Wireless LANs
|
Objective:
|
The most popular standard for wireless LAN services is the 802.11 family of specifications. It was developed by the IEEE for wireless LAN technology in 1997. Wireless LANs are data communication systems that were developed to transmit data over electromagnetic waves. Wireless LANs (WLANs) have become popular because of several factors, primarily cost and convenience.
Wireless equipment costs are similar to those of their wired counterparts, except that there are no cable plant costs that are associated with wired LANs. The cable plant is made up of the physical wires of your network infrastructure. Therefore, a business can move into a new or existing facility without cabling and incur none of the usual costs of running a LAN drop to each end user. Besides cost savings, wireless equipment is more convenient. Just think about that last group meeting or 35 students in a classroom with each requiring a network connection. Wireless makes using network services much easier and allows users to move around freely.
The next section starts off by discussing some wireless basics, and then moves on to wireless attack hacking tools and some ways to secure wireless networks.
Wireless LAN Basics
|
Objective:
|
A simple WLAN consists of two or more computers connected via a wireless connection. The wireless connection does not consist of a cable or wired connection. The computers are connected via wireless network cards that transmit the data over the airwaves. An example of this can be seen in Figure 9.1.
Figure 9.1. Ad-hoc wireless LAN.
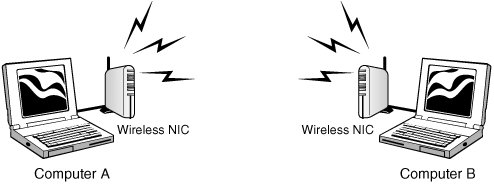
Figure 9.1 shows an example of two computers operating in ad-hoc mode. This is one of two modes available to wireless users: The other one is infrastructure. Ad-hoc mode doesn't need any equipment except wireless network adaptors. Ad-hoc allows a point-to-point type of communication that works well for small networks and is based on a peer-to-peer style of communication.
Exam Alert
Ad-hoc wireless communication is considered peer-to-peer.
Infrastructure mode is centered around a wireless access point (WAP). A WAP is a centralized wireless device that controls the traffic in the wireless medium. An example of a WLAN setup with a WAP can be seen in Figure 9.2.
Figure 9.2. Infrastructure wireless LAN.
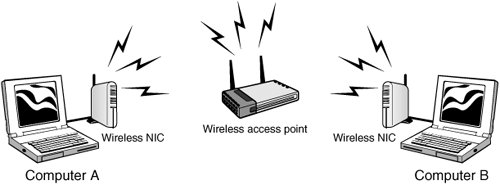
Each device communicates up to the WAP, which then forwards the data to the appropriate computer. For a computer to communicate or use the WLAN, it must be configured to use the same Service Set ID (SSID). The SSID distinguishes one wireless network from another. It can be up to 32 bits and is case sensitive. The SSID can be easily sniffed. Compared to adhoc wireless networks, infrastructure mode networks are more scalable and offer centralized security management.
WLANs present somewhat of a problem to basic Carrier Sense Multiple Access with Collision Detection (CSMA/CD) Ethernet. In a wired network, it's easy for any one of the devices to detect if another device is transmitting. When a WAP is being used, the WAP hears all the wireless devices, but individual wireless devices cannot hear other wireless devices. This is known as the hidden node problem. To get around this problem, Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) is used. The station listens before it sends a packet and if it detects that someone is transmitting, it waits for a random period and tries again. If it listens and discovers that no one is transmitting, it sends a short message known as the ready-to-send (RTS).
Wireless LAN Frequencies and Signaling
Three popular standards are used for WLANs along with a new standard, 802.11n, which is tabled for approval in the 20062007 time frame. The specifications on these standards are shown in Table 9.1.
|
IEEE WLAN Standard |
Over-the-Air Estimates |
Frequencies |
|---|---|---|
|
802.11b |
11Mbps |
2.40002.2835GHz |
|
802.11a |
54Mbps |
5.7255.825GHz |
|
802.11g |
54Mbps |
2.40002.2835GHz |
|
802.11n |
540Mbps |
2.40002.2835GHz |
The 802.11b, 802.11g, and 802.11n systems divide the usable spectrum into 14 overlapping staggered channels whose frequencies are 5MHz apart. The channels available for use in a particular country differ according to the regulations of that country. As an example, in North America 11 channels are supported, whereas most European countries support 13 channels.
Most wireless devices broadcast by using spread-spectrum technology. This method of transmission transmits data over a wide range of radio frequencies. Spread spectrum lessens noise interference and enables data rates to speed up or slow down, depending on the quality of the signal. This technology was pioneered by the military to make eavesdropping difficult and increase the difficulty of signal jamming. Currently two types of spread spectrum technology exist: direct-sequence spread spectrum (DSSS) and frequency-hopping spread spectrum (FHSS):
- Direct-sequence spread spectrum (DSSS) This method of transmission divides the stream of information to be transmitted into small bits. These bits of data are mapped to a pattern of ratios called a spreading code. The higher the spreading code, the more the signal is resistant to interference but the less bandwidth is available. The transmitter and the receiver must be synchronized to the same spreading code.
- Frequency-hopping spread spectrum (FHSS) This method of transmission operates by taking a broad slice of the bandwidth spectrum and dividing it into smaller subchannels of about 1MHz. The transmitter then hops between subchannels, sending out short bursts of data on each subchannel for a short period of time. This is known as the dwell time. For FHSS to work, all communicating devices must know the dwell time and must use the same hopping pattern. Because FHSS uses more subchannels than DHSS, it can support more wireless devices. FHSS devices also typically use less power and are the cheaper of the two types.
Wireless LAN Security
|
Objective:
|
The wireless nature and the use of radio frequency for networking makes securing WLANs more challenging than securing a wired LAN. Originally, the Wired Equivalent Privacy (WEP) protocol was developed to address this issue. It was designed to provide the same privacy that a user would have on a wired network. WEP is based on the RC4 symmetric encryption standard and uses either 64-bit or 128-bit key. However, the keys are not really this many bits because a 24-bit Initialization Vector (IV) is used to provide randomness. So the "real key" is actually 40 or 104 bits long. There are two ways to implement the key. First, the default key method shares a set of up to four default keys with all the wireless access points (WAPs). Second is the key mapping method, which sets up a key-mapping relationship for each wireless station with another individual station. Although slightly more secure, this method is more work. Consequently, most WLANs use a single shared key on all stations, which makes it easier for a hacker to recover the key. Now, let's take a closer look at WEP and discuss the way it operates.
To better understand the WEP process, you need to understand the basics of Boolean logic. Specifically, you need to understand how XORing works. XORing is just a simple binary comparison between two bytes that produce another byte as a result of the XORing process. When the two bits are compared, XORing looks to see if they are different. If they are different, the resulting output is 1. If the two bits are the same, the result is 0. If you want to learn more about Boolean logic, a good place to start is here: http://en.wikipedia.org/wiki/Boolean_algebra. All this talk about WEP might leave you wondering how exactly RC4 and XORing are used to encrypt wireless communication. To better explain those concepts, let's look at the seven steps of encrypting a message:
|
1. |
The transmitting and receiving stations are initialized with the secret key. This secret key must be distributed using an out-of-band mechanism such as email, posting it on a website, or giving it to you on a piece of paper the way many hotels do. |
|
2. |
The transmitting station produces a seed, which is obtained by appending the 40-bit secret key to the 24-bit Initialization Vector (IV), for input into a Pseudo Random Number Generator (PRNG). |
|
3. |
The transmitting station inputs the seed to the WEP PRNG to generate a key stream of random bytes. |
|
4. |
The key stream is XORd with plaintext to obtain the cipher text. |
|
5. |
The transmitting station appends the cipher text to the IV and sets a bit indicates that it is a WEP-encrypted packet. This completes WEP encapsulation, and the results are transmitted as a frame of data. WEP only encrypts the data. The header and trailer are sent in clear text. |
|
6. |
The receiving station checks to see if the encrypted bit of the frame it received is set. If so, the receiving station extracts the IV from the frame and appends the IV with the secret key. |
|
7. |
The receiver generates a key stream that must match the transmitting station's key. This key stream is XORd with the cipher text to obtain the sent plaintext. |
To get a better idea of how WEP functions, consider the following example. Let's assume that our preshared key is hacker. This word would be merged with qrs to create the secret key of qrshacker. This value would be used to encrypt a packet. The next packet would require a new IV. Therefore, it would still use hacker, but this time it would concatenate it with the value mno to create a new secret key of mnohacker. This would continue for each packet of data created. This should help you realize that the changing part of the secret key is the IV, which is what WEP cracking is interested in. A busy access point that sends a constant flow of traffic will actually use up all possible IVs after five or six hours. After a hacker can begin to capture reused keys, WEP can be easily cracked.
Exam Alert
WEP does not encrypt the entire transmission. The header and trailer of the frame are sent in clear text. This means that even when encryption is used, a MAC address can be sniffed.
Now as you can see, cracking WEP is not an easy process. The hacker has to capture 5 to 10 million packets, which would take some time on most networks. This changed in August 2004, when a hacker named KoreK released a new piece of attack code that sped up WEP key recovery by nearly two orders of magnitude. Instead of using the passive approach of collecting millions of packets to crack the WEP key, his concept was to actively inject packets into the network. The idea is to solicit a response from legitimate devices from the WLAN. Even though the hacker can't decipher these packets in an encrypted form, he can guess what they are and use them in a way to provoke additional traffic-generating responses. This makes it possible to crack WEP in less than 10 minutes on many wireless networks.
Exam Alert
The lack of centralized management makes it difficult to change WEP keys with any regularity.
These problems led the wireless industry to speed up the development of the planned replacement of WEP. Wi-Fi Protected Access (WPA) was developed as an interim solution. WPA delivers a level of security way beyond what WEP offers. WPA uses Temporal Key Integrity Protocol (TKIP). TKIP scrambles the keys using a hashing algorithm and adds an integrity-checking feature verifying that the keys haven't been tampered with. WPA improves on WEP by increasing the IV from 24 bits to 48. Rollover also has to be eliminated, which means that key reuse is less likely to occur. WPA also avoids another weakness of WEP by using a different secret key for each packet. Another improvement in WPA is message integrity. WPA addressed a message integrity check (MIC) known as Michael. Michael is designed to detect invalid packets and can even take measures to prevent attacks. In 2004, the IEEE approved the real successor to WEP which was WPA2. It is officially known as 802.11.i. This wireless security standard makes use of the Advanced Encryption Standard (AES). Key sizes of up to 256 bit are now available, which is a vast improvement from the original 40-bit encryption WEP used. It also includes built-in RADIUS support. The common modes and types of WPA and WPA2 are shown in Table 9.2.
|
Mode |
WPA |
WPA2 |
|---|---|---|
|
Enterprise mode |
Authentication: 802.1x EAP |
IEEE Authentication: IEEE 802.1x EAP |
|
Encryption: TKIP/MIC |
Encryption: AES-CCMP |
|
|
Personal mode |
Authentication: PSK |
Authentication: PSK |
|
Encryption: TKIP/MIC |
Encryption: AES-CCMP |
Wireless LAN Threats
|
Objective:
|
Wireless networking opens up a network to threats that you may not ever even consider on a wired network. This section discusses some of the attacks that can be launched against a WLAN. These include eavesdropping, open authentication, spoofing, and denial of service. During a pen test, the wireless network is something that an ethical hacker wants to look at closely. Unlike the wired network, a hacker can launch his attack from the parking lot or even across the street. The entire act of searching for wireless networks has created some unique activities, such as
- Warchalking The act of marking buildings or sidewalks with chalk to show others where it's possible to access an exposed company wireless network.
- Wardriving The act of finding and marking the locations and status of wireless networks, this activity is usually performed by automobile. The wardriver typically uses a Global Positioning System (GPS) device to record the location and a discovery tool such as NetStumbler.
- Warflying Similar to wardriving, except that a plane is used instead of a car. One of the first publicized acts occurred on the San Francisco area.
Eavesdropping
Eavesdropping is one of these basic problems. If the attacker is within range, he can simply intercept radio signals and decode the data being transmitted. Nothing more than a wireless sniffer and the ability to place the wireless NIC into promiscuous mode is required. Remember that promiscuous mode means that the adapter has the capability to capture all packets, not just those addressed to the client. If the hacker uses an antenna, he can be even farther away, which makes these attacks hard to detect and prevent. Besides giving the hacker the ability to gather information about the network and its structure, protocols such as File Transfer Protocol (FTP), Telnet, and Simple Mail Transport Protocol (SMTP) that transmit username and passwords in clear text are highly vulnerable. Anything that is not encrypted is vulnerable to attack. Even if encryption is being used, a hacker eavesdropping on a network is still presented with the cipher text, which can be stored, analyzed, and potentially cracked at a later time. Would you really feel safe knowing that hackers have the NT LanMan (NTLM) password hashes? Programs such as L0phtcrack and John the Ripper can easily crack weak passwords if given the hash. If the hacker is limited in what he can sniff, he can always attempt active sniffing. Active sniffing, as discussed in Chapter 7, "Sniffers, Session Hijacking, and Denial of Service," involves Address Resolution Protocol (ARP) poisoning.
Exam Alert
ARP poisoning allows an attacker to overcome a switch's segmentation and eavesdrop on all local communication.
WEP cracking is another type of eavesdropping attack. Soon after WEP was released, problems were discovered that led to ways in which it can be cracked. Although the deficiencies of WEP were corrected with the WPA protocol, those WAPs still running WEP are vulnerable.
Configured as Open Authentication
Can it get any worse that this? Sure it can. If a wireless network is configured as open systems authentication, any wireless client can connect to the WAP. Wireless equipment can be configured as open systems authentication or shared key authentication. Open systems authentication means that no authentication is used. A large portion of the wireless equipment sold defaults to this setting. If used in this state, hackers are not only free to sniff traffic on the network, but also to connect to it and use it as they see fit. If there is a path to the Internet, the hacker might use the victim's network as the base of attack. Anyone tracing the IP address will be led back to the victim, not the hacker.
Many hotels, business centers, coffee shops, and restaurants provide wireless access with open authentication. In these situations, it is excessively easy for a hacker to gain unauthorized information, resource hijacking, or even introduce backdoors onto other systems. Just think about it, one of the first things most users do is check their email. This means that usernames and passwords are being passed over a totally insecure network.
Exam Alert
The biggest insecurity can be that most wireless equipment comes configured with security features disabled by default. If not changed, open authentication can occur.
Rogue and Unauthorized Access Points
Two primary threats can occur from rogue and unauthorized access points. First, there is the employee's ability to install unmanaged access points. The second threat is access point spoofing. A Gartner Group report found that 20 percent of networks have rogue access points attached. Although this isn't the kind of figure you'll be tested on, it is sobering as it indicates that on average one in five access points are unauthorized. The ease of use of wireless equipment and the lure of freedom is just too much for some employees to resist. The way to prevent and deter rogue access points is by building strong policies that dictate harsh punishments for individuals who are found to have installed rogue access points and by performing periodic site surveys.
Exam Alert
Site surveys are a good tool to determine the number and placement of access points throughout the facility and to locate signals from rogue access points.
Access point spoofing is another real security risk. Access point spoofing occurs when the hacker sets up his own rogue access point near the victim's network or in a public place where the victim might try to connect. If the spoofed access point has the stronger signal, the victim's computer will choose the spoofed access point. This puts the hacker right in the middle of all subsequent transmissions. From this man-in-the-middle, the hacker can attempt to steal user-names and passwords or simply monitor traffic. When performed in an open hot spot, this attack is sometimes referred to as the evil twin attack. An example can be seen in Figure 9.3.
Figure 9.3. Evil twin (man-in-the-middle attack).
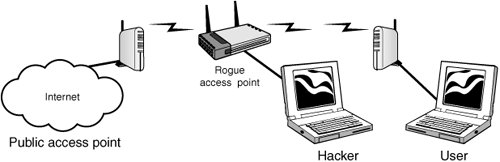
Host routing is also a potential problem for wireless clients. Both Windows and Linux provide IP forwarding capabilities. Therefore if a wireless client is connected to both a wired and wireless network at the same time, this can expose the hosts on the trusted wired network to any hosts that connect via the wireless network. Just by a simple misconfiguration, an authorized client might be connected to the wired network while unknowingly having its wireless adapter enabled and connected to an unknown WLAN. If a hacker is able to compromise the host machine via the open WLAN adapter, he would then be positioned to mount an attack against the hosts on the wired network.
Denial of Service (DoS)
If all else fails, the hacker can always attempt a DoS. For example, these attacks can target a single device, can target the entire wireless network, or can attempt to render wireless equipment useless. Some common types of wireless DoS attacks are discussed here:
- Authentication flood attack This type of DoS attack generates a flood of EAPOL messages requesting 802.1X authentication. As a result, the authentication server cannot respond to the flood of authentication requests and consequently fails at returning successful connections to valid clients.
- Deauthentication flood attack This type of DoS targets an individual client and works by spoofing a de-authentication frame from the WAP to the victim. It is sometimes called the Fatajack attack. The victim's wireless device would attempt to reconnect, so the attack would need to send a stream of de-authentication packets to keep the client out of service.
- Network jamming attack This type of DoS targets the entire wireless network. The attacker simply builds or purchases a transmitter to flood the airwaves in the vicinity of the wireless network. A 1,000 watt jammer 300 feet away from a building can jam 50 to 100 feet into the office area. Where would a hacker get such a device? They are found inside of microwave ovens and known as a magnetron. Normally, a microwave oven doesn't emit radio signals beyond its shielded cabinet. They must be modified to become useful, but little skill is required. This type of attack is as dangerous to people who are near the transmitter as it is to the network itself.
- Equipment destruction attack This type of DoS targets the access point. The hacker uses a high output transmitter with a directional high gain antenna to pulse the access point. High energy RF power will damage electronics in the WAP, resulting in it being permanently out of service. Such high energy RF guns have been demonstrated to work and cost little to build.
Exam Alert
Although denial of service attacks don't give the hacker access to the wireless network, they do attack availability and can bring communication to a standstill.
Wireless Hacking Tools |
Part I: Exam Preparation
The Business Aspects of Penetration Testing
- The Business Aspects of Penetration Testing
- Study Strategies
- Security Fundamentals
- Security Testing
- Hacker and Cracker Descriptions
- Ethical Hackers
- Test PlansKeeping It Legal
- Ethics and Legality
- Summary
- Key Terms
- Apply Your Knowledge
The Technical Foundations of Hacking
- The Technical Foundations of Hacking
- Study Strategies
- The Attackers Process
- The Ethical Hackers Process
- Security and the Stack
- Summary
- Key Terms
- Apply Your Knowledge
Footprinting and Scanning
- Footprinting and Scanning
- Study Strategies
- Determining Assessment Scope
- The Seven-Step Information Gathering Process
- Summary
- Key Terms
- Apply Your Knowledge
Enumeration and System Hacking
- Enumeration and System Hacking
- Study Strategies
- The Architecture of Windows Computers
- Enumeration
- Windows Hacking
- Summary
- Key Terms
- Apply Your Knowledge
Linux and Automated Security Assessment Tools
- Linux and Automated Security Assessment Tools
- Study Strategies
- Linux
- Automated Assessment Tools
- Picking the Right Platform
- Summary
- Key Terms
- Apply Your Knowledge
Trojans and Backdoors
- Trojans and Backdoors
- Study Strategies
- An Overview of TrojansThe History of Trojans
- Covert Communications
- Trojan and Backdoor Countermeasures
- Summary
- Key Terms
- Apply Your Knowledge
Sniffers, Session Hijacking, and Denial of Service
- Sniffers, Session Hijacking, and Denial of Service
- Study Strategies
- Sniffers
- Session Hijacking
- Denial of Service
- Summary
- Key Terms
- Apply Your Knowledge
Web Server Hacking, Web Applications, and Database Attacks
- Web Server Hacking, Web Applications, and Database Attacks
- Study Strategies
- Web Server Hacking
- Web Application Hacking
- Database Overview
- Summary
- Key Terms
- Apply Your Knowledge
Wireless Technologies, Security, and Attacks
- Wireless Technologies, Security, and Attacks
- Study Strategies
- Wireless TechnologiesA Brief History
- Wireless LANs
- Wireless Hacking Tools
- Securing Wireless Networks
- Summary
- Key Terms
- Apply Your Knowledge
IDS, Firewalls, and Honeypots
- IDS, Firewalls, and Honeypots
- Study Strategies
- Intrusion Detection Systems
- Firewalls
- Honeypots
- Summary
- Key Terms
- Apply Your Knowledge
Buffer Overflows, Viruses, and Worms
- Buffer Overflows, Viruses, and Worms
- Study Strategies
- Buffer Overflows
- Viruses and Worms
- Summary
- Key Terms
- Apply Your Knowledge
Cryptographic Attacks and Defenses
- Cryptographic Attacks and Defenses
- Study Strategies
- Functions of Cryptography
- History of Cryptography
- Algorithms
- Hashing
- Digital Signatures
- Steganography
- Digital Certificates
- Public Key Infrastructure
- Protocols, Standards, and Applications
- Encryption Cracking and Tools
- Summary
- Key Terms
- Apply Your Knowledge
Physical Security and Social Engineering
- Physical Security and Social Engineering
- Study Strategies
- Physical Security
- Social Engineering
- Summary
- Key Terms
- Apply Your Knowledge
Part II: Final Review
- Fast Facts
- Ethics and Legality
- Footprinting
- Scanning
- Enumeration
- System Hacking
- Trojans and Backdoors
- Sniffers
- Denial of Service
- Social Engineering
- Session Hijacking
- Hacking Web Servers
- Web Application Vulnerabilities
- Web-Based Password Cracking Techniques
- SQL Injection
- Hacking Wireless Networks
- Virus and Worms
- Physical Security
- Linux Hacking
- Evading Firewalls, IDS, and Honeypots
- Buffer Overflows
- Cryptography
- Penetration Testing
- Certified Ethical Hacker
- Practice Exam Questions
- Answers to Practice Exam Questions
- Glossary
Part III: Appendixes
Appendix A. Using the ExamGear Special Edition Software
- Appendix A. Using the ExamGear Special Edition Software
- Exam Simulation
- Study Tools
- How ExamGear Special Edition Works
- Installing ExamGear Special Edition
- Using ExamGear Special Edition
- Contacting Que Certification
- License
- Software and Documentation
- License Term and Charges
- Title
- Updates
- Limited Warranty and Disclaimer
- Limitation of Liability
- Miscellaneous
- U.S. Government Restricted Rights
EAN: 2147483647
Pages: 247
