Reconnaissance
|
| The heart of the reconnaissance stage is to gather publicly available information about the organization without actually probing targeted systems directly. This often includes general business information as well as the organization's IP address ranges and the names and IP addresses of its public services, such as DNS, web, and mail. We also want to gather nontechnical information that might be used in a social-engineering attack. A key starting place is determining what IP address ranges are associated with your organization. You can get this information by querying the ARIN database at http://www.arin.net. Query instructions are available on its website, but a basic query you'll want to include is ">YOURORG*" (for example, ">George Mason University*"). This will return a list of matching resource records from the ARIN database and show the net blocks associated with each. An example of this is shown in Figure 22.1. You will want to compare this information with the IP ranges you gathered during the planning stage to see if any address ranges got left out. If you discover new address ranges that you feel should be included, you will need to modify your rules-of-engagement document to include the new addresses. Figure 22.1. ARIN can be used to locate the IP address ranges associated with a particular organization.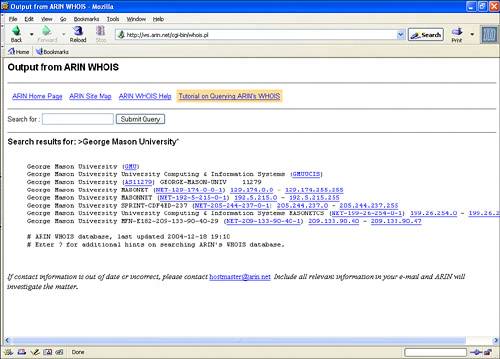 You can also find out useful information by querying the various whois databases for any domain names you have registered. A good site to use for this is Allwhois.com. This site provides a single interface for searching many different registration databases. Whois queries can reveal several useful facts about an Internet site. Whois will give you two main types of information. First, it reveals the DNS names and IP addresses of the name servers. You can use this information in the next step when we attempt to collect DNS information. In addition, whois will often show contact information, including names, addresses, and phone numbers for people within the organization who are responsible in some way for the Internet site. This information can be very useful for social engineering. The following is an example of the type of result you may receive from a whois search: Domain Name: GMU.EDU Registrant: George Mason University 4400 University Drive Fairfax, VA 22030 UNITED STATES Contacts: Administrative Contact: Tracy Holt George Mason University ITU Thompson Hall 4400 University Drive Fairfax, VA 22030 UNITED STATES (703) 993-3356 holt@gmu.edu Technical Contact: Same as above Name Servers: PORTAL-0-8.GMU.EDU 129.174.0.8 THALASSA.GMU.EDU 129.174.1.3 UVAARPA.VIRGINIA.EDU 128.143.2.7 Domain record activated: 14-Oct-1987 Domain record last updated: 05-Mar-2002 Tip For an informative description of social-engineering techniques, take a look at the "Social Engineering Fundamentals" article by Sarah Granger at http://www.securityfocus.com/infocus/1527. Once you've finished your ARIN and whois searches, it is time to start gathering DNS information. Nslookup is a tool included with most operating systems that can be used to determine DNS-related information. Some DNS servers may also allow you to obtain a listing of all registered names and addresses via a technique referred to as a zone transfer. A zone transfer is a complete transfer of all domain information that the DNS server contains. Zone transfers are included in the DNS standard to allow DNS servers within a domain to stay synchronized. Previously, it was common for DNS servers to allow anyone to initiate a zone transfer. Now, most sites have configured their DNS servers to reject anonymous DNS zone transfer requests. It is still worth verifying that your site does not allow zone transfers from every DNS server you maintain. Various websites and utilities are available to make many aspects of the initial reconnaissance phase almost effortless. One such site is http://www.all-nettools.com/toolbox, which provides web-based access to tools, such as whois and nslookup. You can also use utilities such as NetScanTools Pro that run on your workstation and incorporate miscellaneous investigative tools into a single interface (http://www.nwpsw.com/). Figure 22.2 shows the GUI interface of NetScanTools Pro performing a DNS lookup. Figure 22.2. NetScanTools can be used to obtain detailed DNS information about the organization.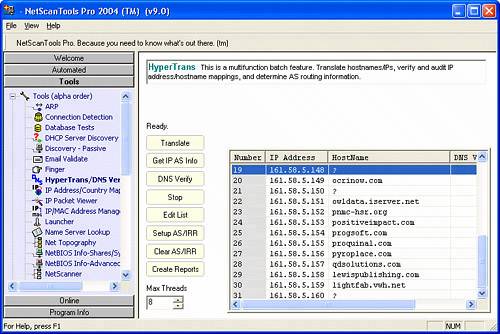 DNS discovery can also be performed using the nslookup command; however, it is much easier to point and click than to issue hundreds of commands via the command line. This example shows how the same investigative steps would look when using nslookup from the command line. The bold text indicates commands, and the rest indicates displayed output. >nslookup Default Server: dns.xyz.com Address: 192.168.200.250 > set type=any > 12.142.174.129.in-addr.arpa. Server: dns.xyz.com Address: 192.168.200.250 Non-authoritative answer: 12.142.174.129.in-addr.arpa name = megalon.ise.gmu.edu 142.174.129.in-addr.arpa nameserver = ite.gmu.edu 142.174.129.in-addr.arpa nameserver = portal.gmu.edu ite.gmu.edu internet address = 129.174.40.84 In addition to standard DNS queries, you'll want to perform reverse lookups. Instead of resolving names to IP addresses, reverse lookups resolve IP addresses to names. Many DNS names are descriptive and can provide valuable information about the purpose of the host, as well as its location, because many organizations use geographic information in their hostnames. For example, what do you think londonfw.example.com could be? Many tools are available that can be used to exhaustively perform a reverse lookup of every IP address in a given range, including NetScanTools Pro. Another great source of information you should include in your initial reconnaissance is your organization's web presence. Organization's often unknowingly publish private information to the Internet, such as usernames and corporate contact information. A tool such as BlackWidow (http://www.softbytelabs.com) can be used to crawl through your websites gathering information, and it provides you with the ability to quickly search through the resultant data. Figure 22.3 shows a sample session of BlackWidow. A couple freeware alternatives are wget (http://www.gnu.org/software/wget/wget.html), a command-line tool included with many Linux distributions, and HTTrack (http://www.httrack.com), an open source tool with GUI that works on both Linux and Windows. Figure 22.3. BlackWidow can be used to download an entire website.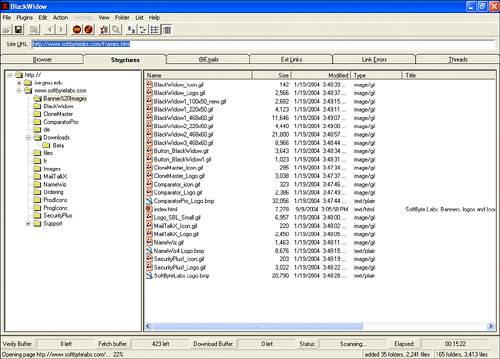 Regardless of which tool you use, you will want to search for sensitive information in the pages you gather. Many types of information may be exposed on a website. For instance, backup copies of the programs that implement the website may be accessible, or you may have accidentally placed sensitive corporate documents within the site. Table 22.2 shows some good search terms you may want to include in your analysis.
You may also want to use terms based on data specific to your organization. For example, if you work for a pharmaceutical company, you may want to search on terms related to any proprietary drug research the company is conducting. More generically, you should search for IT and security-related items, such as network diagrams and firewall policies. You'd be surprised how often this technique reveals breaches in data confidentiality. In addition to searching your websites, you may want to see what web search engines have archived from your sites. Web search engines regularly crawl Internet-accessible websites, including yours. Once they do this, anyone can query the search engine to gather information about you. A whole subcategory of hacking has grown up around search engines. It is often referred to as Google hacking because of the popularity of using Google to perform this type of attack. Two Google search extensions you will find useful (if you're using Google during your assessments) are inurl and link. Inurl allows you to limit Google's search to pages related to your site. For example, to search only on SANS Instituterelated websites, you could specify inurl:sans.org as one of your search terms. Link can be used to see all the web pages that link to a particular page. Normally, some type of relationship exists between organizations that link to each other's sites. Some of these relationships concern business operations. For instance, a company that sells your products may provide a link on its site to yours. Also, it's not uncommon to discover that employees (or ex-employees) have set up personal websites that contain sensitive information about your organization. Because these sites often contain links back to your main web page, Google's link feature allows you to find them easily. Tip The site http://johnny.ihackstuff.com/ contains a large database of Google search terms you can use to discover sensitive information that has leaked out of your websites. This includes searches to find particular web software, locate login portals, and even reveal passwords. You can take the examples provided on the site and combine them with the inurl search syntax to determine whether your site is revealing information it shouldn't. You have now completed the reconnaissance phase of the assessment. At this point, you should have some general knowledge about your organization, its IP address range, and addresses of at least a few publicly accessible servers (such as DNS, web, and mail). Given that these systems are available in some capacity directly from the Internet, they are the most likely systems to be attacked; therefore, you should pay special attention to them. After the initial reconnaissance phase is done, you need to continue by gathering more in-depth information about the targeted network. |
|
EAN: 2147483647
Pages: 230