Planning and Implementing Wireless Security
|
EXAM 70-293 OBJECTIVE 5, 5.4, 5.5, 6, 6.3
Wireless networking is a new technology that has become more widely used since the Institute of Electrical and Electronics Engineers (IEEE) 802.11 specifications have been implemented. These include the following specifications:
-
802.11b, the original wireless networking standard
-
802.11a, the newer wireless standard that provides faster transfer speeds but a shorter distance range
-
802.11g, the newest wireless standard that provides higher speeds like 802.11a but greater distances like 802.11b
-
802.1x, the wireless security standard
The IEEE 802.11 standard provides for all the necessary definitions and constructs for wireless networks. Everything from the physical transmission specifications to the authentication negotiation is defined by the standard. Wireless traffic, like its wired counterpart, consists of frames transmitted from one station to another. The primary feature that sets wireless networks apart from wired networks is that at least one end of the communication pair is either a wireless client or a wireless access point.
Connecting to a wireless network is often transparent to users, and from their perspective is apparently no different from connecting to a copper-based or fiber-based Ethernet network, with the exception that no wires are involved. With Windows XP, Microsoft introduced automatic configuration and seamless roaming from one wireless network to another through its Wireless Zero Configuration service.
The obvious and primary difference between wired and wireless networks is that wireless networks use a special type of electric current, commonly known as radio frequency (RF), which is created by applying alternating current (AC) to an antenna to produce an electromagnetic (EM) field. The resulting RF field is used by devices for broadcast and reception. In the case of wireless networks, the medium for communications is the EM field, the region of space that is influenced by the EM radiation (unlike audio waves, radio waves do not require a medium such as air or water to propagate).
The 802.11 standard provides for two modes for wireless clients to communicate: ad hoc and infrastructure. The ad hoc mode is geared for a network of stations within communication range of each other. Ad hoc networks are created spontaneously between the network participants. In infrastructure mode, wireless access points (WAPs) provide for a more permanent structure for the network.
To distinguish different wireless networks from one another, the 802.11 standard defines the service set identifier (SSID). The SSID can be considered the identity element that “glues” various components of a wireless local area network (LAN) together. Traffic from wireless clients that use one SSID can be distinguished from other wireless traffic using a different SSID. Using the SSID, an AP can determine which traffic is meant for it and which is meant for other wireless networks.
There are a number of different mechanisms for providing security for wireless networks. These include WEP, Remote Authentication Dial In Services (RADIUS) authentication, and the 802.1x standard.
Because of the nature of the 802.11 wireless LANs, the IEEE working group implemented a mechanism to protect the privacy of the individual transmissions. The intent was to mirror the privacy found on the wired LAN (WLAN), and the mechanism became known as WEP. Because WEP uses a cryptographic security countermeasure for the fulfillment of its stated goal of privacy, it has the added benefit of becoming an authentication mechanism. This benefit is realized through a shared-key authentication that allows the encryption and decryption of the wireless transmissions. Up to four keys can be defined on an AP or a client, and they can be rotated to add complexity for a higher security standard in the WLAN policy.
WEP was never intended to be the absolute authority in wireless security. The IEEE 802.11 standard states that WEP provides for protection from “casual eavesdropping.” Instead, the driving force behind WEP was privacy. In cases that require a high degree of security, other mechanisms should be used such as RADIUS authentication, access control, password protection, and virtual private networks (VPNs).
WEP provides for several implementations: no encryption, 40-bit encryption, and 128-bit encryption. Clearly, no encryption means no privacy. When WEP is set to no encryption, transmissions are sent in the clear, and they can be viewed by any wireless sniffing application that has access to the RF signal propagated in the WLAN (unless some other encryption mechanism, such as IPSec, is being used). In the case of the 40- and 128-bit varieties (just as with password length), the greater the number of characters (bits), the stronger the encryption. The initial configuration of the AP will include the setup of the shared key. This shared key can be in the form of either alphanumeric or hexadecimal strings, and must be matched on the client. WEP uses the RC4 encryption algorithm, a stream cipher developed by Ron Rivest (the R in RSA).
The Windows Server 2003 family, including Windows Server 2003 Standard Edition, Enterprise Edition, and Datacenter Edition (but excluding Web Edition), comes with the Internet Authentication Service (IAS), which acts as a centralized connection service for wireless security, VPN, and remote-access connections. IAS uses RADIUS to perform centralized user authentication for wireless clients. IAS can be implemented to provide for wireless authentication using the Extensible Authentication Protocol (EAP) for better wireless security. The current IEEE 802.11b standard is severely limited because it is available only for the current open and shared-key authentication scheme, which is nonextensible. To address the weaknesses in these authentication mechanisms, several vendors (including Cisco and Microsoft) adopted the IEEE 802.1x authentication mechanism for wireless networks. The IEEE 802.1x standard was created for the purpose of providing a security framework for port-based access control that resides in the upper layers of the protocol stack. The most common method for port-based access control is to enable new authentication and key-management methods without changing current network devices.
The 802.1x standards specify the use of EAP over wireless. 802.1x and EAP provide for a mutual authentication capability. This will make the clients and the authentication servers mutually authenticating endpoints and will assist in the mitigation of attacks from man-in-the-middle types of devices.
With the addition of the 802.1x standard, clients are identified by usernames, not by the Media Access Control (MAC) addresses of the devices. This design not only enhances security, but it also streamlines the process for authentication, authorization, and accountability for the network. 802.1x was designed so that it could support extended forms of authentication, using password methods (such as one-time passwords, or GSS_API mechanisms such as Kerberos) and non-password methods (such as biometrics, Internet Key Exchange, and smart cards).
Understanding Wireless Networking
Wireless networks are becoming more and common these days. If you have the right type of adapter card for your laptop, you can sit in a coffee shop and drink your espresso while you check your e-mail. Many universities, airports, and commercial establishments (such as the aforementioned coffee shops) have adopted wireless technologies.
You need to make certain that the equipment you purchase for this technology meets the standards set by one or more of these organizations:
-
Institute of Electrical and Electronics Engineers (IEEE)
-
Internet Engineering Task Force (IETF)
-
Wireless Ethernet Compatibility Alliance (WECA)
-
International Telecommunication Union (ITU)
This will help to ensure that your equipment is compatible with that of the network to which you are connecting.
Wireless Network Types
There are a number of different categories of wireless networks, based on the distance data can be transmitted. Three common types are shown in Table 11.3.
| Network Name | Description | Standard |
|---|---|---|
| Wireless personal area network (WPAN) aka Bluetooth 1.0 and Bluetooth. | Used for devices such as PDAs, cell phones, and laptops. For extremely short distances, it can also use infrared to connect. | 802.15 |
| Wireless local area network (WLAN) | Used to connect devices that are in either a corporate or campus environment. | 802.11, 802.11b, 802.11a, and 802.11g |
| Wireless wide area network (WWAN) aka second-generation or 2G system | Used to provide wireless connections over remote public and private networks. These connections can go between cities and countries via antenna sites or satellite systems. | Not yet available |
| Wireless metropolitan area network (WMAN) | Used to allow for wireless connections between metropolitan areas, such as libraries, without the use of copper or fiber lines. These can also be used as a backup to wired networks. | 802.16 |
| Exam Warning | 802.1x and 802.11x are not the same thing. Do not get these two confused. 802.11x is a wireless standard, and 802.1x is an authentication standard. 802.1x handles authentication using EAP. |
EAP Authentication
When EAP authentication is used, there are two types of roles that a LAN port plays during network access on a wireless network: authenticator or supplicant. The EAP supplicant (in this case, the wireless client) communicates with the WAP over an “uncontrolled port.” The WAP sends an EAP-Request/Identity packet to the supplicant as well as a RADIUS-Access-Request packet to the RADIUS access server. The supplicant then responds with an Identity packet, and the RADIUS server sends a challenge based on the Identity packets sent from the supplicant. The supplicant provides its credentials in the EAP-Response packet that the AP forwards to the RADIUS server. If the response is valid and the credentials are validated, the RADIUS server sends a RADIUS-Access-Accept packet to the WAP, which then allows the supplicant to communicate over a “controlled” port. This is communicated by the WAP to the supplicant in the EAP-Success packet.
| Note | The supplicant is usually the client software, and the authenticator is usually the wireless access point. |
The first data path, the uncontrolled port, allows data exchange between the authenticator and a computing device on the LAN, regardless of the authentication state of that device. This is the path that EAP over LAN (EAPOL) messages will take. EAPOL will encapsulate the EAP messages so that wireless and Ethernet LANs can transport the data securely. The second data path, the controlled port, allows data exchange between an authenticated LAN user and the authenticator. This is the path that all other network traffic will take after the computing device is authenticated. Usually, a RADIUS server is in place to authenticate the supplicant’s credentials. However, the 802.1x specification does not require a RADIUS server.
The procedure is as follows:
-
The wireless supplicant receives a challenge from the wireless authenticator.
-
The supplicant forwards its identity to the authenticator.
-
The authenticator sends the supplicant’s identification to the RADIUS server.
-
The RADIUS server requests the credential of the supplicant.
-
The uncontrolled port on the authenticator processes the requests that are sent between the supplicant and the RADIUS server, because the supplicant’s credentials have not been verified yet.
-
RADIUS receives the supplicant’s credentials and then verifies the information.
-
If the verification is successful, the RADIUS server sends the authentication key to the supplicant.
Figure 11.1 shows the process between LAN port roles.
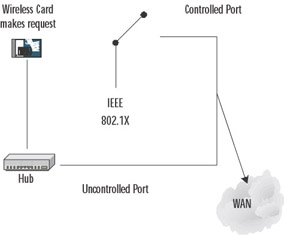
Figure 11.1: Process between LAN Port Roles
| Exam Warning | Understand the differences between the authenticator and the supplicant. Know the function that each of these roles play on a wireless network. |
How Wireless Networking Works
Windows Server 2003 makes it relatively simple to set up and use wireless networking. The operating system has a built-in automatic wireless network configuration so that, with the proper equipment, users can roam from building to building without changing network settings. There are a number of wireless networking technologies in use today, such as the following:
-
WLAN Also known as WI-FI, RF technology that includes 802.11b, which operates in the 2.4GHz range. 802.11a and 802.11g technologies operate at 5 GHz. These differ in terms of data transfer speed and range. Normal range for 802.11b is about 100 to 300 meters, but with a high-gain directional antenna, this can be extended up to several miles.
-
IrDA Uses infrared (IR) signals to transmit data for IrDA 1.1. Normal distance is 3 to 6 meters, although some IR technologies have a maximum distance of 1.5 miles. Because IR signals are used to transmit data, distance limits for long-range IR depend on weather conditions (such as humidity). Additionally, IR is a line-of-sight technology that requires a clear path between the transmitter and receiver.
-
Bluetooth Uses short-range radio waves to transmit data used mainly in PDAs and has a maximum distance range of up to 10 meters.
-
HomeRF Also known as home radio frequency, works up to only about 150 feet.
Authentication for Wireless Networks
There are two authentication methods in the 802.11 standard: open authentication and shared-key authentication. Open authentication is more precisely described as device-oriented authentication and can be considered as a null authentication—all requests are granted. Without WEP, open authentication leaves the WLAN wide open to any client who knows the SSID. With WEP enabled, the WEP secret key becomes the indirect authenticator.
| Note | Open authentication can also require the use of a WEP key. Do not assume that just open authentication is used and that a WEP key does not need to be set. |
Shared-key authentication is a four-step process that begins when the AP receives the validated request for association. After the AP receives the request, a series of management frames are transmitted between the stations to produce the authentication. This includes the use of the cryptographic mechanisms employed by WEP as a validation. The four steps in the process are as follows:
-
The requester (the client) sends a request for association.
-
The authenticator (the AP) receives the request and responds by producing a random challenge text and transmitting it back to the requester.
-
The requester receives the transmission, encrypts the challenge with the secret key, and transmits the encrypted challenge back to the authenticator.
-
The authenticator decrypts the challenge text and compares the values against the original. If they match, the requester is authenticated. On the other hand, if the requester does not have the shared key, the cipher stream cannot be reproduced. At this point, the plaintext cannot be discovered, and theoretically, the transmission is secured.
One of the greatest weaknesses in shared-key authentication is that it provides an attacker with enough information to try to crack the WEP secret key. The challenge, which is sent from authenticator to requester, is sent in the clear. The requesting client then transmits the same challenge, encrypted using the WEP secret key, back to the authenticator. An attacker who captures both of these packets now has two pieces to a three-piece puzzle: the cleartext challenge and the encrypted ciphertext of that challenge. The algorithm is also known—it’s RC4. All that is missing is the secret key.
To determine the key, the attacker simply tries a brute-force search of the potential key space using a dictionary attack. At each step, the attacker tries to decrypt the encrypted challenge with a dictionary word as the secret key. The result is then compared against the authenticator’s challenge. If the two match, the secret key has been determined. In cryptography, this attack is termed a known-plaintext attack and is the primary reason why shared-key authentication is actually considered slightly weaker than open authentication.
You can use the Wireless Monitor console to determine if the wireless network to which you are connecting has multiple APs. To access the Wireless Monitor console, add the Wireless Monitor snap-in to a custom Microsoft Management Console (MMC).
| Note | When using 802.1x for enhanced security, authentication is available only to Windows XP Service Pack 1 clients and Windows Server 2003 systems. |
Exercise 11.01: Setting UP A Windows XP Client for Wireless Networking
Installing and configuring wireless networking on a Windows XP client is simple. Make sure you have an 802.11b wireless network interface card (NIC) installed. After the wireless NIC has been installed, the Automatic Wireless Wizard Configuration window appears. Windows XP will automatically search the network for a WAP. If a WAP is found, it will attempt to make a connection.
To manually configure the wireless network connection on the Windows XP machine, use these instructions:
-
Select Start | Control Panel | Network Connections.
-
Right-click the Wireless Connection and click Properties.
-
Select the Wireless Networks tab.
-
Look in the Available Networks box and choose a WAP to add under the Preferred networks option.
-
In the Wireless Network Properties dialog box, enter the name of the WAP under the Network Name (SSID) box and place check marks in the appropriate boxes that apply to your network settings.
-
Click the OK button. Wireless network access should now be available to you from your Windows XP machine.
| Test Day Tip | Understand how open system and shared key work as authentication subtypes. Know the weaknesses and strengths of each, as well as how they are configured on a domain controller and client machine. |
Defining a Subtype on a Domain Controller
You can configure the subtype you wish to use on a domain controller by configuring Group Policy. To configure the subtype in Group Policy, follow these steps:
-
Select Start | All Programs | Administrative Tools | Active Directory Users and Computers.
-
Find the domain for which you wish to configure the subtype, right-click the domain node, and choose Properties.
-
Select the Group Policy tab.
-
In the GPO Editor, expand Computer Configuration, and then expand Windows Settings.
-
Select the Wireless Network IEEE 802.11 Policies node.
-
Double-click the policy in the right-console pane.
-
On the Preferred Networks tab, click Add to add a new wireless network.
-
Double-click the name of the new wireless network and choose the Network Properties tab.
-
Type in a name for the network. You can choose to enter a description if you wish. You can also select the Network Authentication (Shared Mode) box under Wireless network key (WEP). If you leave this blank, open-system authentication will be used instead.
-
10. To allow the key to be provided automatically for client machines, check the The key is provided automatically box.
Note To ensure that 802.1x will be used for wireless access control, click the IEEE 802.1x tab and check the Enable network access control using IEEE 802.1x check box.
Defining a Subtype on a Client Computer
Next, you can enter the subtype on a client-computer. To do this, perform the following steps:
-
Open Network Connections. Right-click Wireless Network Connection.
-
Click Properties and click Add on the Wireless Networks tab to add the wireless network connection.
-
On the Association tab, for Network name (SSID) service set identifier, enter a unique name. Configure the setting for the use of a network key for data encryption if needed. Next, choose the Data encryption WEP enabled option if it is not already enabled.
-
To specify that a network key be used for authentication to the wireless network, select the Network Authentication (Shared mode) check box.
-
If the network key is automatically provided for dynamically, leave the Network Key option blank. If the network key is not automatically provided, type the key in this field, and then type it again in the Confirm network key field.
-
Click the Authentication tab to specify that 802.1x authentication is being used for the wireless network connection.
Authentication Protocols
Wireless clients and servers can use different types of authentication protocols. Authentication is the method used to verify a user’s identity when the user is trying to access network resources. Windows Server 2003 offers several types of authentication protocols that allow users to use the single sign-on method to access the network.
EAP
EAP is used by 802.1x to take care of authentication. EAP handles conversations between wireless clients and servers. In order for the conversation to work properly, both the client and server must use the same authentication method. EAP is an IEEE standard method for authentication.
EAP-TLS
The strongest authentication method is EAP-Transport Layer Security (EAP-TLS), which is used in certificate-based wireless networks. If you are using smart cards or certificates for client authentication, this is the only protocol that supports those types of authentication. EAP-TLS is the strongest method of authentication, because authentication is mutual between the client and server machine. Also, EAP-TLS is not dependent on the user account password, and the client does not need to intervene when using the authentication method.
EAP-MS-CHAPv2
EAP-Microsoft Challenge Handshake Authentication Protocol version 2 (EAP-MS-CHAPv2) can be implemented when you do not wish to use certificates to authenticate your wireless users. Instead, it uses passwords to authenticate wireless clients. This type of authentication can be installed only on RADIUS servers. After the authentication, users can be allowed to change their passwords. EAP- MS-CHAPv2 is a mutual authentication method that supports password-based user or computer authentication and is available only with PEAP.
PEAP
Protected Extensible Authentication Protocol (PEAP) is a new addition to the EAP extensions. PEAP works by creating an encrypted channel from the wireless client to the authenticator of the wireless session. To create the encrypted channel, PEAP uses TLS. Because TLS creates a secure channel between the client and authenticator, it protects against attacks such as denial of service (DoS). PEAP does not support the use of VPN clients or remote-access clients, because it does not have an encryption method; rather, it allows other authentication protocols to use its TLS channel for much improved security.
To configure PEAP, use the following steps:
-
Select Start | All Programs | Administrative Tools | Internet Authentication Services.
-
Click Remote Access Policies.
-
Open the policy you wish to configure by double-clicking the policy.
-
Click Edit Profile and choose the Authentication tab.
-
In the Authentication tab, select EAP methods.
-
From the Select EAP providers option, click the Add button and select the Protected EAP (PEAP) option.
-
Click the OK button.
-
Select OK.
-
Click Apply, and then click OK.
Exam Warning Understand all of the authentication protocols that are available and remember which protocols work best for scenario-based use.
Using IAS with Wireless
IAS can be used to authenticate wireless connections. Before you begin to implement IAS with your wireless network, you need to plan the deployment carefully. Use the following guidelines as you step through the IAS and wireless configuration process to optimize your setup:
-
Before you start to configure IAS with wireless networking, make sure that all of the equipment being used meets the IEEE specifications. If you do not have hardware that meets these requirements, your deployment might not work properly.
-
Determine whether or not you will be using certificates for authentication. If you will be using certificates, install the certificates on the IAS server and client computers.
-
Install IAS on the server.
-
To install IAS, follow these steps:
-
Select Start | Control Panel | Add/Remove Windows Components.
-
Select Networking Services, and then select Detail.
-
Scroll down to the Internet Authentication Service option and put a check mark in the box. Click OK.
-
To open IAS after it has been installed follow these steps:
-
Open IAS by selecting Start | Programs | Internet Authentication Services.
-
To add RADIUS clients, open the Internet Authentication Service console.
-
Select the Add Radius Client option
-
Choose the New Radius Client option.
-
Enter the Friendly Name of the RADIUS client.
-
Enter the IP address of the client that can be verified by selecting the Verify button.
-
When the information has been entered, click the Next button and choose the Client-Vendor attribute of the RADIUS client.
-
Enter the Shared Secret password and enter it again under the Confirm Shared Secret.
-
If you want to require the Message Authenticator attribute in the request, click the Request must contain the Message Authenticator Attribute box.
-
Click Finish to complete the process.
Wireless Security Issues
There are many threats to networks today. With the advent of wireless networking, the risks have grown. This is especially true if you do not secure the wireless network. Hackers can download and run tools such as NetStumbler, AirSnort, and WEPCrack to locate and access your network without any type of advanced skills. Even if no one with malevolent intent is within range of your wireless network, it is not uncommon for persons with wireless equipment to accidentally access networks they are not authorized to access.
The following are some additional wireless security issues:
-
Rogue WLANs Someone inside your organization can purchase the inexpensive equipment and a wireless LAN card and install a wireless network, connected to your wired network, for their personal use.
-
Spoofing An outside user can send harmful files or viruses to internal users by pretending to be an insider.
-
Drive-by and freeloading Many hackers, who call themselves “war drivers” go out with wireless-equipped laptops and high-gain Yagi antennas, looking for open wireless networks in an attempt to gain free access to Internet bandwidth or access to network data.
-
Eavesdropping This is when a person uses a protocol analyzer (sniffer) to capture unprotected network traffic and open the packets to read the data inside.
-
DoS attacks Attackers can flood your network with unauthorized traffic and bring it to a halt.
Because many businesses do not understand the security and encryption methods involved with a wireless network rollout, these security measures are not implemented. Use the proper encryption and security methods described in this chapter if you implement wireless technologies in your organization.
| Note | AirSnort is used to capture WEP keys. It is sometimes called an auditing tool, but it can also be used to sniff out data packets on WEP. AirSnort works by capturing “interesting packets” with weak keys. If you are using 128-bit encryption, WEP cards can generate roughly 16 million keys, and of those some 9000 are weak. Windows operating system users should be aware that AirSnort runs only on Linux boxes. It is assumed that many passwords can be guessed after about 2000 or so interesting packets. |
Default Settings
Some manufacturers ship wireless network devices with default settings that are well known in the industry, so any malicious user who has a bit of knowledge (experience with the particular device model or the ability to do a little Internet research) already has a head start on the information needed to break into your network.
The default settings that you should be especially concerned with (and should immediately change when you set up your wireless network) include the following:
-
Administrative password
-
SSID
-
SSID broadcasting
-
WEP settings
Administrative Password
When setting up WAPs, the first thing you should do is change the password on the device. Many devices come preset with the Administrator password set to something like admin. Do not leave these devices in their default state. Anyone who knows that you have this hardware could easily change your WAP configuration with this information.
As with any administrative-level password, you should set a strong password on the WAP administrator account. Most WAP vendors provide Web-based administration for performing configuration tasks such as changing the password.
SSID
The SSID acts like a network name for your wireless access device. It has a 32-character identifier attached to the header of data packets that are sent over the WLAN. When this information is sent from the mobile device to the WAP, it acts like a password, in that devices that cannot provide correct SSID information to the WAP will not gain access to the network.
However, the SSID does not provide wireless security for a couple of reasons. First, the SSID is sent over the network in plaintext and is not encrypted. This means that an outsider can use sniffer software to capture the packets being sent over the network and obtain the SSID from them. Additionally, by default, most broadcast their SSIDs, bringing us to the next section.
SSID Broadcasting
SSID broadcasting makes it easy for wireless clients to find the WAP. You don’t even need to know the SSID of the network in order to configure your client to connect; if the WAP broadcasts its SSID, your client computer will automatically intercept it and provide it in the list of wireless networks that are available for you to connect to.
WEP Settings
Another issue to be aware of is that most WAPs do not have WEP enabled by default. Although WEP has some weaknesses (which we’ll discuss in the next section) and is considered by many to provide weak security, it does provide some security and thus should be enabled as a best practice.
Remember that when you enable WEP on the AP, you also must set the client to use it. On a Windows XP client, follow these steps:
-
Double-click your wireless connection icon in the system tray or in Control Panel and select Network Connections to open the Connection Status dialog box.
-
Click Properties.
-
In the Properties box, click the Wireless Networks tab.
-
Under Available networks, select the SSID of the network you want to configure.
-
Click the Configure button.
-
Under the section labeled Wireless network key (WEP), check the check box that says Data encryption (WEP enabled).
-
If the key is provided automatically, check the check box that says The key is provided for me automatically.
-
If the key is not provided automatically, enter the key in the field labeled Network key.
-
Select the Key format (ASCII characters or hexadecimal digits) and the Key length (40 bits for a 5-character key; 104 bits for a 13-character key).
WEP Weaknesses
One factor that makes WEP vulnerable is the lack of a defined key-management process. As discussed previously, WEP uses the RC4 encryption algorithm. This is a symmetric (secret key) algorithm, which means the same key is used both for encrypting and for decrypting the data that travels between the WAP and the wireless client. Thus, all clients must share this same key. This is obviously a weak system because the key must be disseminated so widely, and users must manually enter the key into their wireless configuration.
If someone steals, or even gets temporary access to, one of the organization’s wireless clients, he or she can easily discover the shared key. Many organizations don’t update the keys frequently. Manually rekeying every wireless device can take a lot of time and effort. If the WAP provides the key automatically, this makes changing the key easier.
The second problem with WEP is weak encryption. WEP can use either a 40-bit or 104-bit key. A 40-bit key is fairly easy to break. One would assume that the 104-bit key would be significantly more secure. However, it’s not quite that simple. The problem is the 24-bit initialization vector (IV) that is appended to the WEP key (this creates a 64-bit or 128-bit encryption key that is used to encrypt the data and its checksum). Regardless of the key length, the IV is still only 24 bits. This short IV ensures that the same key stream will be reused. If attackers capture multiple packets that use the same key stream, they can use analysis software to break the encryption.
Attackers can sniff the network and capture packets to determine the IV. By performing an XOR operation on two captured packets, the key can be extrapolated. A hacker needs no special talents to break the WEP key—software such as WEPCrack can do it.
Making Wireless More Secure
Wireless security experts recommend that highly sensitive data should never be sent over a wireless network. If it must be, you should use higher level security mechanisms rather than rely on WEP. If your security requirements are low, you can make WEP more secure by implementing measures such as broadcast key rotation. There are new key-management schemes that use “dynamic WEP.” Instead of a static base key, they provide an updated base key at frequent intervals. Unfortunately, these systems are proprietary and do not really offer a high level of protection. Even with updates every half hour or less, it generally takes only a few hours for a skillful hacker to capture enough packets to analyze and use that information to breach the network.
Another possible solution is hardware that supports the Advanced Encryption Standard (AES). In addition, organizations are investigating the use of IPSec to secure wireless communications. It is possible to incorporate IPSec VPNs into WAPs for high security, but there are some issues with firewalls that do not allow IPSec traffic through. There are also compatibility problems using IPSec with some implementations of network Address translation (NAT), although NAT traversal is a new technology that makes it possible for IPSec and NAT to work together.
A new IEEE subcommittee is working on the WEP problems, under the standard 802.11i. One of their proposed solutions is called the Temporal Key Integrity Protocol (TKIP). This combines a 128-bit “temporal” key with the MAC address of the wireless client and adds an IV. After 10,000 packets, the temporal key changes. Another new technology that uses this TKIP process, WiFi Protected Access (WPA), has been developed by a cooperative effort of the WiFi Alliance and the IEEE. It uses a stronger IV (48 bits), so that the number of possible keys generated is much greater. WPA also uses per-packet key mixing and a hierarchical key structure that can prevent attacks such as those that use AirSnort. A second version of WPA, WPAv2, is expected out in 2004 and will use the Counter with Cipher Block Chaining Message Authentication Code (CCMP) protocol, which is based on AES.
If you do rely on WEP as your primary security for your WLAN, it is important to change the key often. You can also combine other protective mechanisms, such as MAC filtering, with WEP. MAC filtering allows you to specify only particular client MAC addresses that can connect to your WAP. This is set up on the WAP, and the procedure differs depending on the manufacturer. Be aware, though, that knowledgeable hackers can capture packets sent by legitimate wireless clients, discover their MAC addresses, and then spoof the address. So like WEP, MAC filtering offers only a small measure of security.Centralized authentication (using RADIUS/IAS with EAP/PEAP) is Microsoft’s most important solution to overcoming wireless security vulnerabilities.
| Test Day Tip | As a network administrator, you need understand the weaknesses of the wireless network and why WEP is not the best protocol for security. |
|
EAN: 2147483647
Pages: 173