Open-Source Security Testing Methodology Manual
| < Day Day Up > |
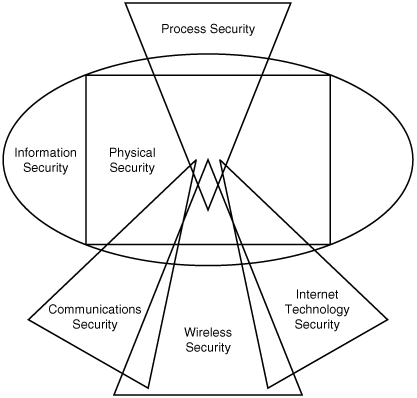
Open-Source Security Testing Methodology ManualAs you know, it is pointless to reinvent the wheel if it has already been made. Peter Herzog, at the Institute for Security and Open Methodologies (http://www.isecom.org), along with 30 contributors from various security organizations, has created the Open-Source Security Testing Methodology Manual (OSSTMM) so that penetration testers do not have to reinvent the wheel when designing a methodology for security auditing. The OSSTMM addresses the following areas of security assessment, as illustrated in Figure 3-2:
Figure 3-2. OSSTMM Security Map©2000 2003 Peter Herzog, ISECOM Note A Spanish version of the OSSTMM is available for free download at http://www.osstmm.org. Each of the areas of security assessment is further broken down into specific modules. For example, the wireless security area (page 71 in the OSSTMM document) is broken down into eleven modules:
Each of these modules is further broken down to detail what a security auditor should test. For example, under Bluetooth testing (page 75), the auditor should do the following: 1. Verify that there is an organizational security policy that addresses the use of wireless technology, including Bluetooth technology. 2. Perform a complete inventory of all Bluetooth wireless devices. 3. Perform brute force attacks against Bluetooth access points to discern the strength of the password. Verify that passwords contain numbers and special characters. Bluetooth access points use case-insensitive passwords, which makes it easier for attackers to conduct a brute force guessing attack due to the smaller space of possible passwords. 4. Verify the actual perimeter of the Bluetooth network. 5. Verify that the Bluetooth devices are set to the lowest power setting to maintain sufficient operation that will keep transmissions within the secure boundaries of the organization. The OSSTMM, although broader than just penetration testing, serves as a good framework to start with. Note Anyone can contribute to the OSSTMM project. If you want to contribute to it, go to http://www.isecom.org/contact.shtml. After you have collected the data, you can begin your assessment. Figure 3-3 illustrates the complete process from the point of signing the contract to the point of writing the report. Figure 3-3. Penetration Testing Life Cycle After you have collated and analyzed all data, it is time to write your report. |
| < Day Day Up > |
EAN: 2147483647
Pages: 209
- Integration Strategies and Tactics for Information Technology Governance
- Linking the IT Balanced Scorecard to the Business Objectives at a Major Canadian Financial Group
- Measuring ROI in E-Commerce Applications: Analysis to Action
- Governing Information Technology Through COBIT
- The Evolution of IT Governance at NB Power