802.11 Networks
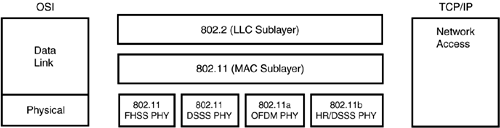
| As you learned in Hour 3, "The Network Access Layer," the details of the physical network reside at the Network Access layer of the TCP/IP protocol stack. The easiest way to imagine a wireless TCP/IP network is simply as an ordinary network with a wireless architecture at the Network Access layer. The popular IEEE 802.11 specifications provide a model for wireless networking at the Network Access layer. The 802.11 protocol stack is shown in Figure 22.1. The wireless components at the Network Access layers are equivalent to the other network architectures you learned about in previous hours (refer to Figure 2.4). In fact, the 802.11 standard is often called wireless Ethernet because of its similarity and compatibility with the IEEE 802.3 Ethernet standard. Figure 22.1. The 802.11 protocols reside at the TCP/IP Network Access layer.
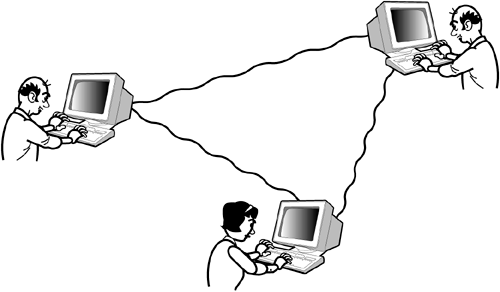
In Figure 22.1, note that the 802.11 specification occupies the MAC sublayer of the OSI reference model. (The MAC sublayer is part of the OSI Data Link layer. Recall from Hour 2 that the OSI Data Link and Physical layers correspond to the TCP/IP Network Access layer. The various options for the Physical layer represent different wireless broadcast formats, including Frequency Hopping Spread Spectrum (FHSS), Direct Sequence Spread Spectrum (DSSS), Orthogonal Frequency Division Multiplexing (OFDM), and High Rate Direct Sequence Multiplexing (HR/DSSS). One quality that distinguishes wireless networks from their wired counterparts is that the nodes are mobile. In other words, the network must be capable of responding to changes in the locations of the participating devices. As you learned in earlier hours, the entire delivery system for TCP/IP networks is built around the assumption that each device is in some fixed location. Indeed, if a computer is moved to a different network segment, it must be configured with a different address or it won't even work. By contrast, devices on a wireless network move about constantly. And, although many of the conventions of Ethernet are preserved in this environment, the situation is certainly more complicated and calls for some new and different strategies. By the Way 802.11 is actually the collective name for a series of standards. The original (1997) 802.11 standard provided transmission speeds of up to 2Mbps in the 2.4GHz frequency range. The 802.11a standard offers speeds of up to 54Mbps in the 5GHz range. The 802.11b standard provides transmissions at 5.5Mbps and 11Mbps in the 2.4GHz range. Independent and Infrastructure NetworksThe simplest form of wireless network consists of two or more devices with wireless network cards communicating with each other directly (see Figure 22.2). This type of network, which is known as an Independent Basic Service Set (Independent BSS, or IBSS), is often adequate for very small collections of computers in a compact space. A classic example of an Independent BSS is a laptop computer that networks temporarily with a home PC when the owner returns from a road trip and transfers files through a wireless connection. Independent BSS networks sometimes occur spontaneously at workshops or sales meetings when participants around a table link through a wireless network to share information. The Independent BSS network is somewhat limited, because it depends on the proximity of the participating computers, provides no infrastructure for managing connections, and offers no means of linking with bigger networks such as the local LAN or the Internet. Figure 22.2. An Independent Basic Service Set.
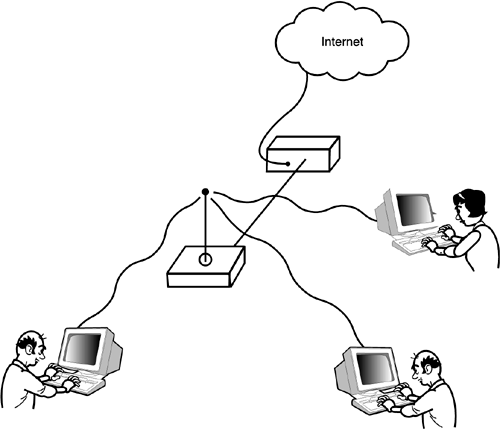
Another form of wireless network, called an Infrastructure Basic Service Set (Infrastructure BSS) is more common on corporate networks and other institutional settings. An Infrastructure BSS depends on a fixed device called an access point to facilitate communication among the wireless devices (see Figure 22.3). An access point communicates with the wireless network through wireless broadcasts and is wired to an ordinary Ethernet network through a conventional connection. Wireless devices communicate through the access point. If a wireless device wants to communicate with another wireless devices in the same zone, it sends a frame to the access point and lets the access point deliver the message to its destination. For communication to or from the conventional network, the access point acts as a bridge. (Refer to Hour 9, "Network Hardware," for more on network bridges.) The access point forwards any frames addressed to the devices on the conventional network and keeps all frames addressed to the wireless network on the wireless side. Figure 22.3. An Infrastructure BSS contains one or more access points.
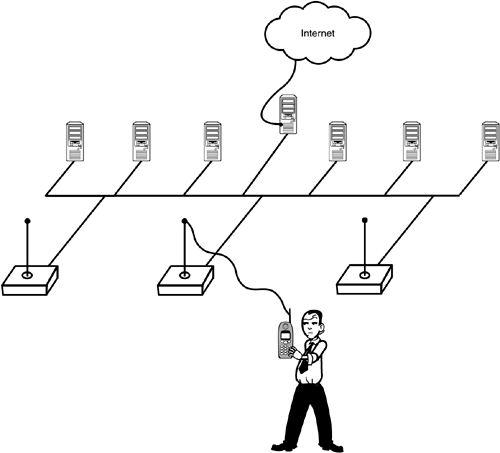
The network shown in Figure 22.3 might appear only marginally more efficient (if at all) than the network shown in Figure 22.2. The benefits of an Infrastructure BSS are more apparent if you consider a larger area served by a collection of access points connected by conventional Ethernet (see Figure 22.4). Figure 22.4. An Infrastructure BSS with multiple access points.
802.11 was devised to address situations like the network depicted in Figure 22.4. The idea is for the roving device to remain connected as it travels anywhere within the area served by the network. The first thing to notice is that, if the device is to receive any network transmissions, the network must know which access point to use to reach the device. This concern is, of course, compounded by the fact that the device is possibly moving, and the appropriate access point might change without warning. Another thing to notice is that the classic concepts of a source address and destination address are not always sufficient for delivering data on a wireless network. In fact, the 802.11 frame makes provision for four addresses:
The 802.11 frame format is shown in Figure 22.5. Some important fields are as follows:
Figure 22.5. 802.11 frame format.
Note that, because 802.11 is a Network Access layer protocol set (equivalent to the OSI Data Link and Physical layers), the addresses used in 802.11 frames are the 48-bit physical addresses you learned about in Hour 3, not IP addresses. As the device moves across the mobile network, it registers itself with the nearest available access point. (Technically, it registers itself with the access point that has the strongest signal and least interference.) This registration process is known as association. When the device roams closer to another access point, it reassociates with the new access point. This association process lets the network determine which access point to use to reach each device. By the Way To ensure the compatibility of 802.11 devices, a group called the Wireless Ethernet Compatibility Alliance (WECA) provides a certification program for wireless products. To earn Wi-Fi (Wireless Fidelity) certification, a product must be tested for interoperability with other wireless devices. To learn more about WECA and Wi-Fi, visit http://www.wi-fi.org. 802.11 SecurityAs you can probably guess, an unprotected wireless network is extremely insecure. To eavesdrop on a conventional network, you must at least be somehow connected to the transmission medium. A wireless network, on the other hand, is vulnerable from anywhere within broadcast distance. Not only can an intruder listen in, an enterprising attacker can simply show up with a wireless device and start participating in the network if the network has no protections to prevent such activities. To address these concerns, IEEE developed an optional security protocol standard to accompany 802.11. The Wired Equivalent Privacy (WEP) standard is designed to provide a level of privacy approximately equivalent to the privacy provided by a conventional wired network. The goal of WEP is to address the following concerns:
WEP handles the confidentiality and integrity goals through encryption using the RC4 algorithm. The sending device generates an Integrity Check Value (ICV). The ICV is a value that results from a standard calculation based on the contents of the frame. The ICV is then encrypted using the RC4 algorithm and transmitted to the receiver. The receiving device decrypts the frame and calculates the ICV. If the calculated ICV value matches the value transmitted with the frame, the frame has not been altered. WEP provides for two forms of authentication:
WEP, unfortunately, has met with objections from security experts. Most experts now regard WEP as ineffective. Some of the objections to WEP are actually objections to the implementation of the RC4 encryption algorithm. WEP theoretically uses a 64-bit key, but 24 bits of the key are used for initialization. Only 40 bits of the key are used as a shared secret. This 40-bit secret is too short, according to the experts, and WEP is therefore insufficient for effective protection. Experts also point to problems with the key management system and with the 24-bit initialization vector used to begin the encryption. An update to WEP was proposed in 2001. Among other things, this WEP2 standard increases the initialization vector to 128 bits and adds Kerberos authentication to organize the use and distribution of secret keys. (See Hour 20 for more on Kerberos.) However, many experts believe WEP2 doesn't solve all the problems of WEP. Several other protocols, such as Extensible Authentication Protocol (EAP) are now under consideration for wireless networks. By the Way The experts, of course, think of security as an ideal and focus on situations where a high level of secrecy is essential. In more casual situations, such as a home network, it is easy to imagine that WEP would be better than no security at all. It is highly probable that WEP could keep your equally casual neighbors from reading your email or discovering what Web sites you're visiting. |
EAN: 2147483647
Pages: 259