Network Service Discovery
|
| In this step of the assessment, you use host and port scanners to actively examine the network ranges you discovered during the reconnaissance step. This will reveal the existence of servers and services running on those servers. Some of the information you discover during this step you will already have uncovered during the initial reconnaissance. However, it is likely that you will uncover a large population of systems that you were previously unaware of. All the information you collect in this step will feed into the next, where you will probe discovered systems to determine their potential vulnerabilities. System EnumerationThe two main aspects of network service discovery are system enumeration and service discovery. System enumeration combines discovery and analysis techniques to locate systems that can be used as access points into the network. Once you have located these systems, you then move on to service discovery, where you attempt to determine what network services are available on the discovered computer systems. We'll first start by showing you how to perform system enumeration. Network ScannersThe standard method to discover devices on a network is to perform an ICMP scan, which simply issues ICMP echo request messages in hopes of receiving ICMP echo replies (for example, ping). You have a huge number of tools to choose from to perform your scan. SuperScan, available from http://www.foundstone.com/, is a free Windows utility that, in addition to supporting other techniques, can perform ICMP scans. Some of the many ICMP scanners for UNIX systems include fping (http://www.fping.com/) and pinger (http://packetstorm.widexs.nl/groups/rhino9/). Figure 22.4 illustrates hosts and devices that are discovered when performing an ICMP scan using SuperScan. Keep in mind that results of an ICMP scan are not always exhaustive because routers and firewalls often block ICMP traffic, effectively hiding internal systems from ICMP scans. This is why we employ several network-scanning techniquesto determine the presence of network devices and hosts that might be invisible to a particular scanner. Figure 22.4. SuperScan can perform ICMP scans to detect systems that are available on the targeted network.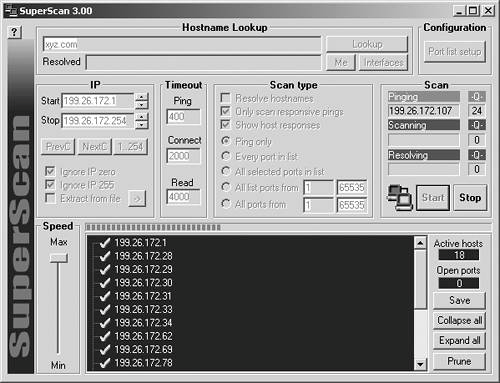 Tip When you're performing the assessment, a good rule of thumb is to start small by scanning one subnet at a time. Performing scans in smaller increments allows for the assessment of a large network to become a more manageable task. Additionally, controlling the rate and breadth of network scans aids in the prevention of network saturation and possible failure. Even if ICMP traffic is blocked at the border of your network, you can still locate remotely accessible hosts by performing scans using TCP or UDP packets. In this case, you would use a network scanner, such as SuperScan or Nmap, to probe all IP addresses in the targeted address range on commonly open ports. Figure 22.5 shows the results of a network scan that SuperScan performed. Instead of issuing ICMP packets, we configured the program to locate all hosts that answer to connections on TCP ports 25 (SMTP), 80 (HTTP), and 21 (FTP). In this case, only two hosts were located, both apparently running web server software. Figure 22.5. SuperScan can locate remotely accessible systems by attempting to connect to commonly used ports.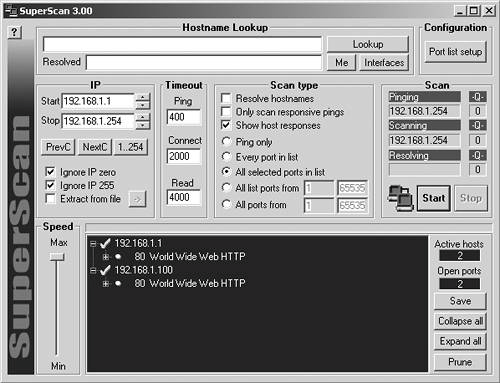 TracerouteIn addition to scanning, you may also want to use traceroute to discover the path your packets are taking to reach the hosts your scans revealed. The following are some ways to use traceroute (or tracert under Windows) to learn about the targeted network:
At this point of the external assessment, you have gone through several stages of learning about the targeted network. You started off with planning, performed initial reconnaissance, and enumerated systems that were accessible from the Internet. You are now ready to focus on the configuration details of the individual hosts you have uncovered so far. Service DiscoveryNow that you have mapped the targeted network, you are ready to probe individual systems in an attempt to determine which operating system they are running, locate ports that can be accessed remotely, determine the service software running on these ports, and access the services to determine additional host details. This prepares you for the next step, in which you probe discovered systems and services for exploitable vulnerabilities. Port scanners can probe individual systems and network ranges to locate open ports associated with commonly used services, potential vulnerabilities, or specific exploits. For example, an attacker can run Nmap to find devices that have TCP port 27374 open, which might indicate that they are infected by the SubSeven Trojan. NmapNmap (http://www.nmap.org/) is one of the most popular and powerful tools for identifying open ports in a system. Nmap can perform different types of scans that help you determine which traffic is allowed to pass through your access control devices. You can use Nmap to perform scans with TCP, UDP, and ICMP packets in an effort to acquire system information. Each Nmap option attempts to connect with the target system in a different way. Nmap is one of the most popular network scanners because of its flexible scanning options and its availability on multiple OS platforms. The following is an example of a SYN scan directed at a remotely accessible server. It shows the Nmap program performing a SYN scan, as specified by the -sS parameter. The O option specifies that Nmap should attempt to guess what type of OS the target system is running. # nmap -sS -O 192.168.254.6 Starting nmap 3.75 ( http://www.insecure.org/nmap/ ) at 2004-12-18 09:56 EST Interesting ports on 192.168.254.6: (The 1661 ports scanned but not shown below are in state: closed) PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn MAC Address: 00:0D:60:F8:FA:62 (IBM) Device type: general purpose Running: Microsoft Windows 2003/.NET|NT/2K/XP OS details: Microsoft Windows Server 2003 or XP SP2 Tip Using Nmap to perform only a SYN scan does not exhaustively determine accessibility of remote systems and services; additional scans, such as FIN, XMAS, and UDP, should be executed as well. This is because different firewalls tend to block different types of discovery activities. By trying more than one scanning method, you can determine how effective your firewall is at blocking these packets. In this example, Nmap not only determined which ports were open on the host, but also was able to guess its operating system, which might help later when assessing the system for vulnerabilities. Knowing open ports on the remote host enables you to determine versions of the services that are listening on those ports. Often, all you have to do is connect to the ports using a tool as commonplace as the Telnet client. The Telnet client can connect to more than the Telnet service. By providing a port number after the host, you can make the Telnet client connect to any TCP port. For instance, telnet 192.168.5.12 21, will make the Telnet client connect to the FTP port on the computer system located at 192.168.5.12. Telnet and Banner RetrievalKnowing which versions of applications are in use on the targeted system can help you locate vulnerabilities that might be exploitable over the network. After you know which TCP ports are open on the targeted hosts, you can try connecting to those ports that look particularly interesting. Some of the services that often announce their version when you simply connect to them using the Telnet client are Telnet (TCP port 23), FTP (TCP port 21), and SSH (TCP port 22). For example, you can often obtain the version of the SSH server running on the target by connecting to its TCP port 22, as follows: # telnet 192.168.5.12 22 SSH-1.99-OpenSSH_2.9 Some services, such as SMTP (TCP port 25) and HTTP (TCP port 80), require you to issue a request after you connect with Telnet before revealing their version. For example, you can determine the version of the remote web server by connecting to port 80 on the server using the telnet command, typing HEAD / HTTP/1.0, and pressing Enter twice: # telnet 192.168.5.12 80 HEAD / HTTP/1.0 HTTP/1.1 200 OK Date: Sat, 02 Mar 2002 00:09:55 GMT Server: Apache/1.3.19 (Unix) Resin/1.2.2 PHP/4.1.2 mod_ssl/2.8.1 OpenSSL/0.9.6 Last-Modified: Thu, 08 Nov 2004 00:08:32 GMT ETag: "9cf48-244-3aa6cd80" Accept-Ranges: bytes Content-Length: 580 Connection: close Content-Type: text/html As you can see, this web server seems to be running Apache version 1.3.19 on a UNIX platform, with several modules that might contain vulnerabilities. Port and vulnerability scanners might be able to automatically obtain versions of certain applications. Nmap has had this ability since version 3.4. You activate it using the sV flag, which stands for version scan. Here is an example that shows that Nmap is able to determine versions of the SSH server and web server on the targeted system: # nmap -sV 192.168.254.2 Starting nmap 3.75 ( http://www.insecure.org/nmap ) at 2004-12-18 10:20 Eastern Standard Time Interesting ports on 192.168.254.2: (The 1659 ports scanned but not shown below are in state: closed) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 3.5p1 (protocol 1.99) 80/tcp open http Apache httpd 2.0.40 ((Red Hat Linux)) 111/tcp open rpcbind 2 (rpc #100000) 6000/tcp open X11 (access denied) MAC Address: 00:0C:29:C2:6F:8F (VMware) Nmap run completed -- 1 IP address (1 host up) scanned in 10.785 seconds You may notice at this point that you are starting to collect a large amount of information about your network. You will need to organize your data collection for it to be any good to you later. One method you may want to use is to build a system matrix that reflects what you know about the targeted systems. Table 22.3 presents an example of one such matrix.
As the amount of information you know about your network grows, the more targeted the next step in the process will be. Network and port scanners bring you closer to the target by locating and analyzing open service ports. A different class of scanners is needed to test these open service ports to detect vulnerabilities. Scanners that are able to obtain detailed information about remotely accessible applications and determine whether they are vulnerable to known exploits are called vulnerability scanners. Vulnerability scanners are used to locate exploitable weaknesses in applications and operating systems, as we discuss in the following section. |
|
EAN: 2147483647
Pages: 230