Steganography
Steganography is the art of secret writing. With steganography, messages can be hidden in images, sound files, or even the whitespace of a document before it's sent. This type of secret communication has been around for centuries. Books were written on this subject in the fifteenth and sixteenth centuries. Steganography derived from a Greek word that means covered writing. One of the ways it was originally used was to tattoo messages onto someone's shaved head; after the hair had grown out, that individual was sent to the message recipient. While this is certainly a way to hide information in plain sight, it is a far cry from how steganography is used today.
Steganography took a big leap forward with the invention of computers. Today, steganography uses graphics, documents, and even MP3 sound files as carriers. The carrier is the non-secret object that is used to transport the hidden message. Steganographic programs work in one of two ways. They can use the graphic or sound file to hide the message, or the message can be scrambled or encrypted while being inserted into the carrier. This method of encryption could be DES, 3DES, IDEA, or other encryption standards. The dual level of protection vastly increases the security of the hidden object. Even if someone discovers the existence of the hidden message, the encryption method to view the contents must be overcome. With steganography, someone could be looking right at some type of covert message and never even realize it! Next, this Chapter discusses how steganography works, and then it looks at some stegano-graphic tools.
Steganography Operation
Steganogaphy works by hiding information in pictures or bitmaps. Steganography hides information in a bitmap by spreading the data across various bits within the file. Computer-based pictures or bitmaps are composed of many dots. Each one of the dots is called a pixel. Each pixel has its own color. These colors can range between no color (binary 0) to full color (binary 255). Steganography in sound files work in a similar fashion, as sound is also represented by a corresponding binary value. For example, let's say that your Windows startup sound file has the following four bytes of information in it:
|
225 |
38 |
74 |
130 |
|
11100001 |
00100110 |
01001010 |
10000010 |
If you want to hide the decimal value 7 (binary 0111) here, you could simply make the following change:
|
224 |
39 |
75 |
131 |
|
11100000 |
0010011 |
01001011 |
10000011 |
Could you audibly tell the difference? Most likely you could not because the actual sound file has changed just a little. In this example, the least significant bit was used to hide the data. Strong steganographic tools will vary the bit placement used to store the information to increase the difficulty of someone attempting to brute force the algorithm. The actual amount of data that can be hidden within any one carrier depends on the carrier's total size and the size of the hidden data. What does this mean? There is no way to hide a 10MB file in a 256KB bitmap or sound file. The container or carrier is simply too small.
Steganographic Tools
Steganographic tools can be used to hide information in plain sight. Three basic types are discussed in this section. First, there are those tools that hide information in documents in an unseen manner. One such program is Snow Snow is used to conceal messages in ASCII text by appending whitespace to the end of lines. Spaces and tabs are usually not visible in document viewer programs; therefore, the message is effectively hidden from casual observers. If encryption is used, the message cannot be read even if it is detected. If you would like to try the program, it can be downloaded from www.darkside.com.au/snow.
The second type of steganographic program includes those that hide information in a sound file. Two tools that can hide information in sound files include StegonoWav and MP3Stego. One primary worry for the hacker might be that someone becomes suspicious of a large number of sound files being moved when no such activity occurred before. Although recovering the contents of the messages could prove difficult for the security administrator, he could always decompress and recompress the MP3 file, which would destroy the hidden contents.
The third type of steganographic tool discussed hides information in pictures or graphics. Some of these tools include
- S-Tools A steganography tool that hides files in BMP, GIF, and WAV files. To use it, simply open S-Tools and drag pictures and sounds across to it. To hide files, just drag them over open sound/picture windows.
- Image Hide Another steganography tool that hides files in BMPs and GIFs.
- Blindside A steganographic application that allows one to conceal a file or set of files within a standard computer image. Just as with the other software products listed previously, the new image looks like a human eye.
- WbStego This steganographic tool hides any type of file in bitmap images, text files, HTML files, or Adobe PDF files. The file in which you hide the data is not visibly changed. It can be used to exchange sensitive data secretly.
Just as with many of the other tools that have been discussed in this book, the best way to increase your skill set is by using the tools. S-Tools is one of these steganographic tools, and it is available as shareware at http://www.jjtc.com/Security/stegtools.htm. After the program is open, simply drag the graphics file you would like to use onto the S-Tools screen. Then use Explorer to select the text file that you want hide, drag the text file over the open picture file that you selected, and let go. It's really that simple. You now have the option to encrypt the text inside the bitmap, as shown in Figure 12.7. IDEA, DES, and 3DES are some of the encryption methods you can choose.
Figure 12.7. S-Tools encryption method.
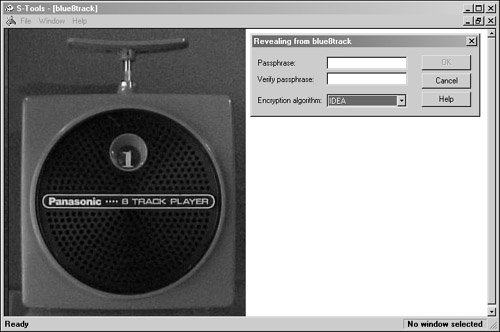
After you choose the encryption method, there will be a short pause while the encryption proceeds. When the hiding process is complete, the steganographically altered image will appear in a second window. An example of this can be seen in Figure 12.8. See if you can tell any difference between the two photos.
Figure 12.8. Original and duplicate graphic with hidden text.

What's also nice about the S-Tools program is that it shows the total amount of data that can be stored within any one image without image degradation. In this particular case, the image can hold a total of 60,952 bytes. If you save the image, you will see that both the original and the one with the hidden message are the same size. Although it has been rumored that terrorists and others groups have used steganography, it's not a mainstream product because a finite amount of data can be stored in any one carrier file. The amount of data hidden is always less than the total size of the carrier. Another drawback to the use of steganography is that the possession or transmission of hundreds of carrier files could in many cases raise suspicion, unless the sender is a photographer or artist.
Digital Watermark
The commercial application of steganography lies mainly in the use of a digital watermark. A digital watermark acts as a type of digital fingerprint and can verify proof of source. It's a way to identify the copyright owner, the creator of the work, authorized consumers, and so on. Steganography is perfectly suited for this purpose, as a digital watermark should be invisible and permanently embedded into digital data for copyright protection. The importance of digital watermarks cannot be understated, as the Internet makes it so easy for someone to steal and reproduce protected assets at an alarming rate. Proprietary information can be copied, recopied, and duplicated with amazing speed. Digital watermarks can be used in cases of intellectual property theft to show proof of ownership. Adobe Photoshop actually includes the ability to add a watermark; its technology is called Digimarc. It is designed to help an artist determine if his art was stolen. Other possible applications would be that of marking music files that are pre-released. This would allow the identification of the individuals who released these onto peer-to-peer networks or spread them to other unauthorized sources.
Digital Certificates |
Part I: Exam Preparation
The Business Aspects of Penetration Testing
- The Business Aspects of Penetration Testing
- Study Strategies
- Security Fundamentals
- Security Testing
- Hacker and Cracker Descriptions
- Ethical Hackers
- Test PlansKeeping It Legal
- Ethics and Legality
- Summary
- Key Terms
- Apply Your Knowledge
The Technical Foundations of Hacking
- The Technical Foundations of Hacking
- Study Strategies
- The Attackers Process
- The Ethical Hackers Process
- Security and the Stack
- Summary
- Key Terms
- Apply Your Knowledge
Footprinting and Scanning
- Footprinting and Scanning
- Study Strategies
- Determining Assessment Scope
- The Seven-Step Information Gathering Process
- Summary
- Key Terms
- Apply Your Knowledge
Enumeration and System Hacking
- Enumeration and System Hacking
- Study Strategies
- The Architecture of Windows Computers
- Enumeration
- Windows Hacking
- Summary
- Key Terms
- Apply Your Knowledge
Linux and Automated Security Assessment Tools
- Linux and Automated Security Assessment Tools
- Study Strategies
- Linux
- Automated Assessment Tools
- Picking the Right Platform
- Summary
- Key Terms
- Apply Your Knowledge
Trojans and Backdoors
- Trojans and Backdoors
- Study Strategies
- An Overview of TrojansThe History of Trojans
- Covert Communications
- Trojan and Backdoor Countermeasures
- Summary
- Key Terms
- Apply Your Knowledge
Sniffers, Session Hijacking, and Denial of Service
- Sniffers, Session Hijacking, and Denial of Service
- Study Strategies
- Sniffers
- Session Hijacking
- Denial of Service
- Summary
- Key Terms
- Apply Your Knowledge
Web Server Hacking, Web Applications, and Database Attacks
- Web Server Hacking, Web Applications, and Database Attacks
- Study Strategies
- Web Server Hacking
- Web Application Hacking
- Database Overview
- Summary
- Key Terms
- Apply Your Knowledge
Wireless Technologies, Security, and Attacks
- Wireless Technologies, Security, and Attacks
- Study Strategies
- Wireless TechnologiesA Brief History
- Wireless LANs
- Wireless Hacking Tools
- Securing Wireless Networks
- Summary
- Key Terms
- Apply Your Knowledge
IDS, Firewalls, and Honeypots
- IDS, Firewalls, and Honeypots
- Study Strategies
- Intrusion Detection Systems
- Firewalls
- Honeypots
- Summary
- Key Terms
- Apply Your Knowledge
Buffer Overflows, Viruses, and Worms
- Buffer Overflows, Viruses, and Worms
- Study Strategies
- Buffer Overflows
- Viruses and Worms
- Summary
- Key Terms
- Apply Your Knowledge
Cryptographic Attacks and Defenses
- Cryptographic Attacks and Defenses
- Study Strategies
- Functions of Cryptography
- History of Cryptography
- Algorithms
- Hashing
- Digital Signatures
- Steganography
- Digital Certificates
- Public Key Infrastructure
- Protocols, Standards, and Applications
- Encryption Cracking and Tools
- Summary
- Key Terms
- Apply Your Knowledge
Physical Security and Social Engineering
- Physical Security and Social Engineering
- Study Strategies
- Physical Security
- Social Engineering
- Summary
- Key Terms
- Apply Your Knowledge
Part II: Final Review
- Fast Facts
- Ethics and Legality
- Footprinting
- Scanning
- Enumeration
- System Hacking
- Trojans and Backdoors
- Sniffers
- Denial of Service
- Social Engineering
- Session Hijacking
- Hacking Web Servers
- Web Application Vulnerabilities
- Web-Based Password Cracking Techniques
- SQL Injection
- Hacking Wireless Networks
- Virus and Worms
- Physical Security
- Linux Hacking
- Evading Firewalls, IDS, and Honeypots
- Buffer Overflows
- Cryptography
- Penetration Testing
- Certified Ethical Hacker
- Practice Exam Questions
- Answers to Practice Exam Questions
- Glossary
Part III: Appendixes
Appendix A. Using the ExamGear Special Edition Software
- Appendix A. Using the ExamGear Special Edition Software
- Exam Simulation
- Study Tools
- How ExamGear Special Edition Works
- Installing ExamGear Special Edition
- Using ExamGear Special Edition
- Contacting Que Certification
- License
- Software and Documentation
- License Term and Charges
- Title
- Updates
- Limited Warranty and Disclaimer
- Limitation of Liability
- Miscellaneous
- U.S. Government Restricted Rights
EAN: 2147483647
Pages: 247
- Operations Security
- Business Continuity Planning and Disaster Recovery Planning
- Legal, Regulations, Compliance, and Investigations
- Appendix D The Information System Security Engineering Professional (ISSEP) Certification
- Appendix E The Information System Security Management Professional (ISSMP) Certification
