What is Wi-Fi?
| Wi-Fi stands for Wireless Fidelity, and is a wireless network protocol. Wi-Fi is becoming a prevalent way to connect to networks and the Internet. Wi-Fi usually refers to an 11 Mbps protocol (a protocol is a defined way to communicate electronically) called 802.11b. 11 Mbps is about as fast as 10 Mbps Ethernet, and about one-tenth as fast as 100 Mbps Fast Ethernet. Wireless often seems slower than Ethernet. 802.11b operates at the 2.4 GHz frequency range, which can conflict with other devices such as walkie-talkies and microwave ovens. Other options for wireless networking include 802.11a and 802.11g. See Table 10.1 for the differences between each protocol.
One big problem with 802.11g implementations is that typically they do not in practice reach the same speed as 802.11a due to interference and other issues. Also, 802.11g has been shown to be much slower than 802.11a if you have a mix of 802.11b and 802.11g devices on the same network all accessing a 802.11g access point. However, because of its compatibility with 802.11b, I still expect the 802.11g protocol to win the battle in the near term, or at least until there is an even faster, more secure wireless protocol. Note
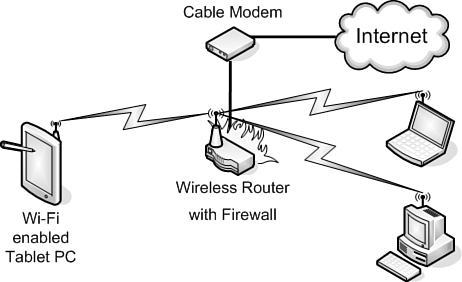
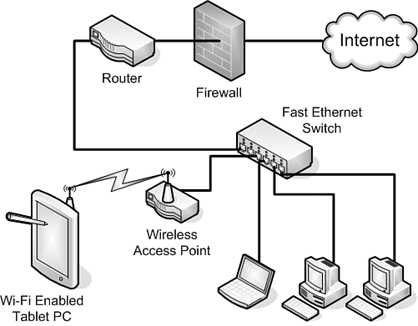
Components of a Basic Wi-Fi NetworkWi-Fi is composed of a router or access point and wireless network adapters for the Tablet PC, other computers, and peripherals that will access the Wi-Fi network. Figure 10.1 shows a diagram of a simple wireless network in a home. Figure 10.1. A simple home wireless network. A company has different needs for protection than home users. The entire office network must be protected from intrusion. For this reason, the router and firewall are usually separate devices in an office deployment because most offices have a different type of connection to the Internet than a cable or DSL link. Notice in Figure 10.2 that the Wi-Fi access point is inside the firewall, and that it is connected directly to the network switch/hub. Figure 10.2. A simple office wireless network. In this scenario, you will want to make sure that you are protected on the wireless side as well as at the Internet connection point. Wi-Fi can inadvertently allow people from outside the company to access resources if proper security precautions are not taken. The last section in this chapter, "Securing Your Wireless Network," will detail ways to tighten security on your wireless connections. For a more in-depth coverage of wireless networking, see Appendix A, "Additional Resources," for books about the subject. Note
|
EAN: 2147483647
Pages: 172