NTFS File Permissions
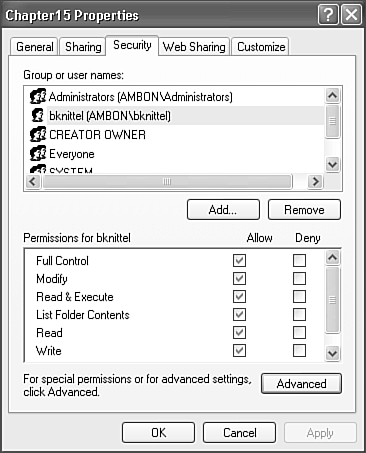
| If your hard drive is formatted using the NTFS (NT File System) directory structure, and you're not using Simple File Sharing, you can assign control of who is permitted to access files and folders on a per-user or per-group basis. To display or modify NTFS permissions, select a file or folder in Windows Explorer, right-click Properties, and select the Security tab, as shown in Figure 28.14. Figure 28.14. You can use the NTFS Permissions dialog box to a folder to restrict access to both network and local users.
In the top part of the dialog box is the list of users or user groups with access to the file or folder. You can select any of the names in the list to view their associated permissions in the bottom half of the dialog. The permission properties can each be granted or revoked individually. The permissions are Full Control, Modify, Read & Execute, List Folder Contents, Read, and Write. Their properties are listed in Table 28.2.
Note that each permission has both Allow and Deny check boxes. To get access to a given resource, a user must be explicitly listed with Allow checked or must belong to a listed group that has Allow checked, and must not be listed with Deny access or belong to any group with Deny marked. Deny preempts Allow. All these permissions are additive. In other words, Read and Write can both be checked to combine the properties of both. Full Control could be marked Allow but Write marked Deny to give all access rights except writing. (This permission would be strange but possible.) The most productive use of NTFS file permissions is to assign most rights by group membership. One exception is with user home directories or profile directories, to which you usually grant access only to the Administrators group and the individual owner. TIP If you edit Permissions, before you click OK or Apply, click the Advanced button and view the Effective Permissions tab, as discussed later in this chapter. Enter a few usernames to see that the permissions work out as you expected. If they do, only then should you click OK.
Inheritance of PermissionsNormally, permissions are assigned to a folder (or drive), and all the folders and files within it inherit the permissions of the top-level folder. This makes it possible for you set permissions on just one object (folder), to manage possibly hundreds of other files and folders contained within. If necessary, explicit permissions can be set on a file or subfolder to add to or override the inherited permissions. Permissions displayed in the Security tab (as in Figure 28.13) will be grayed out if they have been inherited from a containing folder. You can view or change the inheritance setting for a file or folder by clicking the Advanced button on the Security properties page. In Figure 28.15, the folder has a check in Inherit from Parent the Permission Entries that Apply to Child Objects. That's the usual case. Figure 28.15. The Advanced Permissions dialog box lets you control the inheritance of permissions, and set detailed permissions for user and groups.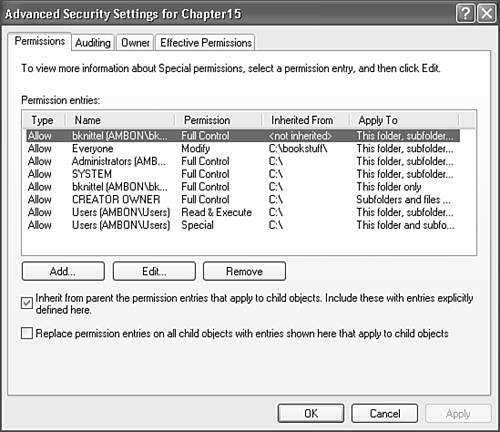 If you uncheck the box, Windows gives you the option of starting with a blank permissions list (Remove) or keeping a copy of the settings it had before (Copy). In either case, the item now has its own independent list of access rights, which you can edit at will. When you change permissions on a folder, you may want to cancel any manually added permissions set on the files and folders it contains. Checking the Replace Permission Entries on All Child Objects box will reset the permissions on all files in this folder and in subfolders, and will force all subfolders to inherit permissions from this folder. CAUTION Changing the permissions of the root folder of the drive containing Windows may make your system unusable. It's best not to mess with the permissions of your boot (usually C:) drive. Advanced Security SettingsIf you edit access permissions in the Advanced Security Settings dialog, you can exercise more "fine grained" control over permissions. It's rarely necessary, but for your reference, Table 28.3 lists the available permission settings.
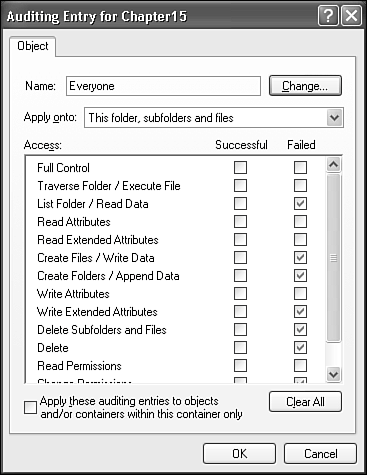
Viewing Effective PermissionsThe Effective drive Permissions tab on the Advanced Security page lets you enter a username and see what privileges the user will have as a result of the current security settings on the file or folder, as shown in Figure 28.16. Figure 28.16. Effective Permissions shows you how edited Permissions settings will work before they're actually applied to the file.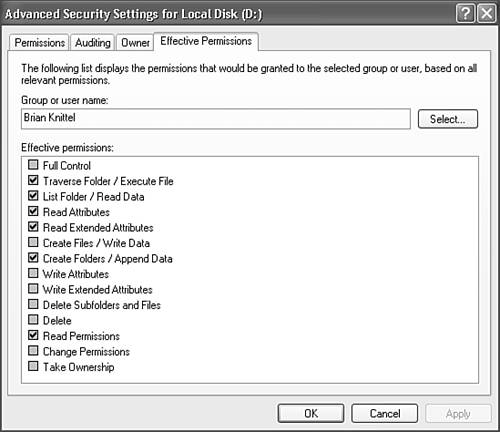 This dialog box displays the effective permissions as edited, before they are applied to the file folder. This lets you verify that the permissions you have set operate as desired before committing them to the file by clicking OK or Apply. Access AuditingThe Advanced Security drive Settings dialog provides a way for you to monitor access to files and folders through the Event Log. The Auditing tab (see Figure 28.17) lets you specify users and access types to monitor, and whether to record log entries for successful access, failure to access, or both. Auditing can be set for the use of each access attribute that you can set with Permissions: List Folder, Write Data, and so on. Figure 28.17. Auditing properties record events in the Security Event log whenever the selected access privileges succeed and/or fail.
Auditing is useful in several situations:
To enable auditing, locate the folder or file you want to monitor, view its Security properties, click Advanced, view the Auditing page, and click Add. Select a specific user or group (or Everyone), and check the desired events to audit. You can prevent a new audit setting from propagating into subfolders by checking Apply These Auditing Entries to Objects and/or Containers Within This Container Only. You can enable the resetting of audit properties of all subfolders and files by checking "Replace Auditing Entries on All Child Objects…" An entry is made in the Security Event log for each audited access, so be careful if you are enabling auditing on the entire hard drive! Taking Ownership of FilesSometimes files or folders have security attributes set so stringently that even Administrator can't read or modify them. Usually this occurs when the file has permissions set only for its owner and not the usual list: Owner, Administrator, System, and Backup Operators, as when a user account is deleted. In this case, no user is able to access the files in that user's My Documents folder. If you absolutely need to access such files, you can take ownership of the file or folder, and then assign permissions to read and write as appropriate. To take ownership of a file or folder
Assigning Permissions to GroupsIt's common in an office environment to want shared folders that are accessible by some users and not by others. For instance, you may wish to put payroll information in a shared folder and grant access only to certain administrative employees. In a school environment, you might want some folders that are accessible only by teachers, and others accessible only by members of a particular class. If you're using Simple File Sharing, this isn't possible, but if you are using manual permissions, it's fairly straightforward. The best practice in this case is to create local user groups, which are collections of users that can be given privileges that carry over to the group's members. You can add the group and assign permissions for specific folders and files without having to list each of the qualified users separately. Another benefit is that you can add and remove users from the group later on without having to modify the settings of the various folders. To create local user groups, follow these steps:
To grant the group permissions to specific folders
Securing Your PrintersIf you have a printer that uses expensive paper or ink, and are concerned that guests, kids or unauthorized persons might use your printer, you should know that printers can be secured in the same way that access is controlled for files and folders: through user and group privileges. In the case of printers, the privileges allow users to add jobs to the printer, delete other people's jobs, and so on. On a domain network, the network manager usually takes care of this. And on a workgroup it's generally not important to restrict access to printers. If you are using Simple File Sharing, it's not even possible to set up specific printer access privileges. If you decide to, however, you can set printer access permissions by right-clicking a printer in your Printers folder and selecting Properties. The Security properties tab resembles the properties tab of files and folders, and can be modified in the same way. |
EAN: 2147483647
Pages: 450