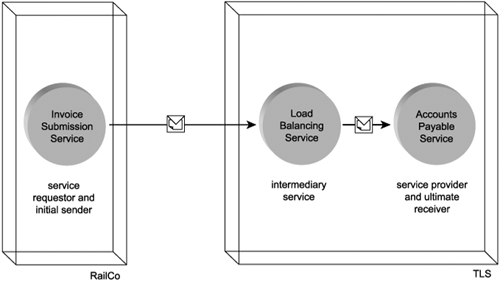
The communications framework established by Web services contrasts the predictable nature of traditional point-to-point communications channels. Though less flexible and less scalable, point-to-point communication was a great deal easier to design. Web services communication is based on the use of messaging paths, which can best be described as point-to-* paths. This is because once a service provider submits a message, it can be processed by multiple intermediate routing and processing agents before it arrives at its ultimate destination. (Message paths are explained at the end of this chapter.)
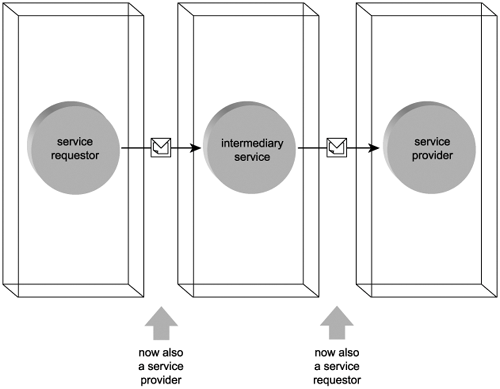
Web services and service agents that route and process a message after it is initially sent and before it arrives at its ultimate destination are referred to as intermediaries or intermediary services. Because an intermediary receives and submits messages, it always transitions through service provider and service requestor roles (Figure 5.5).
Figure 5.5. The intermediary service transitions through service provider and service requestor roles while processing a message.
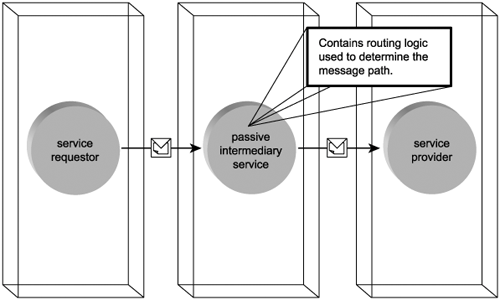
There are two types of intermediaries. The first, known as a passive intermediary, is typically responsible for routing messages to a subsequent location (Figure 5.6). It may use information in the SOAP message header to determine the routing path, or it may employ native routing logic to achieve some level of load balancing. Either way, what makes this type of intermediary passive is that it does not modify the message.
Figure 5.6. A passive intermediary service processing a message without altering its contents.
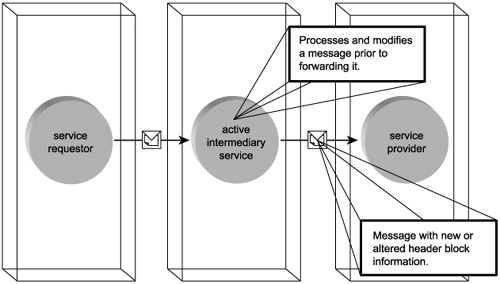
Like passive intermediary services, active intermediaries also route messages to a forwarding destination. Prior to transmitting a message, however, these services actively process and alter the message contents (Figure 5.7). Typically, active intermediaries will look for particular SOAP header blocks and perform some action in response to the information they find there. They almost always alter data in header blocks and may insert or even delete header blocks entirely. (Header blocks are explained later in this chapter.)
Figure 5.7. An active intermediary service.
Initial sender and ultimate receiver
Initial senders are simply service requestors that initiate the transmission of a message. Therefore, the initial sender is always the first Web service in a message path. The counterpart to this role is the ultimate receiver. This label identifies service providers that exist as the last Web service along a message's path (Figure 5.8).
Figure 5.8. Web services acting as initial sender and ultimate receiver.
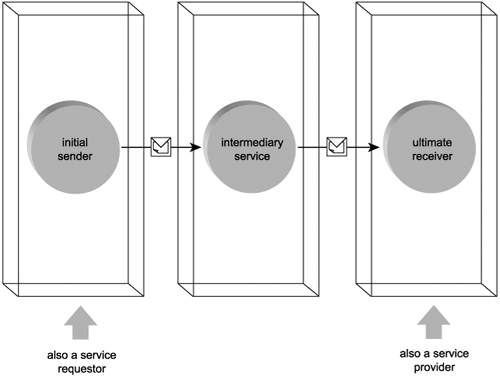
Note that intermediary services can never be initial senders or ultimate receivers within the scope of a service activity.
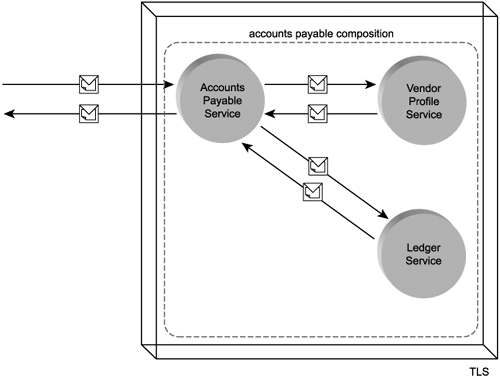
Service compositions
As the name suggests, this particular term does not apply to a single Web service, but to a composite relationship between a collection of services. Any service can enlist one or more additional services to complete a given task. Further, any of the enlisted services can call other services to complete a given sub-task. Therefore, each service that participates in a composition assumes an individual role of service composition member (Figure 5.10).
Figure 5.10. A service composition consisting of four members.
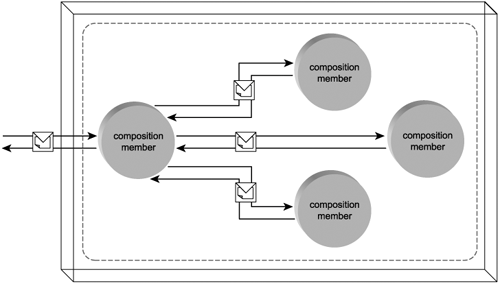
Typically, Web services need to be designed with service composition in mind to be effective composition members. Service-orientation principles place an emphasis on composability, allowing some Web services to be designed in such a manner that they can be pulled into future service compositions without a foreknowledge of how they will be utilized.
The concept of service composability is very important to service-oriented environments (and is explained as a service-orientation principle in Chapter 8). In fact, service composition is frequently governed by WS-* composition extensions, such as WS-BPEL and WS-CDL, which introduce the related concepts of orchestration and choreography, respectively (as explained in Chapter 6).
Note
Service compositions also are referred to as service assemblies.
Note
A characteristic of this particular composition that is not discussed here is the fact that all three actions we described would very likely be wrapped in a transaction. Should one of them fail, all others would be rolled back. (Concepts relating to service transactions are covered in Chapter 6.)
5.2.2. Service models
The roles we've explored so far are agnostic to the nature of the functionality being provided by the Web service. They are generic states that a service can enter within a generic context. The manner in which services are being utilized in the real world, though, has led to a classification based on the nature of the application logic they provide, as well as their business-related roles within the overall solution. These classifications are known as service models.
The sections that follow describe the basic set of common service models. Additional service models are introduced in later chapters. Appendix B further provides a reference table listing all service models covered in this book. It is important to note that a service can and frequently does belong to more than one service model.
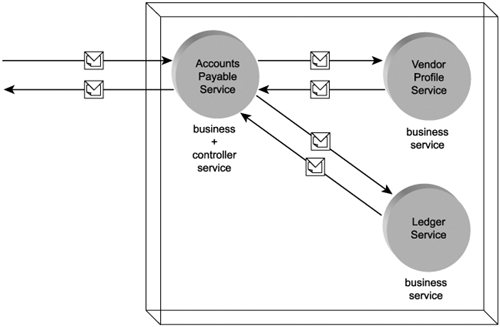
Business service model
Within an SOA, the business service represents the most fundamental building block. It encapsulates a distinct set of business logic within a well-defined functional boundary. It is fully autonomous but still not limited to executing in isolation, as business services are frequently expected to participate in service compositions.
Business services are used within SOAs as follows:
- as fundamental building blocks for the representation of business logic
- to represent a corporate entity or information set
- to represent business process logic
- as service composition members
For future reference, when building an SOA around layers of abstraction, the business service model can correspond to the business service layer introduced in Chapter 9. In this case the business service would act as a controller, composing utility application services. (The controller service model is explained shortly.)
Utility service model
Any generic Web service or service agent designed for potential reuse can be classified as a utility service. The key to achieving this classification is that the reusable functionality be completely generic and non-application specific in nature.
Utility services are used within SOAs as follows:
- as services that enable the characteristic of reuse within SOA
- as solution-agnostic intermediary services
- as services that promote the intrinsic interoperability characteristic of SOA
- as the services with the highest degree of autonomy
When working with the service abstraction layers described in Chapter 9, a utility service is most commonly associated with the application service layer. As a result, a utility service can be referred to as a utility application service.
Controller service model
Service compositions are comprised of a set of independent services that each contribute to the execution of the overall business task. The assembly and coordination of these services is often a task in itself and one that can be assigned as the primary function of a dedicated service or as the secondary function of a service that is fully capable of executing a business task independently. The controller service fulfills this role, acting as the parent service to service composition members.
Controller services are used within SOAs as follows:
- to support and implement the principle of composability
- to leverage reuse opportunities
- to support autonomy in other services
Note that controller services themselves can become subordinate service composition members. In this case the composition coordinated by a controller is, in its entirety, composed into a larger composition. In this situation there may be a master controller service that acts as the parent to the entire service composition, as well as a sub-controller, responsible for coordinating a portion of the composition (Figure 5.12).
Figure 5.12. A service composition consisting of a master controller, a sub-controller, four business services, and one utility service.
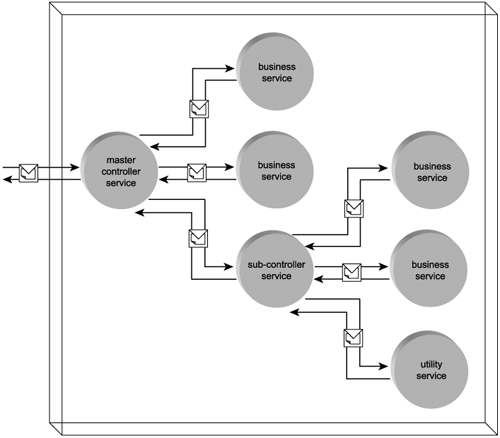
The controller service model is used frequently when building SOA with specialized service abstraction layers, as explained later in Chapter 9.
|
SUMMARY OF KEY POINTS |
|---|
|
Introduction
- Why this book is important
- Objectives of this book
- Who this book is for
- What this book does not cover
- How this book is organized
- Additional information
Case Studies
- Case Studies
- How case studies are used
- Case #1 background: RailCo Ltd.
- Case #2 background: Transit Line Systems Inc.
Part I: SOA and Web Services Fundamentals
Introducing SOA
- Introducing SOA
- Fundamental SOA
- Common characteristics of contemporary SOA
- Common misperceptions about SOA
- Common tangible benefits of SOA
- Common pitfalls of adopting SOA
The Evolution of SOA
- The Evolution of SOA
- An SOA timeline (from XML to Web services to SOA)
- The continuing evolution of SOA (standards organizations and contributing vendors)
- The roots of SOA (comparing SOA to past architectures)
Web Services and Primitive SOA
- Web Services and Primitive SOA
- The Web services framework
- Services (as Web services)
- Service descriptions (with WSDL)
- Messaging (with SOAP)
Part II: SOA and WS-* Extensions
Web Services and Contemporary SOA (Part I: Activity Management and Composition)
- Web Services and Contemporary SOA (Part I: Activity Management and Composition)
- Message exchange patterns
- Service activity
- Coordination
- Atomic transactions
- Business activities
- Orchestration
- Choreography
Web Services and Contemporary SOA (Part II: Advanced Messaging, Metadata, and Security)
- Web Services and Contemporary SOA (Part II: Advanced Messaging, Metadata, and Security)
- Addressing
- Reliable messaging
- Correlation
- Policies
- Metadata exchange
- Security
- Notification and eventing
Part III: SOA and Service-Orientation
Principles of Service-Orientation
- Principles of Service-Orientation
- Service-orientation and the enterprise
- Anatomy of a service-oriented architecture
- Common principles of service-orientation
- How service-orientation principles inter-relate
- Service-orientation and object-orientation (Part II)
- Native Web service support for service-orientation principles
Service Layers
- Service Layers
- Service-orientation and contemporary SOA
- Service layer abstraction
- Application service layer
- Business service layer
- Orchestration service layer
- Agnostic services
- Service layer configuration scenarios
Part IV: Building SOA (Planning and Analysis)
SOA Delivery Strategies
- SOA Delivery Strategies
- SOA delivery lifecycle phases
- The top-down strategy
- The bottom-up strategy
- The agile strategy
Service-Oriented Analysis (Part I: Introduction)
- Service-Oriented Analysis (Part I: Introduction)
- Service-oriented architecture vs. Service-oriented environment
- Introduction to service-oriented analysis
- Benefits of a business-centric SOA
- Deriving business services
Service-Oriented Analysis (Part II: Service Modeling)
- Service-Oriented Analysis (Part II: Service Modeling)
- Service modeling (a step-by-step process)
- Service modeling guidelines
- Classifying service model logic
- Contrasting service modeling approaches (an example)
Part V: Building SOA (Technology and Design)
Service-Oriented Design (Part I: Introduction)
- Service-Oriented Design (Part I: Introduction)
- Introduction to service-oriented design
- WSDL-related XML Schema language basics
- WSDL language basics
- SOAP language basics
- Service interface design tools
Service-Oriented Design (Part II: SOA Composition Guidelines)
- Service-Oriented Design (Part II: SOA Composition Guidelines)
- Steps to composing SOA
- Considerations for choosing service layers
- Considerations for positioning core SOA standards
- Considerations for choosing SOA extensions
Service-Oriented Design (Part III: Service Design)
- Service-Oriented Design (Part III: Service Design)
- Service design overview
- Entity-centric business service design (a step-by-step process)
- Application service design (a step-by-step process)
- Task-centric business service design (a step-by-step process)
- Service design guidelines
Service-Oriented Design (Part IV: Business Process Design)
- Service-Oriented Design (Part IV: Business Process Design)
- WS-BPEL language basics
- WS-Coordination overview
- Service-oriented business process design (a step-by-step process)
Fundamental WS-* Extensions
- Fundamental WS-* Extensions
- You mustUnderstand this
- WS-Addressing language basics
- WS-ReliableMessaging language basics
- WS-Policy language basics
- WS-MetadataExchange language basics
- WS-Security language basics
SOA Platforms
Appendix A. Case Studies: Conclusion
EAN: 2147483647
Pages: 150