Establishing Good Security Practices
| Security is important for your Tablet PC especially because it's possible for intruders to tap into your Tablet PC wirelessly. If you turn off wireless networking and don't have your network cable connected, you're safe from data thieves as long as your machine is in your possession. Note
If you let the machine out of your sight, however, others could access your files. That's when you want other levels of security. This section will help you establish safe computing practices and help you lock down your computer as much as practical. You can certainly take serious measures to protect your machine, but for most users, these protection schemes can get in the way of getting work done. The protection scheme you choose depends on your ability to accept risk, and the sensitivity of your data. User Accounts and PasswordsThe first thing you need to do to protect your Tablet PC is to establish user accounts for those who will use the machine. (Note that it's possible that user accounts were set up before you received your machine.) Note
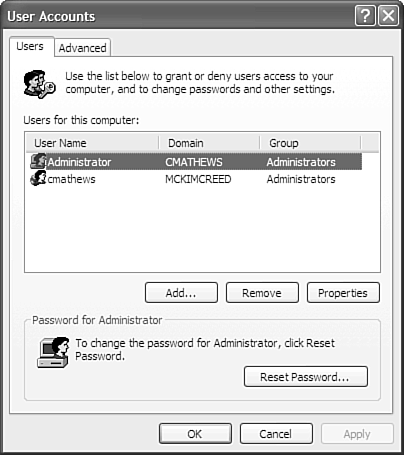
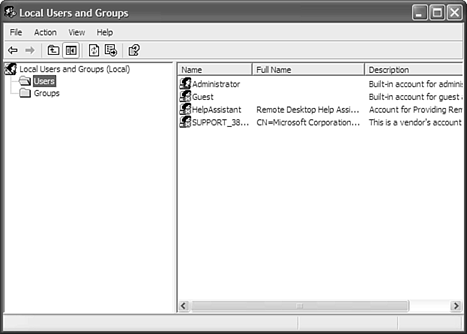
To get to the user account setup, go to the Control Panel, then choose User Accounts. In the User Accounts dialog box that appears, you will see a list of current users, as shown in Figure 11.1. Figure 11.1. The list of user accounts on my machine. In the list, you see Administrator, which is a system account that cannot be changed. You also see my login, CMATHEWS. Notice also that there are two different domains. The CMATHEWS domain is just the local computer; the MCKIMCREED domain is the domain I log on to at work. A domain is a trusted security grouping that recognizes users by username and password. If your computer is not part of a work domain, you will probably want to have just two users, Administrator and your username. The domain will just be the name of your computer. To add a user, simply click the Add button and follow the prompts. If you intend to add multiple users, you may want to establish groups. To do this, tap on the Advanced tab and then tap the Advanced button to open the Local Users and Groups window, as shown in Figure 11.2. This window displays a list of all your named users. Guest is disabled, as denoted by the circled X. Figure 11.2. A more in-depth look at the user accounts on my machine. To boost security, make sure that the Guest user is disabled and that the Administrator user has a unique password (unless your IT department set it up for you, in which case you will want to ask them how your security is configured). To disable the Guest account, double-click the Guest username and check the Disable account check box. Leaving the guest account enabled is a potential security hazard. Caution
Requiring Ctrl+Alt+Delete for Secure LoginsTo configure your Tablet PC to require users to log in securely, again open the User Accounts dialog box (choose User Accounts from the Control Panel), but this time tap the Advanced tab. There, tap the Require users to press Ctrl+Alt+Delete check box; this will require a secure login, which users perform by pressing you guessed it Ctrl+Alt+Delete. Any time people log into your Tablet PC, they will then need to press Ctrl+Alt+Delete to log in. Require Login When Returning from a Power-Saving ModeIn addition to configuring your Tablet PC to require users to log in securely, it's a good idea set up your machine to require a login every time it boots, returns from hibernation and standby, and resumes from a screensaver. This will prevent anyone without the proper credentials from getting into your machine easily. Caution
Establishing good usernames and passwords is important. Making sure that passwords are required is the next step. If you allow your Tablet PC to return from standby or hibernate mode without asking for a password, it can be easy for someone to access your machine. To require a password when returning from standby or hibernation, do the following:
Require Login When Returning from ScreensaverYou also have potential security risks when you walk away from your machine for a while. You can make your screensaver require a login when resuming from the screen saver. If you're away long enough for your screensaver to kick in, it's long enough for someone else to gain access to your machine. Tip
To establish this policy, open the Control Panel and choose Display Properties. Click on the Screensaver tab, and check the On resume, password protect check box. Install and Configure Virus ProtectionVirus protection is an important safety precaution if you think you'll ever connect to the Internet or a network (which is a big reason for getting the Tablet PC in the first place). Basically, you need it. There are numerous virus-protection packages available, including Symantec's Norton Antivirus, McAfee's VirusScan, and packages by Computer Associates and Trend Micro. McAfee and Symantec have the largest installed bases and are always excellent choices. Install the software according to the instructions provided with your package. Usually, accepting the defaults will yield a reasonable protection level. When you first install the application, you will probably be required to scan your hard drive before doing anything else. After that, you can configure your anti-virus product to scan on a regular basis, such as once a week, and also to protect in real-time, checking all files coming into your computer. Caution
If your Tablet PC is company-owned, your IT staff may have already set up virus protection for you. Ask them how often the virus definitions get updated. If it's any less than a month or week, ask if they can make it more frequent. I have my company's virus files updated daily. Use a Firewall to Protect Against Internet AttacksIf you're using your Internet connection for multiple users, you will want to purchase a firewall device. These are inexpensive, and can be purchased in a multipurpose device, such as a wireless broadband router/firewall/switch combination. If you're setting up a network at home to include wireless access to the Internet, I'd encourage you to purchase and configure one of these devices. If you don't have a firewall at work, put this book down and go get one right now. Seriously. Caution
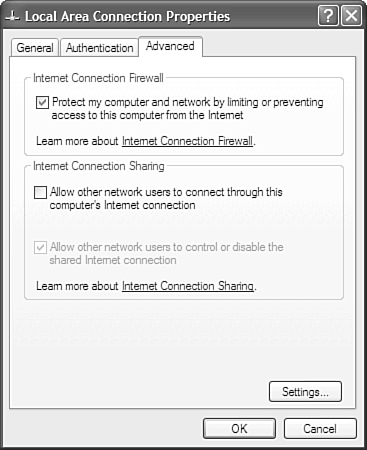
You could purchase any one of probably a hundred or so different firewall products. I have used both the Linksys and D-Link broadband router/firewall/switch combos, and have been pleased with each. The amount of security you need will determine your device requirements. If you plan to create a wireless network, refer to Chapter 10, "Wireless Networking," for more information on what to buy and how it should be configured. Enabling Internet Connection FirewallIf you're only going to have your Tablet PC connected to the Internet (and not multiple machines), you don't have to have the hardware-based firewall, even though I recommend it. Windows XP includes the Internet Connection Firewall (ICF) as an option. Using this, you can protect your machine at a basic level against data thieves and other miscreants. Internet Connection Firewall prevents others from coming through the Internet and getting on your computer. Tip
The Internet Connection Firewall can slow down your system and interfere with other services on your Tablet PC, but it is an option for those who don't want to buy a firewall device. To enable the ICF, do the following:
If you find that enabling ICF interferes with anything you need to do, you can follow the same procedure, but uncheck the check box to disable ICF. For more information on ICF, enter the phrase "Internet Connection Firewall" into Help and Support (Start, Help and Support). The Internet Connection Firewall overview explains what ICF is, and how it works. It also details issues that you may need to be aware of when enabling ICF on your system, such as possible contention with Internet Connection Sharing (ICS) and not enabling it if not connected directly to the Internet. Because this book deals more with the Tablet PC than Windows XP, you may want to find a good Windows XP book for information on items like this. Setting Up File and Folder SecurityFile and folder security allows you to establish even greater control over what files are protected. If you have particularly sensitive files, you will want a firewall, antivirus program, sign-on accounts and passwords, and file-level security. Folder- and file-level security is only available on NTFS-partitioned drives. Many Tablet PCs have FAT32 partitions, while others will have NTFS. NTFS is a more secure and higher-performing partitioning method than FAT32. You can convert from FAT32 to NTFS easily, but you cannot readily go back to FAT32. To convert your C: drive to NTFS, you can do the following:
Caution
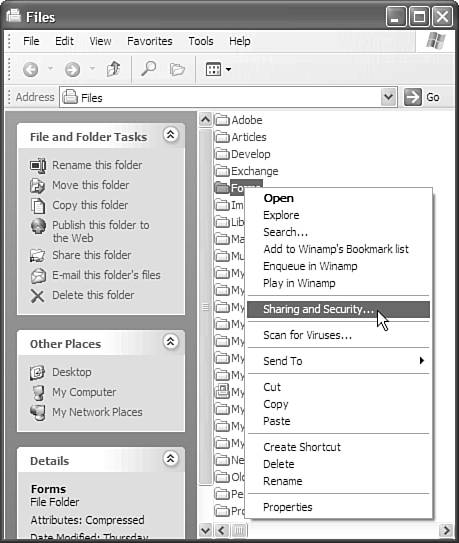
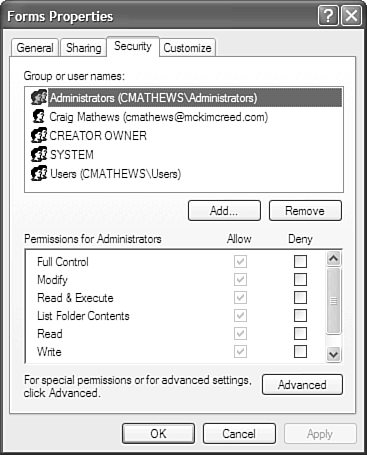
The process may take quite a bit of time, depending on the size of your hard drive and the amount of data you have. To establish file- or folder-level security, drill down in My Computer or Windows Explorer to the folder or file on which you want to establish higher security. Then right-click the folder or file and choose Sharing and Security, as shown in Figure 11.5. Figure 11.5. To enable folder-level security, right-click the folder you want to add security to and choose Sharing and Security. After you do that, you will see the Folder Properties dialog box (where Folder is the name of the folder). Click on the Security tab, and you will see something similar to what is shown in Figure 11.6. Figure 11.6. Reduce the groups and users to the fewest who need access to your files. This is only available on NTFS-partitioned drives. Notice that only a few of my users and groups can access this folder. I could further reduce the number of potential users by eliminating all but my account. This could be problematic, though, if my account was re-created or destroyed for some reason. The main thing to keep in mind here is that if you want your files secure, you need to limit access to only those who need access, and no more. Likely, this will be just you. You (or your network administrator, if you are using your firm's Tablet PC) will need to determine whether you want the administrator to access your folder(s). You probably will, but if you do, make sure that the administrator password is secure. File and folder security can be implemented on everything you have on your machine, but I would recommend you take other precautions before going to this extreme. I basically allow myself and the administrator to have rights to my system, and I have control over both accounts. Of course, I'm also in charge of IT in my company. If you get a message that you cannot remove a user or group because "this object is inheriting permissions from its parent," you can get around this by clicking on the Advanced button on Folder Properties dialog box's Security tab, and then deselecting the first check box. You may want to refer to a more in-depth Windows XP book for more information on file and folder security. Alternatively, you might want to speak with someone in the IT field who can help you with your specific data-protection needs. Disable Folder SharingWhen your computer comes to you, it will probably have drive and folder sharing enabled. If it does, all it takes is one person knowing that he or she can access your hard drive by using the \\computername\c$ access method to thwart your other security measures. The easiest way to remove folder sharing is to do the following:
Caution
Before you performed step 3, did you notice that your C: drive was shared as C$? This is an administrative share that most people don't know about, but that is easily compromised. You can certainly choose to share any folder that you want on your machine, but I'd recommend making it a folder that you're sharing, and not the entire drive. |
EAN: 2147483647
Pages: 172