Section 20.4. Privacy as a Process
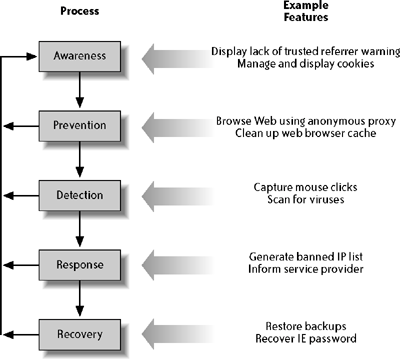
20.4. Privacy as a ProcessAs we progressed, it became more and more apparent that the most natural way to look at the privacy space was to view privacy as a process using the framework to model that process. In the process model, there is a "building up" of information feeding back to the user. We could say that the more categories a solution's features belong to, the more comprehensive it must be (and assume that a more comprehensive solution is better, as it gives the user more control over his privacy). Hence, the "best" solutions have features to address each stage of the process. Figure 20-3 illustrates this idea, showing examples of features from the study[28] along each stage in the privacy process.
The privacy process shown in this figure begins with general awareness of privacy needs and issues and includes feedback from each stage, with each stage adding to our knowledge and ability to make informed decisions, as follows:
This process description may seem confusing because there is a lot of interplay between stages, and because our vocabulary to describe what is happening is somewhat limited. Still, it is important for users to understand that privacy is an ongoing process that requires continuous attention. |
EAN: 2147483647
Pages: 295