Configuring an IKE VPN in Traditional Mode
Here we will create a VPN from ExternalFW to our branch office firewall, BranchFW. The two firewalls are managed by the same management station. Be sure to define network objects for the networks that will be participating in your VPN domain. We will use LAN and BranchNet (10.0.0.0/24) for these networks. In this example, we use Simplified mode to configure the VPNs.
Defining Objects
For any site-to-site VPN, you need to create and properly configure certain network objects, including both gateways and the networks or group objects representing your VPN domains.
Local Gateway
Under the VPN tab of ExternalFW s Properties window, select Traditional mode configuration . The Traditional mode IKE properties dialog box comes up (see Figure 10.2). Select any and all of the encryption and data integrity methods you want your gateway to support, and check Pre-Shared Secret under Support authentication methods (you would check Public Key Signatures if you were using certificates). You will not be able to edit this secret until you define your remote gateway s encryption properties.
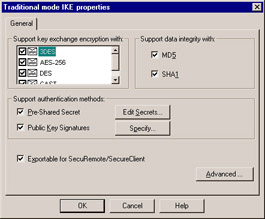
Figure 10.2: The IKE Properties Dialog Box
Next, open the Topology tab of the Check Point Gateway Properties window (see Figure 10.3). This is where you will define the VPN domain for your local gateway. Under VPN Domain , select Manually Defined , and choose your local network (LAN) from the drop-down list. Selecting Manually Defined also allows you to restrict the networks that are accessible via a VPN in the event that you do not want your entire network to be available through the VPN. If you have your topology configured correctly, you can instead choose All IP Addresses behind Gateway based on Topology information . This option summarizes all the networks behind interfaces defined as internal and dynamically creates the VPN domain for you.
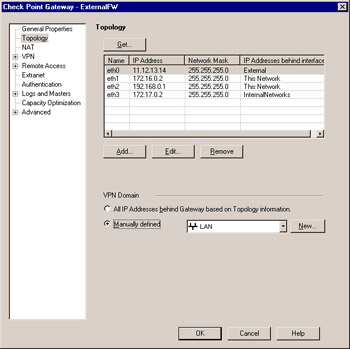
Figure 10.3: VPN Domain Configuration
Remote Gateway
Configuration of the remote gateway is a nearly identical process ”you just need to make sure that you support at least one of the same methods of encryption and data integrity methods as you did on the local gateway. When you check Pre-Shared Secret this time, you can click Edit Secrets , where you should see your peer, BranchFW, in the Shared Secrets List window (see Figure 10.4). You can edit the shared secret by highlighting the peer gateway in the list and clicking Edit . Enter the agreed-on shared secret in the Enter secret text field, and click Set to define it. Don t forget to define your VPN domain under the Topology tab, by opening the Topology tab of the Check Point Gateway Properties window (refer back to Figure 10.3). You can see very quickly that defining a secret for each and every gateway could get very cumbersome in a large deployment. This is solved by Simplified-mode VPNs, discussed later in this chapter. Under VPN Domain , select Manually Defined , and choose your remote network (BranchNet) from the drop-down list.
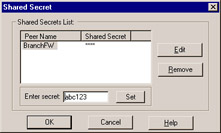
Figure 10.4: Shared Secret Configuration
Adding VPN Rules
You will want to modify your Rule Base so that traffic between LAN and BranchNet is encrypted. You do this by adding two rules to your Rule Base (see Figure 10.5).
One rule specifies the following:
-
Source LAN
-
Destination BranchNet
-
Service Any
-
Action Encrypt
-
Track Log
The other specifies the following:
-
Source BranchNet
-
Destination LAN
-
Service Any
-
Action Encrypt
-
Track Log
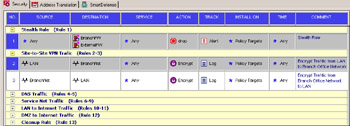
Figure 10.5: IKE Encryption Rules
Note that we do not have a rule to allow the IKE traffic to talk from one firewall to the other. This is because it is part of the Global Properties. A rule to allow IKE between the two gateways is necessary only if you have Accept VPN-1 & FireWall-1 control connections unchecked in your security policy s Global Properties window (see Figure 10.5). This is checked by default, so in most cases you won t need a rule to be manually defined.
If you double-click the Encrypt action in either encrypt rule, you will open the Encryption Properties dialog box, from which you select IKE and click Edit , which pops up another box (see Figure 10.6).
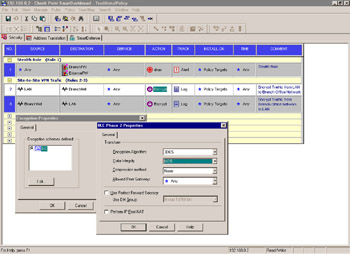
Figure 10.6: IKE Properties Dialog Box
There are many options here. Go through the options one at a time:
-
Encryption Algorithm Choose an encryption algorithm from the list. Strong encryption (e.g., Triple-DES or AES) is available, and recommended, with IKE.
-
Data Integrity Choose the hash method used to provide authentication. SHA1 is available here, in addition to MD5.
-
Compression Method Normally, only Deflate is available here. This specifies the method used to compress IP datagrams. Select None if you do not want the added CPU overhead. This is not often supported by other third-party VPN devices.
-
Allowed Peer Gateway Specifies exactly which gateways with which this one is prepared to establish a VPN. Defaults to Any , meaning that you will allow VPN traffic from or to any gateway if the packet s source or destination IP address is in the other gateway s VPN domain. If this policy is to be installed on both firewalls, we would create a group with both firewalls in it. This is because each rule would be used for encrypting on one end and decrypting on the other.
-
Use Perfect Forward Secrecy (PFS) PFS adds another measure of security to key exchanges, with some additional overhead.
-
Use DH Group This enables you to select the Diffie-Hellman group you would like to use for encryption. Selecting a longer group means better key security but, again, more overhead.
-
Perform IP Pool NAT Allows the use of a predefined pool of IP addresses that are assigned to incoming VPN connections. This is typically used to prevent or fix asymmetric routing conditions in which inbound and outbound VPN traffic follow different routes.
-
You may also need to add a rule to the NAT Rule Base to disable NAT between these networks if you are using NAT for your network objects.
Now that the rules have been created, push the policy and test the VPN.