Vulnerability Discovery
|
| Vulnerability discovery is the assessment step where you start to determine what your findings will be. Sometimes, just the information that your port scanning and banner grabbing gives you is enough to strongly suggest certain vulnerabilities. For instance, if your scanning revealed to you that one of your Windows servers is running Apache 2.0.38, it is likely that the server is susceptible to a directory traversal attack (http://www.securityfocus.com/bid/5434). This can be tricky, though. In the case of this vulnerability, the administrator could have fixed the problem by upgrading the Apache software or by making a change to the Apache configuration file. The first approach would be easily detected because the software upgrade would also cause the banner to change. The second approach, although just as effective at fixing the vulnerability, would not change the banner, leaving us with a false impression of vulnerability. This is the problem that vulnerability scanners are meant to solve. These tools work at the application layer, combining various testing techniques to determine whether a vulnerability exists. Although not perfect, they are a large step beyond what we can accomplish through port scanning alone. Vulnerability scanners often possess network- and port-scanning capabilities similar to the scanners we have discussed so far, but they can also probe audited systems for vulnerabilities. Unlike port scanners, which typically operate at the transport layer and lower, vulnerability scanners have the ability to locate vulnerabilities at the application layer. By using both port and vulnerability scanners, you can achieve a comprehensive awareness of the state of your network's defenses. We begin by looking at Nessus, an open source vulnerability scanner, which we will then compare to several commercially available alternatives. Note Even if you cannot locate any known vulnerabilities in your network, it may still be vulnerable to attack. Unknown vulnerabilities are ones that exist in services you are using but have not been discovered (or revealed) to the computer security community. Because you have no way to know they exist, you will not know to look for them. A proactive approach to this problem is discussed in Chapter 23, "Design Under Fire." However, don't be too concerned. If the computer security community does not know of the vulnerability, the majority of network attackers will not know of it either. It's always better to fix what you can fix first before worrying about harder problems. NessusNessus (http://www.nessus.org/), a high-quality open source vulnerability scanner, offers the ability to scan for accessible service ports, and it can perform security checks to determine whether known exploits can be applied to discovered systems. Most vulnerability scanners rely on a database of scripted tests they perform to attempt to discover vulnerabilities on scanned computer systems. Nessus refers to these scripts as plug-ins. The set of plug-ins available for Nessus is large (currently over 5,800). Plug-ins exist to attempt many classic vulnerability types (for example, remote access) and to assess many types of devices (for example, Cisco, Windows, UNIX). You can also write your own plug-ins either using your favorite scripting language or using the Nessus attack scripting language (NASL), Nessus's internal scripting language. Tip All of Nessus's included plug-ins are written in NASL and are available for your review. You can learn a lot about how Nessus operates by examining these scripts. This can be especially useful to learn the limitations of the scripts. If you have a particular finding that continually shows up in your environment, but you have verified that it is unimportant (for example, a false positive), you can look at the script that is reporting the vulnerability to see if it can be improved for your site to produce better results! While you are performing the vulnerability discovery phase of the assessment, you might decide to audit your systems in stages, according to the function they perform. For example, consider first focusing on your high-profile devices, such as your firewalls. You would then configure Nessus to test for only commonly exploited firewall vulnerabilities. You might then focus special attention on your web servers because of their high visibility and accessibility. Whatever the case, you simply have to select the Nessus plug-in family you require and specify which systems to scan. Nessus plug-ins are grouped into categories, such as backdoors, small services, Microsoft Windows, and CGI abuses. Tip Limiting the tests that a vulnerability scanner uses will dramatically speed up the time it takes the scanner to run. This can be very important if you plan to scan frequently or if you have a large network to examine. A good practice is to occasionally run comprehensive scans while running targeted scans much more frequently. Depending on your environment, daily scans may not be too frequent. To make this work, you will need to spend time deciding what tests to include in your frequent scan. A good place to start building your list is the SANS Top 20 Vulnerabilities (www.sans.org/top20/). After performing a vulnerability scan, Nessus compiles a summary report, illustrated in Figure 22.6, which helps to focus your attention on security weaknesses that require your immediate attention. In this example, Nessus was able to enumerate various user accounts while assessing a Windows file server. Figure 22.6. A Nessus assessment report summarizes findings of the vulnerability scanin this case, of a Windows system.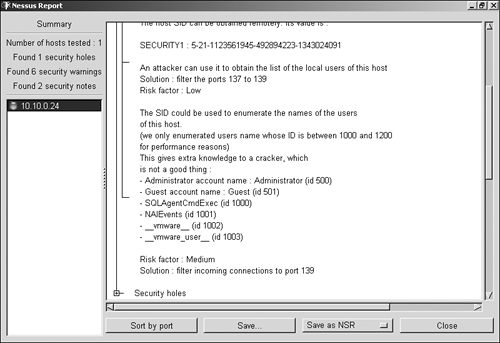 Note Although Nessus is an open source tool, Tenable, the company maintaining Nessus, has recently decided to start selling the plug-ins it produces. Plug-ins created by the open source community will remain free, and Tenable does currently allow free (though delayed) access to its private plug-ins for noncommercial use. ISS Internet ScannerISS Internet Scanner (http://www.iss.net/) is another popular vulnerability assessment tool, which rivals the thoroughness of Nessus and has the advantages and the disadvantages of being a commercial product. ISS Internet Scanner performs many of the same functions as Nessus, including port scanning, service verification, and software fingerprinting. ISS Internet Scanner offers tailored sessions depending on the OS, the role of the system, and the level of thoroughness you desire. For example, if your plan is to assess a UNIX system that is running Apache, you might select the UNIX web session with the desired level of thoroughness. The higher the level, the more vulnerability checks will be performed. ISS Internet Scanner also produces high-quality, flexible reports that can be tailored to executives, management, or technicians. Figure 22.7 shows a vulnerability detail screen from ISS Internet Scanner. As you review the vulnerability report, you have a comprehensible description of the vulnerability as well as a path to remedy the problem. In this illustration, you can see that a high-risk vulnerability in the Microsoft SQL server service has been found. The description of the "MDAC OpenRowSet buffer overflow vulnerability" shows what impact the vulnerability would have on the systemin this case, allowing an attacker to gain complete control over the SQL server and possibly issue operating system commands. This information will be very useful to you later as you try to prioritize the vulnerabilities in your report. ISS also provides remediation information. In this example, you are directed to Microsoft Security Bulletin MS02-040 to understand how to resolve the vulnerability. Figure 22.7. ISS provides detailed information about each discovered vulnerability.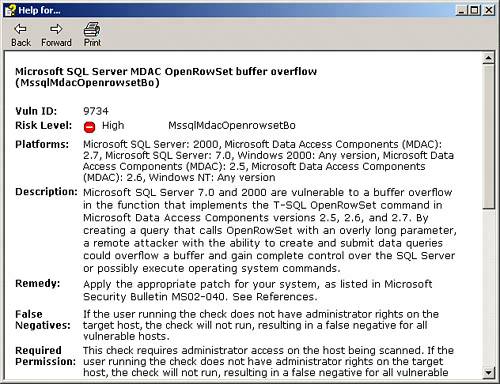 ISS Internet Scanner provides an extensive vulnerability database. In addition, it offers an easy-to-use update feature, guaranteeing that the most current data is available. When a new vulnerability is discovered or when new malicious code becomes publicly available, ISS's X-Force team quickly updates its vulnerability database to allow customers to scan for these items. It is important to note that all the vulnerability-scanning product vendors (including Nessus) claim to provide rapid updates to their database, and, in fact, this is true. It is also true that each tool has some vulnerabilities that it uniquely scans for. For this reason, it is not a bad idea to include more than one vulnerability scanner in your toolbox. RetinaRetina is a commercial scanner produced by eEye Security (http://www.eeye.com/) that competes with ISS Internet Scanner. Retina provides a clean Windows-based interface, as illustrated in Figure 22.8. Retina offers a single interface that incorporates a vulnerability scanner, an Internet browser, a system miner module (which simulates hacking stimulus), and a tracer utility (which offers traceroute-like functionality). Retina offers a quality solution because of its user friendliness, technical robustness, ability to automatically correct some vulnerabilities, as well as detailed explanations for resolving discovered issues. Figure 22.8. In this example, Retina discovers several critical vulnerabilities, including specific problems with the web server running on the system.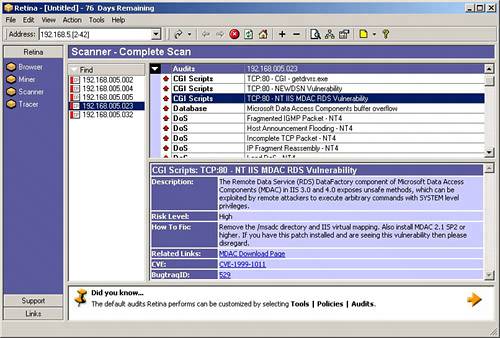 Some scanners are better at probing specific operating systems or applications than others. LANguard, for example, is a powerful scanner for probing systems regardless of their OS, but it is particularly effective for obtaining detailed information about Windows hosts. LANguardGFI LANguard Network Security Scanner (http://www.gfi.com/lannetscan) provides robust functionality for scanning networks and individual hosts. This tool performs especially well when assessing Windows-based systems. Among other techniques, LANguard can utilize Windows null session connections to execute information-gathering and enumerating processes. LANguard also comes in handy when assessing any device that accepts Simple Network Management Protocol (SNMP) connections. If you are able to guess the target's SNMP community string, which is just like a password, you might be able to access extensive amounts of information regarding this device. In Figure 22.9, LANguard discovers enough information to plan an attack against this Windows XP system. Figure 22.9. In this example, LANguard enumerates sensitive information from a Windows XP system.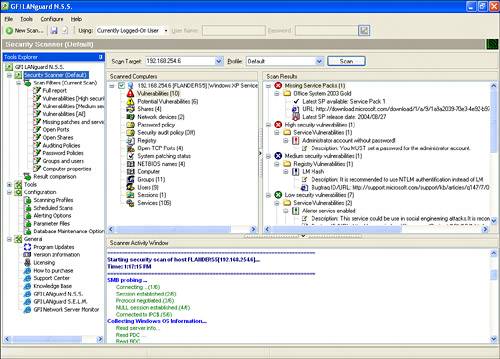 All four vulnerability scanners we've discussed offer many similar options and functionality. Let's summarize how they relate to each other:
You have now completed several steps in your external assessment, starting with planning and continuing to enumerate systems, services, and vulnerabilities. By using a variety of network and vulnerability scanners, you can gain an understanding of the possible weaknesses in your security perimeter. You can learn which service ports can be accessed and exploited from the outside world, and you can discover configuration errors that might result in the network's defenses operating differently from what you originally expected. You have used these network and vulnerability scanners to gather information about your organization, and your system matrix should be fully populated with an assortment of information about your external devices. The next step of the assessment is to further research what vulnerabilities are likely to affect your systems that are publicly accessible. Vulnerability ResearchOne of the problems with automated vulnerability assessment tools is they often report vulnerabilities that do not actually exist. These bogus findings are called false positives. You will need to perform some additional research to determine which vulnerabilities are real and which are fake. As a security analyst, you can research vulnerabilities in effort to determine whether they are real as well as the level of risk associated with them. You will also need to determine the best ways of mitigating each of them. An excellent source of information on vulnerabilities and their resolutions are your software vendors' websites, along with vulnerability announcement mailing lists, such as Bugtraq. You can conduct additional research by checking security-oriented websites such as the following:
These sites provide much more detail about particular vulnerabilities than is typically provided by a vulnerability-scanning tool. By carefully analyzing the information from the vulnerability announcement, combined with examination of the system the vulnerability was reported on, you may be able to eliminate the vulnerability from consideration. This can be somewhat laborious, but well worth the effort if it allows your administrators to concentrate on what's important instead of wasting time responding to false information. At this point in the assessment, you have determined what public services you are allowing out to the Internet and whether these services have potentially exploitable vulnerabilities. You still have work to do, though. Your perimeter devices may be allowing more packets to flow through them than required. In addition, other backdoor access to your network may be possible using either modems, wireless devices, or VPN connections. In the next couple steps, you will examine these additional access methods to ensure they are as secure as possible. |
|
EAN: 2147483647
Pages: 230