Hack 67. Upgrade Your Wireless Router


Run a Linux distribution or other custom code on many models of wireless routers.
The release of the Linksys WRT54G wireless router back in 2003 was kind of a watershed moment for wireless hackers and Linux hackers alike. It was quickly determined that the WRT54G was running a Linux kernel. Source code for the unit was demanded (and eventually released), hacks were found to pass arbitrary commands to the unit, and an entire community slowly emerged around modifications to the Linksys firmware. In addition, complete Linux kernel distributions have become available, allowing all sorts of functionality that Linksys (probably) never imagined.
There are now wireless routers on the market from Linksys, Netgear, Asus, Buffalo, Belkin, Motorola, and Siemens. All of these routers use chipsets from Broadcom. Some use Broadcom radios as well, while others use Prism or Atheros radios. A pretty complete list of these devices can be found at http://openwrt.org/TableOfHardware.
This hack covers the Linksys-based alternate firmware for these wireless routers, and shows how to install a complete Linux distribution, as well as some of the cool things that will let you do.
When Linksys finally released the modified Linux kernel and utilities they had included with the WRT54G, and made the code available as required by the General Public License (GPL), it became possible for software developers around the world to start modifying this code to suit their purposes. Code for all Linksys products that use Linux internally is available at http://www.linksys.com/support/gpl.asp.
We don't have the space to cover all of the alternate firmware available for Linksys and other Broadcom-based wireless routers. Two good places to go for information on other firmware, as well as to find updated releases, are http://linksysinfo.org and http://www.wrt54g.com.
|
5.6.1. Sveasoft Firmware
One of the first modified versions of the Linksys firmware came from a Swedish company, Sveasoft. They have continued to improve their product and now have two different offerings. Their stable tested code is released to the public with source code, free of charge, as required by the GPL. Newer code under development and access to their support forums are available for a $20 yearly subscription fee.
Early in the development process, access to the development code and the forums was freely available, and the conversion from a free to a paid service met with a lot of resistance from the community. One result of this is that there are now several forks of the Sveasoft firmware, by different developers, and over time these forks have developed different feature sets. You can find many of these forked firmware images on the web sites mentioned in the previous section.
At the time of this writing, the freely available Sveasoft firmware is known as Alchemy. We obtained our copy from http://linksysinfo.org. Converting your wireless router to the Alchemy firmware is fairly trivial and follows the same process for installing upgraded Linksys firmware.
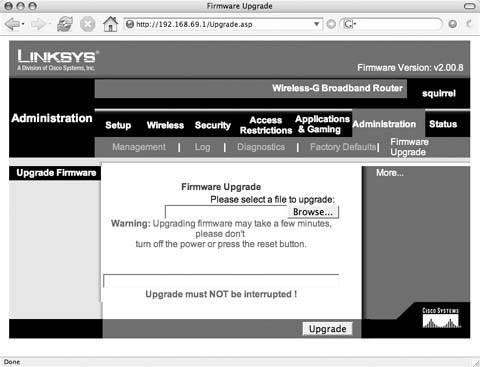
Use a web browser to load the Linksys administrative web pages. The default IP address for a Linksys router is 192.168.1.1. Login with the username and password you set. (You did change the default password from admin, didn't you?) Choose Administration images/U2192.jpg border=0> Firmware Upgrade, as shown in Figure 5-1.
Click Browse and locate the unzipped firmware file Alchemy-V1.0.bin. Select Upgrade to begin the firmware upload and upgrade. Do not interrupt this process! Upon completion, the router will reboot and load the new firmware.
|
The Sveasoft firmware gives your WRT54G some advanced features. We can't cover them all here, but we'll try to hit some of the high points. One of the most useful features for anyone who is sharing their broadband connection is the Quality of Service (QoS) capabilities now available. Anyone who's tried to make a VoIP phone call over a congested ADSL line will know exactly why QoS is so great.
Figure 5-1. WRT54G firmware upgrade
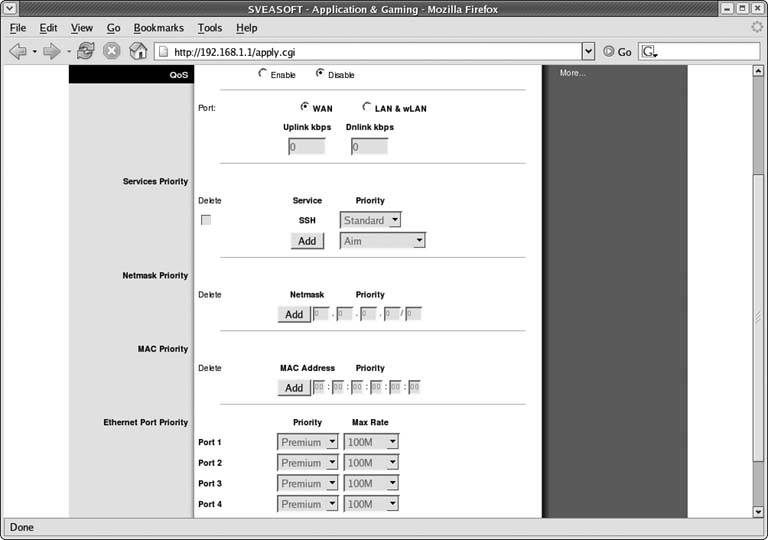
As shown in Figure 5-2, you can set the maximum uplink and downlink speeds for your WAN or LAN/Wireless connections. Once enabled, you can set QoS service priorities for protocols such as SSH, VoIP, and many others. This means that you can set the service priority for VoIP to High to ensure no other traffic takes priority. You can also set priorities for specific netmasks, MAC addresses, or the four Ethernet ports on the WRT54G.
Among the other features the Sveasoft firmware gives you are the ability to do OSPF routing, enable communication between access points using the Wireless Distribution System [Hack #69], run a SSH client and server, and finally, enable a Client Mode that allows you to connect to other access points.
5.6.2. OpenWRT
OpenWRT is the antithesis of all the Linksys-based firmware projects. It is a minimal Linux distribution with basic command-line tools and support for adding functionality via a package manager. While not practical for basic home use, OpenWRT is a powerful option for anyone who wants to have specific features enabled on their wireless router.
Figure 5-2. QoS settings
The project is under heavy development. As of this writing, the stable release has been removed from the web site, and the experimental code is available at http://openwrt.org/downloads/experimental/bin. The original OpenWRT code booted using a small partition in RAM, then created a secondary partition for loading the full firmware. The experimental release offers a second option of a single jffs2 (Journaling Flash File System) partition, which makes operations of the distribution much more simple.
In order to install the experimental release of OpenWRT you'll need to get the right version for your wireless router hardware. There are specific versions for WRT54G and WRT54GS hardware, as well as Motorola routers, and a generic version for other hardware models. Our units were both WRT54G models, so we downloaded the openwrt-wrt54g-jffs.bin file.
You can install the OpenWRT firmware using the Linksys web-based administration tools, as shown previously in Figure 5-1, or from any of the Linksys-based projects, all of which support firmware upgrades from their web pages. An alternative method involves enabling the boot_wait parameter in the NVRAM of your Linksys router and using a tftp client to send firmware to the Linksys during the boot process. Unless you have already installed an alternate firmware such as Sveasoft Alchemy, which allows you to set boot_wait from the web interface, this involves taking advantage of a bug in Ping.asp in the standard Linksys firmware. Details on this method can be found at http://openwrt.org/OpenWrtDocs/Installing.
The jffs2 versions of the OpenWRT firmware will take several minutes for the first bootup and will reboot before becoming usable. While booting, the DMZ LED will be lit and will turn off once the firmware has booted. The firmware configures the network interfaces, using DHCP for the WAN interface, and sets up a basic NAT/firewall. Once booted, you can telnet to the router using the last LAN IP address it was configured for.
As the documentation says:
Why no telnet password? Telnet is an insecure protocol with no encryption, we try to make a point of this insecurity by not enabling a password. If you're in an environment that requires password protection we suggest using the dropbear ssh server.
Setting up the dropbear SSH server is as simple as setting the root password:
# passwd foo
Once a password has been set, the telnet daemon is disabled, sshd is enabled, and you can now use any SSH client to access your router. You now have a complete, albeit small, Linux distribution running. What can you do with it?
The first thing you should do is see what packages come installed by default, using the ipkg package manager:
ipkg list_installed
Anyone who's used apt-get in Debian or Ubuntu distributions will be familiar with the syntax of ipkg. You'll want to update the list of available packages, and then you can list them:
ipkg update ipkg list
5.6.3. Hacking the Hack
Your options are really unlimited at this point, especially if you've loaded OpenWRT. This is a complete Linux distribution, and short of running things like a window manager, just about anything is possible. There are packages available to run a web server, FreeRADIUS for authentication, IPSec VPN software, and at least two different captive portal packages: NoCatSplash [Hack #75] and WiFiDog (http://old.ilesansfil.org/wiki/WiFiDog). For even more fun with OpenWRT, you can set up true mesh networking [Hack #68] using the OLSR mesh networking protocol.
Bluetooth, Mobile Phones, and GPS
- Hacks 122: Introduction
- Hack 1. Set Up Bluetooth on Linux
- Hack 2. Set Up Bluetooth on Windows XP
- Hack 3. Connect Mac OS X with a Bluetooth Phone
- Hack 4. Connect Linux with a Bluetooth Phone
- Hack 5. Connect Windows XP with a Bluetooth Phone
- Hack 6. Use Your Treo as a Modem
- Hack 7. Send SMS from a PowerBook
- Hack 8. Remote Control Mac OS X with Bluetooth Phones and PDAs
- Hack 9. Remote Control Linux with a Bluetooth Phone
- Hack 10. Control XMMS with Bluetooth
- Hack 11. Liven Up Parties with a Participatory Slideshow
- Hack 12. Send SMS from Linux
- Hack 13. Remote Control Windows with Bluetooth Phones and PDAs
- Hack 14. Control Your Bluetooth Phone with FMA
- Hack 15. Control Your Computer from Your Palm
- Hack 16. Control Your Home Theater from Your Palm
- Hack 17. Choose a Cellular Data Plan
- Hack 18. Blog from Your Mobile Phone
- Hack 19. Get Google Maps on Your Mobile Phone
- Hack 20. Share Your GPS
- Hack 21. Broadcast Your GPS Position
- Hack 22. Map Wi-Fi Networks with Kismet and GPSd
Network Discovery and Monitoring
- Hacks 2339: Introduction
- Hack 23. Find All Available Wireless Networks
- Hack 24. Discover Networks with NetStumbler
- Hack 25. Detect Networks with Handheld PCs
- Hack 26. Find and Join Wireless Networks with AP Radar
- Hack 27. Detect Networks on Mac OS X
- Hack 28. Scan Passively with KisMAC
- Hack 29. Detect Networks with Kismet
- Hack 30. Monitor Wireless Links in Linux with Wavemon
- Hack 31. Analyze Traffic with Ethereal
- Hack 32. Track 802.11 Frames in Ethereal
- Hack 33. Watch Network Traffic
- Hack 34. grep Your Network
- Hack 35. Check Wi-Fi Network Performance with Qcheck
- Hack 36. Estimate Network Performance
- Hack 37. Get Real-Time Network Stats
- Hack 38. Graph Your Wireless Performance
- Hack 39. Find Radio Manufacturers by MAC
Wireless Security
- Hacks 4051: Introduction
- Hack 40. Stop Moochers from Stealing Your Wi-Fi Bandwidth
- Hack 41. Visualize a Network
- Hack 42. Secure Your Linux Network with WPA
- Hack 43. Control Wireless Access by MAC
- Hack 44. Authenticate Wireless Users
- Hack 45. Forward Ports over SSH
- Hack 46. Proxy Web Traffic over SSH
- Hack 47. Securely Connect Two Networks
- Hack 48. Generate a Tunnel Configuration Automatically
- Hack 49. Poll Wireless Clients
- Hack 50. Interrogate the Network
- Hack 51. Track Wireless Users
Hardware Hacks
- Hacks 5262: Introduction
- Hack 52. Add an External Antenna
- Hack 53. Do-It-Yourself Access Point Hardware
- Hack 54. Boot from a Compact Flash Hard Drive
- Hack 55. Increase the Range of a PowerBook
- Hack 56. Send Power over Your Ethernet
- Hack 57. The NoCat Night Light
- Hack 58. Upgrade the Linksys WET11
- Hack 59. Scan for Wireless Networks Automatically
- Hack 60. Backlight Your Zipit
- Hack 61. Unwire Your Pistol Mouse
- Hack 62. Mobilize Your WRT54G with the WiFiCar
Software Hacks
- Hacks 6382: Introduction
- Hack 63. Build Your Own Access Point with Linux
- Hack 64. Bridge Your Linux AP
- Hack 65. Protect Your Bridge with a Firewall
- Hack 66. Filter MAC with HostAP and Madwifi
- Hack 67. Upgrade Your Wireless Router
- Hack 68. Set Up an OLSR Mesh Network
- Hack 69. Extend Your Wireless Network with WDS
- Hack 70. Pebble
- Hack 71. Wall Off Your Wireless
- Hack 72. Run Your Mac as an Access Point
- Hack 73. Run Linux on the Zipit Wireless Messenger
- Hack 74. Capture Wireless Users with NoCatAuth
- Hack 75. Capture Wireless Users on a Small Scale
- Hack 76. Build an Online Community in Your Offline Neighborhood
- Hack 77. Manage Multiple AirPort Base Stations
- Hack 78. Advertise Bonjour Services in Linux
- Hack 79. Advertise Any Service with Bonjour in Mac OS X
- Hack 80. Redirect Brought to you by Bonjour Ads
- Hack 81. Use a Windows-Only Wireless Card in Linux
- Hack 82. Use Your Orinoco Card with Hermes AP
Do-It-Yourself Antennas
- Hacks 8393: Introduction
- Hack 83. Make a Deep Dish Cylindrical Parabolic Reflector
- Hack 84. Spider Omni Antenna
- Hack 85. Pringles Can Waveguide
- Hack 86. Pirouette Can Waveguide
- Hack 87. Primestar Dish with Waveguide Feed
- Hack 88. Primestar Dish with Biquad Feed
- Hack 89. Cut a Cable Omni Antenna
- Hack 90. Build a Slotted Waveguide Antenna
- Hack 91. The Passive Repeater
- Hack 92. Determine Your Antenna Gain
- Hack 93. Build Cheap, Effective Roof Mounts
Wireless Network Design
- Hacks 94100: Introduction
- Hack 94. Analyze Elevation Profiles for Better Long-Range Wireless Networking
- Hack 95. Build a Wireless Network for the Large House
- Hack 96. Establish Line of Sight
- Hack 97. Calculate the Link Budget
- Hack 98. Align Antennas at Long Distances
- Hack 99. Slow Down to Speed Up
- Hack 100. Take Advantage of Antenna Polarization
Appendix A. Wireless Standards
- Appendix A. Wireless Standards
- Section A.1. 802.11: The Mother of All IEEE Wireless Ethernet
- Section A.2. 802.11a: The Betamax of the 802.11 Family
- Section A.3. 802.11b: The De Facto Standard
- Section A.4. 802.11g: Like 802.11b, only Faster
- Section A.5. 802.16: WiMAX Long Distance Wireless Infrastructure
- Section A.6. Bluetooth: Cable Replacement for Devices
- Section A.7. 900 MHz: Low Speed, Better Coverage
- Section A.8. CDPD, 1xRTT, and GPRS: Cellular Data Networks
- Section A.9. FRS and GMRS: Super Walkie-Talkies
- Section A.10. 802.1x: Port Security for Network Communications
- Section A.11. WPA & 802.11i
- Section A.12. BSS Versus IBSS
Appendix B. Wireless Hardware Guide
EAN: 2147483647
Pages: 178

